
Our goal is to collect a kind of carry-on criminalistic handbag that would be available to general public as long as be compact, obtainable and legal.
So, all the gadgets in out kit are supposed to correspond to further parameters:
- Legality
Which means an absolute legitimacy in terms of purchase, transportation, and storage of gadgets. The usage stands slightly isolated, because, for example, we can use certain devices absolutely legally anywhere, while the usage of some other ones in terms of special institutions, or against certain individuals, and moreover, for personal purposes could end up with administrative or criminal responsibility. - Cheapness
Quite important parameter. As a rule, we can get anything, it is always just the matter of price. Well, the devices that we are going to review in the article have quite moderate price range available for most people. - Accessibility
Anyone could find all the components with little effort, which is to say except those that are designed for certain certified organisations, legal persons, furthermore, except those gadgets and devices that could be distributed only on designated area. - Easy handling
In my opinion, this is one of the most important parameters. That means that anyone could use a gadgets after briefing. - Portability
Here, everything is obvious: small size, light weight in order to ergonomic placement in our criminalistic handbag or organizer, as long as workability. - Portability
That means the gadget could work off-line or urges for minimum requirements and little dependence on other devices. For example it could work on different software, in case if it is supposed to be connected to a computer or smartphone.
Detecting beetles and spy cams
Searching for spy cams
In older times the ‘red’ eyes were the real bum for snappers. Today almost every photo camera has the build-in function dealing automatically with this photo defect. However, today the nature of this nuisance is used to detect a spy camera. According to encyclopegy the ‘ red-eye effect’ appears as a result of the strong flash’s light flux reflection from the human eye ground. Its membrane is rich for blood vessels, is red and in terms of bright flash become well-visible. So, any photo or video camera lens have similar properties. In fact, if we direct a flash light on the spy cam lens then it will be reflected and all we will need to do is to detect this light. Maybe it sounds quite complicated but, generally, it is not, moreover, anyone could build up such an elementary device for task performance. Well, we are not going to invent a bicycle and will consider the СС308+ pocket device that is quite good not only in detecting of spy cams but also GSM, WI-FI and other things, but this we will be discussing a bit later.

Fig 1. CC308+ detector
By and large, the operating peculiarities are quite simple: it shed light by means of six red Leds on the founding environment and, if there is a spy cam lens the light is reflected. If we look at the reflection through a special colour filter ( in our case it is a simple red semi-transparent plastic) we will be able to see it. Moreover, if we repeat the flashes with a certain latitude we will easily recognise the specific blinking of the spy cam lens. Although the method is far to simple it works in 100 % of cases detecting spy cams no matter whether they are turned on or off. If they have a lens they will be found. Remarkably, that this method is used in military technology, in particular, in terms of computer vision when it is necessary to distinguish and follow the potential target by means of different emissions ( infrared, acoustic or radio signal).
Anyway, let’s back to our device. If you buy this Chinese industrial miracle via internet it will coast you about 16$ including free home delivery within a month. On CIS site it costs around 100$, so if you are not deprived of entrepreneurial skills, go for it. It has the same size as an average mobile phone, made of black rubber plastic, that is, actually, quite nice on the touch. Also it has an expandable antenna for better detection of wireless networks, besides it has red semi-transparent plastic spy-hole, six red Leds, the turn on button which is simultaneously a manner mode switcher , audio-exit for headphones, the button that turn on the Leds’ blinking and useless compass. It is not difficult to use the device: after you turned the Leds on, you should look through the spy-hole, directing the emission toward the places we are interested in. If there is a spycam we will see through the spy-hole the notable red and white spot reflected from its lens, furthermore, the closer we will stand to it the more visible will be the reflection. As an example, here we show the detection of a spy cam inbuilt in simple pen (image2).

Also, the visible angle is very important, the reflection will be more recognisable in terms of the right angle rather then oblique one.
Beetles
As we mentioned above the gadget is equipped with the antenna that detects the radio-frequency signals. If there are no difficulties with spycams then, in terms of beetles there are certain nuances. As long as the device fall into pocket gadgets category, it is able to detect only strong radio signals, like, Wi-Fi, GSM or radiophone. By and large, it is more then enough regarding the detection of GSM loads. There are two working modes: usual and soundless. Using first mode, we can understand the signal power by means of Leds blinking and vibration, while using the second mode we consider the sound intensity along with Leds.
Also we can use the device as a gatekeeper to detect active wiretapping. We need to put the device near a smartphone and turn on, If we see the relevant LEDs blinking or sound, then, consequently, if we are not calling anywhere we can think about unauthorised activation, or simply about wiretapping.
Conclusion
Despite all the advantages, the device is made quite bad and biased to brake. For example, after a month of exploitation the lithium battery inside the case unglued, so I needed to dismantle the device and to glue it back.

