The development of Kolibri progressed quite rapidly until 2009. The program became versatile enough to run on various hardware, requiring at least a first-generation Pentium processor and eight megabytes of RAM. The minimum system requirements for Kolibri are as follows:
- CPU: Pentium, AMD 5×86, or Cyrix 5×86 without MMX, running at 100 MHz;
- RAM: 8 MB;
- Video card: VESA-compatible with VGA mode support (640 × 480 × 16 colors).
The modern iteration of Kolibri consists of regularly updated “nightly builds” based on the latest official release, which was launched in late 2009. We tested build 0.7.7.0+, dated August 20, 2017.
warning
By default, KolibriOS does not have access to the disks recognized by the BIOS. Be sure to think carefully and create a backup before changing this setting.
Although changes in the nightly builds have been incremental, they have accumulated significantly over the years. The updated Kolibri can now write to FAT16-32 and ext2-ext4 partitions, and it supports other popular file systems like NTFS, XFS, and ISO-9660 in read-only mode. It now includes support for USB and network cards, a TCP/IP stack, and audio codecs. In essence, it has become practical to use for more than just a quick look at a super lightweight OS with a GUI and its impressive boot speed.
Like its previous versions, the latest Kolibri is written in flat assembler (FASM) and fits on a single floppy disk—1.44 MB. This allows it to be fully stored in specialized memory. For instance, some enthusiasts have managed to install KolibriOS directly into Flash BIOS. While running, it can fit entirely into the cache of some processors. Just imagine: the entire operating system, along with its programs and drivers, is cached!
info
When visiting the kolibrios.org website, your browser might warn you about potential risks. This seems to be due to the presence of assembly language programs in the distribution. However, VirusTotal currently identifies the site as completely safe.
