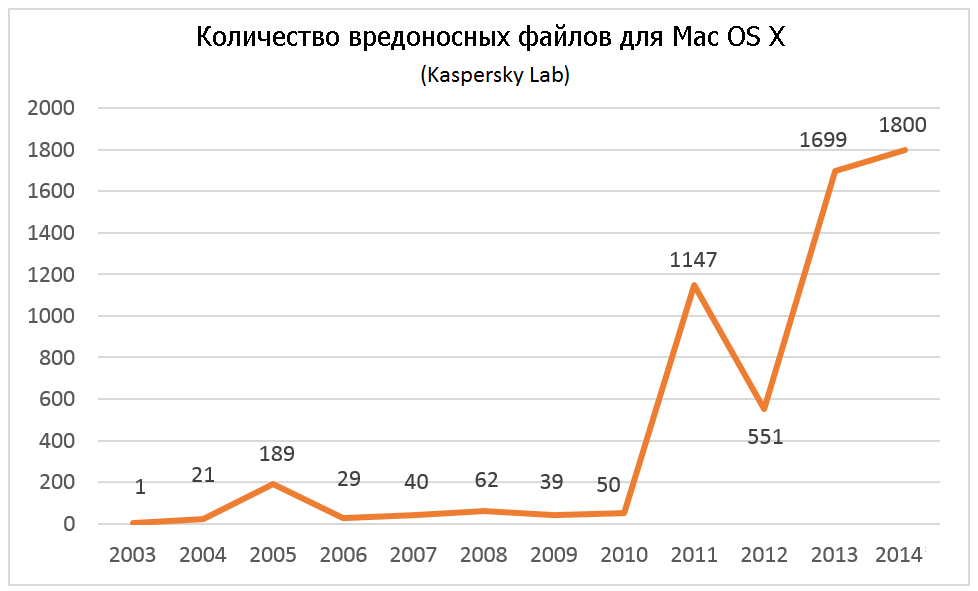
According to Kaspersky Lab, the number of malicious programs targeting Apple products is nearing 1800. In the first eight months of 2014 alone, researchers have found some 25 new families of malware for OS X.
Of course, it was influenced by the fact that, since 2008, the share of computers running this OS almost doubled by jumping from 4.9 to 9.3%. The key difference between the evolution of malware for this platform and malicious programs targeting Windows is that there was no so-called “infancy” period. I mean there was some amateurish lamer stuff, but not any mass dominance of Trojans created as a “kitchen-table” effort or “just for fun”. I will briefly describe some instances of the past few years.
Renepo aka Opener (October 2004)
Malicious bash script with a backdoor and spyware. Required root privileges in order to work. Was able to spread through USB drives. Downloaded John The Ripper, a password cracker, and tried to crack passwords collected on the computer. Blocked the built-in firewall and opened the port to listen for commands from a remote host.
Leap (February 2006)
Distributed via iChat messenger. After infecting a computer, it was sending itself to all found contacts as latestpics.tgz, an archive, and, once unpacked, was disguised as a JPEG picture. Worked only with root privileges.
RSPlug aka Jahlav (October 2007)
In fact, this was an implementation of DNSChanger, a Trojan, for Mac platform. The infection occurred when a user visited some malicious porn sites. The attempt to view the video was followed by a message requiring to download and install missing codecs to the system. Malicious files were downloaded as DWG virtual disk image and, again, the installation required root privileges. Subsequently, the malicious program substituted DNS server and all traffic was redirected to phishing servers used by hackers. The user was flooded with advertising, but it was only half of the problem. All credentials also ended up in the hands of bad guys. DNSChanger family has its roots in Zlob family, which, in turn, is of Russian origin and is associated with the activities of infamous Russian Business Network.