After this not really sophisticated fix I did not face any other problems. On the other hand, the simplicity of the construction allows to examine and ‘update’ it easily. Particularly, further we are going to regard how to make an acoustic safe that could run together with the device. Generally, the device run smoothly, it is portable and the battery retain the charge quite good. My opinion is that the purchase is reasonable, the device is compact, cheap, good in terms of spycams detecting. Nonetheless, if you have couple hundreds spare dollars and the genuine interest in the subject you could buy something more interesting from the professional equipment.
Spy cams
The name of the device is supposed that the camera or other devices are used when the target object do not know that he is being recorded. On the one hand it is obvious, however, on the other hand there is one nuance. In fact, we can legally place the camera in our window and record the people passing by, but if we put it in our pocket and go to visit somebody then it will fall under administrative responsibility. Consequently, the cameras that was designed for spying are illegal to use by ordinary people. So, let’s figure out, legally speaking, which cameras are considered as spycams and which are not.
So, if a camera do not indicate the record by light or sound it could be considered as a spy one. We can draw a parallel between the cold guns and simple knifes, when regarding the lack of one of parameters, like lack of handguard or the whittle down blade tip, in fact, could set a combat knife equal to a touristic one. By and large, it is partly explains why do cameras manufactories make a shot shutter sound. However, nowadays it became possible to turn the sound off by means of certain applications. Further, you will find a list of popular spy cams that you can find in the internet shops.
MD80
Small portable camera, that is juridically marked as a video recorder. The device is no bigger then an AAA battery which allows to hide it in the interior, moreover, it is packed with several types of fittings.
Besides, there is a special silicon cover in case of bad weather if we need to install the camera outside. Also, the device fitted with a sound detector, which is quite convenient and save your time, because you simply do not need to watch the ‘empty’ videos. Experience has shown that the detector reacts very good on voice, footsteps over two meters distance, furthermore, it reacts very good on the enter-phone door opening. The general use that I have found for the device is the role of gatekeeper or watch man. By placing the camera in the certain room we can figure out who and when came and whether there were any suspicious persons. I left the camera in a holding mode for approximately a day, never was recording something for a long time, however, I suppose that in the active mode it will work for about an hour or two. The time could be prolongated if you connect the device to an additional battery using USB-connecter, also it could be used along with two AA batteries and an extension bar for the mini USB. The recording is indicated with the light, however, it could be covered with the black electrical tape. Generally, it seems that the camera is pretty good and the quality of the recording is not bad as well. I suppose that the major advantages of the camera are the price ( about 6$), portability, sound detecter and the possibility of using the additional power source.
Pen – camera
The camera looks like a respectable business-pen and has all the parameters of such object. For example, I like very much to write with it :). It coasts about 5$, has a camera on the top part and the indicators that are almost invisible on the other side.
Legally speaking, the pen indicates recording, so it could not be classified as a spy one. It has a small button on the top. If you press and hold it the record starts, if you make two short presses it makes a photo. Inside there is a micro-SD slot, as long as a computer jack. The record quality is quite good, it could not make a panorama shot but could make a photo of the object you are interested in details. I guess this device is supposed to be at hand, like, for example on your workplace. In case of appearance of an ‘interesting’ or ‘very friendly’ visiter you would have the possibility to record him just in case. Also, the pen could be placed on the breast pocket of a jacket or shirt and be used for recording as well.
Conclusion
A lot of people buy such cameras to protect themselves. By and large, I consider this approach is right, of coarse, we should use them rationally and do not go to extremes. Moreover, any video even with a bad quality is much more forcible argument rather then an audio, considering the fact that we have to conduct a supplementary expert examination to prove that the voices on the record belong to the people involved. However, you should bear in mind that regarding authentication you are supposed to provide the device that was used for video recording. That is why if you decide to brake Led or dynamic ( that actually make your camera a spy one legally speaking) then this could carry consequences.
Autopsy shows. Lockpicking
Since on the several hacker’s conferences appeared stands about lockpicking, the subject became the concern of a lot of people and, consequently, we faced a number of articles consecrated to different methods of locks opening. Today I am not going to repeat all of them, my task is to focus on the picklocks, as long as practical aspects of their usage.
Picklocks
I took interest in lockpicking after the acute need of opening a 5-pin lock in the spirit of the best spy movies, i was using a piece of wire that I had found in the street. I would not talk big and assure that it was noiseless lapidary breaking up, as we see it in movies, more likely, it was forceful rape of the lock by a person with Parkinson disease. So, It was starting to hit the fun. Along with first experience I understood that the large majority of locks are just the illusion of safety. Nevertheless, the access control of a room is one of the key elements, and specifically, of the info security, that, actually, mentioned in corresponding international standard ISO 27001. After some time I decided to make several simple handmade picklocks. I was using minimum amount of tools and resources. As a base for the picklock I took a steel wire, that was slightly flattened with hammer and then filed down. For handle I used an aluminium wire that I just braided around the steel wire. Well, it was pretty awkward, however, using it I was able to open couple soviet padlocks that were gathering dust. After the experience I realised that the lockpicking is the game of skills and tools. Later I ordered a Chinese kit of picklocks via internet that costed me about 30$ ( image 6).