Kolibri can be easily launched from a floppy disk, hard drive, flash drive, Live CD, or in a virtual machine. For emulation, you just need to set the OS type to “other”, allocate it a single CPU core, and some RAM. Connecting a disk is optional, and if there’s a router with DHCP, Kolibri will instantly connect to the internet and local network. Upon startup, you’ll see a notification confirming the connection.
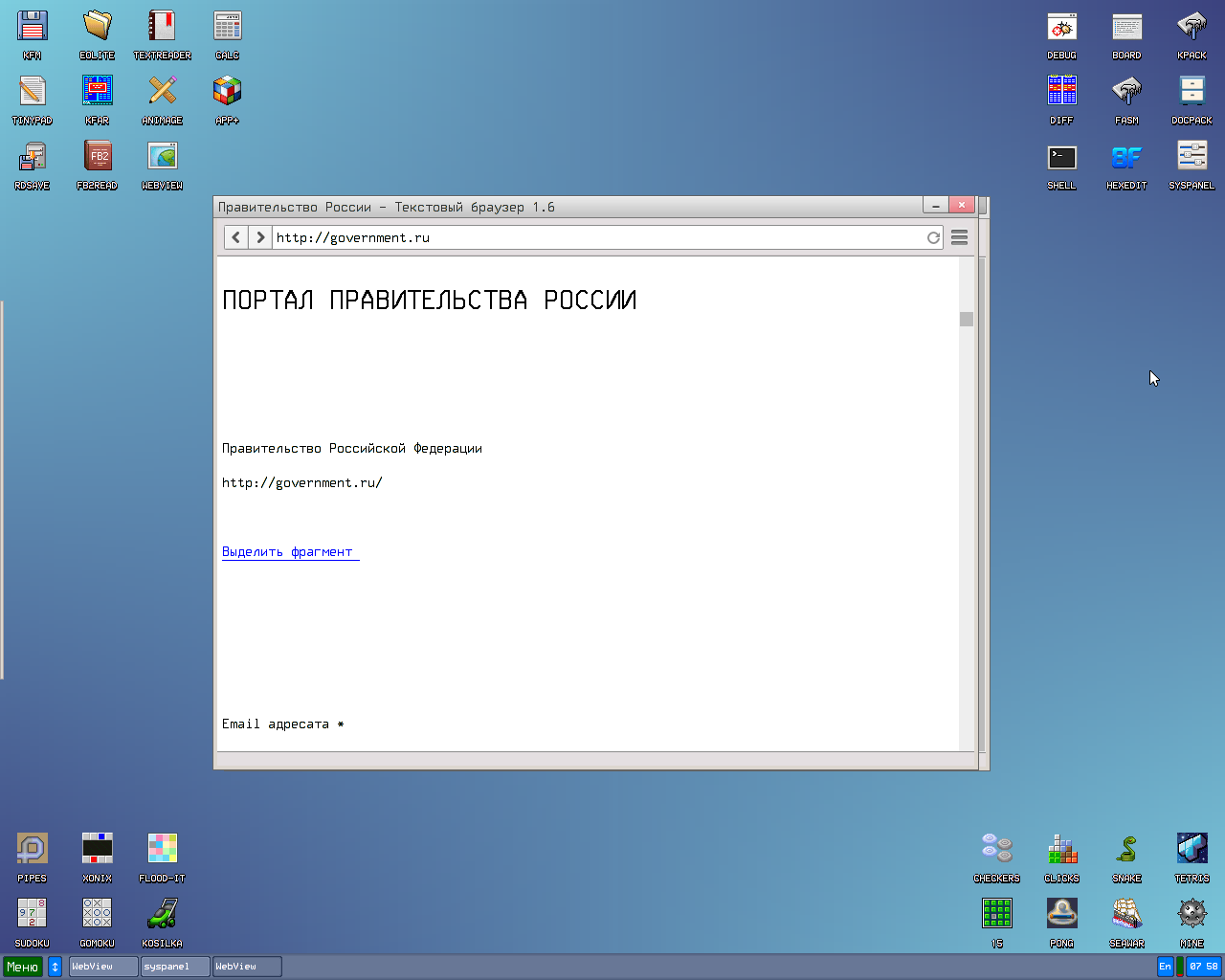
One issue is that the built-in browser in Kolibri does not support the HTTPS protocol. Because of this, it couldn’t load the Xakep.ru site, nor could it open pages for Google, Yandex, Wikipedia, “Sberbank”… basically, any standard web address. Everyone has switched to the secure protocol by now. The only site I came across using old-school plain HTTP was the “Russian Government Portal,” but even that looked poor in the text-based browser.
The appearance settings in Kolibri have been improving over the years, but they are still far from perfect. The list of supported video modes can be displayed on the Kolibri boot screen by pressing the ‘A’ key.
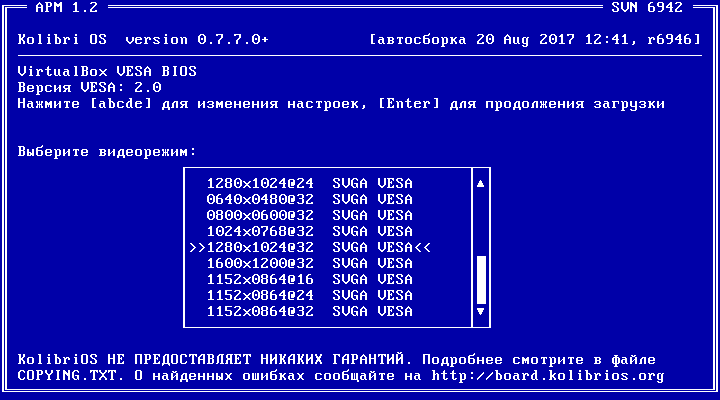
The list of available options is limited, and you might not find the needed resolution there. If your graphics card is an AMD (ATI) GPU, you can immediately add custom settings. To do this, pass the parameter -m< to the ATIKMS loader, for example:
/RD/1/DRIVERS/ATIKMS -m1280x800x60 -1
Here, / is the path to the bootloader (RD stands for RAM Disk).
When the system is running, you can check the selected video mode using the vmode command and theoretically switch it manually. If KOLIBRI OS is running in a virtual machine, this window will remain empty. However, for a clean boot, Intel video drivers can be added from i915 up to and including Skylake.