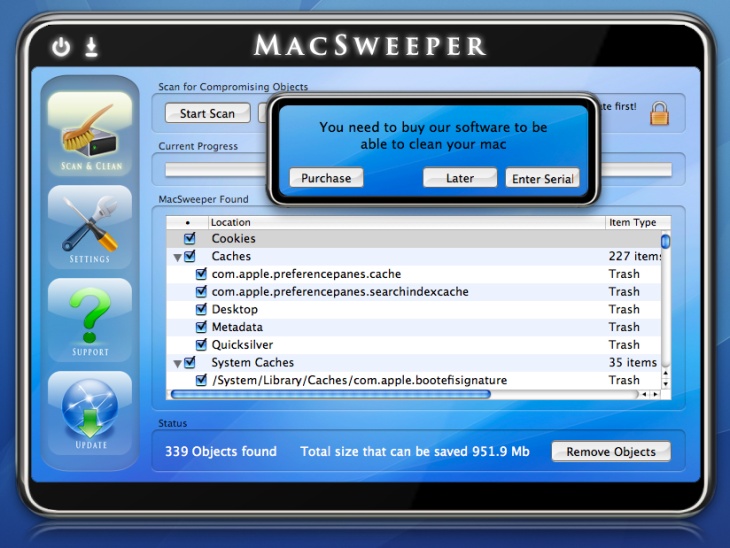
MacSweeper (January 2008)
First representative of rogue software for Mac OS. Tried to clean the computer from hell knows what and demanded money for it. Designed by an obscure firm called “KiVVi Software” and distributed through their web site with installers of other applications. Also had its own web site macsweeper.com, where the entire section about was taken from the web site of Symantec. As they say, “an offense committed with great cynicism”.
Tored (April 2009)
E-mail worm. Written in RealBasic, used its own implementation of SMTP to send copies of itself to everyone found in address book. Contained some errors and, as a result, was unable to function in some cases. Inserted the following line in the subject field of the message: “For Mac OS X!:(If you are not on Mac please transfer this mail to a Mac and sorry for our fault :)”, hoping that Windows users would forward this message to someone else.
First Wave
As you can see, all of these instances were not particularly frightening. This is true, but everything was still to come…
FlashFake
In March 2012, Kaspersky Lab published information about a botnet that included some 600 thousand Mac computers. All of them were infected with a Trojan dubbed FlashFake. This name was chosen because it was masquerading as the installer of Adobe Flash Player. The first versions of FlashFake were discovered in September 2011. FlashFake used DGA to communicate with its command servers.
The main feature of FlashFake was that it did no longer require any action by a Mac user, except visiting the web site with malicious redirects. Previously, the malicious programs were masquerading as installation files and, for their successful work, the user had to enter a password, which substantially reduced the risk of infection. The first version of FlashFake also was well on the beaten track, but the second, which appeared in February 2012, began to use for its installation the vulnerabilities of Java virtual machine CVE-2011-3544 and CVE-2008-5353.
So how did the infection happen? In Google search results alone, there were about four million Web pages containing redirects to a malicious JAR file. In the case of its successful launch, the loader of FlashFake located in the JAR file would contact the command and control center and download two modules. One of them was the main module responsible for further interaction with C&C and updates, while the second was used for embedding into the browser. The latest versions of FlashFake have been noted for the search of their command and control centers via Twitter.
After exploiting as much as they could the computing power of unsuspecting users, the unidentified attackers closed down their shop in May of 2012. This is when the command and control centers stopped their operation. The profit was generated by driving up the traffic to the web sites (advertising revenue) and manipulating search results (using “forbidden” methods of Black SEO to promote web sites). This has shaken somewhat the faith of Mac users in their “secure” platform.
Revir/Imuler
The entire year of 2012 passed under the motto “More Good and Diverse Trojans for Macs in Tibet”. The first sign was Revir/Imuler family (according to F-Secure classification), its double name can be explained as follows: Revir is a dropper and Imuler is a backdoor (Dr.Web calls it Muxler) installed by the dropper.
The methods used for distributing Revir were rather primitive but effective. The infection was targeted and focused. In fact, these were APT attacks. Revir.A was an executable file that masqueraded as PDF. Revir.B, a variation, was secretly installing Imuler.A (just like Revir.A), but it was masquerading as JPG picture. Revir.C also disguised itself as a picture, but it was placed in the archive, which also included many real pictures of Irina Shayk, a Russian model. For its part, an archive with Revir.D and another set of pictures downloaded Imuler.B.
It was assumed that the distribution of these threats was linked to Chinese-Tibetan conflict and aimed against various militant organizations fighting for the independence of Tibet.
Crisis
The Crisis string was contained within the code of another malware detected by Intego in July 2012 on VirusTotal, a well-known web site. Crisis was a cross-platform Trojan and could install itself on computers running Windows and those running Mac OS X. The computer was becoming infected after the launch of malicious Java applet called AdobeFlashPlayer.jar, which had a digital signature created by using a self-signed certificate allegedly owned by VeriSign. Depending on the target platform, an installation module for Win or Mac was extracted from Java applet, saved to the disk and then run.
It is worth noting that the Crisis did not use any vulnerability exploits. This was quite strange, since the Mac version had on board a rootkit to hide files and processes, and you cannot install a rootkit without root privileges.
