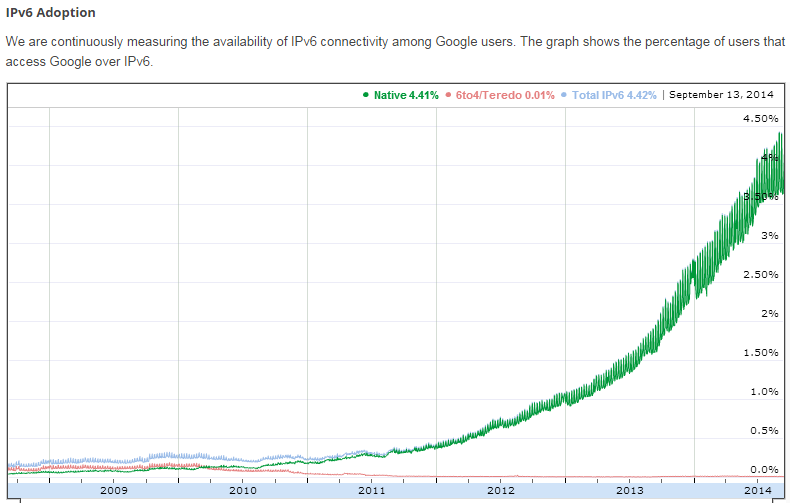
The most conservative estimates indicate that, by the end of 2015, the share of IPv6 traffic will reach at least 10%, and this growth will continue. A special protocol for regional registries also came into force recently. Now, a new block of IPv4 addresses will be issued only if the company proves it has already implemented IPv6. So if anyone needs a subnetwork of white IPv4 addresses, they will need to implement IPv6. This fact will also encourage the further growth of IPv6 systems and lead to an increase in traffic. As far as ordinary users are concerned, providers began appearing all over the world, issuing real IPv6-addresses to end subscribers. And so, IPv6 will be encountered more and more often, and that’s a fact we cannot ignore.
If we study charts provided by the regional registry of IP addresses and autonomous systems, we will discover that the number of registered IPv6 autonomous systems already exceeded 20% as of September 1, 2014. This seems like a significant number at first, but if we only take into consideration the real number of IPv6 traffic in the world, we’ll see that it now accounts for about 6% of all global Internet traffic. It was only 0.5% just three years ago.
What is new in IPv6?
The first thing that catches the eye is addresses. They have become longer, are written in hexadecimal format, and are hard to memorize. However, anyone working with IPv6 will discover that addresses, in general, can be memorized, especially if reduced record formats are used. Recall that IPv4 uses 32-bit addresses, which limit the address space to 4,294,967,296 (2^32) unique possibilities. And in the case of IPv6, 128 bits have been provided for the address. Correspondingly, there are 2^128 available addresses. This is approximately 100 addresses for each atom on the surface of the Earth. So there should be enough addresses for quite a long time.
The addresses are recorded in the form of eight groups of hexadecimal values. For instance, an IPv6 address might look like 2001:DB8:11::1. One interface can have several IPv6 addresses, and this is normal. For instance, an interface can have a private address, a white address, and an additional address obtained through DHCPv6. Everything will also operate in a standard mode: each task will use its specific address. If you need to go out to the world, a white address will be used. Need to get to a nearby server? Use your private address. All of this will be decided through an ordinary analysis of the destination field.
All IPv6 addresses are divided into two groups: Link-Local and Global Unicast. From the name, it is obvious that Link-Local is an address that is used only within a single link. Such addresses will be used to support a variety of mechanisms, such as automatic address setting, discovery of neighbors without a router, and so on. Such addresses are not permitted to be used for access to the world.
A Link-Local address is assigned automatically as soon as the host gets online. Such addresses remotely resemble the APIPA mechanism in Windows OS. It always starts with FE80, and the last 64 bits is a MAC address with FFFE entered in the middle; plus, one bit is inverted. The mechanism for such address generation is also called EUI–64. As a result, the address will be unique, as MAC addresses are usually different for all hosts. However, some OSs use a random identifier instead of the EUI–64 mechanism.
What else is new?