I am satisfied with the kit, the picklocks showed a good quality, they are neither heavy, neither light, moreover they are firm and do not bend. If you want to buy the picklocks just in case, as well, I would not limited myself with two-three simple picklocks and buy the whole kit. The case is that they do not take a lot of space and if it is necessary you could always take several from there. Some authors advise to use picklocks in the form of a cross-functional ‘pencil’, the body of which represents a container for the threaded nozzles. Nonetheless, initially, it could seems quite convenient, but I suppose that it is not really practical in terms of usage. The case is, that when you are dealing with lockpicking you need to alternate picklocks from time to time, so, if you use the ‘pencil’ you will need to change nozzles with one hand which is ineffective and inconvenient. It is much better to have all the picklocks well-arranged so you do not need to get distracted by irrelevant operations.
Pickgun
The readers interested in lockpicking should know a pickgun ( image 7), as long as the break-in method based on bumping. The core idea of the method is to use inertness along with the bump by all the pins.

Fig. 7. Pickgun
We can find a lot of spectacular videos on Youtube regarding the using of a pickgun, moreover, there are always plenty of spokespersons on the special conferences praising this gadget, however, in my practice everything appeared to be not that bright and happy. And it is all about details. First of all, the locks could be installed differently: like, in America and certain European countries locks are usually installed with the base on top, while in the other European and CIS countries locks are installed with the base underneath. Thus, a pickgun could be meant only for one type of locks. There are a lot of sites in the internet where you can order a pickgun, anyway, be careful, because most of them are designed for american lock style. Of coarse, you can turn it upside down for the other lock type, but it is not really convenient and , also, quite difficult to maintain the right position. Second, each pickgun has its own shock rating that is supposed to be adjusted regarding the certain lock type. In case if you are a beginner it could be quite complicated task to do. Like, a too small amplitude produce too weak bump so the pins will just take the right position, however, if the amplitude will be too strong then the pickgun will be twitching and move out of position, so it would be impossible to make a synchronistic impact with pins. Third, if you adjust the amplitude incorrectly, or put the pickgun in a lock bumpily, or the nozzles are of bad quality then you could brake them down. Luckily, I has not faced this problem yet, but there are plenty of people who did. Furthermore, I would like to mention that the whack is quite loud and unpleasant. So, think about all this, I just mention that I bought my pickgun for approximately 25$.
Thievish comb
Strangely, but I have not seen anywhere the mentions regarding another picklock type, that popularly called ‘thievish comb’ ( image 8).

Fig. 8. Thievish comb
Its operating peculiarities differ from the traditional picklosk’s ones. If the previous picklocks set pins just like a key do, then the thievish comb just press them through a the lock base. They have been called ‘combs’ because of the shape. I must say that it is hellish thing, although it has one disadvantage. The case is that it is made individually for each lock type. On the one hand that implements certain restrictions, on the other hand if the lock could be opened with certain ‘thievish comb’ , then we can brake it within few seconds. Moreover, this kind of picklock is kind of cross-function skeleton key, and if there are locks of the same type in a building that could be opened with such picklock then things are not so good. By and large, it is quite easy as to buy them, so to make it by ourselves. You can buy a full kit for about 17$, but it is quite commen situation that picklocks need to be adjusted a bit for certain locks ( image 9).
