Microsoft has never hidden that it collects user data; in the past, though, it relied on vague wording about sending “some information to improve the user experience.” After the General Data Protection Regulation and several other laws came into force, the company’s lawyers had to spell out the details. Here you can read what data is collected, where it’s sent, how it’s processed, and under what circumstances it’s disclosed.
To placate consumers, Microsoft claimed to let you configure the type and amount of data being sent. To do this, install the update package (for builds below 15063.0) and use the Privacy settings screen. Ideally, do this during setup.
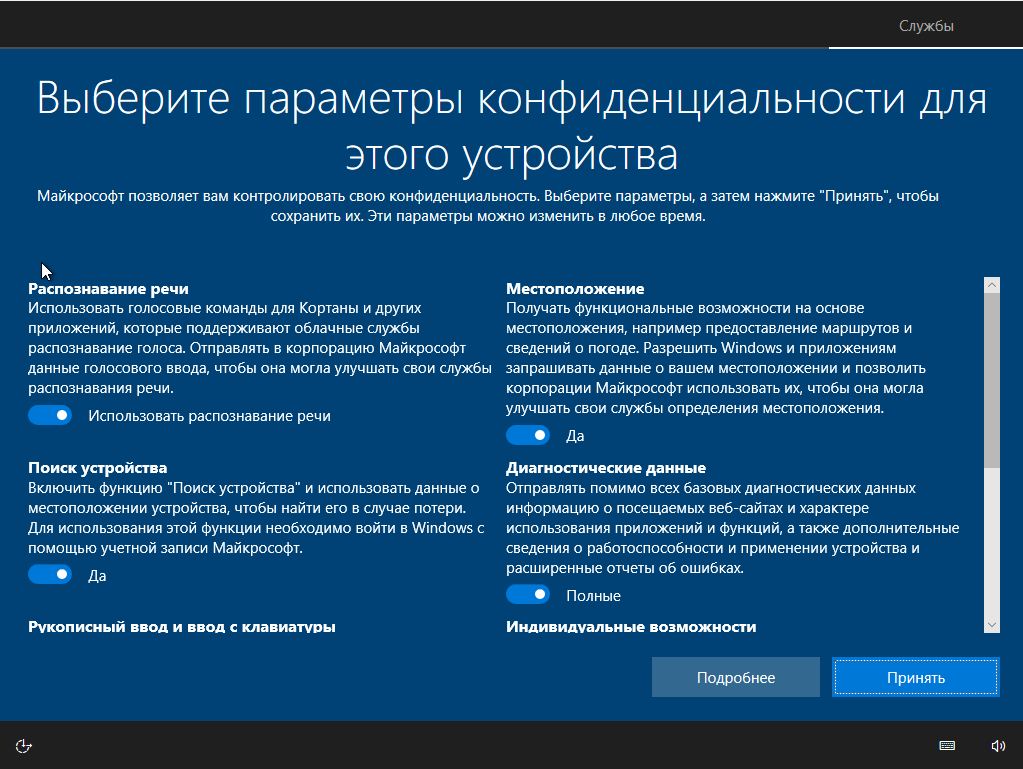
By design, the user is led to believe that if everything is turned off, no data will leak. In reality, that’s a deliberately engineered illusion. Let’s run a packet sniffer and see what’s really going on.
Testing methodology
All tests were run in parallel on two Windows 10 Pro test builds — 1709 and 1803. To keep conditions identical, each “anti-spy” tool was deployed to clones of the same VM. In the screenshots, the first image shows results on 1709 and the second on 1803, unless stated otherwise. The following utilities were used: Wireshark 2.6.3 (64-bit), TCPView v3.05, and Regshot v2.1.0.17.
In all the programs we tested, we cranked the blocking settings up to the max. If you leave any feature or app unblocked, you introduce uncertainty. You won’t know whether the data leak is caused by that unblocked item or because the program failed to disable some feature. The ideal outcome is a network traffic dump with no Microsoft IP addresses at all. Let’s see how each one handles that, but first, we’ll check Windows’ built-in privacy controls.
Auditing Privacy Settings
With the default settings, immediately after the OS boots you’ll see a significant spike of outbound traffic to Microsoft endpoints.
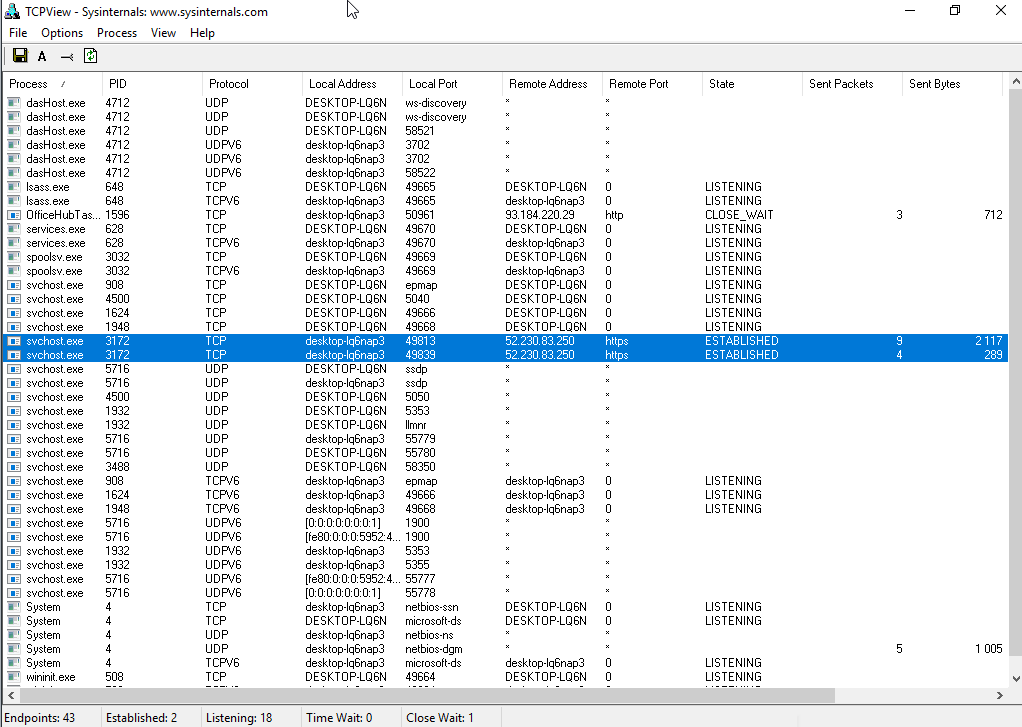
Now turn off everything you can on the Privacy screen. The results speak for themselves.
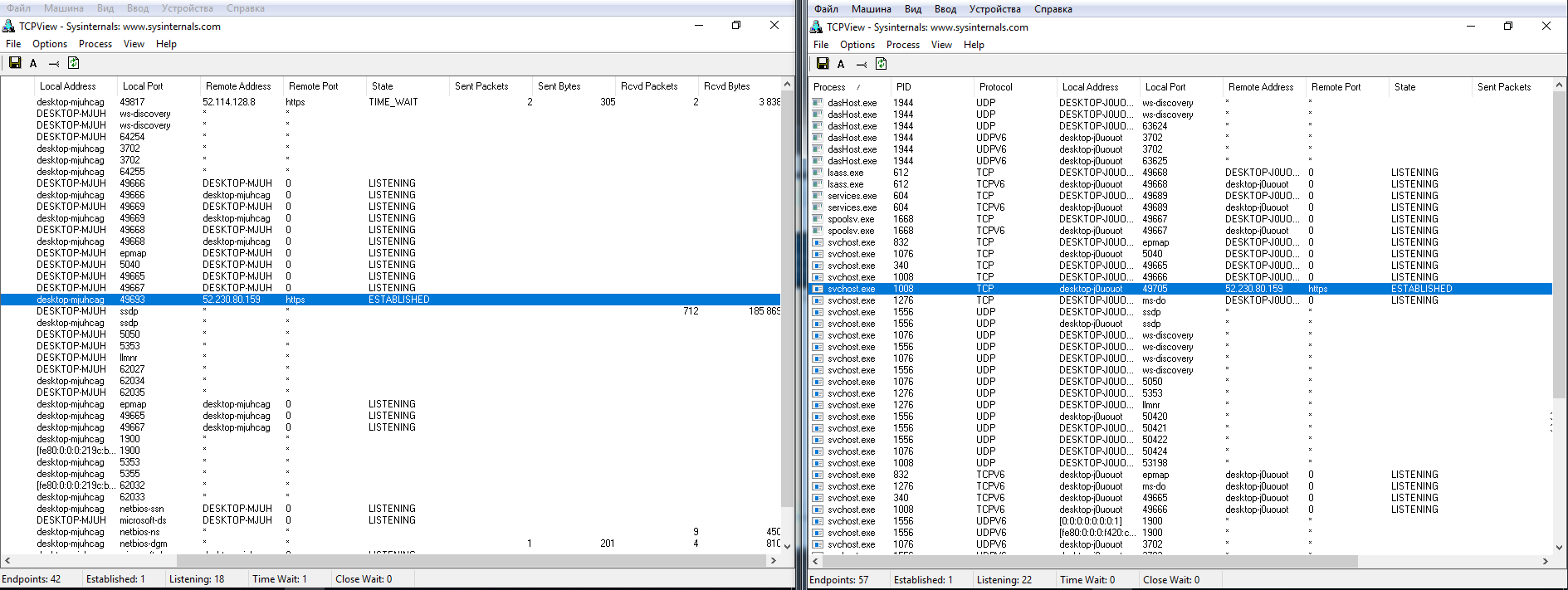
Even after setting every toggle to the most restrictive position, some data is still sent immediately to the Microsoft Azure cloud—specifically to Singapore. In the Wireshark logs, I saw IP addresses for Microsoft network endpoints from various countries. That’s presumably due to load balancing. The connections aren’t persistent (connect, send what’s needed, then tear down). The address pool is very large. I cross-checked them and confirmed that almost all belong to Microsoft or its partner networks.
