Analysts from AquaSec discovered new malware for Linux. The malware, named Koske, is believed to have been developed using AI. To execute directly into memory, the malware uses JPEG images of pandas.
Researchers describe Koske as a “sophisticated Linux threat,” whose adaptive behavior suggests that the malware is being developed using large language models (LLMs) or automation frameworks.
The main goal of Koske is to deploy CPU- and GPU-optimized miners that utilize the host’s computing resources to mine various cryptocurrencies.
As Serbian IP addresses and phrases were discovered in the scripts during the study of the malware, along with the Slovak language in the GitHub repository where the miners were hosted, experts were unable to determine a precise attribution.
Initial access is gained by attackers exploiting misconfigurations in JupyterLab, which allow for command execution. After this, the attackers download two .JPEG images of pandas into the victim’s system, hosted on legitimate services such as OVH images, freeimage, and postimage. The malicious payload is hidden within these images.
It is emphasized that the hackers do not use steganography to hide malware inside the images. Instead, they rely on polyglot files, which can be read and interpreted as several different formats. In Koske attacks, the same file can be interpreted as an image or a script, depending on the application that opens or processes it.
Images of pandas contain not only the picture itself, with correct JPEG format headers, but also malicious shell scripts and code written in C, allowing for both formats to be interpreted separately. That is, when opening such a file, the user will only see a cute panda, while the script interpreter will execute the code added at the end of the file.
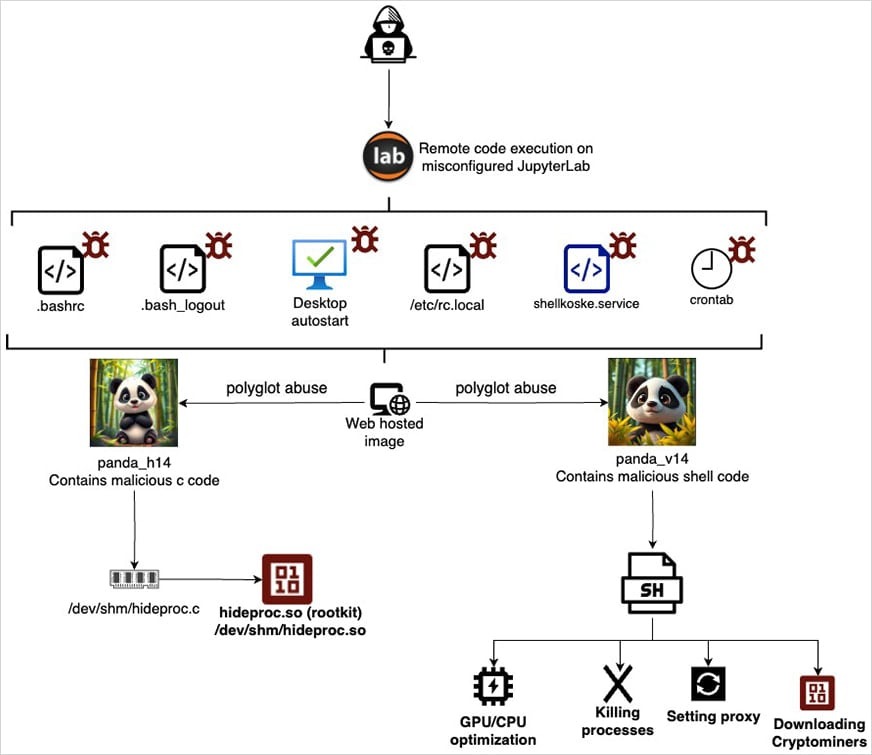
Researchers report that each image hides one payload, with both being executed in parallel.
“One payload consists of C code, which is directly written into memory, compiled, and executed as a shared object (.so file), functioning as a rootkit,” explain the experts. “The second payload is a shell script, which is also executed from memory. It uses standard Linux system utilities for stealth and persistence, leaving minimal traces.”
The script also ensures connection stability and bypasses network restrictions: it rewrites /etc/resolv.conf to use DNS from Cloudflare and Google, and protects this file with chattr +i. Additionally, the malware resets iptables rules, clears system variables related to proxies, and runs a custom module for brute-forcing working proxies using curl, wget, and direct TCP requests.
Due to this adaptability and behavior, researchers suggest that the malware may have been developed either with the help of large language models (LLM) or using automation platforms.
Before deploying on the victim’s machine, the malware assesses the host’s capabilities (CPU and GPU) to select the most suitable miner: Koske supports mining 18 different cryptocurrencies, including Monero, Ravencoin, Zano, Nexa, and Tari.
If a certain currency or pool becomes unavailable, the malware automatically switches to a backup option from an internal list, which also indicates a high degree of automation and flexibility.