Surprisingly, KolibriOS has managed to fit in a multitude of games. It features puzzle and arcade games, including sliding puzzles, snake, and tank games (no, not WoT) – an entire “Game Center”! Even Doom and Quake have been ported to Kolibri.
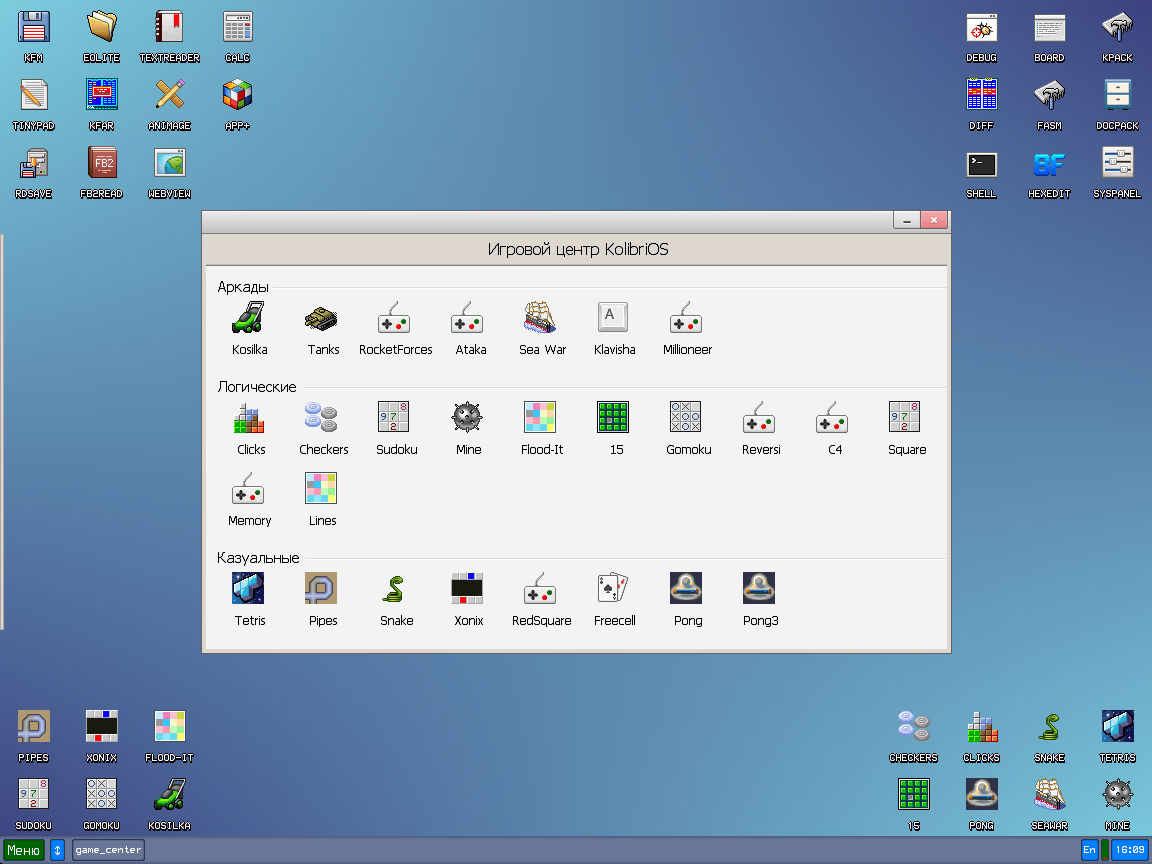
Another important tool we discovered is the FB2READ reader. It handles Cyrillic text correctly and offers customizable text display settings.
I recommend storing all user files on a flash drive, but be sure to connect it via a USB 2.0 port. Our USB 3.0 flash drive (connected to a USB 2.0 port) with 16GB of storage and an NTFS file system was recognized immediately. If you need to write files to the drive, it’s best to use a flash drive formatted with the FAT32 file system.
The Kolibri distribution includes three file managers, utilities for viewing images and documents, audio and video players, and various other user applications. However, its primary focus is on assembly language development.
The built-in text editor features ASM syntax highlighting and even allows you to run the entered programs immediately.