Utility comparison
For comparison, we selected the following “anti-spy” tools: Blackbird 1.0.28, Destroy Windows 10 Spying 1.0.1.0, DoNotSpy10 4.0, O&O ShutUp10 1.6.1399, Disable Win Tracking 3.2.1, and WPD 1.2.940. All of these apps share one goal: to keep Microsoft from collecting data through known channels. They also offer various perks like blocking updates. Here’s a general list of what you can expect from such utilities:
- Disable user activity history
- Disable sending keyboard typing data to Microsoft
- Disable sending handwriting/inking samples
- Disable collection of diagnostic data (telemetry)
- Disable collection of location data
- Disable and reset Cortana personalization
- Disable Internet access for Windows Media DRM
- Disable app access to account info, calendar, messages, camera, microphone, and location
- (Optional) Disable Windows Update for other Microsoft products
Of course, this isn’t a complete list—just a sensible baseline to aim for. You can make all these changes manually. So‑called “anti-spy” utilities are appealing mostly because they apply hundreds of tweaks with a couple of clicks.
How do these tools actually work?
- Modify registry keys that control privacy settings.
- Append to the hosts file (%WINDIR%\System32\drivers\etc\hosts) a list of domains known to the authors as endpoints Microsoft uses to collect data.
- Add Windows Firewall deny rules that block connections to known Microsoft IP addresses.
- Stop “tracking” services.
- Remove “spyware” scheduled tasks.
- In the hardcore variant, delete system files and directories responsible for these “spy” features.
warning
Trying to squeeze maximum privacy out of these tools can break essential components, invalidate Windows activation, make the OS unstable, or even prevent it from booting. We strongly recommend not relying solely on their built-in backup features and instead using third‑party software to create a full disk image. That way you can reliably roll the system back to its original state, no matter what happens during your experiments.
Blackbird 1.0.28
The program runs in console mode. Initially, it has only three functions:
- Scan the system and list all issues the tool (in the developer’s view) detects.
- Launch the blocking manager.
- Back up the settings. I want to call this feature out: not every app offers it, so if something goes wrong, you can simply restore your pre-blocking settings and keep working. The backup is saved in the program’s folder, and once it’s created, the app changes the corresponding option from “Back up” to “Restore from backup.”
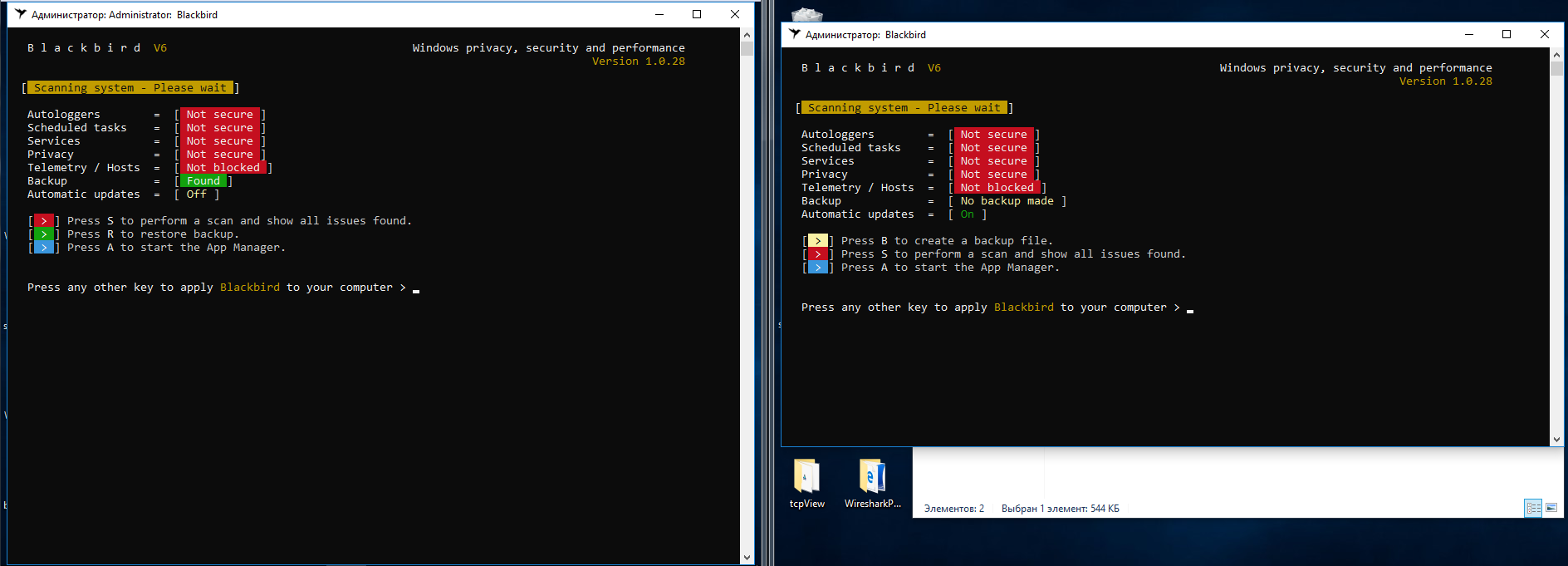
After the scan, it produces a very long list of “issues” that need to be fixed.
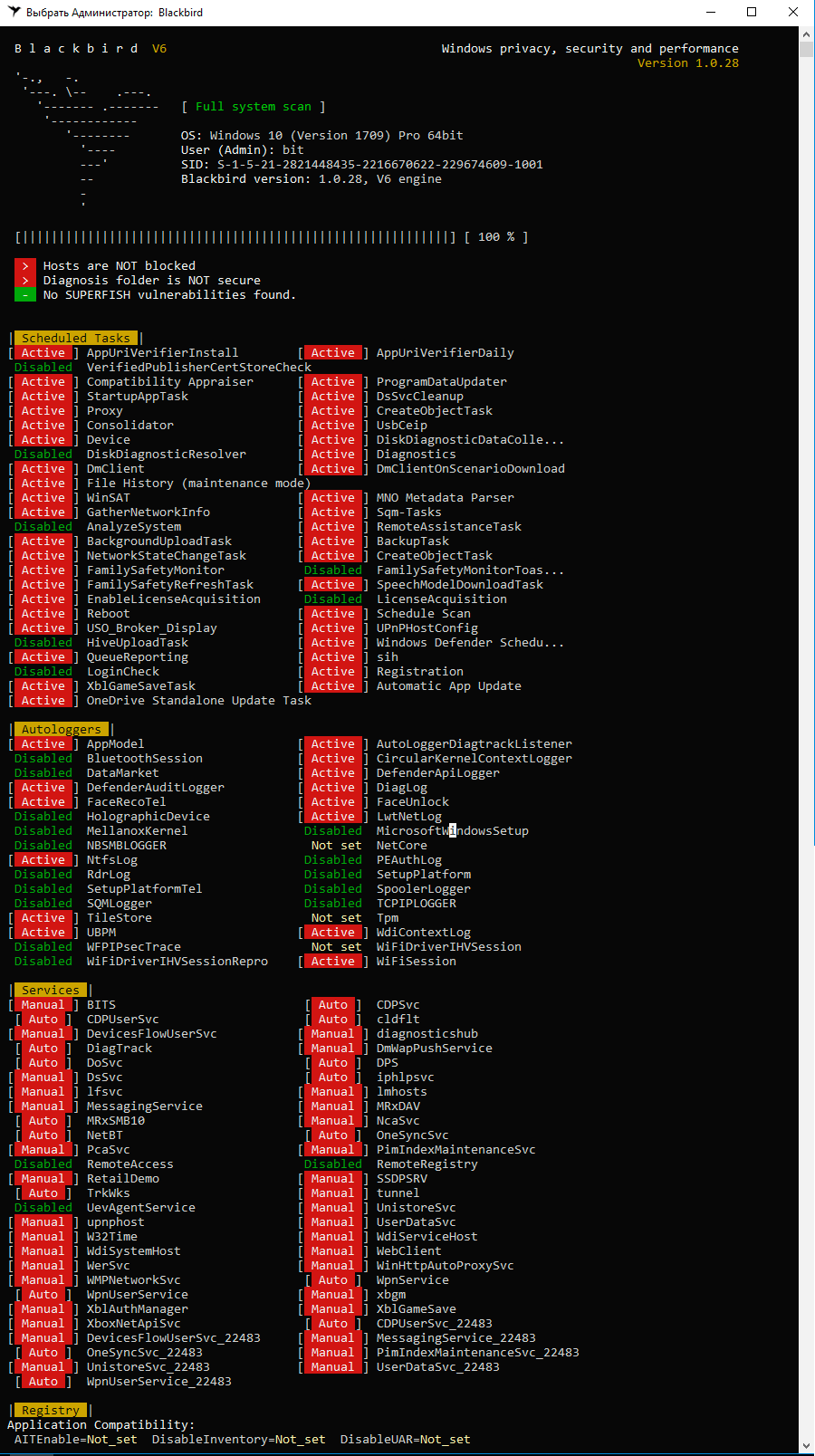
There are indeed a lot of items in there, but some of them are quite questionable. For example, the recommendation to disable the Windows Time (W32Time) service really stood out. If the machine is joined to a domain, how is it supposed to synchronize time with the server?
