I2P is built as an overlay: an anonymous, secure layer that runs on top of another network—the Internet. One of I2P’s defining features is its decentralization. The network has no DNS servers; instead, it uses automatically updated “address books.” Addresses are cryptographic keys that don’t reveal the underlying machines. Any user can obtain their own key, and it cannot be traced.
Many users often wonder why use I2P when VPNs and Tor are available. Compared to the Tor Browser, I2P differs in the following ways:
- Tor uses “onion” routing, sending your traffic through the proverbial eight proxies, but on its own it doesn’t inherently prevent decryption. I2P, by contrast, relies on encrypting the traffic.
- Tor is a big fan of SOCKS, whereas I2P prefers to use its own API. Which is more convenient is up to you.
- I2P tunnels are one-way, unlike Tor.
- Tor, despite having some peer-to-peer traits, is still centralized. I2P is fully decentralized.
These are just the key differences between I2P and Tor. Even based on those alone, you can confidently say that I2P is the more secure and anonymous option. Comparing I2P to a VPN yields a similar picture: a VPN is only as reliable as its provider or hosting company.
Hacker has already covered how I2P works in the article “Unveiling the Secrets of the I2P Network,” so we won’t dwell on the technical implementation and will jump straight into the promised journey. But first—let’s gather our gear.
This Isn’t Tor
Tor and I2P have one thing in common: you can’t access their resources without additional software. With Tor it’s straightforward—download the browser and you’re good to go—whereas I2P is trickier for the average user. Here’s what you’ll need.
- Java. Download the Windows version from https://www.java.com/ru/download/windows-64bit.jsp and install it.
- Get the official installer from the I2P site: http://www.i2p2.de/download_ru. Pick the one that matches your OS and install. The list even includes Android.