Naturally, the changes do not end with addresses. The header has also been significantly simplified (see Fig. 2).
![Fig. 2. IPv6 Header vs. IPv4 Header]](https://hackmag.com/wp-content/uploads/2014/08/ipv6vsipv4.png)
Now, everything that is not mandatory for routing a package from Point A to Point B is optional. And if it is optional, it is moved to an extension header that lies between the IPv6 header and the TCP/UDP data. Fragmentation, IPsec, source routing, and many other functions already supported in this extension-header.
The router task is now significantly simpler, as routers do not need to recalculate checksums. As a result, IPv6 is processed faster than IPv4. Checksums have been eliminated altogether. First, the L2 level frame has CRC. Second, the above-lying protocols (TCP) will also ensure integrity of delivery. As a result, the header has lost the unnecessary fields and has become simpler, faster, and more reliable.
AutoConfiguration and service protocols
There are two basic options for designation of IPv6 addresses: stateless autoconfiguration when the router sends the clients the address of the network, default gateway, and other necessary information, and statefull autoconfiguration when a DHCPv6 server is used. So, while DHCP was previously the only option for information distribution, it became a supplementary option in IPv6.
ICMP Version 6 has also gotten some attention, with many features added to it. For instance, there is the router discovery mechanism: Clients can listen to information the router provides to them (ICMPv6 message type 134 router advertisement, which are received during the stateless autoconfiguration process), and when it is enabled, they can immediately call the router for help, sort of “help me to configure” (ICMPv6 message type 133 router solicitation).
A neighbor discovery mechanism has also been added: it can be called a specific replacement of ARP that helps to determine the MAC addresses of neighbors and routers, and it can even discover duplicate addresses on a segment (duplicate address detection DaD). It works exclusively by multicast. There is no pure broadcast in IPv6 anymore, but we should not forget that certain cheap dumb switches broadcast the whole multicast, which renders some of the new mechanisms mentioned previously useless.
IPv6 Penetration Testing Tools
Before moving on to vulnerability and attacks, it would be nice to review which instruments exist in the penetration testing toolbox. Until recently, there was only one set of utility programs to conduct attacks against the IPv6 and ICMPv6 protocols. It was THC-IPV6 from well-known Marc van Hauser, author of the bruteforcer THC-hydra and lots of other irreplaceable tools. In 2005, he took a serious interest in this subject and performed extensive research on the IPv6 protocol. He also remained a pioneer until recently, but over the past year, the situation has begun to change. More and more researchers have started paying attention to IPv6, and, naturally, new utilities and new scanners have started to appear. But as of today, THC-IPV6 remains the best set of tools for penetration testing. This set already includes over 60 tools divided into various categories — from scanning and MITM to flooding and fuzzing. But let’s not forget the true tool scapy — a utility program used to manually create any packages, with any headers, even if such variations are not envisioned in any RFC.
Exploration in IPv6-networks
Before attacking a target, the target needs to be identified somehow, and so, a standard penetration test usually starts with a search of live hosts. But we have a problem here: We cannot scan the whole range. Scanning just one subnetwork will take years, even if you send a million packages per second. The reason is that the /64 subnetworks alone (or, as they are also called, prefixes) are significantly larger than the whole Internet today. So the biggest problem with IPv6 is discovering the targets.
Luckily, there is a way out. First, we need to find an AS (autonomous system) that belongs to the target (penetration test object). There are plenty of services that use AS to search for their owners. You can do it directly on the sites of regional registries. (The European registry is RIPE NCC.) Then, knowing the AS number that belongs to a certain company, we can search for the IPv6 subnetworks assigned to it. The most convenient search service is provided by Hurricane Electric. As a result, you can find several huge subnetworks, which, as we have already realized, cannot realistically be scanned for live hosts. And so, we need to create a list of frequently used addresses and do a targeted scan with those addresses.
We can put together such a dictionary by analyzing how the companies that have already implemented IPv6 issue addresses to clients, allowing us to distinguish three main groups: autoconfiguration, manual assignment of addresses, and DHCPv6.