Let’s open the blocklist. On the program’s main screen, press A and you’ll see a screen like this.
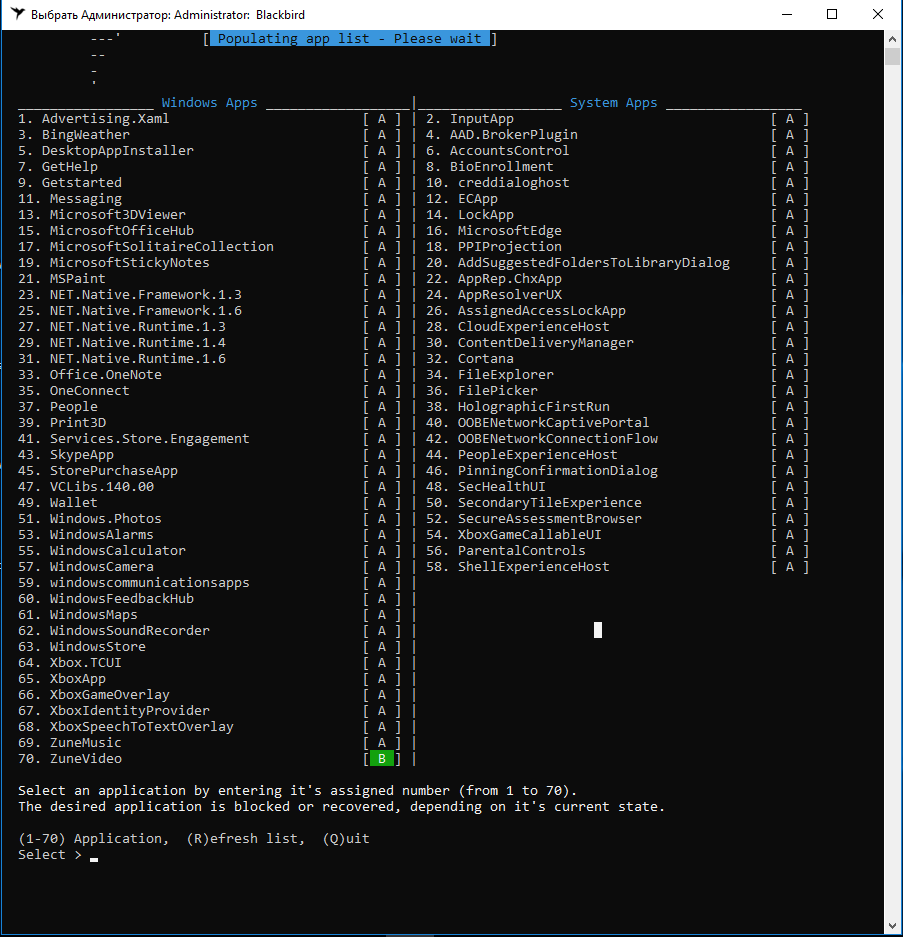
Note that build 1803 introduced several new features, so there are 78 items to block, not 70 as in 1709. This is a clear example of why I chose two Windows 10 releases for the test.
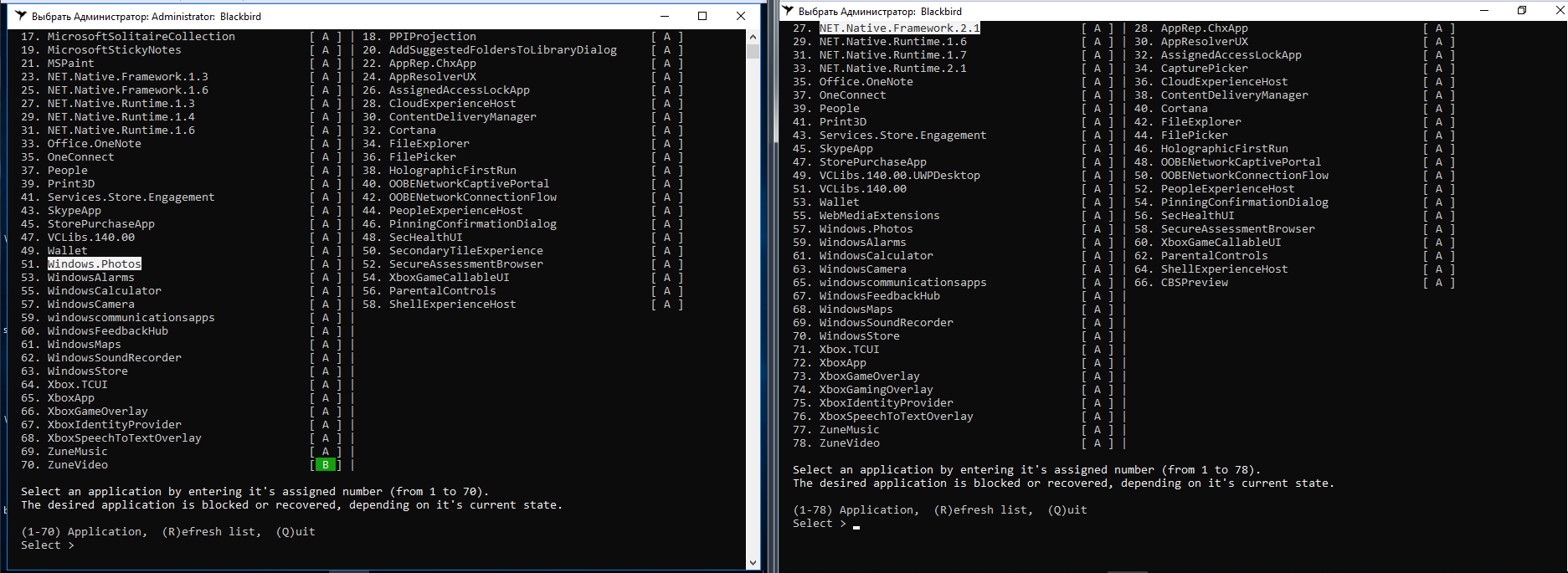
Windows Update isn’t among the components Blackbird can disable. And the disablement workflow is clunky: there are no preset profiles, so you have to select every option manually.
After following the steps on build 1709, all “tracking” features were successfully disabled—the tool worked flawlessly. On build 1803, one feature couldn’t be turned off, and for some reason the total count increased to 79.
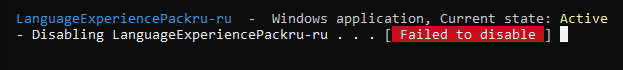
Two days of monitoring OS behavior showed that after running Blackbird, outbound traffic dropped severalfold. However, the test PC running build 1803 kept sending data to IP 104.25.219.21. Shodan reports this address belongs to the cloud provider Cloudflare. As far as I know, Microsoft has long rented hosting there for virtual servers that collect telemetry. No other similar network activity was observed, aside from downloading updates.
Blackbird did a decent job blocking tracking features, but it left both test builds unusable. The Start menu won’t open. Edge and IE won’t launch. The Store and Mail try to start and then immediately close. The notification center shows messages you can’t open. In short, you can’t live with an OS this mangled. On the plus side, updates installed without a hitch.
Restoring from a Blackbird backup didn’t help. On Windows 10 version 1709, activation was lost and two registry errors appeared. A reboot didn’t fix any of it. On version 1803, Blackbird wouldn’t even start to restore from the backup, complaining about a file system error (even though the FS was fine).