- On Windows, go to Start → All Programs → I2P and choose “Start I2P (no window).” On Linux, you probably know the drill.
- Next, open a browser, for example Firefox. Go to Settings/Options → Advanced → Network → Proxy settings (Use a proxy). Fill in the fields as shown in the screenshot.
- If the I2P console page doesn’t open automatically, open it manually: http://127.0.0.1:7657/home.
Great! You’re all set to explore the I2P network. Later, you can enable automatic fetching of personal link libraries pointing to I2P resources—this will make navigation easier.
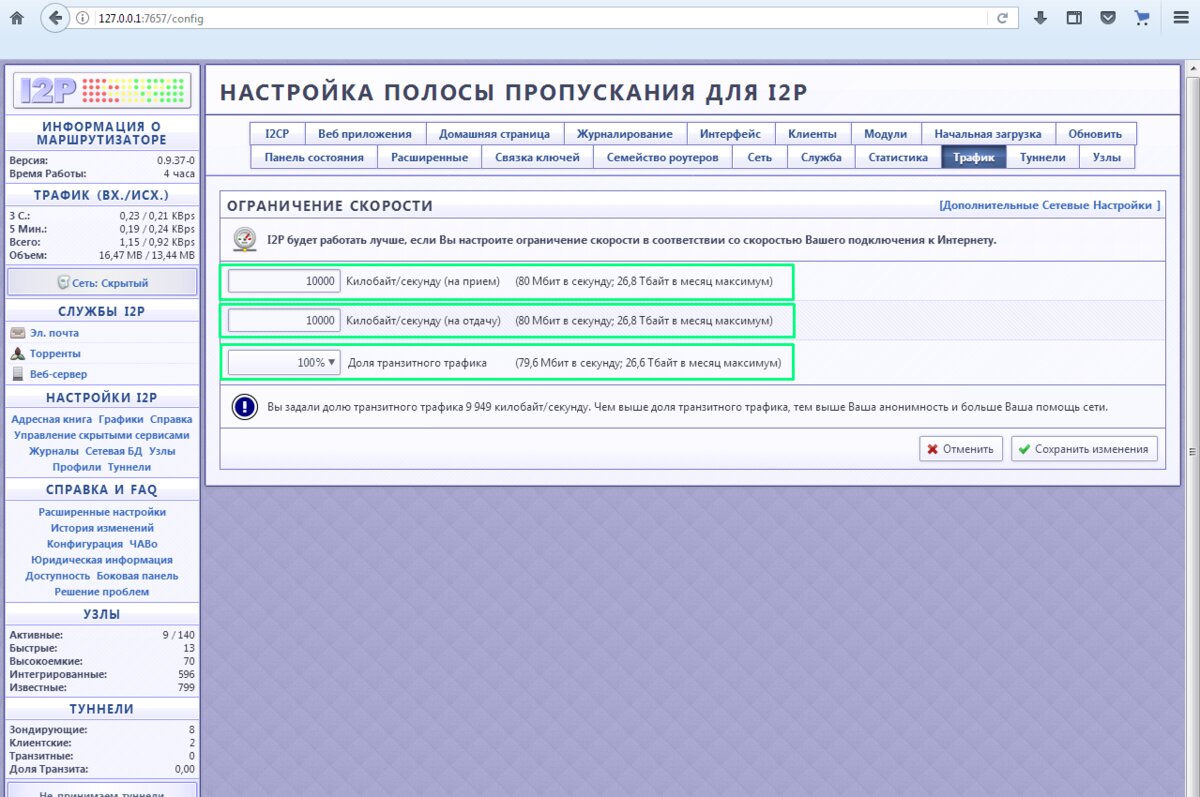
И one more optional step. You can go to the “Трафик” section, set the share of transit traffic to 100%, and increase the per‑second upload and download kilobytes to the maximum—as shown in the screenshot. In practice, this reduces network latency.
All right, come on in—shoes off, make yourself at home. Just don’t take off your gloves; leaving fingerprints here is strictly forbidden.
What you’ll find on I2P
The I2P ecosystem isn’t as rich as Tor’s onion landscape. Still, if you know where to look, there’s plenty to find—useful, unsettling, and just plain interesting.
Blogs, imageboards, and forums
The first place worth visiting is the Hidden Answers forum. Fans of Onion services will find it familiar—maybe even a bit like home. People ask all kinds of questions there, from “Who’s your favorite YouTuber?” to “How do you get an abortion?” Answers come from regular users. Sure, they’re not always good or even on-topic, but there’s plenty of interesting content. There’s also a Russian-language counterpart called SecretChat.
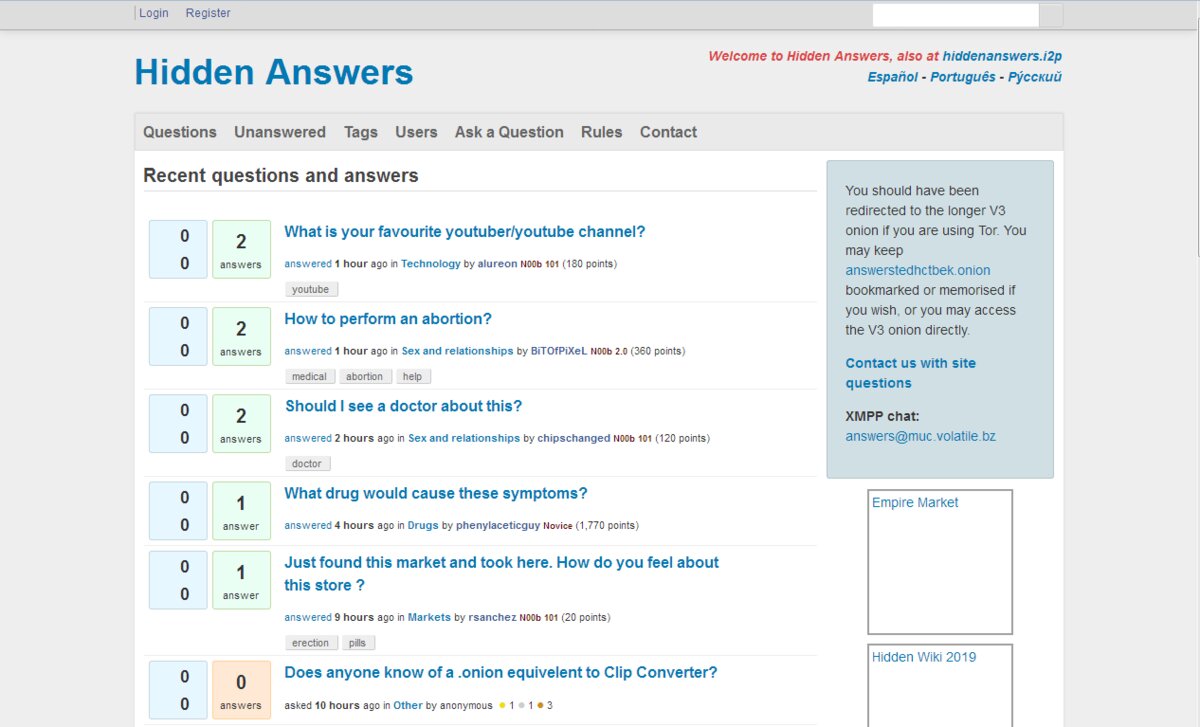
On I2P, people love to set up their own blogs where they share all sorts of information and viewpoints. They generally write about topics that they’re hesitant to discuss openly on the clearnet.
