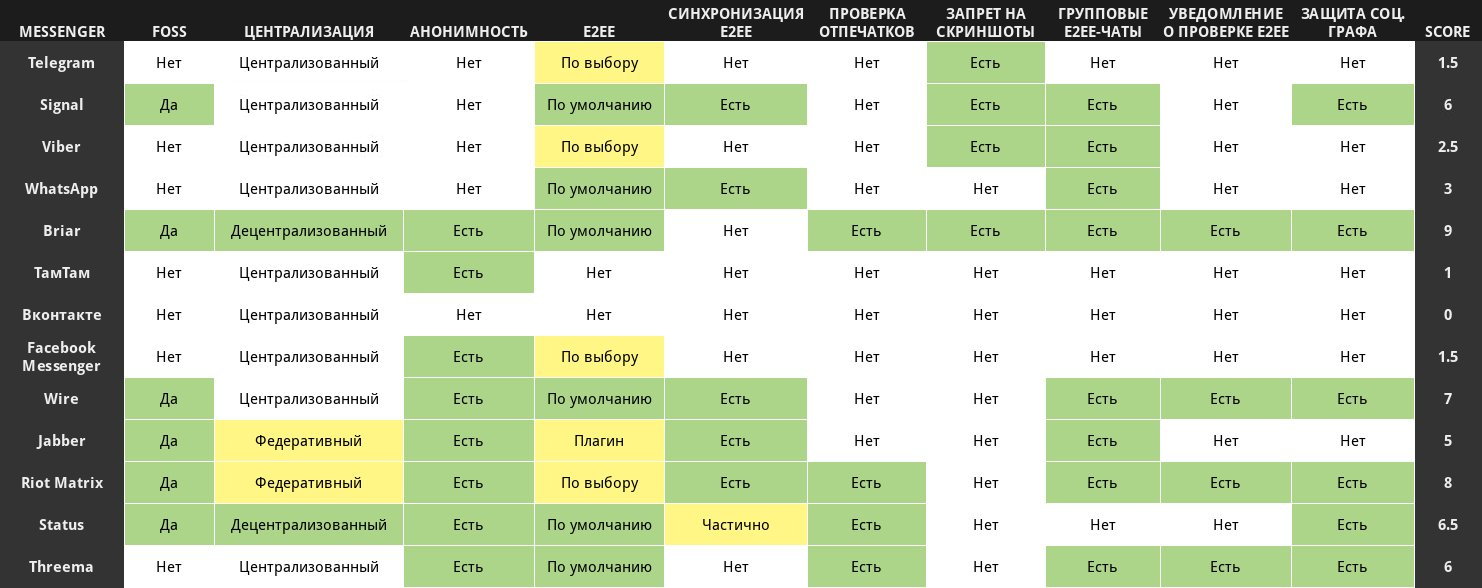
We have put together a list of messaging apps to evaluate how each handles security. This selection includes both popular apps and those with promising security features. Be advised that we will delve into the technical aspects only as much as necessary for the average user, no further.
In many ways, we followed the approach of the authors of the Electronic Frontier Foundation’s series of articles titled Secure Messaging Scorecard, but we chose different criteria that we believe are more important.
Criteria
FOSS
Is the source code of the messenger distributed under one of the open-source licenses? If so, is the development conducted in an open manner? How closely do the developers interact with the community? Do they accept pull requests? All of these factors are important to consider when making a choice.
Degree of Centralization
Here, there are three possible options:
- Centralized — Requires a server, can potentially be blocked. Examples: VK, Telegram, Facebook;
- Federated — A network of servers that communicate with each other. Notable examples: Email, Jabber (XMPP), Riot Matrix;
- Decentralized (meaning P2P) — Every client simultaneously acts as both a client and a server.
Anonymous Registration and Usage Options
For some services, a phone number might only be needed to protect against spam during registration, making it quite easy to use temporary or rental phone number services for SMS verification.
In other cases, the messenger is closely tied to the phone. This is problematic because if two-factor authentication isn’t enabled, gaining access to that phone number could allow someone to enter the account and extract all data. Even if two-factor authentication is enabled, there’s still a possibility of deleting all data from the account. Moreover, it’s effectively like registration with a personal ID (considering Russian realities, as other options aren’t available).