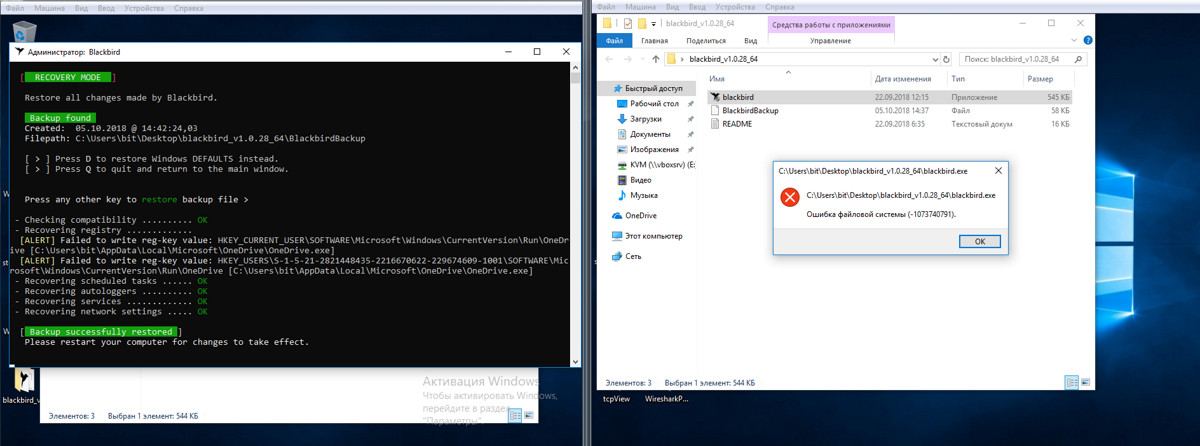
The conclusion is obvious: Blackbird belongs in our former “Dirty Tricks” column.
Destroy Windows 10 Spying 1.0.1.0
https://github.com/Nummer/Destroy-Windows-10-Spying
Destroy Windows 10 Spying is a small utility that’s probably familiar to anyone who’s tried to stop Windows from sending data to Microsoft. Rumor has it (https://twitter.com/nummerok/status/1007868805840850945) that after version 1.0.1.0 the developer changed and newer releases started bundling a trojan. So we’ll use the last official version released by Nummer.
Version 1.0.1.0 was released in April 2018. It launched on my builds and identified them correctly. Among other things, the program includes a feature to disable Windows updates, which I took advantage of as well.
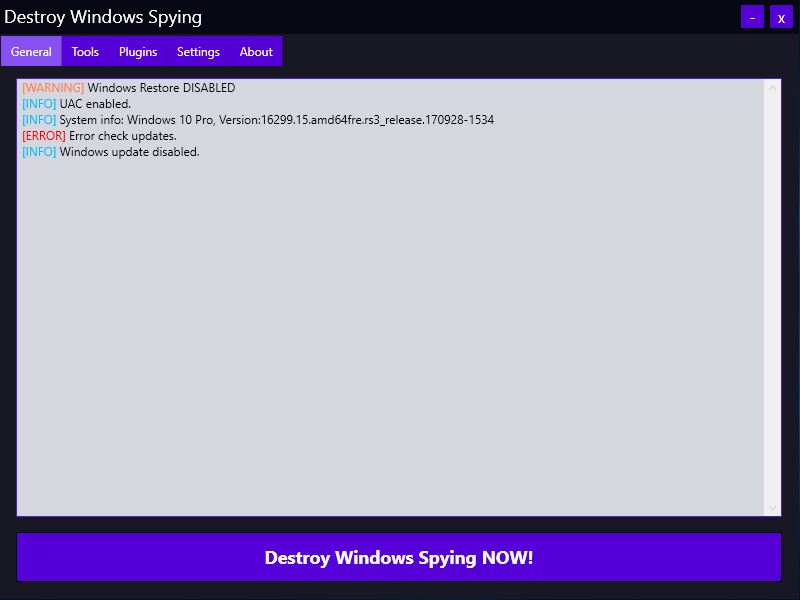
All changes are applied when you click the big “Destroy Windows Spying NOW!” button. The program runs in three phases: it disables “spying” (telemetry) services, adds known IP addresses to the firewall rules, and writes the URLs of Microsoft telemetry servers to the hosts file. It then reboots to apply the changes.
I was disappointed by DWS’s results.
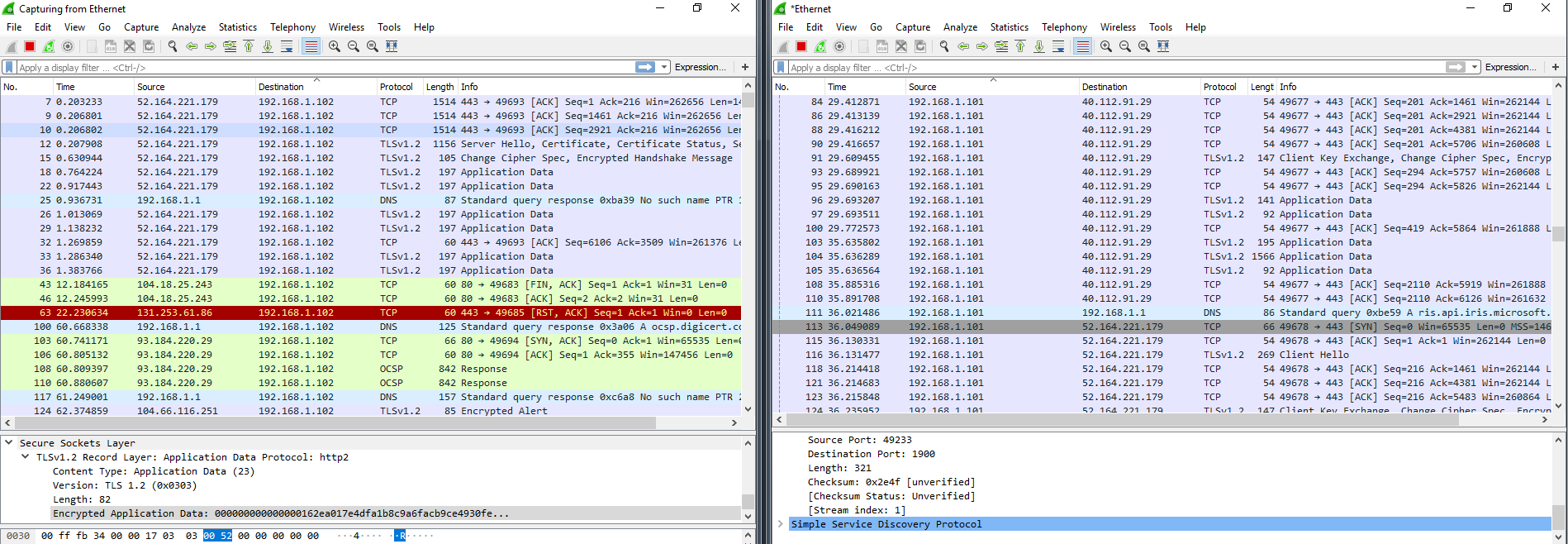
Outbound traffic to sketchy addresses went down, but there was still active chatter with IPs we don’t want. The program is outdated, and on newer Windows builds it doesn’t really do its job. On the upside, it doesn’t cripple the OS like Blackbird. My VMs survived DWS. Over three days we didn’t see any software issues. Right after a reboot, build 1709 did freeze a couple of times, but it was a minor hiccup and everything recovered.
DWS also botched the Windows Update block. After four or five Windows restarts, svchost showed up in the TCPView logs again and went right back to pulling down updates as if nothing had happened. I also noticed build 1709 talking a lot to an IP address in Akamai Technologies’ network (they partner with Microsoft) and a sharp increase in SSDP packets. It’s possible Windows was cycling through fallback paths to send data when its own servers were partially unavailable.
DoNotSpy10 4.0
https://pxc-coding.com/donotspy10
Another popular tool with a user-friendly interface. The developer provides a brief description for each option, so it’s easy to set up—just tick the boxes and you’re good to go!