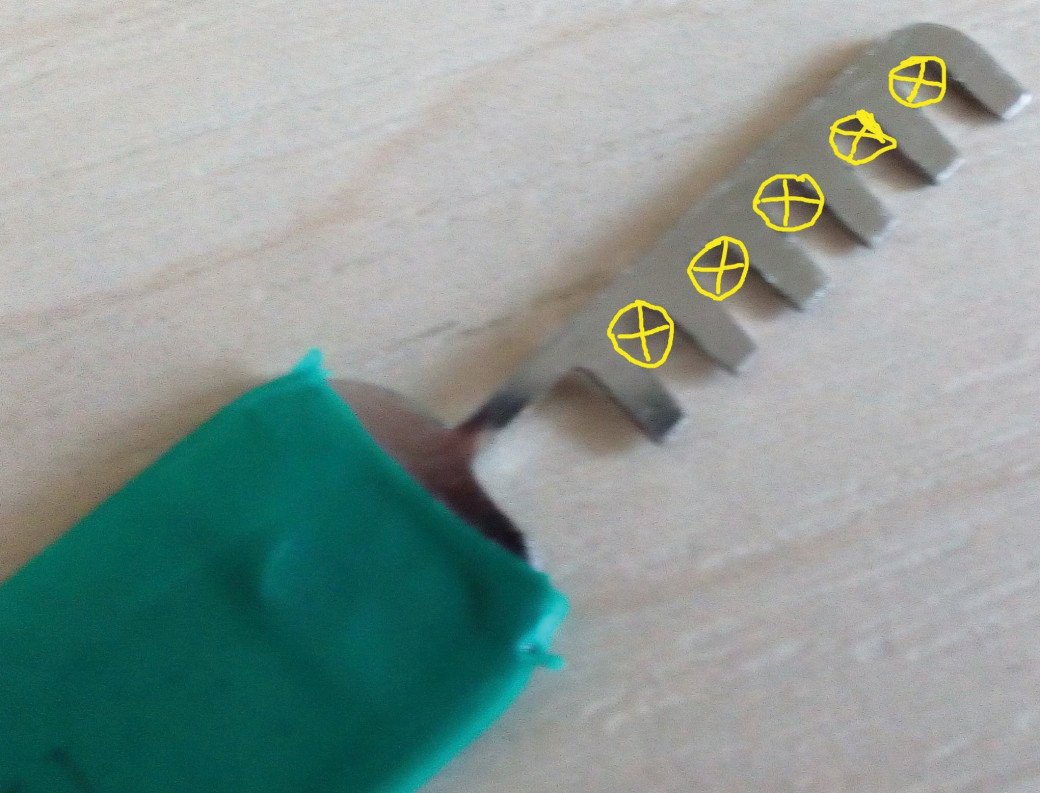
Fig. 9. Adjusted Thievish comb
For example, in certain combs that i bought i had to file down the gutters so they could go below and push the pins till the necessary depth.
Bump key made out of simple one
I guess everybody heard about bump keys – you can buy one or make it out of the one you have. It is quite firm and, moreover, a zero-fault device, that has only one disadvantage – each bump key is unique and made for a certain lock. However, sometimes, the situation could be even more simple, i mean, for example, the situation when you need to open a lock with the key similar to original one, or with a similar to bump-key shape. We can find dozens of such examples. Here is the good one – the personal locker in a gym, or another simple locks that have 4-5 pins as a rule. Usually, the locks in such organisations are similar and it is quite possible to open another person’s locker using your key. The thing is to use your key as a bump-one. All you need to do is to put the key inside the lock by halves and then dart it till the end rotating like for opening. The funny thing that the process does not look suspicious because it seems that the owner just trying to open the lock that stuck. Often you can see the inscription “ The organisation will not be liable for the stuff left in lockers”…
Duplicate key
This subject is a bit separated from lockpicking, however, I would not avoid it. The case is that it is very bad idea to give your key to somebody or leave it unattended. Anyone could take it and make a duplicate. Nonetheless, if a person is in the picture, all he need to make a copy of a simple tooth key are a piece of metal from a soda can, a marker and a scissors. We need to affix the key to a metal and delineate it with a marker, then cut it out and pierce grooves just like on the original key. Done. If we give our’s best we could do everything within a minute. Then if we put the fake key in the lock and rotate it will bend, however, its major purpose is to adjust the pins in the necessary position just like the original key does, after what, we can, actually, open the lock by means of simple flat tip screw or possessor. In certain cases we need to move the key from side to side in order to place it correctly. If we have time we can make several similar copies and glue them together so we would have almost the original key, however that could be absolutely unnecessary. That is why most hotels use exchangeable plastic cards instead of keys, and change these pass keys before each guest check-in. It seems more secure, but, anyway, the plastic card could not be a security standard, however, it would be a bit more difficult to copy it.
Conclusion
By and large we can open most of the ‘daily living’ locks using the picklocks we have discussed above, that is why it is fair enough to include them to the our usual. Furthermore, they are quite cheap and portable. As for me , I keep them in a glasses’s case.

Fig. 10. Picklock kit
Handmade acoustic safe, or why to pay more?
Like i promised, now we are going talk about how to make a handmade acoustic safe by means of small adjustments. If you have not heard about such devices, I will describe them briefly, the purpose of the gadget is to create acoustic interferences or noise in order to suppress a wiretaps. The peculiarity is that such devices does not really obstruct bugging, however, because of the acoustic interference it is impossible to emphasise anything efficient out of tapped information. This principle is very effective against a passive bugging, that claim momentum along with the growth of number of smartphones. For example, you can install a spyware on your smartphone, that activates dictaphone but sent the record later, after a particular time or after a command from outside. It is impossible to nick up this bugging right away unlike the active one, that sending audio along with recording. For example, when someone secretly activate a phone, it make a noteless call and deliver everything that is heard through the microphone. That is why the effective way to counter work to passive bugging is to isolate the insecure device from the conversation zone or to create a permanent acoustic obstructiveness. Carry on the subject, we could mention different types of the acoustic safes. The could differ by size: the portable ones, as a rule, are used for mobile phones, web-cams microphones and in laptop integrated microphones; bigger ones could consist of several modules, that allow to create obstruction in a whole room. Also they have different activation modes: some launches obstructions permanently, others only when they detect possibly suspicious activity, for example, an illegal call out. In turn the acoustic obstructions could be different as well, it could be white noise, pink noise, speech-like acoustic obstruction and others.