Not everything is grim. There are messaging apps that allow you to register using an email address or social media account. There are even some where you can create an account directly in the messenger without linking it to anything else.
End-to-End Encryption (E2EE) Availability
Some messaging apps have this feature enabled by default, in others it can be turned on, but there are also those that simply do not offer end-to-end encryption.
End-to-End Encrypted Chat Synchronization
This feature is still not as common as we would like, but having it makes life significantly easier.
Notification on the Need to Verify E2EE Fingerprints
When initiating E2EE (end-to-end encrypted) chats, some messengers offer the option to verify the fingerprints of your contacts, while others do not make this option as explicit. However, not all messengers have the capability to verify fingerprints.
Disabling Screenshot for Secret Chats
It’s not the most useful feature, because to bypass the restriction, you just need to have a second phone handy.
Group E2EE Chats
Group E2EE (end-to-end encrypted) chats might not always be essential, but they are certainly convenient. The rule “more than two, speak out loud” is best left for kids.
Alert: Verify E2EE Fingerprints in Group Chats
When adding a new contact whose fingerprints haven’t been verified to a secret group chat, not all messaging apps offer the option to check their fingerprints. This oversight undermines the purpose of having secret chats.
Protecting Your Social Graph
Some messaging apps collect information about a user’s contacts and other data, such as whom the user has called and for how long they talked. There’s an interesting article on this topic.
www
We selected only a few of the criteria that may influence the choice of a messenger. There are others as well, though not all are directly related to security. A group of researchers from European universities did a great job organizing them in the paper Obstacles to the Adoption of Secure Communication Tools (PDF). It’s also always helpful to review the results of an independent audit, if available. For example, Signal underwent such an audit (PDF).
Telegram
License: Formally, it’s GPLv3. However, a significant portion of the development is closed. A look at the repositories reveals that recently there has been activity primarily in the web version, suggesting an illusion of openness.
Degree of Centralization: Centralized
Anonymous Registration and Usage: No
Availability of E2EE: Implemented, but as an add-on. By default, chats are not encrypted.
Synchronization of E2EE Chats: No. A secret chat can only be used from one device, so it cannot be accessed from another.
Notification of E2EE Fingerprint Verification: No. Users can manually check settings to compare fingerprints.
Screenshot Restriction for Secret Chats: Available, though not on all devices.
Group Chats E2EE: No
Social Graph Protection: No
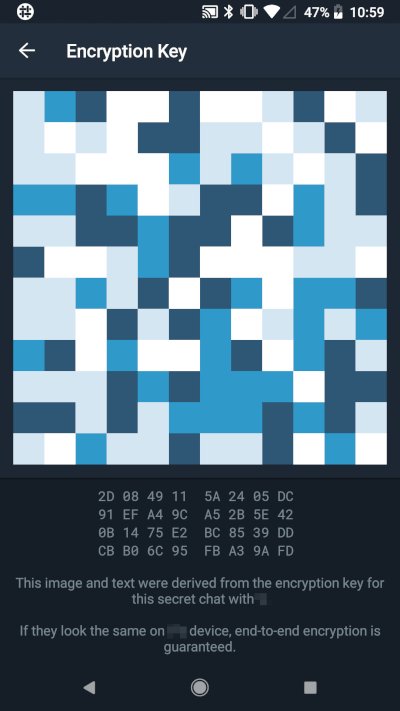
The messaging app developed by Pavel Durov’s team is built on the MTProto encryption protocol. Currently, it is partially blocked in Russia, but that is a separate topic altogether.
The messenger is controversial. There’s a lot of buzz around it, but is it justified? There’s no access to the source code, chats aren’t encrypted by default, and there’s no protection for your social graph (all your contacts are stored on Telegram’s servers). It lacks group E2EE (end-to-end encrypted) chats, E2EE chats aren’t supported in the desktop version, only on mobile. The messenger is centralized, messages are stored on the server (and, as noted, they’re not encrypted), and there’s no option for anonymous registration.
If you want to use Telegram while ensuring your conversations are secure, be sure to create secret chats. In the mobile version, you can do this by selecting “New Secret Chat.” However, keep in mind that among the desktop versions, only some support secret chats (for example, one of the two clients available for macOS).