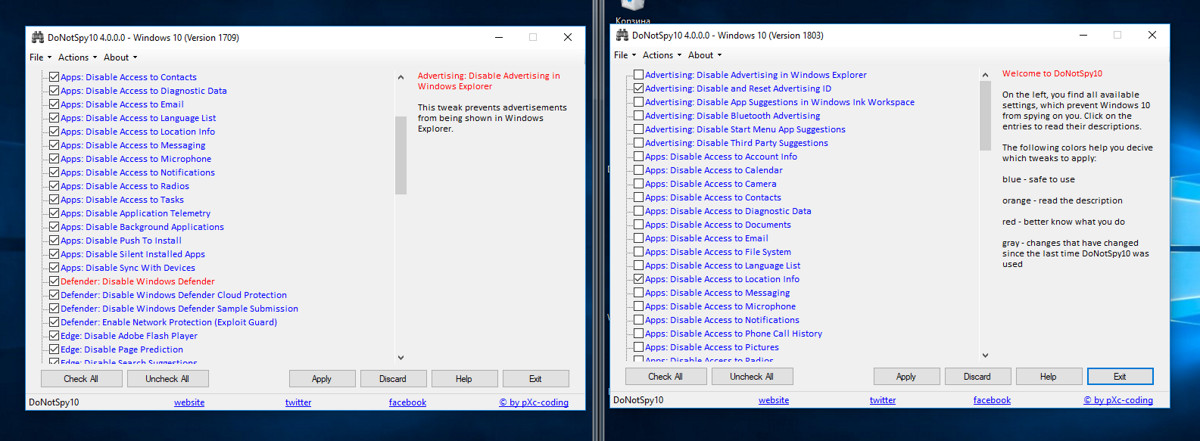
This tool lets you create a system restore point before applying changes (not just a settings backup, an actual restore point). In my view, they went overboard with the feature set—there’s just too much stuffed in. I cranked everything up to the max, and the outcome surprised me. After four hours of idle time, the systems started rebooting on their own. Turns out “blocked” updates had quietly installed in the meantime. Wireshark captured nearly 400,000 packets in an hour—something I hadn’t seen with other utilities. Most of those packets were headed exactly to the endpoints DoNotSpy10 was supposed to block. To top it off, licenses got deactivated on both OSes.
Masochists will love DoNotSpy10, and everyone else will be disappointed.
O&O ShutUp10 1.6.1399
https://www.oo-software.com/en/shutup10
This utility from the German vendor O&O Software has a clean interface and several configuration profiles. You can apply only the recommended tweaks or everything at once with a single click. Another plus is the ability to import and export registry settings—something that, in practice, proves quite important. The Russian machine translation is rough, but it’s sufficient to understand the tooltips that pop up when you click to disable a feature.
The program window has a column labeled “Recommended?” with several entries marked “NO.” At first glance, it looks like these are particularly risky tweaks, but the list even includes automatic updates.
One important note up front: in build 1709 the tool suggests changing 97 items, while in 1803 it’s up to 100. The three new items are under “App privacy” and block access to documents, pictures, and videos.
As soon as I selected the first monitoring feature, the app warned that System Restore point creation is disabled on this system. Another brownie point!
As in all the previous tests, I chose the Ultra preset to get the most out of the program. Right before closing, O&O ShutUp10 warned that if updates get pushed to the PC—and, in the developers’ view, they will anyway—you’ll have to relaunch the tool and reapply the settings. So why not just block updates from installing altogether?
One more small observation (a nitpick, but the perfectionist in me is annoyed): after the warning, the program offers to reboot, but it can’t actually do so on either build 1709 or 1803. I had to reboot both manually.
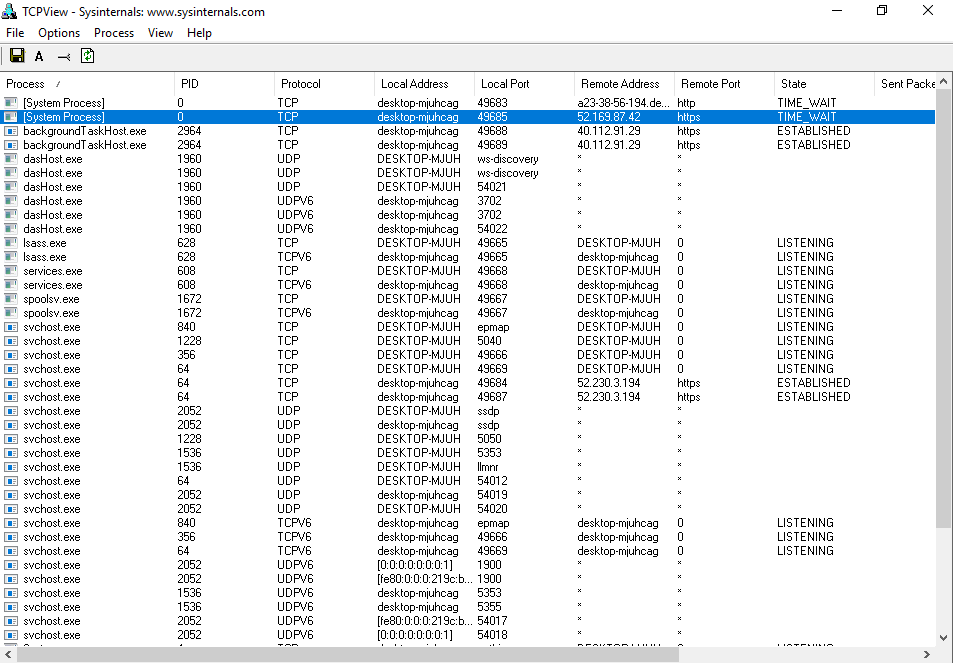
Right after the next OS boot, and before launching Wireshark, TCPView painted an unpleasant picture: processes were once again talking to Microsoft addresses.
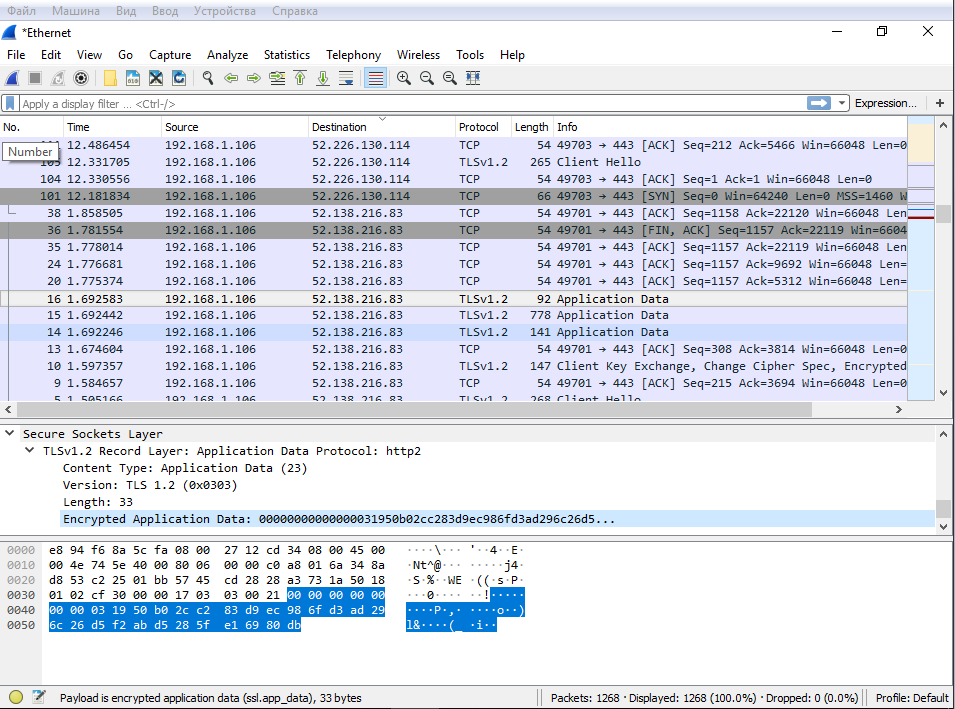
The Wireshark capture was disappointing as well. The session setup and data transfer are clearly visible, even though not that many packets are being sent.
As expected, svchost.exe is still pulling down updates, even though I disabled them in O&O ShutUp10 by toggling the two Windows Update–related options.
After 5–8 hours, internet access went down. Restarting the network adapter restored it, but the next check for updates in Windows failed.
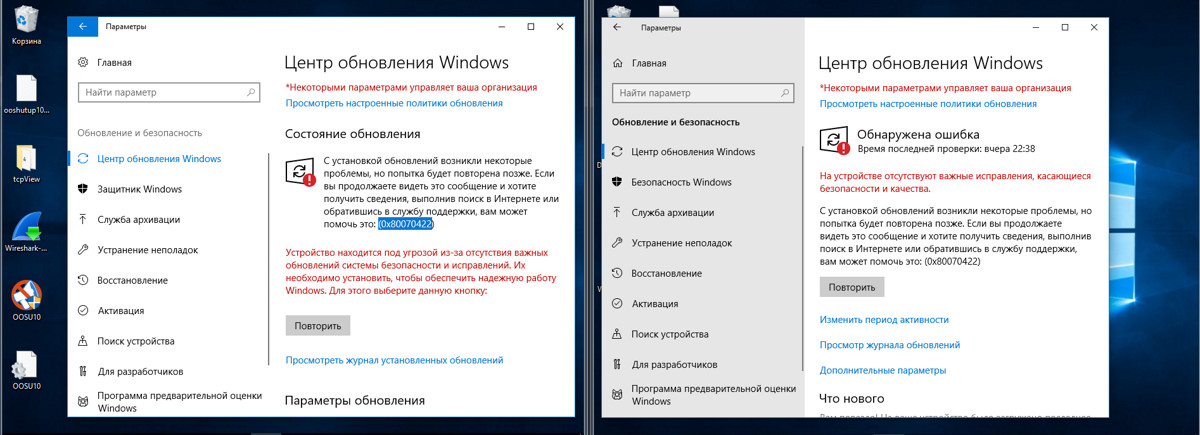
After 24 hours, two settings had changed: “Prevent apps from running in the background” and “Disable telemetry (3/3)” were both turned off. This didn’t happen on 1709.
