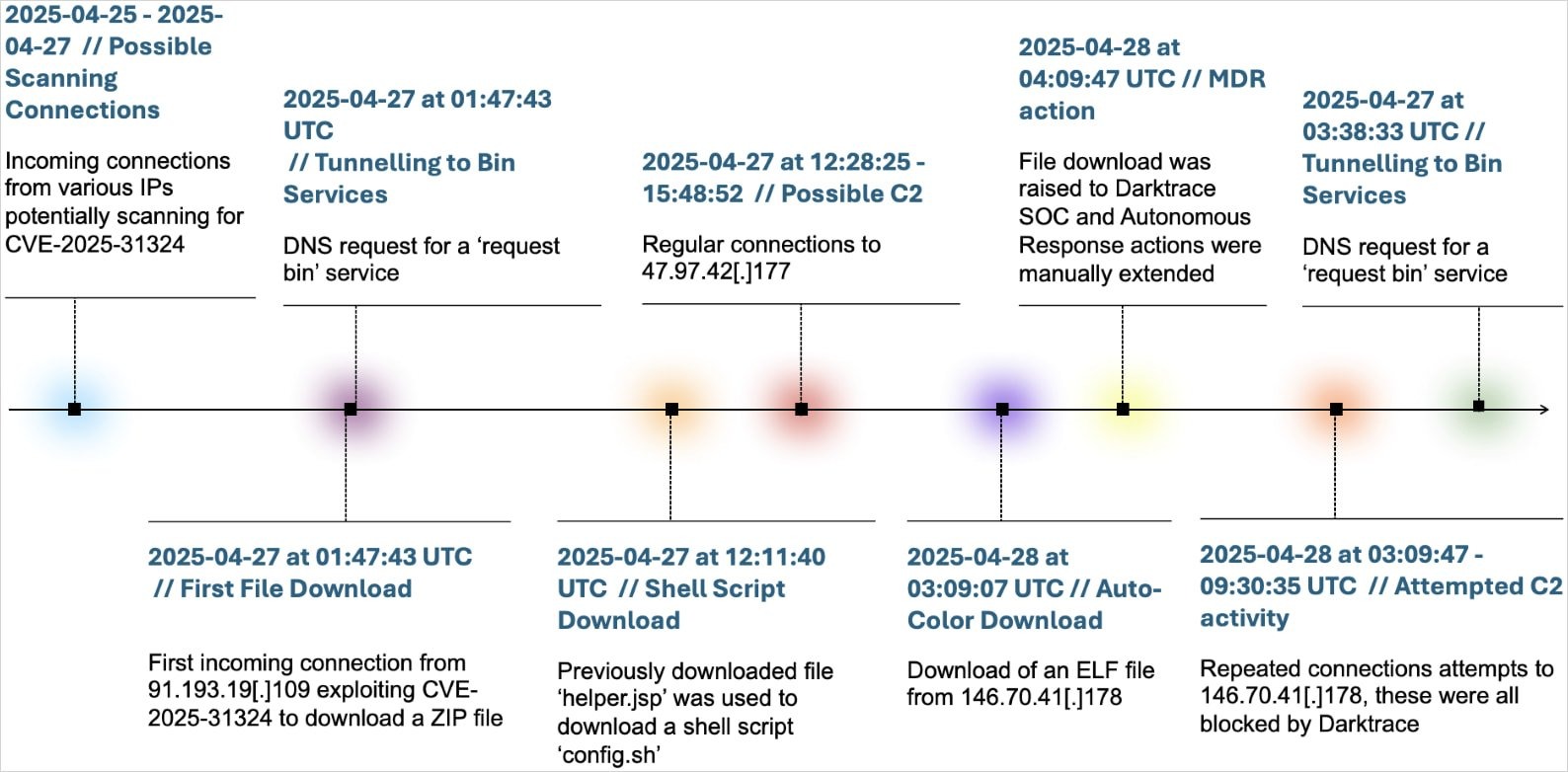
Experts at Darktrace warned that hackers exploited a critical vulnerability in SAP NetWeaver (CVE-2025-31324) to deploy Linux malware Auto-Color into the network of an unnamed American chemical company.
Researchers discovered an attack in April 2025, and during the incident investigation, it was revealed that in recent months Auto-Color has changed and begun employing new methods to evade detection.
Recall that Auto-Color was first discovered by Palo Alto Networks specialists in early 2025. At that time, it was noted that the malware possesses an entire arsenal of techniques which it uses to evade detection. Among these are: using seemingly harmless file names (such as door or egg), concealing C&C communications, and employing proprietary encryption algorithms to mask communication and configuration information.
The backdoor adjusts its behavior depending on the user’s privilege level and uses ld.so.preload for covert data preservation through shared object injections.
Auto-Color is capable of: launching a reverse shell, collecting system information, creating and modifying files, running programs, using the infected machine as a proxy, and even self-destructing with the help of a special “kill switch” in the code. This last feature allows attackers to remove traces of the infection from compromised machines.
“If the command and control server is unavailable, Auto-Color effectively halts and does not engage its full malicious functionality, appearing quite harmless to analysts,” notes Darktrace. “This behavior hinders analysis and prevents the identification of specific payloads, credential theft mechanisms, or persistence methods being used.”
However, specialists from Palo Alto Networks were unable to identify the initial attack vector, which at the time targeted universities and government organizations in North America and Asia.
As experts from Darktrace have now reported, the attackers behind Auto-Color are exploiting the critical vulnerability CVE-2025-31324 in NetWeaver, which allows malicious binaries to be uploaded for remote code execution without authentication.
SAP developers patched this vulnerability in April 2025, but even then, cybersecurity specialists warned of active exploitation attempts. By May 2025, ransomware groups and Chinese “government” hackers had joined the attacks, and the company Mandiant found evidence that the vulnerability had been used as a 0-day at least since mid-March 2025.