Experts warn that hackers are actively exploiting the critical CVE-2025-10035 vulnerability in Fortra’s GoAnywhere MFT, disclosed earlier this month. The bug allows remote command execution without authentication.
GoAnywhere MFT is a file transfer tool designed to help organizations securely exchange files with partners and maintain audit logs of who accessed shared files. It is developed by Fortra (formerly known as HelpSystems), which also develops the well-known and widely used Cobalt Strike tool, intended for pentesters and red teams and focused on exploitation and post-exploitation.
Developers at Fortra reported the issue CVE-2025-10035 on September 18, 2025. How and by whom exactly this bug was discovered has not been disclosed. It is also unclear whether the company was aware of its exploitation.
CVE-2025-10035 (10 out of 10 on the CVSS scale) is a deserialization vulnerability in the GoAnywhere MFT License Servlet component (license handler). The issue enables command injection provided the attacker has a valid, correctly signed license response.
To address the issue, GoAnywhere MFT 7.8.4 and Sustain Release 7.6.3 were released. Administrators who cannot immediately install the updates were advised to protect vulnerable systems by ensuring the GoAnywhere administrator console is not accessible from the internet.
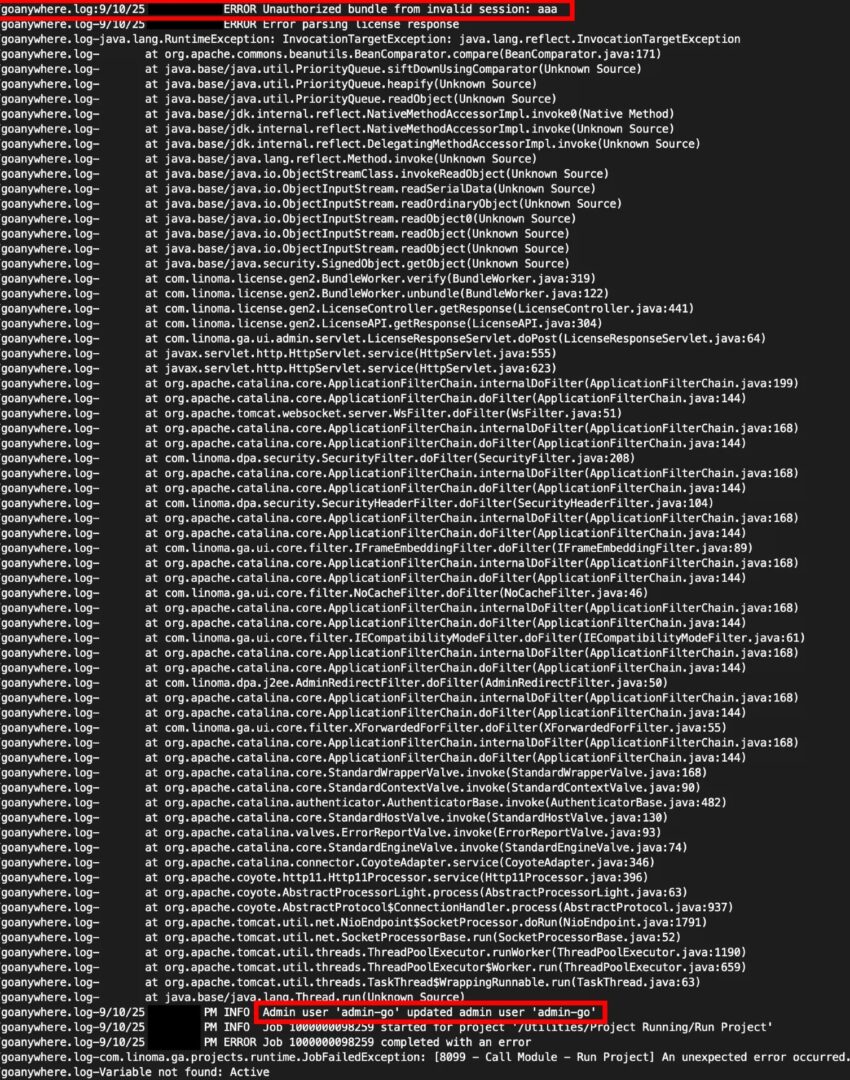
As researchers from WatchTowr Labs now report, they have found compelling evidence that the CVE-2025-10035 issue was exploited by hackers as a zero-day starting on September 10, 2025 — that is, eight days before the vendor’s security advisory was published.
Experts report that the attackers:
- achieved unauthenticated remote command execution by exploiting a deserialization vulnerability;
- created a hidden administrative backdoor account named admin-go;
- using this account, created a web user with “legitimate” access;
- uploaded and executed several additional payloads.
Among the indicators of compromise published by the researchers are payloads such as zato_be.exe and jwunst.exe. The latter is a legitimate binary of the SimpleHelp remote access product. In this case, it was used to establish persistent control over the compromised hosts.
It was also noted that the attackers executed the whoami /groups command, which displays information about the current user account and Windows group memberships, and saved the result to a file named test.txt for subsequent exfiltration. This allowed them to verify the privileges of the compromised account and explore options for lateral movement.
Interestingly, experts at Rapid7 believe that CVE-2025-10035 is not just a single deserialization vulnerability, but rather a chain of bugs consisting of three separate issues:
- an access control bypass known since 2023;
- the CVE-2025-10035 deserialization vulnerability;
- a yet-unknown issue whereby attackers are able to obtain a specific private key.
WatchTowr and Rapid7 analysts emphasize that they were unable to find the private key serverkey1, which is required to forge the license response signature needed to successfully exploit CVE-2025-10035.
Both companies note that the vulnerability can only be exploited if the private key leaks and ends up in the hands of attackers; if the attackers manage to trick the license server into signing a malicious signature; or if the attackers have somehow gained access to serverkey1.
