There are many ways to increase fault tolerance and reliability of corporate networks. Among other things, First Hop Redundancy Protocols (FHRP) are used for this purpose. In this article, I will explain how pentesters interact with FHRP in the course of network attacks.
CONTINUE READING 🡒 Top 5 Ways to Use a VPN for Enhanced Online…
This is an external third-party advertising publication.
CONTINUE READING 🡒 What Challenges To Overcome with the Help of Automated e2e…
This is an external third-party advertising publication.
CONTINUE READING 🡒 Playful Xamarin. Researching and hacking a C# mobile app
Java or Kotlin are not the only languages you can use to create apps for Android. C# programmers can develop mobile apps using the Xamarin open-source platform. Today, I will explain how to research such apps and find ways to hack them.
CONTINUE READING 🡒 Challenge the Keemaker! How to bypass antiviruses and inject shellcode…
Recently, I was involved with a challenging pentesting project. Using the KeeThief utility from GhostPack, I tried to extract the master password for the open-source KeePass database from the process memory. Too bad, EDR was monitoring the system and prevented me from doing this: after…
CONTINUE READING 🡒 Vulnerable Java. Hacking Java bytecode encryption
Java code is not as simple as it seems. At first glance, hacking a Java app looks like an easy task due to a large number of available decompilers. But if the code is protected by bytecode encryption, the problem becomes much more complicated. In this article,…
CONTINUE READING 🡒 Blindfold game. Manage your Android smartphone via ABD
One day I encountered a technical issue: I had to put a phone connected to a single-board Raspberry Pi computer into the USB-tethering mode on boot. To do this, I used Android Debug Bridge (ADB), a handy debugging interface for Android devices. There are several…
CONTINUE READING 🡒 Climb the heap! Exploiting heap allocation problems
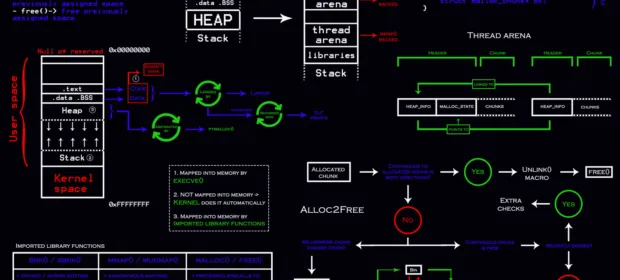
Some vulnerabilities originate from errors in the management of memory allocated on a heap. Exploitation of such weak spots is more complicated compared to ‘regular’ stack overflow; so, many hackers security researchers have no idea how to approach them. Even the Cracking the Perimeter (OSCE) course doesn’t…
CONTINUE READING 🡒 Quarrel on the heap. Heap exploitation on a vulnerable SOAP…
This paper discusses a challenging CTF-like task. Your goal is to get remote code execution on a SOAP server. All exploitation primitives are involved with the heap in one way or another; so, you’ll learn a lot about functions interacting with it. Also, you’ll…
CONTINUE READING 🡒 Routing nightmare. How to pentest OSPF and EIGRP dynamic routing…
The magic and charm of dynamic routing protocols can be deceptive: admins trust them implicitly and often forget to properly configure security systems embedded in these protocols. In this article, I will explain what nightmares can occur if the network admin doesn’t take a good care…
CONTINUE READING 🡒 First contact. Attacks on chip-based cards
Virtually all modern bank cards are equipped with a special chip that stores data required to make payments. This article discusses fraud techniques used to compromise such cards and methods used by banks to protect cardholders against attackers.
CONTINUE READING 🡒 Log4HELL! Everything you must know about Log4Shell
Up until recently, just a few people (aside from specialists) were aware of the Log4j logging utility. However, a vulnerability found in this library attracted to it a great attention from researches nowadays. Let’s take a closer look at the origin and operation mechanism of this bug…
CONTINUE READING 🡒 WinAFL in practice. Using fuzzer to identify security holes in…
WinAFL is a fork of the renowned AFL fuzzer developed to fuzz closed-source programs on Windows systems. All aspects of WinAFL operation are described in the official documentation, but its practical use – from downloading to successful fuzzing and first crashes – is not that simple.
CONTINUE READING 🡒 Cybercrime story. Analyzing Plaso timelines with Timesketch
When you investigate an incident, it’s critical to establish the exact time of the attack and method used to compromise the system. This enables you to track the entire chain of operations performed by the malefactor. Today, I will show how to do this using the Timesketch tool.
CONTINUE READING 🡒 F#ck AMSI! How to bypass Antimalware Scan Interface and infect…
Is the phrase “This script contains malicious content and has been blocked by your antivirus software” familiar to you? It’s generated by Antimalware Scan Interface (AMSI), a protection mechanism embedded in Windows 10 that blocks the execution of malicious scripts. But can AMSI be bypassed?…
CONTINUE READING 🡒 Fastest shot. Optimizing Blind SQL injection
Being employed with BI.ZONE, I have to exploit Blind SQL injection vulnerabilities on a regular basis. In fact, I encounter Blind-based cases even more frequently than Union- or Error-based ones. But how to raise the efficiency of such attack? This article provides an overview of approaches…
CONTINUE READING 🡒 Elephants and their vulnerabilities. Most epic CVEs in PostgreSQL
Once a quarter, PostgreSQL publishes minor releases containing vulnerabilities. Sometimes, such bugs make it possible to make an unprivileged user a local king superuser. To fix them, Postgres DBAs release patches simultaneously with the updates and sleep peacefully. However, many forks share a large codebase…
CONTINUE READING 🡒 Timeline of everything. Collecting system events with Plaso
As you are likely aware, forensic analysis tools quickly become obsolete, while hackers continuously invent new techniques enabling them to cover tracks! As a result, valiant DFIR (Digital Forensics and Incident Response) fighters suffer fiascoes on a regular basis. So, I…
CONTINUE READING 🡒 First contact: How hackers steal money from bank cards
Network fraudsters and carders continuously invent new ways to steal money from cardholders and card accounts. This article discusses techniques used by criminals to bypass security systems protecting bank cards.
CONTINUE READING 🡒 EVE-NG: Building a cyberpolygon for hacking experiments
Virtualization tools are required in many situations: testing of security utilities, personnel training in attack scenarios or network infrastructure protection, etc. Some admins reinvent the wheel by assembling fearsome combinations of virtual machines and all kinds of software. I suggest another way: set up an emulation…
CONTINUE READING 🡒