Many antivirus companies have different names for Crisis: Symantec uses the name given by the “author”, Kaspersky Lab calls this malware Morcut, and Dr. Web calls it DaVinci, because Crisis is part of Remote Control System DaVinci developed by Hacking Team, an Italian company. Hacking Team positioned its product as a legal spyware designed for use by governments and law enforcement agencies of different countries. Over time, the Italians rebranded it and, now, RCS is called Galileo.
A researcher of inner workings of Mac OS X known as reverser made a detailed analysis of the Crisis version for Mac and concluded that the skills of developers leave much to be desired. Despite an extensive spying functionality, this malware does not include any new ideas, it is an example of massive borrowing of third-party designs and is written in “Hindu” style. Many of its things could have been done better and more efficiently.
Reverser made another interesting observation: apparently, all detected instances of Crisis relate to 2012, despite the fact that they have been found in 2013 and 2014.
HackBack
Initially, HackBack was discovered on a MacBook of Angolan activist who attended the Freedom Forum in Oslo, a human rights conference. Ironically, one of the issues discussed at the conference was the protection against surveillance by government agencies.
The most interesting thing in the HackBack that it was signed by Apple Developer ID, a certificate issued by Apple to a certain Rajinder Kumar. For that reason, the second name of HackBack is KitM (Kumar in the Mac).
HackBack was used for directed attacks from December 2012 to February 2013 and was distributed through phishing e-mails with ZIP archives. HackBack installers hidden in these archives were Mach-O executable files, whose icons have been replaced with icons of images, videos, PDF and Microsoft Word documents.
Main functionality: collecting files found on computer, creating screenshots, compressing them into a ZIP archive and uploading to remote server.
Clapzok.A
The first real virus for Mac (and not only for it) was detected in 2013. It was a conceptual design illustrating the possibility of infecting Windows, Linux and Mac platforms. Based on the source code developed in 2006 by a certain JPanic, this malware had a jawbreaking name CAPZLOQ TEKNIQ v1.0. So we can say that Clapzok.A is the version number two. It was written in Assembler language.
The spread of this virus is limited by many factors. First of all, it infects only the files with 32-bit architecture. In addition, many files are digitally signed, so there is no point in infecting them, because the security system of OS X will simply not allow to launch such a file.
These Days
In general, we are seeing the emergence of the following trends: use of Java and Adobe Flash vulnerabilities for installation, code signing, and wide distribution of spyware used for targeted attacks on users of Apple products.
In 2014, the number of new families of malicious programs for Mac has become almost the same as their total number for all previous years.
Appetite
This malware represents interest because of all the media fuss about it. Its media-hyped name is Careto (meaning “mask” in Spanish) or The Mask. In 2014, Kaspersky Lab has published a report on yet another advanced cyber campaign. The advanced features of this campaign included the use of malicious programs for different platforms, including Windows, Linux, and OS X. The modules targeting Windows were called dinner.jpg, waiter.jpg, chef.jpg, hence the name – the Appetite.
The report released by Kaspersky Lab, which is still available only in English, describes in detail the components of Windows. However, the description of the Mac version raises some questions.
One of Careto’s components was a backdoor based on an open source clone of a netcat tool called Backdoor Shadowinteger’s (SDB), which was developed as far back as in 2004.
The dropper infected the system after the user clicked on a link in a phishing e-mail, which forwarded the request to exploit pack. In particular, it used the vulnerabilities of Java (CVE-2011-3544) and Adobe Flash (CVE-2012-0773). The dropper file was called banner.jpg, but this was an executable Mach-O file.
The dropper performed the following actions:
- Copying Safari, the system browser, to /Applications/.DS_Store.app;
- Extracting and unpacking (bzip2) SDB as /Applications/.DS_Store.app/Contents/MacOS/Update;
- Modifying /Applications/.DS_Store.app/Contents/Info.plist so that it points to SDB;
- Extracting from itself the file
Library/LaunchAgents/com.apple.launchport.plistto ensure the startup.
SDB communicated with the remote server on port 443 and used AES encryption. The three detected C&C servers included itunes212.appleupdt.com, itunes214.appleupdt.com, itunes311.appleupdt.com.
It is interesting to note that Kaspersky Lab did not provide the dropper banner.jpg with MD5 02e75580f15826d20fffb43b1a50344c for information security community. In fact, it is not available in the VirusTotal database. There is SDB backdoor (Trend Micro described it in its note about the traffic encryption algorithm), but not the dropper.