By and large, we have already told enough, so, it is time to get down to business. Returning to our CC308+: it could detect a call from mobile phone, consequently, if we turn on the device and place it near the phone then we will see appropriate LED blinking our sound along the call-out. In fact, we already have part of functional for our acoustic safe, detecting a suspicious activity. Now we need to connect the module that would launch acoustic obstructions regarding the illegal device activation. Here, we could emphasise two points:
- The creation of an adapter from the device to our jamming device.
- The creation of the jamming device itself.
Let’s begin one by one. The CC308+ has an 2,5 audio connecter for headphones, which I suppose is absolutely useless, because they are similar to internal speaker. However, we will use this connecter for out jamming device. Consequently, we will need 2.5 mini jack connecter, KT816 transistor with any alphabetic notation a the end or the similar one, couple pieces of wire, preferably copper ones, not too thin. All the stuff you can buy in the shop with radio components for less than a dollar. When you will have everything all you need to do next is to solder everything circuit-wise ( image 11).
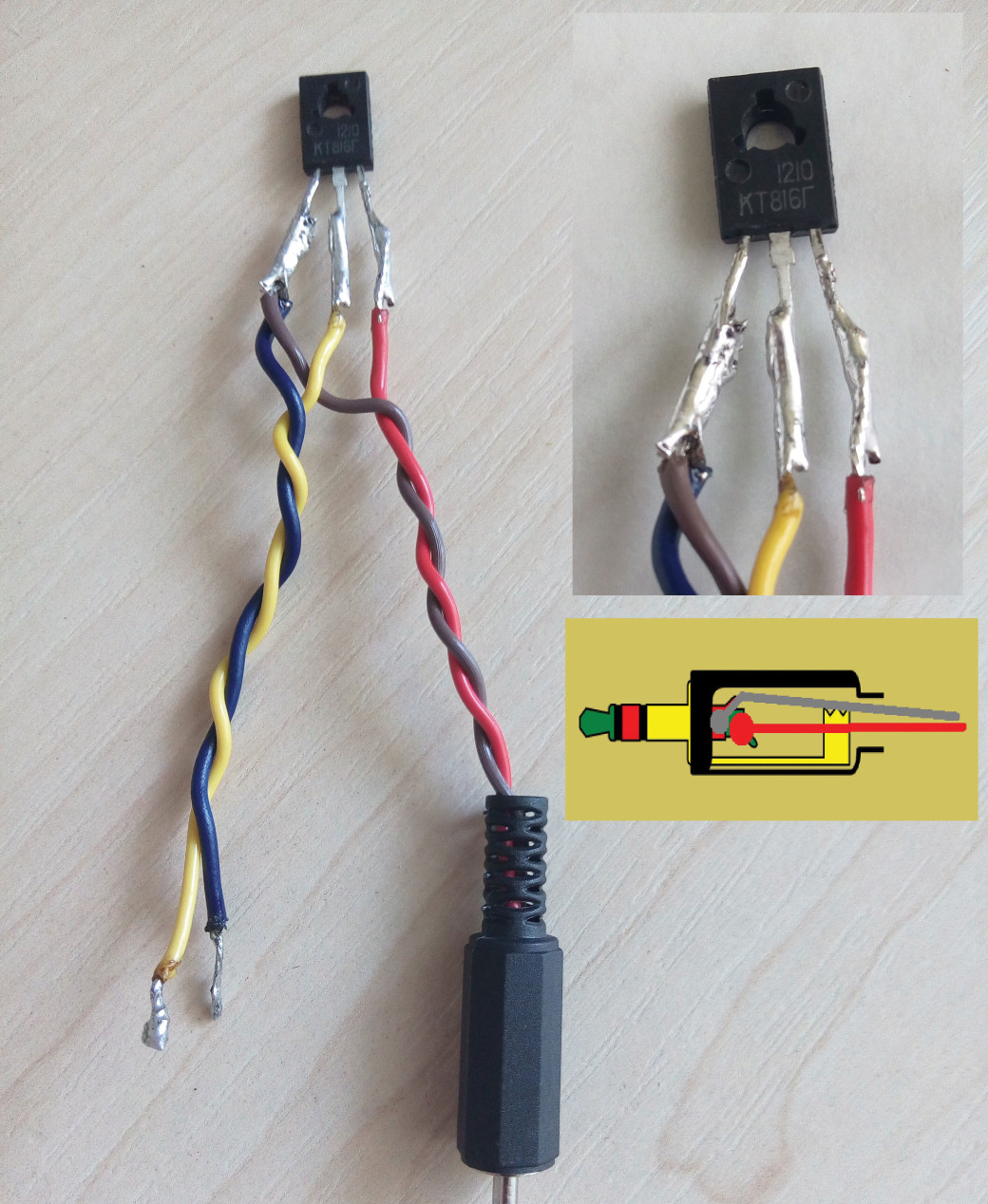
Fig. 11. Adapter connection
The circuit scheme is really complicated, I guess anyone could solder it, even if you have never kept a copper in your hands before. Verified by me and my friends. All the geniuses had time for sure to realise, for the rest I explain, when the sound will be going to the connecter ( red and grey wire) the transistor will close the circuit ( yellow and blue wire). In its turn, the yellow and blue wires will be connected to the noise maker, therethrough to turn it each time there will be a honk. Nothing too complicated.