In a secret chat, messages are encrypted and not stored on the messenger’s servers. You also cannot take a screenshot of a secret chat, but nothing prevents you from taking a photo of the chat on your screen.
Signal
- License: AGPLv3
- Degree of Centralization: Centralized
- Anonymous Registration and Use: Not available. A phone number is required, with no alternative options.
- Availability of E2EE: Yes
- E2EE Chat Synchronization: Yes
- Notification for E2EE Fingerprint Verification: No. Users are advised to scan each other’s QR codes or compare fingerprints.
- Secret Chat Screenshot Restriction: Can be enabled or disabled.
- Group Chats with E2EE: Yes
- Notification for E2EE Fingerprint Verification in Group Chats: No
- Social Graph Protection: Yes
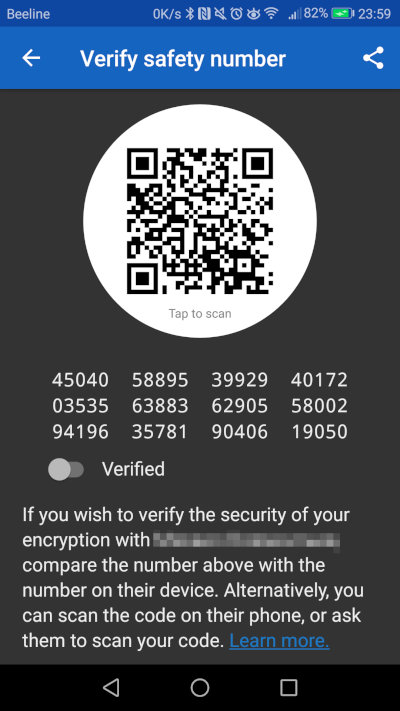
The Signal messenger was developed by the American startup Open Whisper Systems, which, besides its two founders, employs only a few people. For message encryption, it uses a cryptographic protocol designed specifically for it — the Signal Protocol. This protocol is utilized for end-to-end encryption of calls (both voice and video), as well as standard messages. Since then, other messengers have adopted the Signal Protocol, including WhatsApp, Facebook Messenger, and Google Allo.
It might seem that any messenger could be as secure as Signal. However, in practice, this is not the case. Unlike Signal, where encryption is enabled by default, other messengers have it turned off. In Facebook Messenger, you need to activate Secret Conversations, and in Google Allo, you have to enable Incognito Mode to get encryption.
Although Signal is centralized, its code is open and distributed under a free license. Signal supports group E2EE chats, protects the social graph, and includes disappearing messages that are erased on a timer.
However, don’t confuse security with anonymity. Signal is not anonymous: you must provide a phone number during registration, which the messenger is linked to. As for disappearing messages, this feature is also available in other messaging apps, such as Viber and Telegram (in the secret chat menu, you need to select the command ‘Set self-destruct timer’).
Viber
License: Proprietary
Degree of Centralization: Centralized
Anonymous Registration and Usage: Available only via phone number
E2EE Availability: Enabled by default. Secret and hidden chats provide additional security
Synchronization of E2EE Chats: Not available. A secret chat created on the mobile version does not appear on the desktop version
Notification for E2EE Fingerprint Verification: Not available
Screenshot Restriction for Secret Chats: Enabled
E2EE Group Chats: Available
Notification for E2EE Fingerprint Verification in Group Chats: Not available
Social Graph Protection: Not available
 |
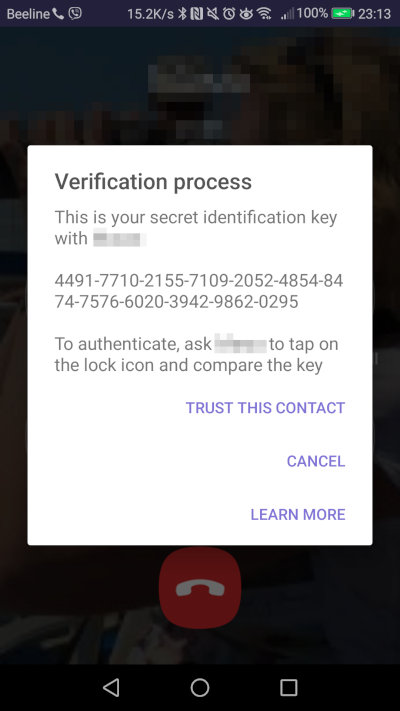 |
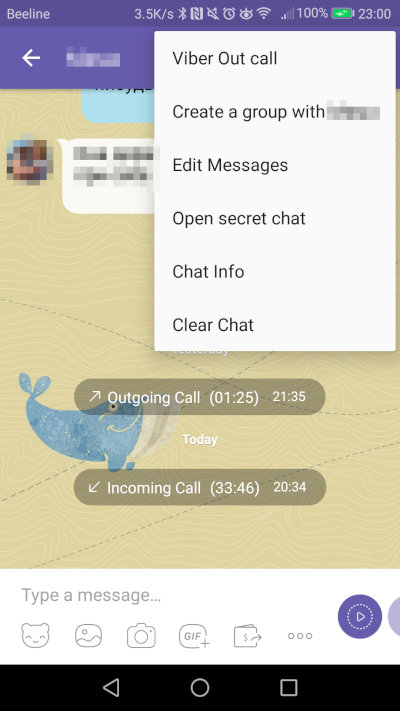
Viber is an intriguing messaging app. On one hand, it is proprietary, centralized, and only ties to a phone number, not offering protection for the social graph. On the other hand, it features end-to-end encryption based on the Signal protocol and is enabled by default, even in the desktop version. For additional security, there are secret chats with the option for group communication.