There are also some head-scratchers: for example, on rebel.i2p random, content-free images just cycle endlessly. And of course there are adult sites, but you won’t find anything new there—especially if you’re actually an adult.
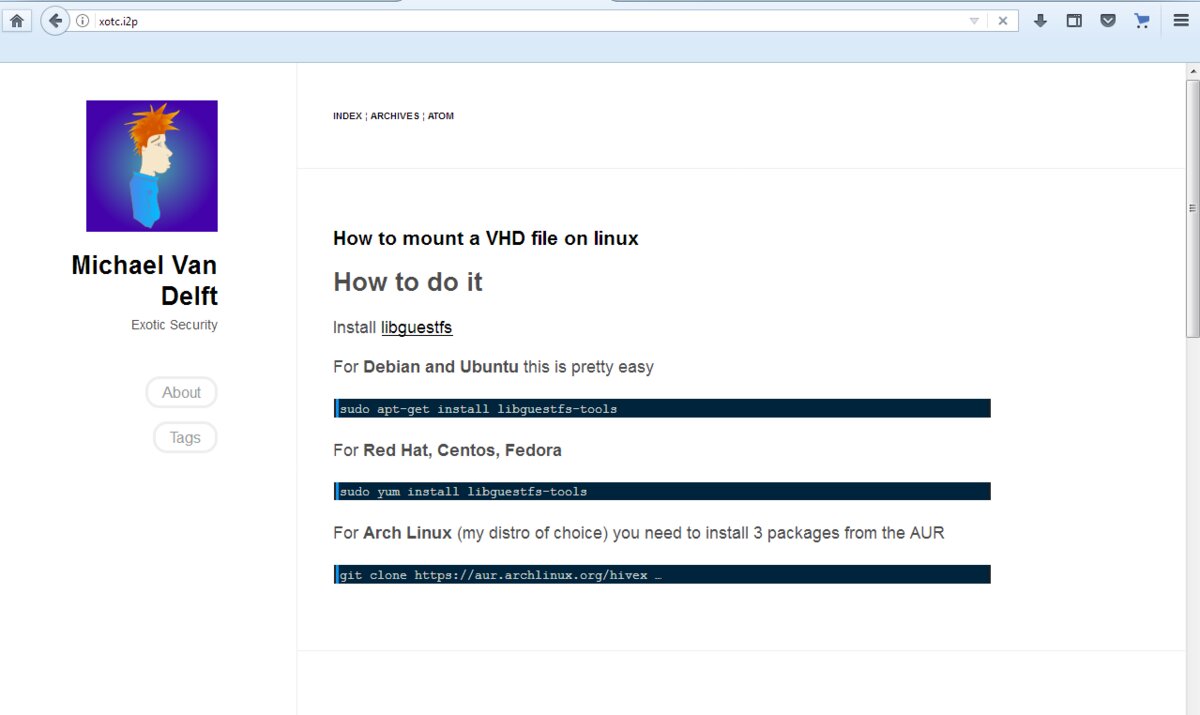
A good example of a useful blog is Michael van Delft’s page titled Exotic Security. There, Michael shares insights into truly exotic approaches to network security and discusses handy features for developers. For instance, he covers topics like reflashing MacBook firmware and other intriguing subjects.
Any underground network is expected to have its own board where people can talk about anything. I2P is no exception to this tradition and offers a place called F*ck Society. It has subforums on various topics, including a Runion presence. You’ll find threads about illegal substances, violence, politics, and other darknet staples.
