Microsoft has reported that attackers could have exploited a recently patched vulnerability bypassing Transparency, Consent, and Control (TCC) to steal confidential information from macOS users, including cached Apple Intelligence data.
TCC is a security mechanism and framework in macOS that blocks applications from accessing users’ personal data, giving macOS control over how information is accessed and used by applications across all Apple devices. TCC is responsible for requesting permissions to run new applications and displaying warnings if an application tries to access sensitive data (including contacts, photos, webcams, and so on).
The vulnerability, identified as CVE-2025-31199 and discovered by Microsoft specialists, was patched in March 2025 with the release of updates for macOS Sequoia 15.4.
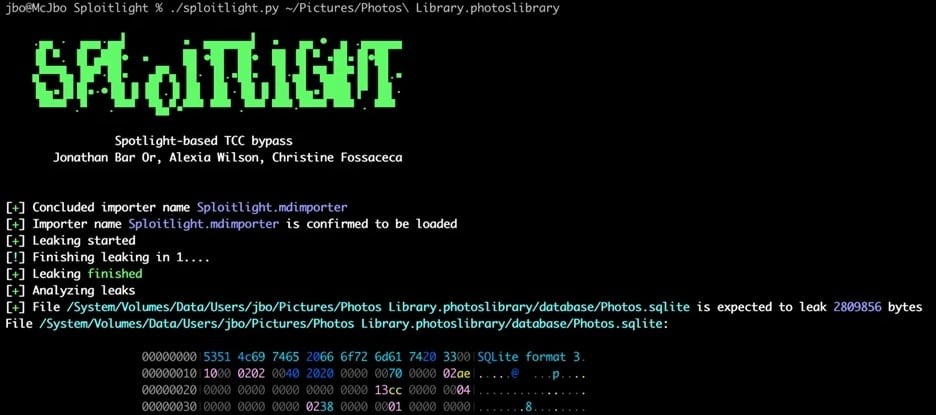
The issue was that although Apple restricts TCC access to applications with full disk access and automatically blocks unauthorized code execution, Microsoft researchers found that attackers could exploit the privileged access of Spotlight plugins to gain access to sensitive files and steal their contents.
In the recently published report, Microsoft experts demonstrated that the vulnerability (which they named Sploitlight) could have been used to collect data, including Apple Intelligence information and remote information about other devices associated with an iCloud account.
This way, attackers could gain access to photo and video metadata, geolocation data, face and people recognition data, user activity information, photo albums and shared libraries, search history and user preferences, as well as deleted photos and videos.
“While this issue is similar to previous TCC bypasses, including HM-Surf and powerdir, the implications of this vulnerability, which we have named Sploitlight (due to the exploitation of Spotlight plugins), are more severe as it allows for the extraction and theft of confidential information cached by Apple Intelligence. For instance: precise geolocation data, photo and video metadata, facial recognition data, search history, and much more,” explained Microsoft. “The risks are further compounded and intensified by the possibility of remotely linking iCloud accounts. This means that an attacker with access to a macOS user’s device can exploit the vulnerability to obtain remote information about other devices associated with the same iCloud account.”