It looks that again this was just a PR campaign. The hackers have taken a third-party code and used some rather old exploits (although, at the time of their use, they could have been not so old). By the way, the exploit for Adobe Flash (CVE-2012-0773) has an interesting origin. By the way, the exploit for Adobe Flash (CVE-2012-0773) has an interesting origin. Incidentally, Hacking Team also used this exploit.
What is the overall verdict? Careto is simply an order, which some people try to present as yet another mega cool design.
iWorm
Oddly enough, this is actually a Trojan and not a worm. It was detected by Doctor Web in September 2014.
The dropper creates a directory /Library/Application Support/JavaW and, in this directory, a malicious file named JavaW. It also creates a config file named %pw_dir%/.JavaW and a file /Library/LaunchDaemons/com.JavaW.plist for startup.
The dropper uses reddit.com, a web site, to obtain the addresses of its command and control servers. First, it computes the current day value by using the formula cur_day = year_day + 365 * year. The obtained value is used to calculate MD5 hash, in which the values of first 8 bytes are used to generate a request such as https://www.reddit.com/search?q=<MD5_hash_first_8_bytes>.
After establishing connection with command and control server, the Trojan shares with it a special set of data that allow to authenticate the remote host by using a number of calculations. The sent data are encrypted with AES-256.
The Trojan contains a built-in interpreter of Lua, a scripting language. This feature allows an attacker to expand the functionality of the Trojan when needed by downloading and executing the scripts developed for specific tasks.
The set of basic commands for the backdoor allows you to perform the following operations:
- Getting the type of operating system;
- Getting the version of the bot;
- Getting UID of the bot;
- Sending GET request;
- Downloading a file;
- Opening socket for incoming connection with the subsequent execution of incoming commands;
- Relaying traffic when the data received on one socket is sent without any changes to other socket;
- Executing a system command;
- Executing nested Lua script.
The binary code of the Trojan is packed by using UPX and written in C++, which led the researchers to conclusion that the developer most like used to write the code for Linux because the majority of Mac programs are written in Objective-C.
The scale of infection extends to about 18 thousand computers. I was somewhat perplexed that, in their description, the employees of Doctor Web didn’t bother to mention the infection vector, even though the word “worm” is included in the name of the Trojan. We will fill this gap. There was no self-replication mechanism, the Trojan was distributed in a rather trivial way by infecting popular distribution packages and uploading them to The Pirate Bay, a torrent tracker. This is why the users were not alarmed when they were prompted to enter the administrator password. By the way, the information on infection method was obtained by the owner of The Safe Mac (thesafemac.com) through e-mail from an anonymous sender.
XSLCmd
Another example of malware used in APT attacks. Its Mac version was detected in August 2014. This is a ported version of similarly-named reverse shell for Windows that was used for attacks since 2009. XSLCmd for OS X has two additional features that are not found in the versions for Windows, such as capturing keystrokes and making screen shots.
The authorship is attributed to cyber group called GREF, because they usually tried to use Google Analytics code to embed scripts redirecting to exploit pack. The members of GREF don’t like attacks with phishing e-mails and prefer the Watering Hole technique, i. e. hacking web sites popular among people who work in certain industries and embedding malicious JavaScript files in the pages of these web sites.
GREF has a rather diverse set of targets ranging from Pentagon contractors to electronics and engineering companies, as well as foundations and non-governmental organizations, particularly those with interests in Asia. This group often uses the following IPs for its command and control servers: 210.211.31.x (China Virtual Telecom, Hong Kong), 180.149.252.x (Asia Datacenter, Hong Kong) and 120.50.47.x (Qala, Singapore), which raises some suspicions about the Chinese involvement.
Ventir
A backdoor for Mac with two key loggers on board. Why two? If there were no root privileges, a file named EventMonitor would be saved from \_keylog section in the data area of dropper. The implementation of this file used API functions of Carbon Event Manager. It should be noted that this method does not always work correctly. For example, for the currently latest version OSX 10.10, it can log only the strokes of modifier keys (Ctrl, Alt, Shift, etc.) and that’s all because this interface is considered as obsolete.
If there were root privileges, an archive named kext_tar would be saved to the disk from the section \_kext.tar, and the following files would be extracted from the archive:
updated.kext– kernel driver that captures the user’s key strokes;Keymap.plist– a map matching the codes of key strokes to their values;EventMonitor– an agent that interacts with the driver and logs key strokes.