We can form autoconfiguration in three ways: based on MAC address with the use of privacy option (i.e. randomly and, for instance, changed once a week) and fixed random (absolutely randomly). In this situation, we can scan only those addresses that are constructed on the basis of the MAC. As a result, we can identify subnetworks comparable in size to an А-class IPv4 subnetwork. Working with such networks is not exceedingly fast, but still quite realistic. For instance, if we know that the target company largely uses laptops from a certain vendor, we can construct a scan based on the knowledge of how the address will be generated.
If the addresses are set manually, they can be assigned either randomly or in a certain pattern. The latter, naturally, is encountered much more often in real life. And this pattern can be ::1,::2,::3 or ::1001,::1002,::1003. Also, service ports may sometimes be used as an address, depending on the server. For instance, a web server might have the following address: ::2:80.
In the case of DHCPv6, the addresses are usually issued from the pool sequentially. (Exactly the same behavior can be observed with an ordinary DHCPv4 server.) In DHCPv6, we may often encounter a pool like ::1000-2000 or ::100-200. And thus, we can use the alive6 utility (which is included in THC-IPV6 set and, as are all tools we reviewed today, included by default in Kali Linux) and launch it as follows:
alive6 -p eth0 2001:67c:238::0-ffff::0–2 Alive: 2001:db8:238:1::2 [ICMP echo-reply] Alive: 2001:db8:238:3::1 [ICMP echo-reply] Alive: 2001:db8:238:3::2 [ICMP echo-reply] Alive: 2001:db8:238:300::1 [ICMP echo-reply] Scanned 65536 systems in 29 seconds and found 4 systems alive
If live machines are identified in this matter, only the part responsible for the host address will change. Using this approach, we can find live hosts in previously discovered subnetworks quite effectively and within sensible time limits.
But this is not all: naturally, we can also use DNS. DNS-zone transfers and DNS bruteforce dictionary attacks did not cease with the advent of Ipv6. By using all of these techniques together, we can discover up to 80% of all enabled hosts in a given IPv6 subnetwork, which is not too bad. If just one host is compromised, we can easily discover all of its neighbors using multicast. Just launch the same alive6 utility, but with the -l option.
Among the new features in THC-IPV6, particularly the alive6 utility, we can also note the ability to search for live hosts using an entire IPv4 subnetwork as a search pattern:
# alive6 -4 192.168.0/24
Almost nothing has changed in terms of classic scanning. The same Nmap and the same port scanning options are present. The only difference is that we can now scan only one host at a time, but this is quite an obvious solution.
The only additional technique for scanning ports is that IPv4 is scanned first, and then, the IPv6 information on these hosts is obtained. That is, the attack surface has expanded somewhat. This can be accomplished using both the auxiliary module in the ipv6_neighbor metasploit and separate ipv6_surface_analyzer scripts. They work based on a similar principle: accept an IPv4 subnetwork at the entrance; scan it; find the live hosts; check the ports for openness; and then, after detecting the MAC address, use it to calculate the IPv6 address and try to work with it. It really helps sometimes, but in some cases (privacy option), IPv6-addresses cannot be discovered, despite the fact that they exist.
IPv6 Perimeter Threats
If we review the external perimeter, we’ll discover that many companies that have already started implementing IPv6 are in no rush to close their administrative ports (SSH, RDP, Telnet, VNC, etc.). If almost everybody tries to somehow filter IPv4, then either IPv6 is forgotten or people just do not know that it has to be protected in the same way as IPv4. If we can somehow understand the telnet used by IPv4 — for instance, limited memory or CPU do not allow the full use of SSH — each device that supports IPv6 today is simply guaranteed to support SSH protocol. There are cases in which ISPs set the IPv6 administrative ports on their routers to world-accessible. It turns out that even providers are more vulnerable to IPv6 attacks. This happens for various reasons. First, not very many good IPv6 firewalls are available yet. Second, they have not yet been bought and set up. The main reason is that many do not even suspect the IPv6 threats. There is a popular opinion that, as long as there are no IPv6 hackers, malware, or IPv6 attacks, there is nothing to defend against.