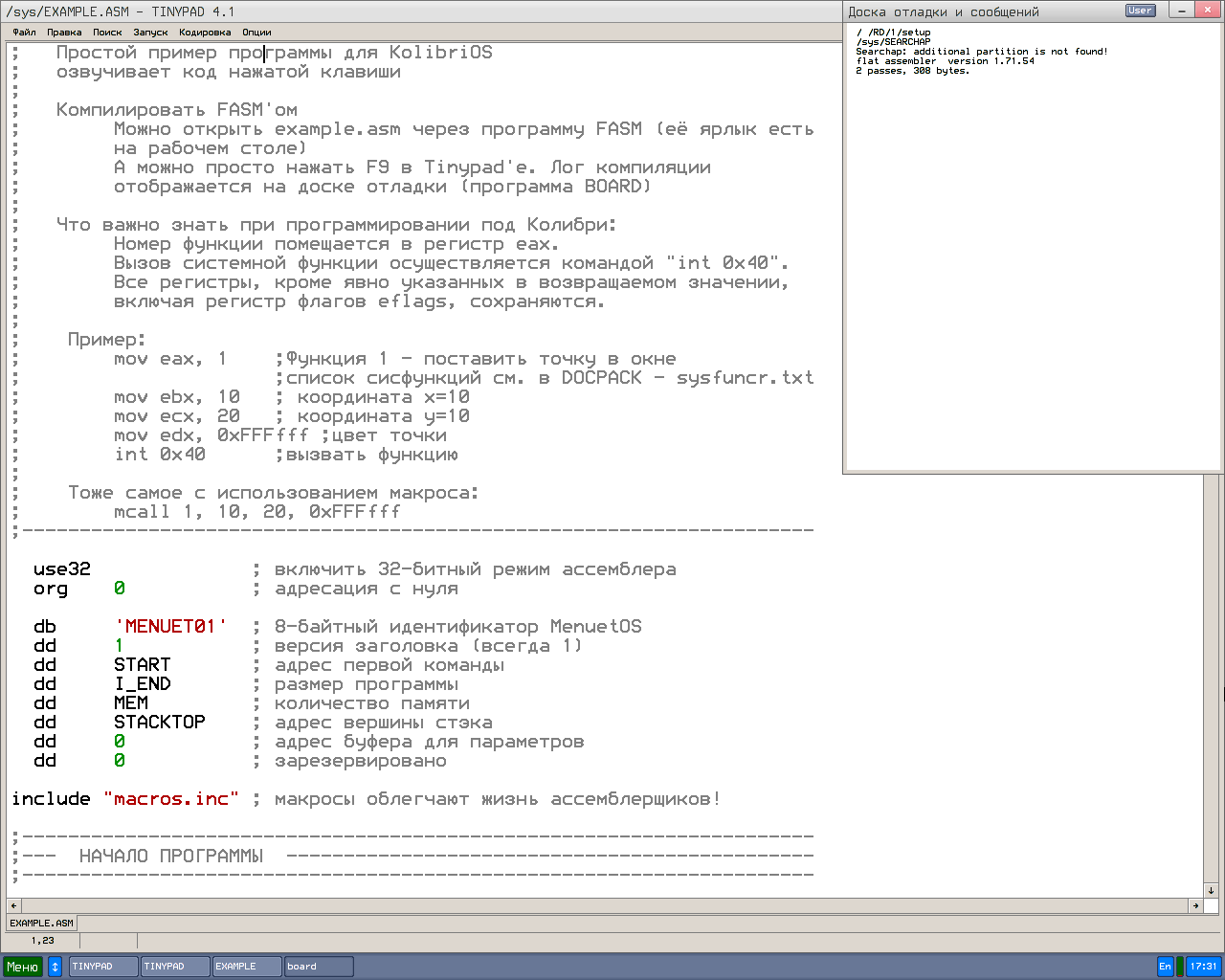
Among the development tools available, there is an Oberon-07/11 compiler for i386 systems on Windows, Linux, and KolibriOS, along with low-level emulators such as E80 — a ZX Spectrum emulator, FCE Ultra — one of the top NES emulators, and DOSBox v.0.74, among others. All of these have been specifically ported to Kolibri.