The second key logger is based on LogKext, an open source project available on GitHub. The driver was loaded into the kernel by using kextload, a standard utility in OS X.
All files of the malicious program were saved to /Library/.local for the root user or to ~/Library/.local for the ordinary user (~ is the path to the current user’s home directory). The backdoor had nothing special. Here is a list of its supported commands:
- reboot – restart the computer;
- restart – restart the backdoor;
- uninstall – uninstall the backdoor from the system;
- down exec – update the backdoor from C&C server;
- down config – update config file;
- upload config – send config file to C&C server;
- executeCMD:[option] – execute command specified in the option by using
popen(cmd, "r"), send the command’s output to C&C server; - executeSYS:[option] – execute command specified in the option by using
system(cmd); - executePATH:[option] – run file from
Library/.local/, file name is specified in the option; - uploadfrompath:[option] – upload file with the name specified in the option from
Library/.local/to C&C server; - downfile:[option] – download file with the name specified in the option from C&C server and save it to the path specified in the option.
As you can see, the key logger worked independently of the backdoor, it saved the log to Library/local/.logfile, which the attackers could upload to their C&C server with a command.
As already mentioned, the method based on using a driver is much more versatile and reliable, but it requires root privileges. Probably, the authors thought that working with root privileges would be the primary mode of operation for their Trojan. It is possible that the dropper was introduced to the computer through a parent application that could use exploits to escalate privileges. Unfortunately, the mechanisms used for distributing Ventir so far remain unknown.
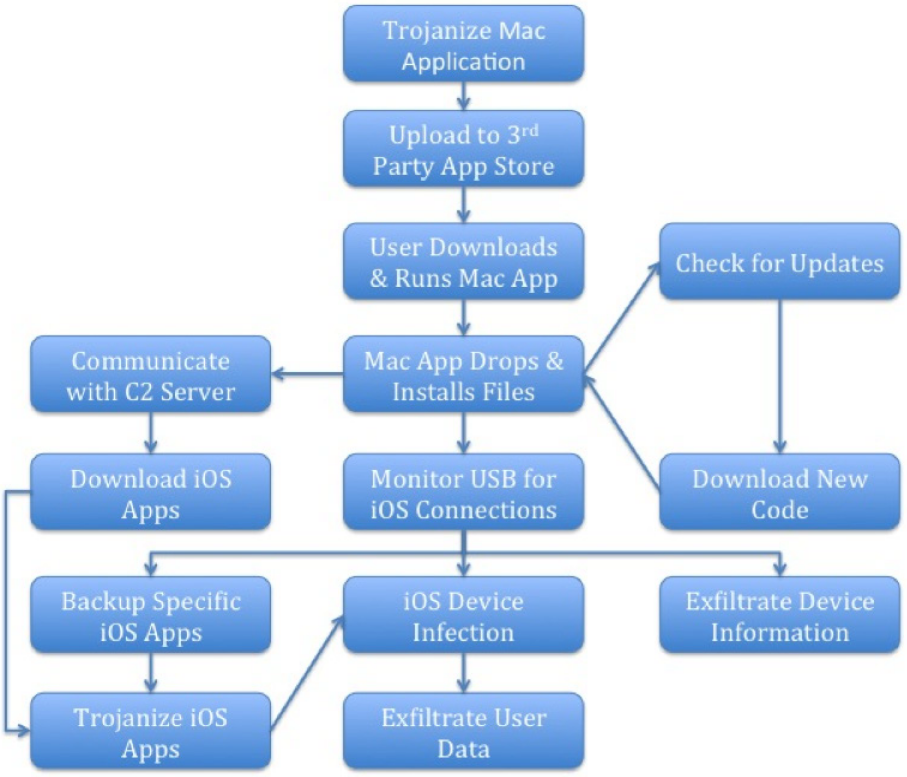
Wirelurker
Has many epithets, including the one describing it as a representative of “new era in malware”. Detected and studied in detail by specialists from Palo Alto Networks. Brief description: Among all known malware families for Mac based on Trojans embedded in installers, it made the largest number of infections; it can infect iOS devices, even those that have not been jailbroken.
To infect with Wirelurker, the attackers used Maiyadi App Store, a third-party Chinese application directory. It hosted 467 apps with embedded Trojan. These apps have been downloaded 356,104 times. So the Trojan was probably installed on hundreds of thousands of computers and mobile devices. The first reports of suspicious activity surfaced in June 2014. Most of infected apps were the games.
The operation algorithm is shown in the Figure. As you can see, a process of Wirelurker continuously monitored USB connections to the infected computer. To infect iOS devices, this malware used a vulnerability called Masque.