Threats within LANs LAN
If we go back to IPv4, we’ll discover that there are three attacks that are still effective in local networks. These are ARP spoofing, DHCP spoofing, and ICMP redirects. (This attack class was discussed in detail during my lecture at PHDays, so you can search for a corresponding video online.)
In the case of IPv6 protocol, when the attacker is in the same local segment as the victim, oddly, the situation remains almost the same. ARP has been replaced with NDP, and DHCP with autoconfiguration, and ICMP simply got updated to ICMPv6. It is important that the attack concept remained almost unchanged. Additionally, new mechanisms, such as DAD, were added, and new corresponding vectors and attacks immediately appeared.
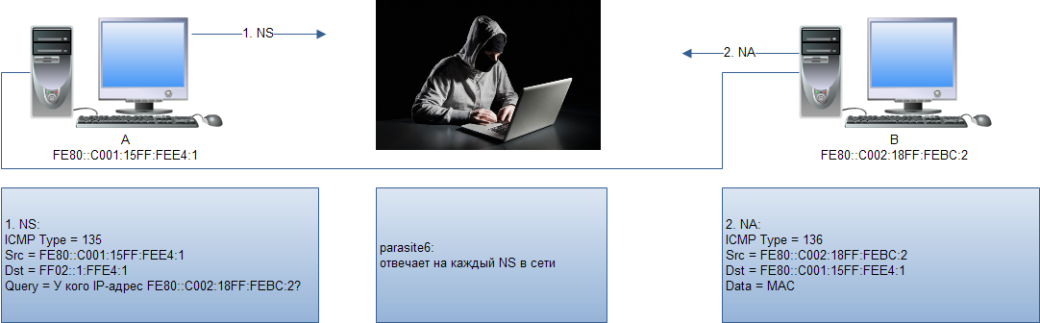
The Neighbor Discovery Protocol (NDP) is the protocol used for IPv6 hosts to discover each other, determine the data link layer address of another host (instead of ARP as was used in IPv4), and discover routers and so on. For this mechanism to work — which it does, with the use of multicast — each time that a Link-Local or global IPv6 address is assigned to an interface, the host joins a multicast group. In fact, there are only two types of messages used in the neighbor discovery process: information request or NS (neighbor solicitation) and provision of information or NA (neighbor advertisement).
The interaction in this mode can be seen in Fig. 3.

As a result, the attacker only needs to launch the parasite6 utility that will respond to all NS passing through a certain segment. (See Fig. 4.) Do not forget to enable forwarding first (echo 1 >/proc/sys/net/ipv6/conf/all/forwarding). Otherwise, it will be a DoS rather than an MITM attack.
INFO
When using protocol IPv4 and ARP, it can sometimes be quite useful to check the ARP cache; this can be done using the
arp -acommand, on both the Linux and Windows platforms.
Now, for IPv6 in Linux, in order to see the neighbors useip -6 neighborshowcommand, while in the Windows environment, it can be done using thenetsh interface ipv6 show neighborscommand.
The weak points in this attack are that the attacker will try to send an ND-cache of all the hosts, which is, first of all, noisy, and second of all, complicated, if the traffic volume is high. So we need to use scapy and conduct this attack manually and in a targeted manner. First, we need to fill out all necessary variables.
>>> ether=Ether(src="00:00:77:77:77:77",dst="00:0c:29:0e:af:c7")
The addresses of the data link layer come first. The MAC address of the attacker is used as the sender’s address, and the MAC address of the victim is used as the recipient’s address.
>>> ipv6=IPv6(src="fe80::20d:edff:fe00:1",dst="fe80::fdc7:6725:5b28:e293")
Then the network layer addresses are specified, the sender’s address will be spoofed (which is, in reality, the router’s address), and the recipient’s address is the IPv6 address of the victim.
>>> na=ICMPv6ND_NA(tgt="fe80::20d:edff:fe00:1", R=0, S=0, O=1)
We will specify the third variable in the form of a correctly assembled NA package, where ICMPv6ND_NA is ICMPv6 Neighbor Discovery — Neighbor Advertisement, and tgt is the actual address of the router that is noted as the attacker’s address. It’s important to correctly set all the flags: R=1 means that the sender is the router, S=1 will specify that the notice is sent in response to the NS-message, and O=1 is a so-called override flag.