If you leave KolibriOS idle for a few minutes, a screensaver will activate. You’ll see lines of code scrolling across the screen, which include references to MenuetOS.
The Emergence of KolibriOS
The concept behind Kolibri is quite intriguing. It’s not just another Linux clone, but a completely unique creation. The only thing it shares with Linux is its open-source nature and Finnish origins.
Many of the developers behind Kolibri previously worked on another project, MenuetOS, from which this new system evolved. They recognized a common issue with operating systems: an excessively bloated and, consequently, unreliable kernel. Even in the early 2000s, Bruce Schneier discussed this in his book “Secrets and Lies: Digital Security in a Networked World.” At the time, he believed that the popular operating systems, such as the various UNIX clones, Windows NT 4.0, and its successor Windows 2000 (NT 5.0), suffered from severe security problems due to their massive kernels.
“When the UNIX system was first written, it was considered essential to place non-essential codes outside of the kernel. … All current varieties of UNIX suffer, to some extent, from bloated kernels: they either have too many commands in the kernel, mysterious utilities that run with root access, or something else.
Windows NT is much worse. This operating system serves as an example of how historical security lessons can be completely ignored. … Windows seems to hold the view that since anything in the kernel is protected by definition, everything can just be loaded into the kernel. If developers didn’t know how to secure something, they would just shove it into the kernel and consider it secure. …
The philosophy of Windows NT is to always prefer simplicity over security — both in handling and in development,” wrote Schneier in 2000. It’s not to say that his book was a revelation, but it did articulate ideas that had long been in the air.
Around that time, a group of programmers from Finland, Poland, and former Soviet states attempted to create a fundamentally new operating system. Their goal was to write it almost from scratch and make it as compact as possible—ideally small enough to fit on a floppy disk (since flash drives didn’t exist back then, and even CD burners were considered a novelty).
The system in question is MenuetOS, developed under the inspiration of Ville Mikael Turjanmaa. Previously, he had worked on MrOS—a graphical multitasking shell for DOS that eventually evolved into a standalone operating system. The concepts from MrOS formed the foundation of MenuetOS.
Initially, MenuetOS developed at a slow pace, much like the small, intricate steps of the French dance for which it is named. A turning point occurred in 2001 when an interview with the developer was published on OSNews. Shortly thereafter, other programmers joined the project, and following the porting of FASM, further code could be compiled directly within MenuetOS.
Over time, the development team composition changed frequently. Ongoing disagreements led to a split in 2003, where a group decided to create their own fork. During its development, it was called MENUETOS RE, but for the release, it was renamed to Kolibri 0.1.0.0. The name was suggested by Stanislav “VaStaNi” Valyski. It was intended to highlight the lightweightness and speed of the operating system. Officially, Kolibri was released in May 2004. KolibriOS 0.50 is considered a true fork, as more than half of its code differed from MenuetOS.
The Present and Future of the Little Bird
Currently, Kolibri is distributed under the GPLv2 license, whereas its predecessor, MenuetOS, became proprietary in its 64-bit version.
In addition to the standard KolibriOS distribution, there is also an extended version available. This version includes the DrvInst driver installation utility and other additional components. DrvInst allows you to install device drivers that are not included in the IMG image. For example, it supports installing SATA drivers with AHCI support, video drivers for Intel processors, AMD graphics cards, and VMware virtual machines.
The Kolibri operating system is gradually introducing an expanded set of fonts along with smoothing functionality. This is beneficial, as the built-in font set was originally optimized for older, low-resolution screens.
info
Kolibri has already made its mark in the fields of science and cyberpunk. Researchers from Columbia University and the New York Genome Center have encoded the KolibriOS operating system into DNA, alongside other data totaling 2342 KB.
The main purpose of KolibriOS remains the same: programming in assembly language within a pure environment without any software layers. However, developers can also write their code for KolibriOS in high-level languages like C/C++, Modula, Forth, and Pascal. This approach makes it significantly easier to create libraries, drivers, and applications.