60+ Gift Ideas for Hackers: Best Geeky Gadgets for Friends and Yourself
Date: 31/08/2025

Date: 31/08/2025

📟 News
Date: 30/08/2025

By posting fake projects on popular developer platforms (GitHub and GitLab), attackers trick users into executing malicious payloads that fetch additional components from a hacker-controlled repository. As a result, remote access trojans and spyware are downloaded onto victims’ devices.
Read full article →📟 News
Date: 30/08/2025

Jon von Tetzchner, head of the Norwegian company Vivaldi Technologies, which develops the browser of the same name, shared his thoughts on integrating AI into browsers. In von Tetzchner’s view, the industry’s attempts to merge AI models with web browsing have gone too far.
Read full article →Date: 30/08/2025
📟 News
Date: 30/08/2025
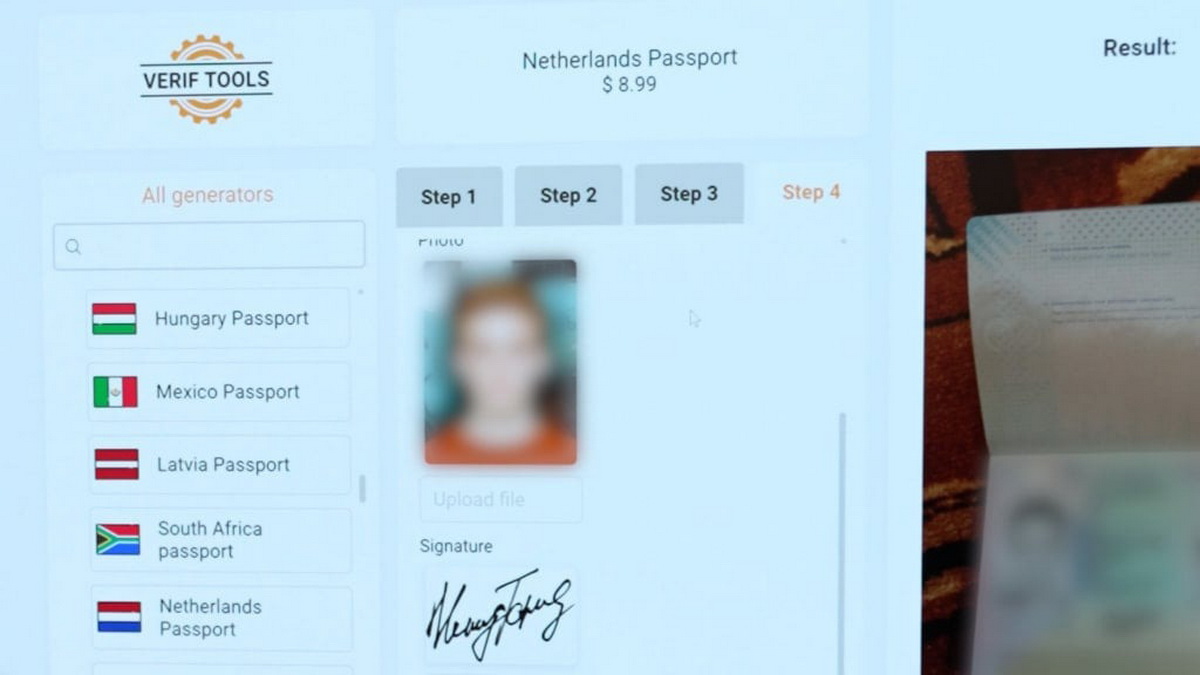
The FBI and Dutch police report the shutdown of the VerifTools marketplace, which specialized in creating fraudulent documents. Law enforcement seized the service’s servers located in Amsterdam.
Read full article →📟 News
Date: 30/08/2025

The maintainers of NX warned users about a supply chain attack dubbed s1ngularity that occurred on August 26, 2025. The compromise of one developer’s token allowed the attackers to publish malicious versions of the popular npm package and other tools, and then steal user data.
Read full article →Date: 30/08/2025