Numerous Cisco devices are vulnerable to an actively exploited zero-day vulnerability (CVE-2025-20352) in IOS and IOS XE. The issue allows attackers to remotely trigger a denial-of-service condition or execute code on vulnerable devices.
According to the developers, the vulnerability is present in all supported versions of Cisco IOS and Cisco IOS XE—the operating system that runs on a wide range of the company’s networking equipment. The bug can be used by low-privileged users for DoS attacks, or by high-privileged users to execute arbitrary code with root privileges.
“The Cisco PSIRT team is aware of exploitation of this vulnerability in real-world attacks following the compromise of local administrator credentials,” the company said in its published advisory. “Cisco strongly recommends that customers update to a fixed software version to remediate this vulnerability.”
At the same time, no further information about the vulnerability’s use in real-world attacks has been disclosed.
The vulnerability is caused by a stack overflow in the IOS component responsible for handling SNMP (Simple Network Management Protocol) — a protocol that routers and other equipment use to collect and process information about devices on the network. To exploit the issue, an attacker only needs to send specially crafted SNMP packets over IPv4 or IPv6.
To execute malicious code, a remote attacker will need a read-only community string—an SNMP-specific form of authentication for accessing managed devices. The attacker will also need to have privileges on the vulnerable system, after which they can achieve remote code execution with root privileges.
To carry out a denial-of-service attack, an attacker needs only a read-only community string or valid SNMPv3 user credentials.
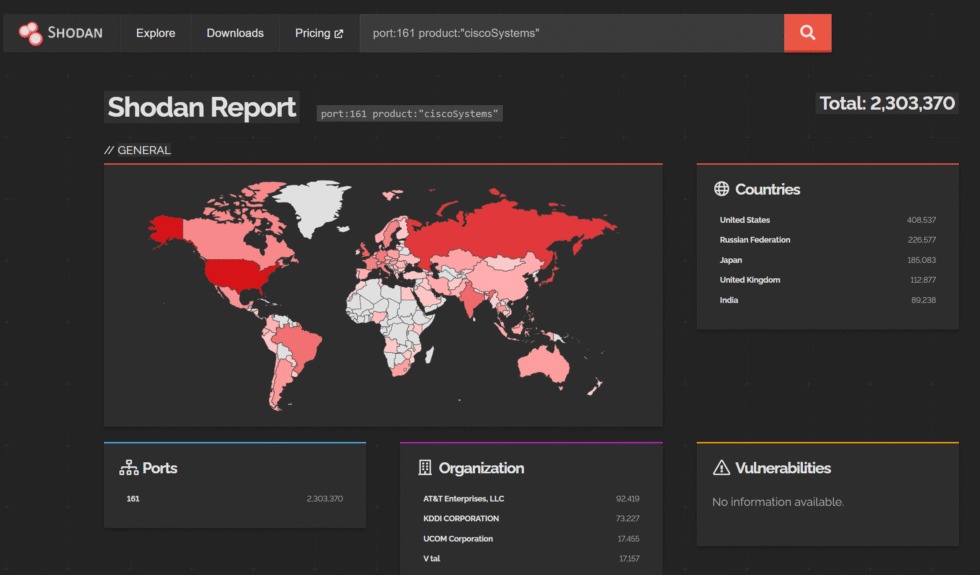
In general, leaving SNMP devices accessible over the Internet is considered bad practice. However, noted security researcher Kevin Beaumont points out that the Shodan search engine shows more than 2 million such devices accessible worldwide.
To protect against exploitation, it’s recommended to install the patch released by Cisco as soon as possible. For those who cannot do this immediately, it is recommended to restrict SNMP access to trusted users only and monitor Cisco devices using the snmp command in the terminal.
In addition to CVE-2025-20352, Cisco has fixed 13 vulnerabilities in its products, including two issues for which proof-of-concept exploits are already available.
The first is a reflected XSS vulnerability in Cisco IOS XE (CVE-2025-20240) that an unauthenticated remote attacker can use to steal cookies from vulnerable devices.
The second is a denial-of-service (DoS) vulnerability (CVE-2025-20149) that allows authenticated local attackers to forcibly reboot affected devices.
Additionally, Cisco is urging customers to urgently patch two vulnerabilities affecting the VPN web server in Cisco Secure Firewall Adaptive Security Appliance (ASA) and Cisco Secure Firewall Threat Defense (FTD), which, according to the company, are already being exploited by hackers.
CVE-2025-20333 (9.9 on the CVSS scale) is a vulnerability in the validation of user input in HTTP(S) requests that allows an authenticated remote attacker with valid VPN user credentials to execute arbitrary code with root privileges by sending specially crafted HTTP requests.
CVE-2025-20362 (6.5 on the CVSS scale) — a vulnerability in improper validation of user input in HTTP(S) requests that allows an unauthenticated remote attacker to access protected sections of the web interface without authentication by sending specially crafted HTTP requests.
Cisco says it is aware of “attempts to exploit” both vulnerabilities but does not disclose who might be behind them or how widespread the attacks are. The bugs are believed to be used together to bypass authentication and execute malicious code on vulnerable devices.
