Experts from Eclypsium demonstrated at DEF CON 33 an attack codenamed BadCam, which exploits vulnerabilities in certain Lenovo webcam models, turning them into tools for remote BadUSB-style attacks.
“This allows remote attackers to perform stealthy keystroke injections and launch attacks regardless of the host operating system,” the authors of the attack say.
The BadCam issue has been assigned CVE-2025-4371, and the researchers claim it is the first real-world demonstration that attackers who remotely seize control of Linux‑based USB peripherals can use them for malicious purposes.
BadUSB attacks were first demonstrated more than 10 years ago by security researchers Karsten Nohl and Jakob Lell at the Black Hat 2014 conference.
Today this term refers to a whole class of attacks that, for example, can exploit vulnerabilities in device firmware, causing a connected device to masquerade as something else—such as an HID device (keyboard or mouse), Ethernet (network adapter), or Mass Storage (removable drive). This allows the device to be used to covertly execute commands or launch malicious software on the victim’s computer.
However, BadUSB devices are usually created in advance and deliberately. For example, in 2022 the FIN7 hacking group sent malicious USB devices to U.S. companies in the hope of infecting their systems and gaining an initial foothold for attacks. Similarly, in 2020, a U.S. company in the hospitality industry was mailed a fake Best Buy gift card along with a malicious USB flash drive.
Now researchers at Eclypsium have demonstrated that ordinary USB peripherals, never intended for malicious activity, can also become a vector for BadUSB attacks. In particular, it turned out that such devices can be remotely hijacked and turned into BadUSB devices without physically unplugging or replacing them.
“An attacker who has obtained remote code execution on the system can reflash a connected webcam running Linux, repurposing it to function as a malicious HID device or to emulate additional USB devices,” the researchers explain. “After that, the innocuous webcam could perform keystroke injections, deliver malicious payloads, or serve as a beachhead for deeper persistence in the system, all while retaining its normal appearance and primary functionality.”
It is also noted that the infection would allow an attacker to establish a persistent foothold in the system and re-compromise the victim’s computer even after a full wipe and OS reinstallation.
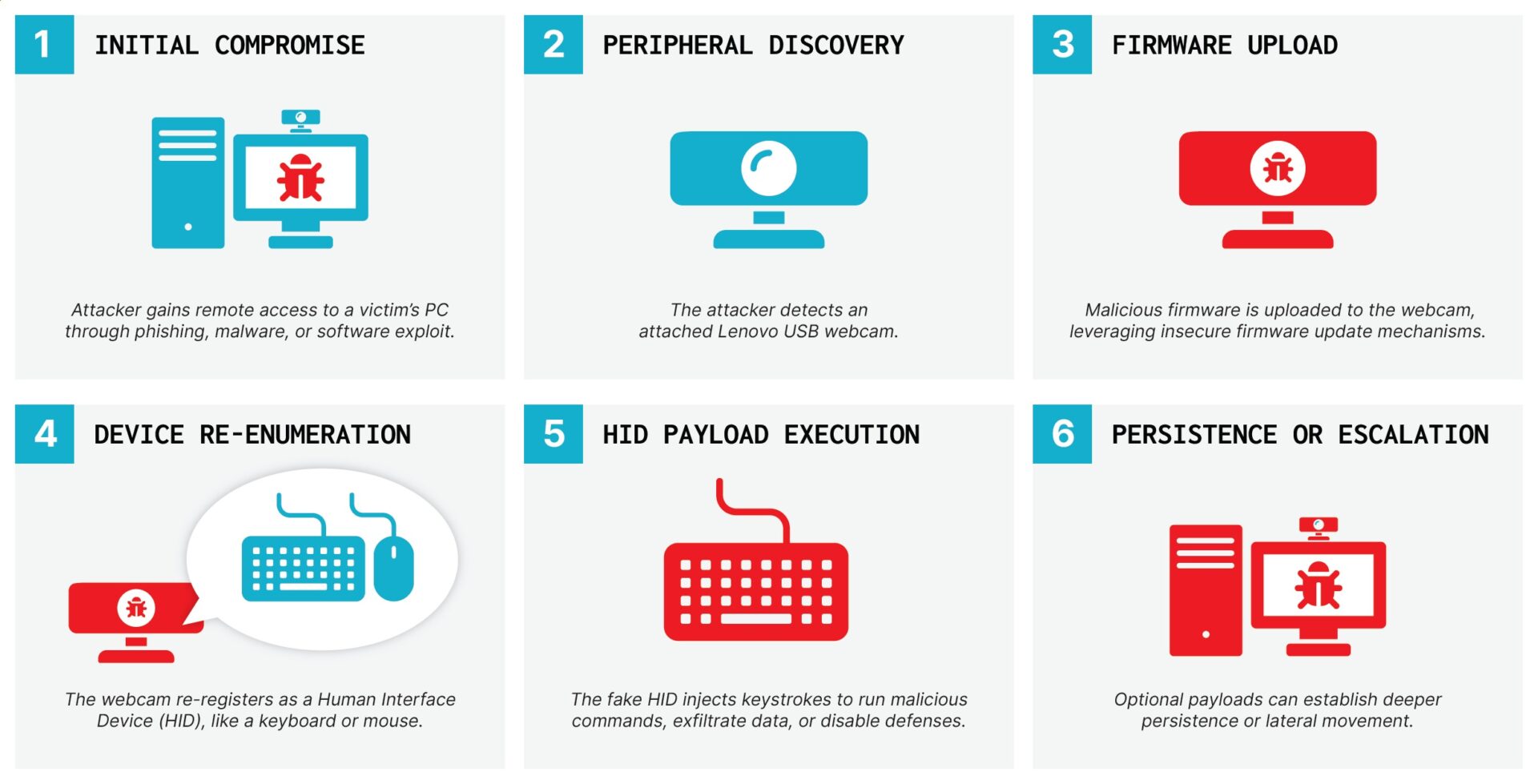
Vulnerabilities enabling the BadCam attack were discovered in the Lenovo 510 FHD and Lenovo Performance FHD webcams, whose firmware was developed by the Chinese company SigmaStar. The issues stemmed from the devices not validating firmware—there was no signature verification—so the cameras were susceptible to full compromise, since they run Linux with USB Gadget support.
Researchers say that a known Linux kernel vulnerability (CVE-2024-53104), for example, could have been used to gain control of the host in order to deploy malicious firmware to a connected USB camera.
Experts notified Lenovo about the discovered issues in April 2025, after which the manufacturer released a firmware update (version 4.8.0) to address the vulnerabilities and, together with SigmaStar, developed a tool that fixed the issue.
“This first-of-its-kind attack clearly illustrates a subtle yet extremely dangerous vector: enterprise and consumer computers often trust their internal and external peripherals, even when those peripheral devices are capable of running their own operating systems and receiving remote instructions,” Eclypsium says. “In the context of Linux webcams, unsigned or poorly protected firmware allows an attacker to compromise not only the host, but also any other hosts to which this camera will be connected in the future, spreading the infection and bypassing traditional defenses.”
Although Eclypsium’s research focused on Lenovo webcams, other peripheral USB devices running Linux may also have similar vulnerabilities.