>>> lla=ICMPv6NDOptDstLLAddr(lladdr="00:00:77:77:77:77")
The next variable is a Link-Local address ICMPv6NDOptDstLLAddr (ICMPv6 Neighbor Discovery Option — Destination Link-Layer). This is the MAC address of the attacker.
>>> packet=ether/ipv6/na/lla
All that is left is to assemble the package as a unit and send it to the net.
>>> sendp(packet,loop=1,inter=3)
The loop=1 value indicates that we need to send infinitely, every three seconds.
As a result, some time later, the victim will update the neighbor’s cache and send all traffic that was intended for the router directly into the attacker’s hands. We need to note that, to create a proper MITM, we need to launch another instance of scapy, where the addresses will be inverted in order to infect the router. Nothing complicated, as you can see.
Also, the concept of gratuitous NA does not exist in IPv6 as it used to exist in the time of ARP. (Gratuitous ARP is an ARP response received without request.) Also, the ND cache does not live long and quickly gets outdated. It was developed to avoid sending packages to non-existent MAC addresses. That is why, in an IPv6 network, the exchange of NS — NA messages occurs very frequently, which plays into the hands of the attacker.
End-Host Threats
Now that we have discussed RA, we will move on to the end-host threats – in particular, to hosts not intended to use IPv6. This means we are going to consider attacks on hosts operating in the default IPv6 configuration on a regular IPv4-network. What will happen if any modern OS receives an RA package? As any system now supports IPv6 and expects such packages, it will immediately turn on a so-called dual stack. This is a situation in which IPv4 and IPv6 are used simultaneously within a single operating system. In such a case, a wide variety of previously inaccessible vectors will immediately open. For instance, it will be possible to scan the target, as IPv4 is usually filtered, but, as we know, it is common for people to not even think about IPv6.
Additionally, in most OSs, IPv6 has priority over IPv4. If, for instance, a DNS request comes, it is a bigger possibility that IPv6 will work faster. This provides vast opportunities for various MITM attacks. One of the most effective ones requires installation of a compromised IPv6-router. Each IPv6 router is required to connect to a special multicast group. It is FF02::2. As soon as the router connects to this multicast group, it immediately starts sending out RA messages. Сisco routers send them every 200 sec by default. Another delicate detail is that clients do not need to wait for 200 sec: they send an RS-message — Router Solicitation — to this multicast address, and, in this way, request all information immediately. This whole mechanism is called SLAAC — Stateless Address Autoconfiguration. Correspondingly, the attack developed to take advantage of it has an obvious name: SLAAC Attack.
The attack involves installing your router that will send out RA messages. (This is not to be understood literally, as any Linux machine or even a virtual machine can act as a router.) However, that’s only half of the process. Also, the attacker will need to launch DHCPv6 server, DNSv6, and NAT64 compiler. One can use Router Advertisement Daemon (radvd) as a service that is able to send RA messages. This is an open-source implementation of an IPv6-router. As a result, after correct configuration of all demons, the victim will receive an RA message and turn into a dual stack, and all of the victim’s traffic will absolutely unnoticeably flow via IPv6.
