In this article, I will show how Python scripts can be used to transmit messages between two computers connected to the web. You may need to perform such an operation while developing an app, pentesting a corporate…
CONTINUE READING 🡒 Category: Security
Hack in one click. Comparing automated vulnerability scanners
Searches for vulnerabilities require special knowledge, extensive experience, and a sixth sense. But what about novice security researchers? They have no experience and cannot gain it because don't know where to start from. This is where automated…
CONTINUE READING 🡒 Compressed Token Format (CTF). One-time passwords, LDAP injections, and tricks…
Today, I will explain how to hack the CTF virtual machine available on [Hack The Box](https://www.hackthebox.eu/) training grounds. For the purposes of this article, the abbreviation "CTF" refers to Compressed Token Format, not Capture the Flag. This…
CONTINUE READING 🡒 Ghostcat. How to exploit a new RCE vulnerability in Apache…
This article addresses a vulnerability in Apache Tomcat that enables the attacker to read files on the server and, under certain conditions, execute arbitrary code. The problem lies in the implementation of the AJP protocol used to…
CONTINUE READING 🡒 Conquering the web. Application instruction for OWASP Testing Guide v4
Web security is a very broad term. It includes bugs in old protocols, usage of dangerous techniques, trivial human errors made by developers, and more. It is difficult to test products in such a broad area without…
CONTINUE READING 🡒 Pentester’s suitcase: Identifying OS on remote host
As you are aware, any penetration test starts from information collection. You have to find out what operating system is running on the remote host, and only then you can start looking for vulnerabilities in it. This…
CONTINUE READING 🡒 DoS attacks on ModSecurity: Exploiting critical bug in popular WAF
A critical vulnerability resulting in a denial-of-service error has been recently discovered in ModSecurity, a popular web application firewall (WAF) for Apache, IIS, and Nginx. The bug is truly severe: not only does the library stop working,…
CONTINUE READING 🡒 Protecting MikroTik. How to make your router safe
Firmware of popular routers often contains errors identified by security researchers on a regular basis. However, it is not enough just to find a bug - it must be neutralized. Today, I will explain how to protect…
CONTINUE READING 🡒 The deplorable four. Testing free antiviruses: Huorong, Preventon, Zoner, and…
Today, I am going to battle-test four antivirus programs: a British one, a Chinese one (featuring an original engine), a Finnish one, and an exciting Czech project at the beta-version stage. All of them are free and…
CONTINUE READING 🡒 The weakest link. Phishing emails as a pentesting tool
Conventional wisdom holds that the most vulnerable component of any computer system is its user. Humans may be inattentive, unthoughtful, or misinformed and easily become victims of phishing attacks. Accordingly, this weak link must be tested for…
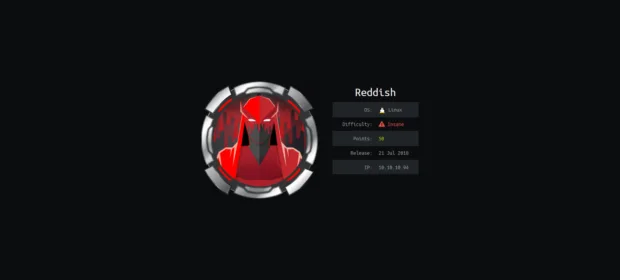
CONTINUE READING 🡒 Diabolically reddish pentest. Building tunneling chains through docker containers on…
How to seize control over a host located in a different subnetwork? The right answer is: build numerous intricate tunnels. This article addresses tunneling techniques and their application in pentesting using as an example Reddish, a hardcore…
CONTINUE READING 🡒 Hack the web! Checking web sites for vulnerabilities and exploiting…
Hacking web sites is one of the most common attack types. This article is dedicated to such attacks and protection against them. I will address the pentesting basics for web applications and explain how to deal with…
CONTINUE READING 🡒 DDoS attacks on Bluetooth. How to disable annoying portable speakers
Gangs of teenagers with portable Bluetooth speakers playing loud music drive me nuts. Today, I will explain how to neutralize this 'natural disaster' without (OK, almost without) committing a criminal offense.
CONTINUE READING 🡒 Solar stroke. Two severe vulnerabilities in Apache Solr
Not long ago, researchers have discovered two severe vulnerabilities in Apache Solr, a popular open-source full-text search platform. The first bug relates to incorrect handling of Velocity templates, while the second one originates from the DataImportHandler module.…
CONTINUE READING 🡒 Over-the-air tricks. Simple and effective Wi-Fi pentesting techniques
In this article, I will demonstrate a few simple and common -although efficient! - Wi-Fi pentesting tricks: hiding your MAC address when you scan a network and attack WPA2, identification of 'hidden' networks, bypassing MAC filtering, and…
CONTINUE READING 🡒 Attacking Active Directory. An overview of actual privilege escalation techniques
Compromising a domain controller involves more than just finding a known vulnerability, stealing user credentials, or identifying an error in the security policy settings. The above 'achievements' grant only the minimum access level that may be insufficient…
CONTINUE READING 🡒 Lateral movement in Active Directory. Offensive techniques used to attack…
Imagine that you have successfully retrieved users' accounts in a network with an Active Directory domain controller and escalated your privileges. But what if you control not the entire network, but just a small segment of it?…
CONTINUE READING 🡒 Hacker’s toolbox 2020. Pentesting devices you should have at hand
HackMag selected fifteen devices enabling you to pentest everything: from mechanisms to contactless cards. This list does not include trivial tools, like screwdrivers and soldering irons, because everybody chooses them individually. Hopefully, this toolkit would be useful…
CONTINUE READING 🡒 Cyberdolphin. The story of Flipper — hacker’s Swiss Army knife
Hacking and pentesting are normally associated with hours-long sitting at your computer, but this is not quite so: many devices and wireless networks can be accessed only personally. In such situations, you need a hacking multitool -…
CONTINUE READING 🡒 Wi-Fi total PWN. Mastering actual Wi-Fi pentesting techniques from scratch
The best way to check the network's security is by trying to hack it. In the past, HackMag had published materials about auditing Wi-Fi networks. Unfortunately, such guides quickly become obsolete. Today, I will share some practical…
CONTINUE READING 🡒