Secret chats allow you to set a self-destruct timer for each message: it will be deleted after a specified time once viewed—both from your device and from all recipients’ devices. Messages in a secret chat are protected from being forwarded, and taking screenshots is either blocked or will leave a notification in the chat.
To start a secret chat, open a chat with the user and select the “Start Secret Chat” option from the menu. This chat will be marked with a lock icon.
Additionally, Viber allows users to create hidden secret chats. To access such a chat, you need to enter a previously set PIN code. This serves as an extra layer of protection in case the phone falls into the wrong hands.
To verify fingerprints, it’s suggested to make a call to the person you’re communicating with, provide your identifier, and then confirm its accuracy. However, there’s no notification indicating that this is necessary for ensuring your own security.
License: Proprietary
Degree of Centralization: Centralized
Anonymous Registration and Operation Capability: Only via phone number
Presence of E2EE (End-to-End Encryption): Enabled by default
Synchronization of E2EE Chats: Available
Notification for E2EE Fingerprint Verification: Only if there’s a key change by the contact. To receive notifications, you need to go to settings and enable this feature. No notifications are provided at the start of a chat.
Prohibition of Screenshots in Secret Chats: No
Group Chats with E2EE: Available
Notification for E2EE Fingerprint Verification in Group Chats: Not available
Protection of Social Graph: No
 |
 |
WhatsApp uses the Signal Protocol, but this alone doesn’t provide any guarantees. Of course, the app is notable for not storing your messages on its servers. Instead, messages are stored on your phone or in cloud services it syncs with (such as iCloud). Additionally, end-to-end encryption (E2EE) is enabled by default and supports group chats.
Although WhatsApp doesn’t access the actual content of the messages, its owners can access metadata, including collecting phone numbers from the address book, the time messages and calls are sent, and more. Imagine you made a call to a phone sex service at 2:30 AM that lasted 24 minutes. Sure, no one knows the specifics of the conversation, but in this case, such details aren’t necessary.
In addition, WhatsApp collects a vast amount of user information, including the phone model, operating system, data from the browser, IP address, mobile number, and more.
Add proprietary code into the mix, and you’ll end up with a solution that is far from ideal for anonymity. While your messages might not be intercepted, the messaging app itself will know a lot about you.
Briar
License: GPLv3
Level of Centralization: Decentralized
Anonymous Registration and Operation: Supported
Availability of E2EE (End-to-End Encryption): Enabled by default
Synchronization of E2EE Chats: Not available
Notification for E2EE Fingerprint Verification: When adding a contact, you must scan the contact’s QR code from their phone’s screen; there is no alternative method to add them. This is considered a notification.
Prohibition on Screenshots of Secret Chats: Implemented
Group Chats with E2EE: Supported
Notification for E2EE Fingerprint Verification in Group Chats: You can only add a contact to the group chat if their QR codes have already been verified. This is also considered a notification.