Noise maker
When we are done with the first stage, all we need to do is to make a noise maker. At first sight it might seem difficult, but I calm you down, we are not going to solder anything, as long as will not invent a bicycle, better try to find the already made solution. In this case I was using a single recorded module for an audio-card, that is also used in toys, packages and so on. You can easily order such module via internet or buy it in an appropriate shop for about 7$.
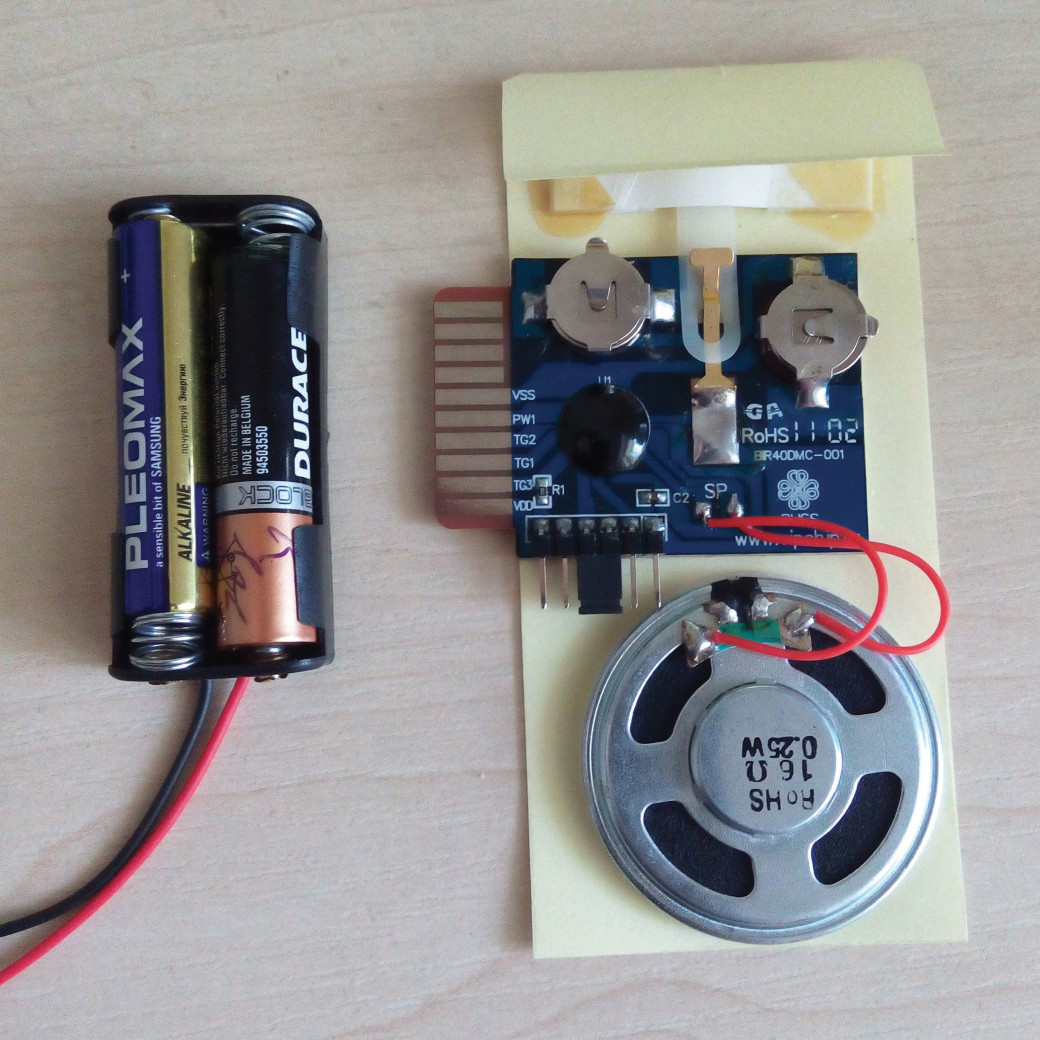
Fig. 12. Musical marker
However, there is a small nuance: the duration of the sound file is only 40 seconds and it plays only once. If we want the module to continue to make noise, we need to dead set the replay during file recording. So, we should point out the further parameter: Press and hold to play and repeat message, release to stop. Be sure that you ask the customer to do this before purchasing because you will not be able to rewrite it later. I was using the MP3 file with white noise as an acoustic obstruction, which is considered as the most effective one in terms of suppression. There is an interesting peculiarity of these modules, we can, actually, install there additional Leds, moreover, the fabricator suggests different activation sensors: motion sensors, magnetic and light sensors. In our case we do not need any additional sensors, all we need to do is to close blue and yellow wires. As we can see on the image, the vane that is used to close the pin during the opening of the card, now is close-loop, furthermore the circuit is closed on connecter. However, it could be done conversely, in other words, we can solder the wires to the pin where the vane is placed and leave the connecter unchanged. Then we connect the device using the mother СС308+ audio connecter and, ta da, the acoustic safe is collected. All we can do now is to simulate an unauthorised phone activation and enjoy the annoying white noise.