Continuing our look at anonymous social networks, we come across Onelon. Think of it as an unrestricted Facebook: you can post whatever you want, to whomever you want, for whatever purpose. People in the .onion space have known about Onelon for at least a few years. The I2P version is almost the same—similar threads and similar comments. That said, the onion version is much more popular.
Communication
Among the useful services available on I2P, it’s worth mentioning vPass, which helps you generate a domain-specific password, and EasyGPG, which creates a personal GPG key for you. In practice, most of I2P’s practical resources can be easily found on .onion and even on the clearnet.
For example, XMPP (Jabber) servers like Echelon and anonymous, decentralized email systems like I2P Bote won’t impress anyone but complete newcomers these days. Still, it’s useful to know they exist.
Marketplaces
And of course, I2P has its own marketplaces. Where .onion has Hydra, I2P has nvspc. Their payment and fulfillment models are similar, and both offer clearnet access. Note that nvspc can also function as a cryptocurrency exchange. It’s also worth mentioning Garden—not a paradise garden, but a marketplace similar to WayAway on .onion.
When it comes to the arts, I2P has a few things too—for example, the streaming platform StreamRadio and Radio Anonymous. But whether anyone actually needs anonymized music is a nontrivial question.
Directories
I2P has its own “Russian I2P Wiki.” The goal of this wiki is to help the I2P project grow by letting users anonymously edit existing articles, somewhat reminiscent of the popular Lurkmore. Among other things, there’s a page with links to interesting resources.
Don’t forget about Eepsites, a link directory. Directories in I2P could be a useful resource, but unfortunately most of the links are dead.
Book Bazaars
Flibusta has also set up shop on I2P and is running smoothly. Beyond the massive libraries with millions of books we’re used to, I2P also offers more niche collections. For example, the owners of “Extreme Chemistry” curate manuals with experiments you could (but really shouldn’t!) try at home or in a garage. As educational entertainment, it’s quite interesting. “Fantasy Worlds” is another narrowly focused library: if you love diving into magical worlds, I2P will please you here doubly.
File Sharing
I2P has a ton of file-sharing services. Where else can you swap files this safely and anonymously? Maybe only in real life—and even that’s debatable. I2P includes the well-known “Схоронил” and plenty of underground spots like Serien. People share via torrents too—check out the RuTor mirror or the Public Torrent Tracker. There’s even a mirror of the “Orthodox Torrent.”
Crime
While the clearnet and .onion are packed with hacking and carding forums, scammers, and fraudsters, the scene on I2P is much smaller. Even the largest crime-focused onion sites often avoid moving to I2P, preferring to stick with easier access paths for users. On I2P, criminal sites are geared toward the truly hardcore—and they’re not easy to find.
For example, the Armada site advertises DDoS attacks, hacking, and similar services. However, the operators themselves claim it’s all bluff, fiction, and a joke—and we didn’t attempt to verify that.
Judging by other hacker resources, it’s hard to tell whether they’re run by masters of disguise or just random people with no real connection to hacking. For example, Project Mayhem appears to offer some services, but outwardly it looks more like a Mayan calendar. The French hacker forum BumpTeam feels like a freshman’s lab assignment. Unfortunately, we couldn’t find any other criminally oriented resources on I2P.
Cryptocurrency
I2P tends to work much better with Bitcoin and crypto in general than with most other things. For example, Zcash is available inside I2P, and there are many more wallets and exchanges with trading platforms. We haven’t used any of them, so we strongly recommend thinking twice before making cryptocurrency transactions over I2P.
By the way, there’s even a site that lets you cash out Bitcoin to a virtual Visa card. It’s unavailable at the moment, but the idea is interesting.
Miscellaneous
I2P hosts quite a few resources that are also accessible from the clearnet. For example, the list of Telegram proxies or RosPravosudie.
We’d like to wrap up the list of the most interesting and accessible I2P resources with the I2P Project’s official website.
Conclusions
Using I2P isn’t straightforward, and as a result the network is far less popular than Tor services. I2P offers a more sophisticated anonymity model, but it can’t compete when it comes to the breadth of available content.
So for now, I2P isn’t really about browsing websites; it’s primarily for anonymous data transfer and keeping your traffic out of sight. In that respect, even if it’s not perfect, it’s at least better than Tor or a VPN.
The existence of a decentralized network that no one controls matters, even if you personally don’t see anything of value in it. So let’s thank those who continue to maintain I2P, and check back in a couple of years.