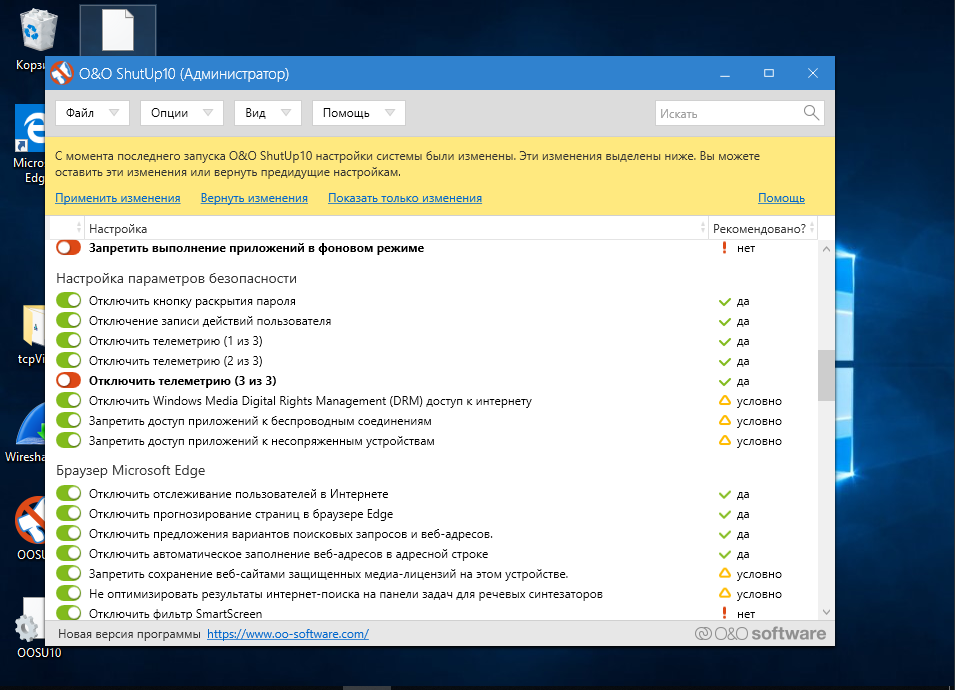
Two days in with O&O ShutUp10: so far so good, and overall the results are encouraging. I still occasionally see traffic to Microsoft servers in various countries. On build 1803, most of that comes from BackgroundTaskHost.exe, dasHost.exe, and svchost.exe (the latter keeps a persistent connection for the entire session), whereas on 1709 it’s only svchost.exe.
Also on 1803, after every reboot the “Prevent apps from running in the background” setting gets switched off (this didn’t happen on 1709), and some settings that O&O ShutUp10 had previously disabled or blocked are automatically restored. So it seems Windows 10 1709 is under control, but 1803 is still a tough nut for it.
Rolling back the settings was painless. There’s not much more to say about it.
No issues with the operating systems themselves after using O&O ShutUp10. Several times I even noticed faster performance—which, given the meager resources split across one host and two guest OSes, is very noticeable.
Disable Win Tracking
https://github.com/10se1ucgo/DisableWinTracking
Disable Win Tracking 3.2.1 is another small, simple utility with a bare-bones interface. It was updated early this year, but there’s no information about support for different Windows builds.
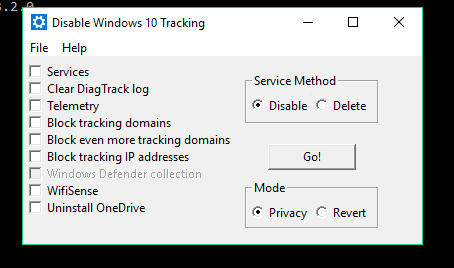
The Services section offers two modes: remove services or disable them (I chose remove). It acts on two services: DiagTrack (the diagnostics/telemetry data collection service) and dmwappushsvc (the WAP Push Message Routing service). Everything else is pretty straightforward. When you select certain items, the tool will politely warn that disabling some features has consequences and some apps may stop working.
info
Initially, DiagTrack was distributed as the optional update KB3022345. This “spy” service could be left uninstalled or removed using built-in tools, but in late 2015 Microsoft renamed it to Connected User Experiences and Telemetry and baked it into the OS as a mandatory component.
Click GO, and when it finishes you’ll get a detailed report of what was done. It’s worth skimming through to see what the program actually does.
Three days into the test, another round of updates was installed. The dmwappushsvc service reappeared in the list, but it was disabled. Based on network monitoring, Microsoft and Akamai addresses were still present in the logs. My systems continued connecting to them regularly, but the traffic volume decreased. Disable Win Tracking didn’t affect OS stability, but Skype stopped working. The system changes were minimal: a few new rules for the built‑in firewall and some registry tweaks.
Windows Privacy Dashboard
The last tool I’d like to cover is WPD 1.2.940. At the time of writing, the current release was dated October 11, 2018, but its rules for blocking tracking components were from September 16. It claims support for Windows 10 up to version 1809. The program’s features are split into three sections: privacy controls, firewall rule creation, and removal of installed apps (“junk,” as the developers call them).
The Privacy module disables scheduled tasks, turns off certain services, and makes registry changes. Firewall rules are generated based on the selected privacy mode: Spy or Extra. Choosing the latter blocks OneDrive, Skype, Live, and similar services (the program warns you about this). As with the other tools, I pushed it to the limit, short of uninstalling apps.
Over four days of testing, I didn’t encounter any OS issues—both test systems ran stably. I’m as satisfied with this tool as I am with O&O ShutUp10. After running WPD, the logs showed only a minimal number of connections to Microsoft and its partners’ servers, and the network packets were very small.
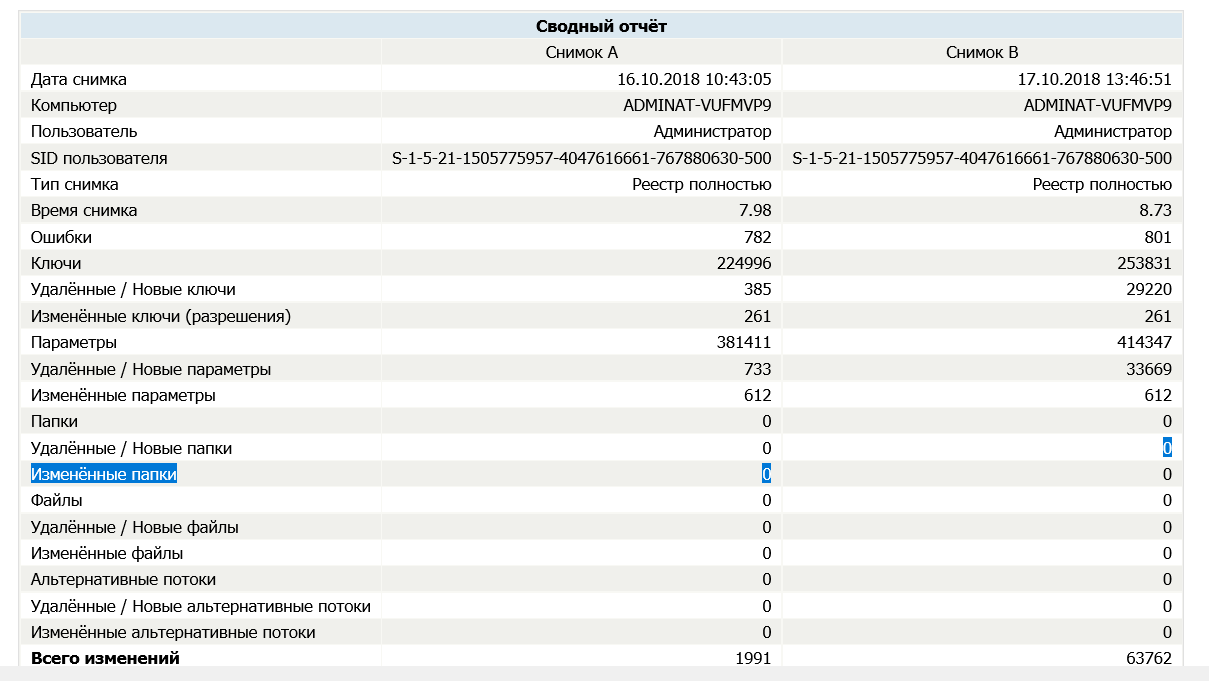
Most of WPD’s changes are applied to the registry. Here’s what the result looks like on Windows 10 (version 1803).