Fig. 13. The test launch of the acoustic safe
.
Well, as they say, there is more to come. The construction allows to make improvements and has a co-called backlog for realisation. For example, we can install a button that would close pins and , thus, activate an obstruction when we need it. It could be useful in terms of confidential negotiations, when all the mobile phones could be collected together along with noise maker, so, the noise background do not impede conversations. All the mobiles are just put in a small box or bag along with noise maker, moreover, the sides of a box provide additional obstruction regarding the information capturing. According to acoustic modules fabricator, the charge from two AAA batteries will be enough to play 40 seconds record for 1000 times, which is approximately equal 11 hours. I have not tried to test it for 11 hours, nonetheless, I was using for 6 hours without breaks. But why should we be limited with this? Instead of two simple batteries I decided to solder a supply unit for two AAA batteries that you can find in the shop with radio components. The further changes have more like decorative character rather than functional one. So, we can get rid of yellow and blue wires and solder the transistor pins directly to the circuit board, also we can shorter the board by cutting out the pigtail for the programming device connection, as long as we do not need it anymore, and, then, to pick up a suitable holder for the ready made scheme. You can see my example of the field acoustic safe on the image 14.
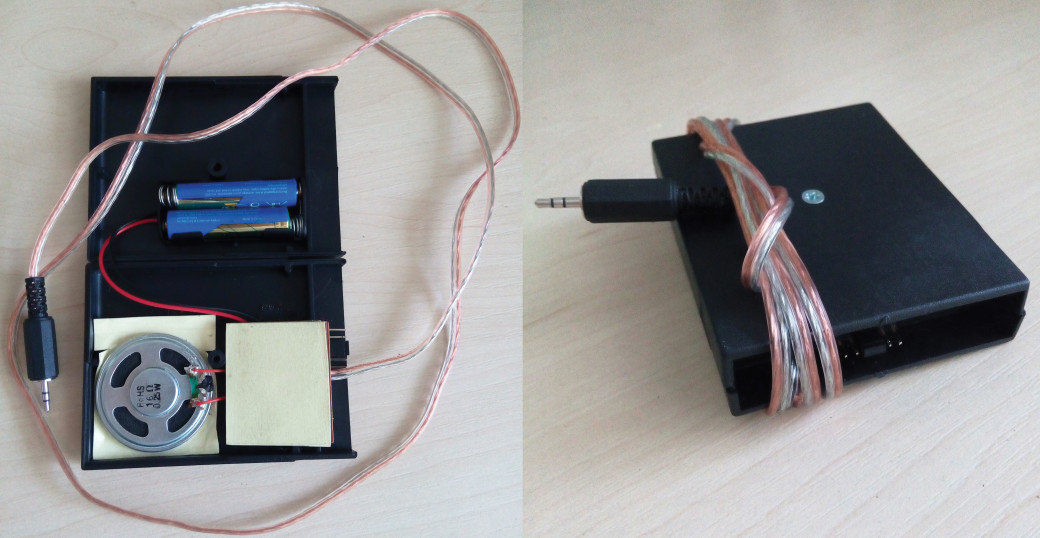
Fig. 14. Acoustic safe
As you may notice there are still plenty of space in the holder, so you can install additional battery, Leds or noise volume regulating relay. In order to produce permanent obstructions we activate the gadget by means of mother bridge that is places in the middle of the connecter, so the transistor in this particular case is installed instead the end-capping vane.