Social Graph Protection: Implemented
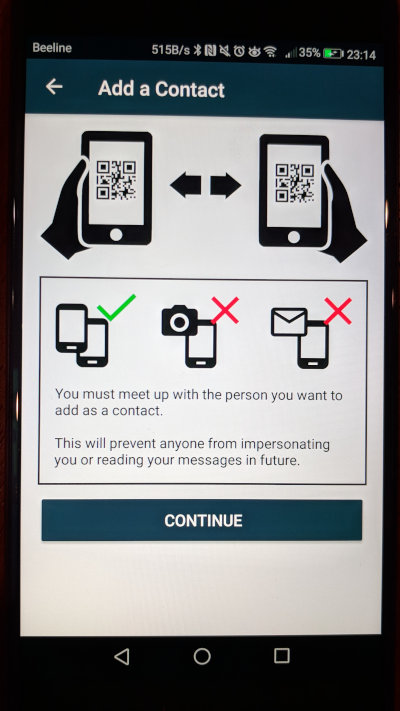
Briar is not a very popular messenger; some of our readers might not even be familiar with it. However, it is quite effective. It is based on decentralized mesh network technology and can operate directly via Bluetooth or Wi-Fi, or through the internet, connecting via Tor in the latter case.
The source code for Briar is open, allowing for anonymous registration and use. Chats are encrypted by default and are not stored on Briar’s servers—your encrypted messages are stored only on your phone. There is social graph protection (your contact list isn’t shared with anyone), and group E2EE (end-to-end encrypted) chats are supported. However, there’s no E2EE chat synchronization across devices, as it’s not possible to use the same account on multiple devices.
Among all the other messengers, Briar stands out quite well if you’re looking for communication anonymity. However, it does have some drawbacks: there’s no version for iPhone and no voice call capability. While the lack of calls might be something you can live with, the absence of support for one of the major platforms significantly limits its user base.
TamTam
License: Proprietary
Degree of Centralization: Centralized
Option for Anonymous Registration and Use: Registration is possible using a Google email account or via “Odnoklassniki”
End-to-End Encryption (E2EE) Availability: No
Protection of Social Graph: No
When “TamTam” was created, security was not a priority, and this should be kept in mind. The only attention it might garner is through the ability to register via Google mail or “Odnoklassniki.” However, message encryption is not supported (or the developers have not mentioned it), and there’s no protection for the social graph. In other words, no matter how you register, without additional precautions, your identity can still be apparent. Overall, this messenger is not suitable even as a replacement for “Telegram,” despite the developers’ intentions.
VKontakte
License: Proprietary
Level of Centralization: Centralized
Anonymous Registration and Use: Phone number required
End-to-End Encryption (E2EE) Available: No
Social Graph Protection: No
Once again, let’s skip it: it’s unlikely that anyone in their right mind would consider using “Vkontakte” for anonymous communication. Messages are stored on the social network’s servers, they’re not encrypted, and registration is only possible with a phone number — basically, all the things we’re trying to avoid here.
Facebook Messenger
License: Proprietary
Level of Centralization: Centralized
Anonymous Registration and Usage: Available. Registration on Facebook is possible via email, and Messenger access requires a Facebook account.
Availability of E2EE: Yes, but not enabled by default
E2EE Chat Synchronization: No
Fingerprint Verification Notifications for E2EE: No. However, users can manually compare each other’s fingerprints.
Screenshot Blocking in Secret Chats: No
E2EE Group Chats: No
Social Graph Protection: No
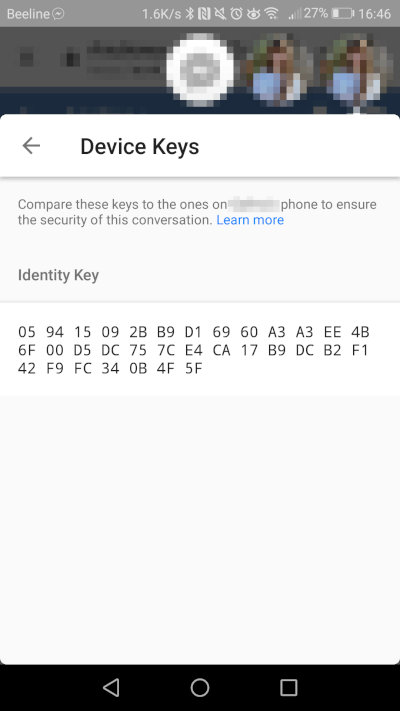

The messenger associated with Facebook is built on the open MQTT protocol. Just to clarify, this is specifically a messaging protocol—not to be confused with an encryption protocol. After Messenger was separated into a standalone app on mobile phones, Facebook users had little choice but to install it as well. However, you can register for Messenger without having a Facebook account.