Overall, there were three versions of Wirelurker. Wirelurker.A was embedded in installers. It began to spread on April 30, 2014. A week later, on April 7, Wirelurker.B began to spread from command and control servers. Since August 2014, C&C servers started to distribute Wirelurker.C. Main differences between the versions:
- Version
Adid not infect iOS devices and communicated with C&C servers inplainmode; - Version
Binfected jailbroken iOS devices and also communicated with C&C servers inplainmode; - version
Cinfected both jailbroken and not jailbroken iOS devices and communicated with C&C servers by using DES encryption.
The latest version introduced two methods of infecting iOS devices. First, Wirelurker determined the jailbreak status by checking AFC2 (com.apple.afc2), an iOS service which is the standard interface for jailbreak tools. If AFC2 was available, a file named sfbase. dylib was downloaded to the mobile device.
Also, the following operations were performed from jailbroken devices:
- Read information on installed apps;
- Use the list of installed apps to search for applications with such IDs as
com.meitu.mtxx(posting photos from Meitu), com.taobao.taobao4iphone (client of Taobao, an eBay analog in China), (client of Alipay, a PayPal analog in China); - If the search was successful, the app would be downloaded to computer, and the information about would be stored in a local SQLite database;
- The downloaded app was unpacked and modified;
- The modified app with embedded malicious code was uploaded back to iOS device.
A different method was used for devices that had not been jailbroken: An app signed with an enterprise certificate was downloaded to computer, such certificates are issued by Apple to companies for signing their enterprise applications. Usually, it is not difficult to get such certificate, a fact that is actively used by the hackers.
The malicious file named sfbase.dylib was the main backdoor that communicated with C&C servers. In particular, the data from the address book and SMS texts were sent to command and control server.
The information about the device was sent the main module of Wirelurker. This information included the following details:
- Serial number;
- Phone number;
- Phone model;
- Apple ID;
- Wi-Fi address;
- Information on memory usage.
The apps with embedded Trojan sent their name and serial number to C&C servers, which allowed attackers to monitor the process of infecting the mobile devices.
By the way, the developers have been arrested shortly after their misdeeds. According to Beijing Municipal Bureau of Public Security, in late fall, Chinese police apprehended three alleged developers and distributors of Wirelurker. The investigators released only the last names of suspects – Wang, Lee and Chen. Qihoo 360 Technology, a Chinese antivirus company, has greatly contributed to catching these hackers.
Conclusion
The entire year of 2014 was particularly “fruitful” in terms of new malicious programs for Mac. We can highlight the following characteristics of the current period in the development of malware for Apple:
- Malware developers are becoming more experienced and their projects are becoming more technologically advanced;
- Most of malware is after obtaining personal information, there are no banking Trojans yet;
- The vast majority of families are designed for APT attacks, which means that developers are backed by people with a lot of money;
- A very large number of known specimens are of Chinese origin;
- Developers often use third-party code by modifying it for their own needs;
- There is a trend toward writing hybrids capable of infecting mobile devices.
All this, along with bizarre policies of Apple, which in March has removed several antivirus apps from its App Store, and peculiar obstinacy displayed by some fans of Apple products insisting that “we have no malware,” makes me to suspect that this is only the beginning. I agree that the security model for Mac and iOS is more elaborate than, for example, the one for Windows. But this does not negate the fact that there is no such thing as absolute protection. Any attempt to pretend that there are no problems will lead to nothing good. In any case, the users should constantly bear in mind that security of their information is in their own hands.
Masque Vulnerability
In November 2014, FireEye, a company, published a report about a vulnerability in iOS that was named MARKDOWN_HASH8ea06fd0586fc49809a25baf9f263015MARKDOWN_HASH. This vulnerability allows to install a malicious application over an existing app, and this new app will gain access to all files of the previous application. For a successful attack, the malicious app must have the same MARKDOWN_HASH0213dc6073adc459a29af09fe99b9d79MARKDOWN_HASH, and also have the attribute MARKDOWN_HASH85489b52b4a47d2014e94d9711baa89fMARKDOWN_HASH, as well as be signed by a digital certificate issued by Apple. The vulnerability can be exploited only against third-party applications, i.e. it would not work against Safari, a built-in iOS browser. By substituting the apps, the attackers can gain access to the data of the application that they are interested in. For example, they can substitute Gmail client and gain access to e-mails and the address book. All these manipulations can be made with devices that have not been jailbroken.