Conclusion
You may ask, why should we bother so much if we can buy a ready made acoustic safe? Well, of coarse, this is much easier, and it will cost you about 300-400$. When we made our one for couple dollars overall, which is much cheaper, however, it is as effective as the expensive one, and may be used as in a stand-alone mode, so along with other devices. Cool! Should I also mention that most of fabricators like to praise their ‘babies’ and tell that there are no analogs to them, but this is just little more than smoke and mirrors. There are no so many miracles in the world, and you always will have time to spend your money :).
RFID. To make a duplicate is not a big deal at all.
Almost all business-centres, banks, aqua-parks and sport centres use electronic access keys. But in order not to go too far away from the subject we are going to discuss the most popular and practice—oriented aspects of the RFID-keys usage.
Most of RFID-keys operate at frequency of 125 kHz. And we can use again the Chinese-made gadget for 24 dollars to make a quick duplicate ( image 15).
The interface is wickedly simple: two buttons read-write, I hope, I should not explain anything. Also it is packed with two rewritable keys made as cards and two made as keys for the enter phone door. Here is one nuance, during the writing and reading there are two short loud and very unpleasant sounds from the internal speaker. I have no idea what for it was plugged-in , I guest so it would be impossible to make secret hidden copy. I give you an advice, the problem could be solved with a copper, all you need to do is to unsolder the speaker ( a successful copy will be indicated with led signal anyway).
The device is very compact, work in a stand-alone mode from two AAA batteries and has already copied dozens keys ranging from enter-phone door keys to ticket barrier cards without any problems. However, sometimes we need to only copy a key, but figure out the key code so we could use the information later.
So, here we can use RFID-usb card for 20$. It communicates with computer by means of HID-protocol and, overall, simulates keyboard which is actually make it cross-platform. It could be used along with a smartphone or computer under Linux or Windows OS. First, we need to open a notepad or any other text editor, then take focus on the text field and after that touch to the key we need. Immediately you will see the key code on the screen. The USB card is very compact and convenient, especially when you need to copy dozens of keys. Moreover, we can try to copy a key code of the other person by connecting the device to our smartphone via special adapter. In order to do that, we need to hold the phone in a hand and hide the device in the shirt-sleeve. I guess you realise that to do so you need to come really close.
As for me, I also mentioned that most of electronic keys are static, more rarely rewritable. And as paradoxically it might seems, it is quite common situation to see the imprinted code on the card..
In fact in this case we do not even need the original key itself, all we need is to find out the key code and we can make the duplicate remotely. However. if you wind up your’s brain, you can go even further. As a rule the static RFID-keys are embedded as a package, by dozens, hundreds and thousands. And all the keys in a package have serial numbers. Consequently, if we find out the number of one of the keys we can increase or decrease the number and find out the codes of other possible keys.
The disadvantage is that we can not be 100% sure that the key will be suitable for the particular door and which priority it would have, however, from the other point of view, we could accidentally get the key of a head of security. If you have possibilities or it is necessary you can also make several dozens of possible keys. The paradox is that you can not do the same thing with the ordinary door lock.
Magnetic cards
Quite often after the discussion of RFID-cards the questions about magnetic cards appeared. By and large, I mean cards with magnetic strip, so tell a few words about them as well. All the information on the magnetic strip is written, in its turn, on the smaller strips, also called channels, that are placed in parallel. On the image 20 you can see the cheap gadget for 21$ that reads first two channels of the magnetic strip. It works on HID-protocol as well, so it is cross-platform.

Image 20. Magnetic-card reader
I bought this device just for sport, rather than because of certain intention, moreover, because of the growing tendency of the magnetic cards number and their use in the everyday life: discount cards, passes, club cards, certificates. If we get such card, we could find out a lot of useful information, like, card owner’s name, the name of an organisation, access code, date issued, birth date and so on… This information could be quite useful in terms of data collection or a pentest itself. Therethrough, we can determine the identity check mode, whether it based on the name or other common parameter, that is settled for everyone, for example, single access code.
The device is aimed only for reading, however you can buy the one for writing as well, and make a full card copy, or a slightly adjusted one with your own information. By the way, if we pass through the device an ordinary bank card we will get its number and bank account.
Conclusion
All the gadgets that we have discussed touch almost all the aspects of the modern life. I am sure that everyone can find here something interesting. Someone will be interested in lockpicking, someone in spy cams, the others in soldering and acoustic safes. More likely, you will try to make your own kit or to adjust the one you already have. Each day we see more interesting and advanced gadgets, the process is ceaseless, in the article we have just reviewed the small part of this diversity, as long as the experience of using such devices. Today the question of security has a new turn, it is just not enough nowadays to install antivirus, adjust firewall and keep calm. Today security is a complex approach that touch all the aspects of our lives. And whether we want it or not, today we do not need another miracle pill offering us another security illusion, we need new approaches, principles and behaviour. Like it was well said – the security begins with ourselves.