When comparing chats in VKontakte and Facebook Messenger, the latter is significantly superior. Firstly, you can register with an anonymous email. Secondly, it supports E2EE (end-to-end encryption) chats, although not by default. To enable message encryption, you need to activate Secret Conversations.
However, keep in mind that Facebook collects a vast amount of information about its users, making it less suitable for anonymous communication. Additionally, end-to-end encrypted (E2EE) chats and many other useful features aren’t supported (see above). If you’re interested in what information Facebook gathers, read their privacy policy. If you don’t have an account, you can view it as a screenshot.
Wire
License: GPLv3
Degree of Centralization: Centralized
Anonymous Registration and Usage: Available. Via email
Presence of E2EE: Yes, by default
Synchronization of E2EE Chats: Supported
Notification on E2EE Fingerprint Verification: Not by default, but possible
Prohibition on Screenshots of Secret Chats: No
Group E2EE Chats: Available
Notification for E2EE Fingerprint Verification in Group Chats: Available. If a user sends a message from an unverified device in a secret group chat, a warning will appear to others when they try to send messages, alerting them of the first user’s new device
Protection of Social Graph: Yes
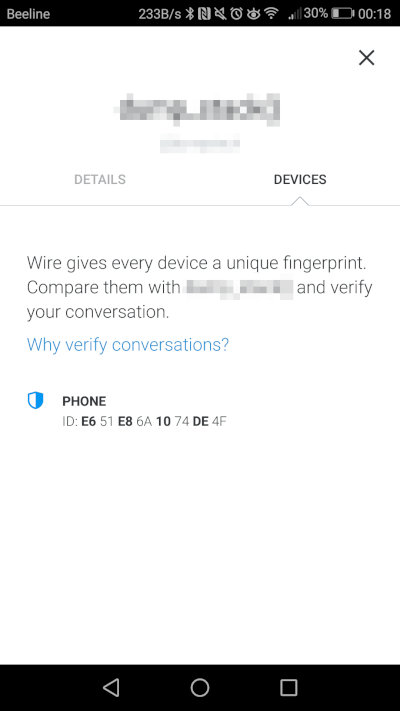
Wire is among the most anonymous messaging apps. It is built on the Wire Swiss protocol, which is based on Signal. What makes it stand out? Firstly, it offers anonymous registration. Secondly, it provides end-to-end encryption by default, with the ability to sync encrypted chats. Thirdly, it protects your social graph, supporting encrypted group chats (up to 128 members) and secure conference calls (up to ten people). Similar features are found in Briar, but Wire also boasts extensive platform support, including Android, iOS, Windows, macOS, and Linux.
Is there a downside? Let’s assume there is one: unlike Briar, Wire is not decentralized and is backed by a small Swiss startup (and, as we know, startups can be here today and gone tomorrow). The developers plan to generate revenue by selling a corporate version and competing with Slack. The subscription costs 6 euros per month or 4 euros with an annual payment. We can only hope that this model will truly allow the company to maintain a free, high-quality, and anonymous messenger.