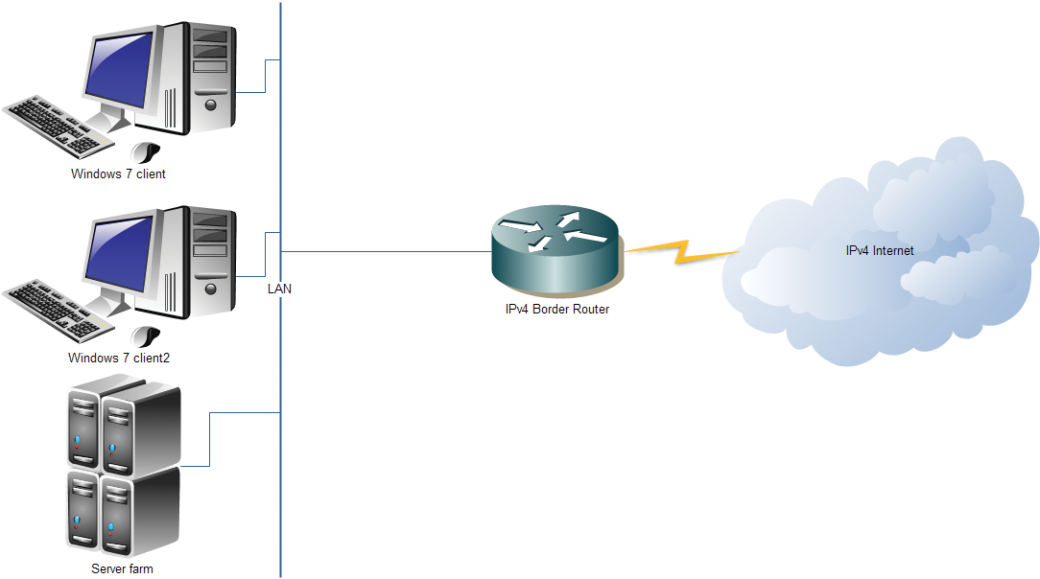
On the attacker’s router, this traffic will be transformed to regular IPv4 using NAT and then go to the real router. DNSv6 requests will also have priority and will also be processed on the attacker’s side.
In this way, the attacker successfully stands in the middle and can observe all of the victim’s traffic, and the victim will not suspect a thing. Such an attack bears a maximum threat and works even when IPv4 firewalls and static AR records are used – when, seemingly, there is no way to affect the victim.
How to protect IPv6
Regarding protection against the abovementioned attacks, it is obviously necessary to filter all the traffic on the perimeter and turn off unused services. We should also pay special attention to administrative services. To reduce the impact of local attacks forwarded to the ICMPv6 service protocol, we can limit the attack surface for such attacks by breaking large networks into subnetworks (also called micro segmentation). The same network infrastructure can be divided into several VLANs with a separate IPv6 prefix for each such VLAN. In this case, the attacker can only attack hosts that are located on the same VLAN as the attacker, and this already significantly limits the potential damage from the attacks.
There is a separate protection that we can implement against false RA messages, which can only come from routers. Cisco implemented a feature called Router Advertisement Guard that prevents injection of untrusted RA messages by noting potentially unsafe ports. Thus, RA packages will simply not be accepted from user ports. This feature works by analogy with DHCP snooping. The only disadvantage is that this feature is available only on a certain class of hardware — on Catalyst Series 2960S, 3560, and 3750. Additionally, in 2012, DHCPv6 Guard and NDP Snooping appeared. These are again the analogs of DHCP Snooping and Dynamic ARP Inspection from the IPv4 world. These protection mechanisms are available on Catalyst 4500/4948 and 7600 series routers.
If we consider end-host protection, we’ll see that all recent versions of Windows allow RA-message processing to be turned off. If all the IPv6 parameters are configured manually, this can be quite a good option, although it somewhat breaks the canonical IPv6 mechanisms. It can be enabled quite easily, straight on the interface with the command
Netsh int ipv6 set int X routerdiscovery=disabled
where X is an interface index. (You can view IPv6-inteface indices using the netsh int ipv6 showint command.) The result can be verified with netsh int ipv6 showintX command.
If we look at the situation with discovery of IPv6 attacks, in general, everything is fine. It’s quite easy to detect IPv6-attacks, but so far, they are hard to prevent.
Completing the Story
In the end, it turns out that the IPv6 protocol itself is neither safer nor weaker than IPv4. The problem lies in users’ insufficient knowledge and working experience with this protocol. We need to filter IPv6 on the perimeter and disable it if it is not used on the end devices. Many people think that IPv6 is much safer than IPv4 because IPv6 requires the use of IPsec. This, however, is a myth. Yes, IPsec can work in the IPv6 medium directly, but this is never mandatory. IPv6 does some things better and some things worse, but most things are simply different from what everyone has gotten used to. In other words, IPv6 protocol is neither more nor less safe than IPv4. IPv6 protocol is just unique, requiring different security considerations to be taken into account.