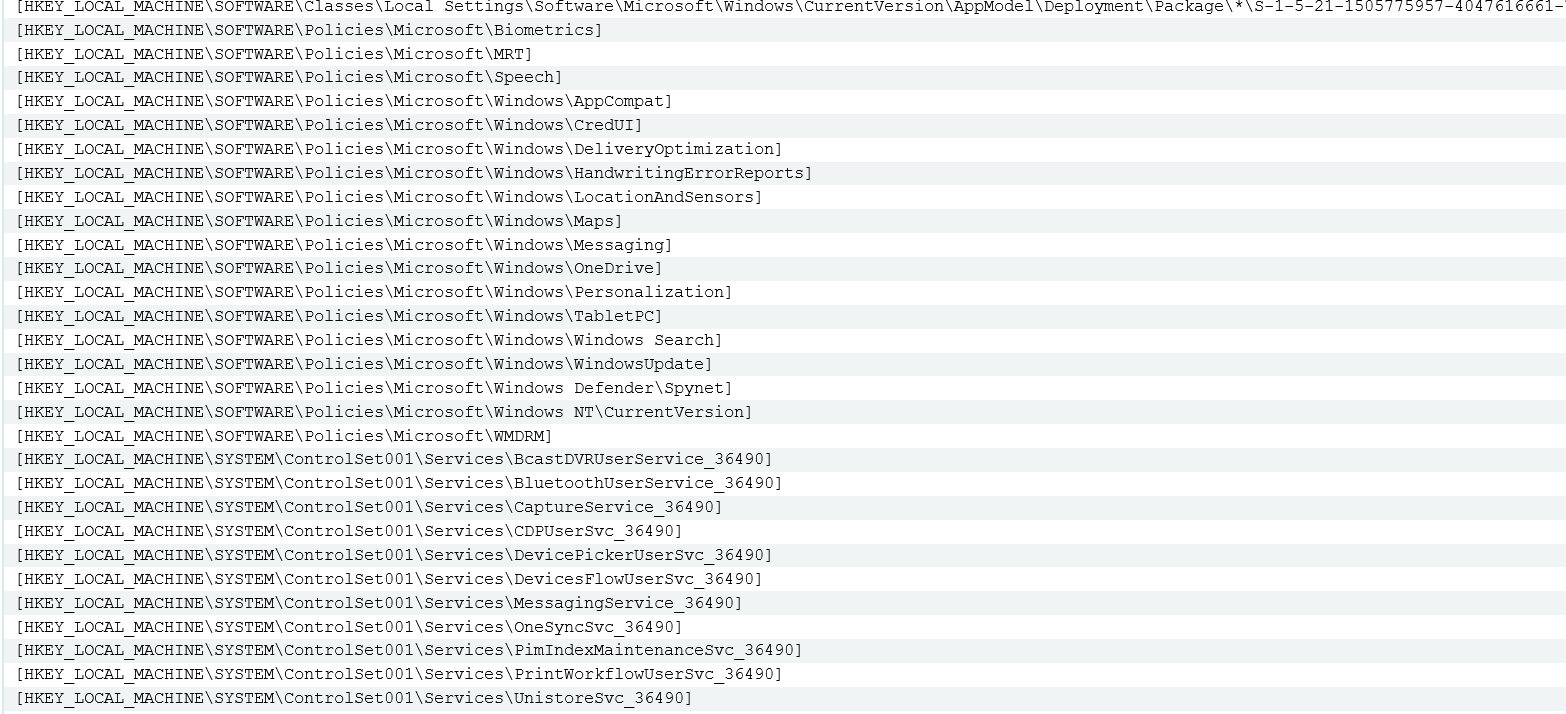
I compared the registry snapshots using Regshot. Listing every modified key would be overly tedious. I think the number in the “Deleted/New values” line speaks for itself.
The program created a single firewall rule and populated it with a long list of IP addresses.
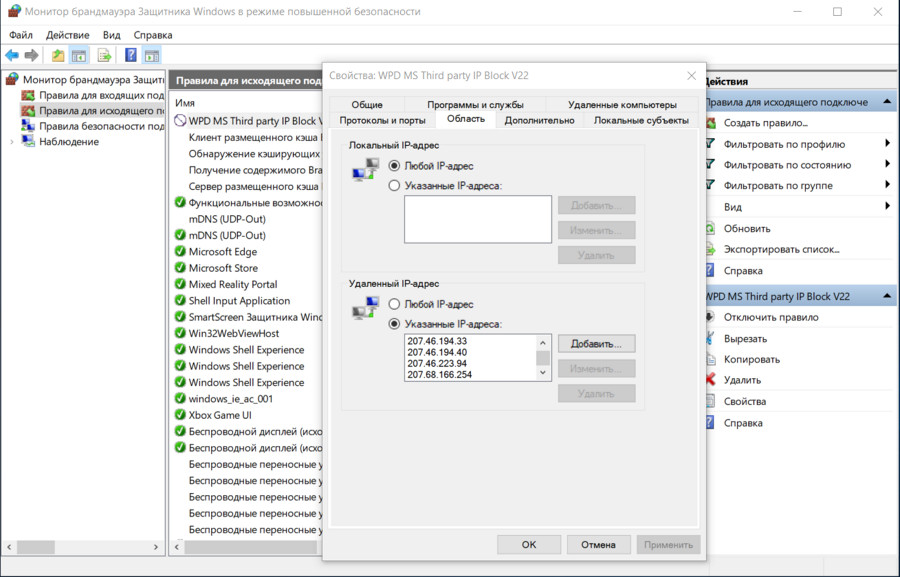
Overall, WPD performed quite well.
Manually Disabling Telemetry
Let’s try to manually perform some of the steps the tools would normally handle. We’ll apply the main blocking measures I mentioned earlier. Proceed at your own risk. Before editing the Registry, I recommend creating a backup.
Disable Activity History
This is controlled by the Timeline feature. Open the Registry Editor (regedit) and navigate to HKEY_LOCAL_MACHINE\. Create a 32-bit DWORD named EnableActivityFeed and set its value to 0.
Disabling the “Keylogger”
This is about the dmwappushsvc service. Go to HKEY_LOCAL_MACHINE\ and set its Start value to 4 (you can also disable DiagTrack here while you’re at it).
Disabling Windows Telemetry
A quick note: on current Windows builds you can’t completely disable telemetry without breaking important system functionality. There are three data-collection levels: Basic, Enhanced, and Full. There’s also a Security level, but it’s only available in Enterprise.
You can set the minimum telemetry level via the registry:
– Key: HKEY_LOCAL_MACHINE\ (create this key if it doesn’t exist)
– Create a 32-bit DWORD named AllowTelemetry and set it to 1.
Disabling location tracking
Go to HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\DeviceAccess\Global{BFA794E4-F964-4FDB-90F6-51056BFE4B44} and set its value to Allow.
Disable Cortana
In the HKEY_LOCAL_MACHINE\ key, set the Allow parameter to 0.
Disabling OneDrive
At HKEY_LOCAL_MACHINE\, find or create a DisableFileSync DWORD (32-bit) value and set it to 1.
Disabling Telemetry Tasks in Task Scheduler
Beyond telemetry, Task Scheduler contains a bunch of preconfigured tasks that consume resources and run without the user’s knowledge. Most of them collect telemetry for the Customer Experience Improvement Program and the SmartScreen cloud protection service.