Jabber (OMEMO)
License: Various open-source licenses
Level of Centralization: Federated
Anonymous Registration and Use: Available. Register using an email address, Facebook, or Twitter account
End-to-End Encryption (E2EE) Availability: Yes. Requires OMEMO extension
Synchronization of E2EE Chats: Yes
E2EE Fingerprint Verification Notification: No notifications, but the option is available
Ban on Screenshots of Secret Chats: No
Group Chats with E2EE: Yes
Notification for E2EE Fingerprint Verification in Group Chats: No
Protection of Social Graph: No
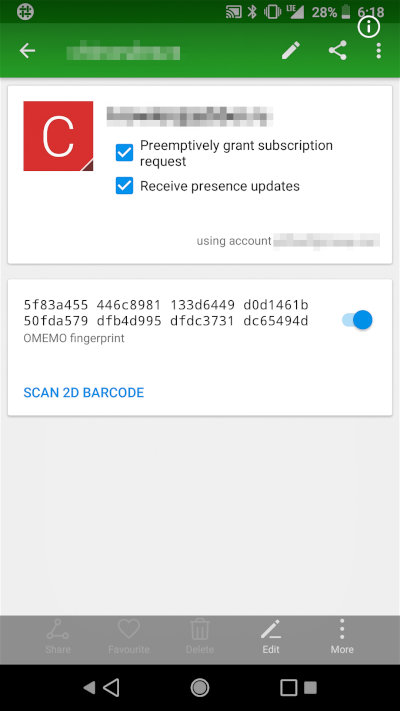
While Jabber might not keep up with modern messengers full of playful stickers and voice calls, it remains invaluable for privacy. It’s federated, supports anonymous registration, and offers end-to-end encryption (E2EE) with the OMEMO extension, including for group chats. Its features may not be groundbreaking, but Jabber is time-tested and available across all possible platforms. Options include ChatSecure for iOS, Conversations for Android, Pidgin for Linux, and more, making the list extensive.
Riot (Matrix)
License: Apache
Degree of Centralization: Federated
Anonymous Registration and Usage: Available
End-to-End Encryption (E2EE): Available, user-selectable
Synchronization of E2EE Chats: Available
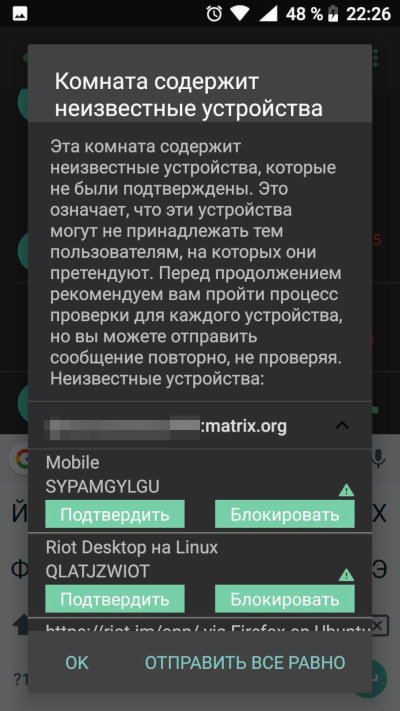
Notification for E2EE Fingerprint Verification: Available
Screenshot Protection in Secret Chats: Not available
Group Chats with E2EE: Available
Notification for E2EE Fingerprint Verification in Group Chats: Available
Social Graph Protection: Available
The creators of this messenger certainly have a knack for coming up with cool names. Matrix is the communication protocol, while Riot is the client application (other options are available, including console-based applications). You can use either the web version or apps for iOS and Android.
Overall, this is another lesser-known federated messenger that supports end-to-end encrypted (E2EE) chat synchronization, including for group chats. Registration is anonymous and does not require linking to a mobile phone number or email. It also supports voice calls and video calls.
In Riot, you can enable or disable message encryption—the presence of a lock icon next to the message input field serves as an indicator. Additionally, if a user joins a secret group chat and their devices have not been verified by other users, participants will receive a notification about this when attempting to send a message.
Overall, Matrix seems like an interesting option, but its novelty combined with having its own protocol might be a bit concerning.
Status
License: MPLv2
Degree of Centralization: Decentralized
Anonymous Registration and Operation: Supported
End-to-End Encryption (E2EE) Available: Enabled by default
Synchronization of E2EE Chats: Partial (see description)
Notification for E2EE Fingerprint Verification: Available. To start a conversation with a user, you must enter their ID or scan it from the smartphone screen.
Screenshot Restriction in Secret Chats: None
E2EE Group Chats: Not available
Social Graph Protection: Available
Status is more than just a messenger. Sure, you can use it solely for communication, but that’s akin to installing Windows just to use Notepad. Communication isn’t exactly smooth here—you can’t even send pictures, let alone something as fancy as stickers. However, it does allow you to send ETH and create requests for receiving it directly within the chat.