You can disable all of this with the following commands:
schtasks /Change /TN "Microsoft\Windows\AppID\SmartScreenSpecific" /Disable
schtasks /Change /TN "Microsoft\Windows\Application Experience\ProgramDataUpdater" /Disable schtasks /Change /TN "Microsoft\Windows\Application Experience\Microsoft Compatibility Appraiser" /Disable
schtasks /Change /TN "Microsoft\Windows\Autochk\Proxy" /Disable
schtasks /Change /TN "Microsoft\Windows\Customer Experience Improvement Program\Consolidator" /Disable
schtasks /Change /TN "Microsoft\Windows\Customer Experience Improvement Program\KernelCeipTask" /Disable
schtasks /Change /TN "Microsoft\Windows\CloudExperienceHost\CreateObjectTask" /Disable
schtasks /Change /TN "Microsoft\Windows\DiskDiagnostic\Microsoft-Windows-DiskDiagnosticDataCollector" /Disable
schtasks /Change /TN "Microsoft\Windows\Maintenance\WinSAT" /Disable
schtasks /Change /TN "Microsoft\Windows\NetTrace\GatherNetworkInfo" /Disable
schtasks /Change /TN "Microsoft\Windows\Shell\FamilySafetyMonitor" /Disable
schtasks /Change /TN "Microsoft\Office\OfficeTelemetryAgentFallBack" /Disable
schtasks /Change /TN "Microsoft\Office\OfficeTelemetryAgentLogOn" /Disable
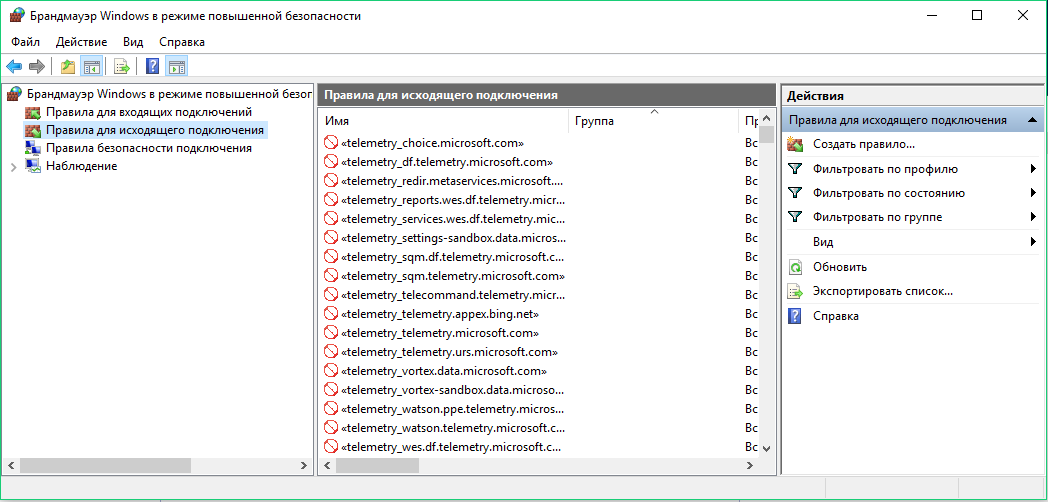
Blocking data transmission to Microsoft’s servers
There are plenty of sites that regularly update lists of Microsoft “spy”/telemetry servers. For example, you can find a primary list on aeronet.cz. The simplest approach is to add those domains to your hosts file and create blocking rules in your firewall.
I tried both methods. After about an hour of runtime, Windows attempted to connect to one of the blocked addresses, but the packet had a zero-length payload.
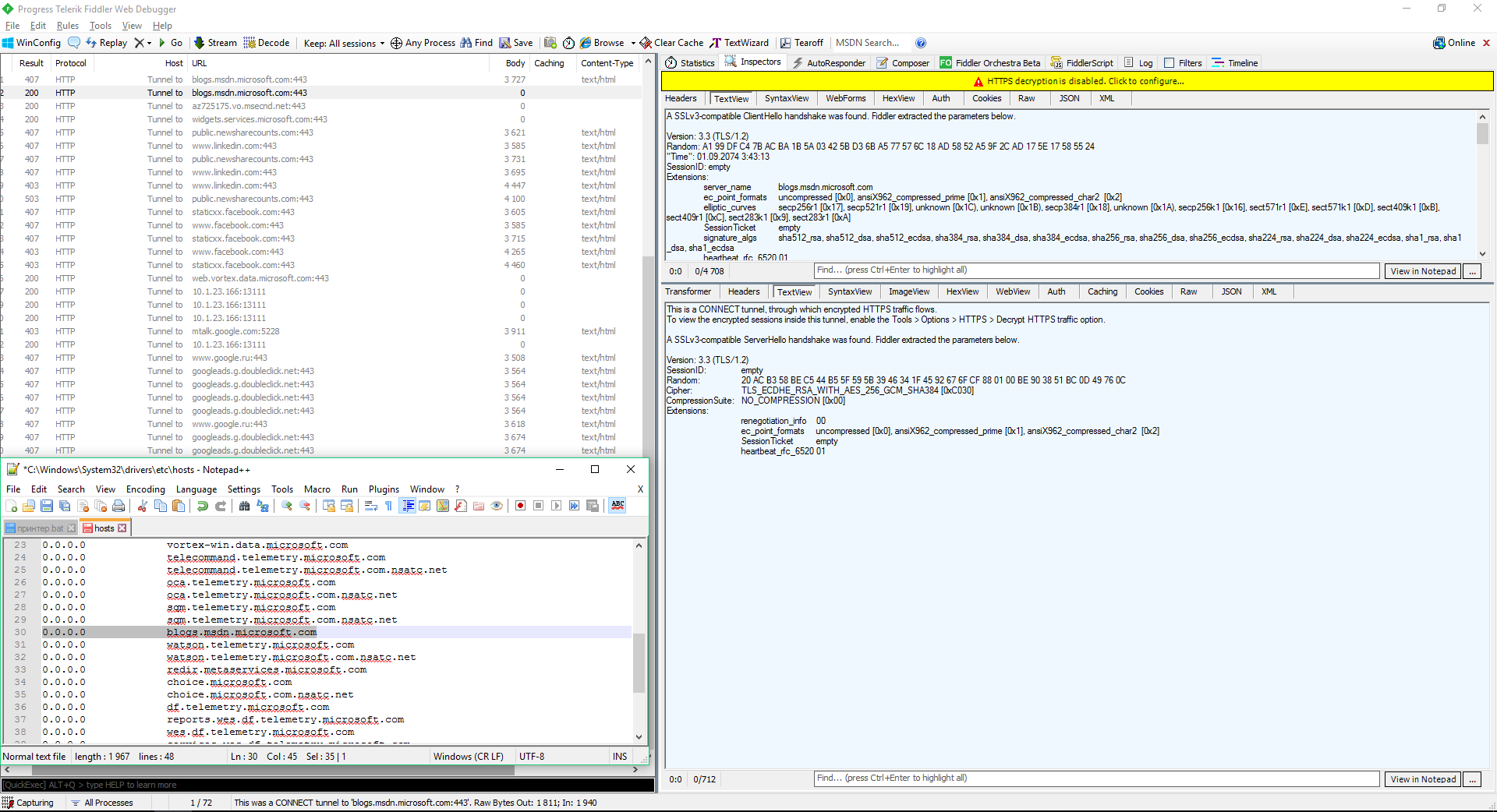
Some security experts believe that Windows system processes (including the “telemetry” ones) can bypass blocks in the hosts file and the built-in firewall. In theory, hosts-based URL blocking can be evaded by connecting directly to an IP address, and IP blocking in a software firewall can be worked around via dnsapi.dll and by hooking protocol-creation functions at the NDIS layer by other Windows kernel components. However, in my small experiment I didn’t observe any stray traffic. After applying hosts and firewall rules, attempts to reach the “spy” servers continued, but the outbound packet count stayed at zero, and there were no inbound packets at all.
Blocking Windows Updates
To wrap up, here’s another small utility whose sole purpose is to block Windows updates—something most tools failed to accomplish despite claiming the feature. It’s StopUpdates10 2.0.32.
The program’s interface is just a single button. Click it, reboot, test.
Over two days of testing, the program blocked update downloads, even as Windows diligently (and unsuccessfully) tried to find them. The Windows messages about component installation errors were a bit annoying.
After two days of waiting and a dozen reboots, I tried checking for updates manually, which also failed. The Installed Updates list only contained those that had managed to download before I launched the program.
Conclusions
We reviewed six tools for disabling telemetry and tightening privacy in current Windows 10 builds. There are tons of similar utilities. Their authors often copy each other’s work (“Fork me on GitHub!”), racing to make the list of tweakable settings and blocked endpoints as long as possible. They rarely bother to properly test them—especially over the long term—and issues with the OS usually don’t show up right after you apply the tweaks. It’s a ticking time bomb.
Most “anti-spy” tools for Windows 10 effectively stalled around 2016–2017 due to a constant arms race. Microsoft frequently changes the IP addresses of its servers, leases cloud capacity from Cloudflare, and routes part of its traffic through the Akamai Technologies partner network. In practice, it operates a highly dynamic IP pool and several large networks, making it impossible to keep up and block everything. On top of that, a single URL is often mapped to multiple IPs or to a multifunction server that’s required for the proper operation of other, non-“spy” Windows components.
You can also add Microsoft telemetry endpoints manually by finding curated lists on GitHub and specialized forums. You’ll need to download them, merge, edit, and validate them (the hardest part), and only then apply the distilled list. It’s a lot of tedious work just to get a result that stays stable for a while. Then Windows updates will roll out, new endpoints will appear, your painstakingly curated list will go stale, and you’ll have to start over.
Of the tools we tested, only O&O ShutUp10 and WPD more or less did their job, though even they aren’t perfect. Some privacy settings can be changed with Windows 10’s built-in controls, but the UI exposes only a fraction of them. If a utility can tweak additional, deeper options, it’s worth using. Just handle it carefully: select what to block judiciously and make backups before applying changes.