The app is currently in the beta-testing phase, so bugs are to be expected. We installed Status on two phones (both running Android). On one phone, the app worked fine, but on the other, the authorization kept failing, requiring the password to be entered each time the messenger was accessed (basically, after each screen lock) — not very convenient.
Sometimes it’s hard to tell whether you’re facing a bug or an undocumented feature. When we created accounts on both phones (which requires nothing more than entering a name) and scanned the QR code on one phone’s screen with the other, a completely unfamiliar name, “Puny Moral Gonolek,” appeared on the second phone. Only after adding the user to the contacts did the name display correctly. Meanwhile, the name of the first participant consistently displayed correctly throughout.
Since there is an option for anonymous registration and all chats are encrypted by default, each chat in Status can be considered secure. There is also synchronization for secure chats, but only incoming messages will be synchronized; messages sent from one account on different devices will not be.
Another potential drawback is that messages are stored both on your phone and on the messenger’s server, though developers assure they are encrypted. However, your contact book is not uploaded to the messenger’s servers, which is a valuable privacy feature these days. Overall, there is security in place, and the ability to transfer cryptocurrency might appeal to some. However, Status is still more of an interesting novelty than a practical tool.
Threema
License: Proprietary for applications, AGPLv3 for the web client
Degree of Centralization: Centralized
Ability for Anonymous Registration and Use: Available. You can create an account without linking it to a phone number or email. A unique ID is assigned to the user, which can be changed.
Presence of E2EE (End-to-End Encryption): Available by default
Synchronization of E2EE Chats: Partial (see description)
Notification of E2EE Fingerprint Verification: Available. Messages in group chats are sent individually to each participant, and you can start a conversation only with those whose identifier is verified.
Ban on Screenshots of Secret Chats: No
Group Chats with E2EE: Available
Notification of the Need for E2EE Fingerprint Verification in Group Chats: Available
Protection of Social Graph: Available. The address book is not uploaded to the server by default, but users can allow access to it if desired.
Threema is a proprietary centralized messaging app with servers located in Switzerland. In addition to text messaging, it offers users voice calls, location sharing, voice messages, and file transfers. Group chats are supported for up to 50 participants.
Messages here are fully encrypted and decentralized on the user’s devices, rather than on Threema’s server. The server acts more like a switchboard: messages are transmitted through it, but not stored permanently. For detailed information on what data is stored and for how long, you can read the FAQ.
Registration does not require providing any personal information that could lead to identification—neither a phone number nor an email. Upon the first launch of the program, a user ID is randomly generated, and a QR code is created based on it. All of this ensures anonymous communication.
To initiate a conversation with a contact, you need to enter their ID. Threema offers three levels of trust for user identification. The highest level is achieved by scanning the ID from the smartphone screen, while the lowest is when entering it manually. Contact synchronization falls somewhere in the middle. The verification level for each contact is displayed as dots next to the contact’s name.
Unlike WhatsApp or Facebook Messenger, Threema does not log who is communicating with whom or store user address books on its servers. All messages are stored in an encrypted form on the user’s devices. The method of encryption depends on the device: iOS uses iOS Data Protection, while Android and Windows Phone use AES-256. Messages, images, and other data transmitted between users are encrypted. Additional details are available in the whitepaper (PDF).
Even though each chat is encrypted and can be considered secure, there are also private chats. These are protected by a PIN code and marked with an icon featuring a hat and glasses. We’ve seen something similar in Viber.
Overall, Threema makes a good impression. Messages cannot be decrypted—even by court order—because they are stored only on the phone, and Threema does not have access to users’ secret keys. Threema’s servers know only who sends the message and to whom, but they do not log this information and cannot decrypt the message’s content.
Let’s move on to the drawbacks. Firstly, there’s the necessity to pay. A one-time fee of 2.6 euros isn’t much, but the mere fact of having to pay might be undesirable. Secondly, there’s a rather complicated situation with chat synchronization: while you can sync messages between the web and phone versions, logging into the same account from two phones is not possible. Each device is assigned a unique ID, meaning you can only transfer logs to another device through a backup.
Summary
We won’t be recommending any specific messenger. We’ve provided you with all the necessary information, and the choice is yours, especially since there are plenty of options to choose from.