Here’s the plan for the article: how to contain an infection if it does manage to get onto your machine, how to remove rootkits, and how to restore the system after an infection if things have gone too far. We’ll wrap up with a few seemingly obvious but still relevant tips on avoiding infection (then again, can you really call “obvious” the kind of advice that, if followed, would reduce the number of infected machines on the Internet by an order of magnitude?).
What to do if your PC is infected
So, if you suspect the machine is compromised, there are a few things you should do right away:
- Isolate the host from the network (unplug the Ethernet cable, disable Wi‑Fi).
- Unplug all external peripherals from the ports (external HDDs and USB devices, phones, etc.).
All these steps are about isolating the infected host from the outside world. You must disconnect it from both the internet and the local network, since the malware will almost certainly try to spread across any segment it can reach. If the threat is part of a botnet or includes RAT components, it may stay dormant until it receives a command from a C2 server on an external network. This also helps prevent data exfiltration, for example via DNS-tunneled channels or similar hacker tricks. By the same logic, unplug any devices connected to the host as soon as possible: if it’s ransomware, it may not have time to reach data on external HDDs and USB flash drives.
You might also hear the advice to immediately power off an infected machine. It’s not that straightforward. On the one hand, this can halt the malware’s destructive activity. On the other, you risk that after a shutdown the OS might never boot again and the disks could get wiped. So you need to act based on the situation—much depends on what malware ran and what it was trying to do. In the case studies below, we’ll cover scenarios for both approaches.
And of course, to successfully combat malware and restore the system, you’ll need administrator-level privileges. Many steps—editing system files, stopping and restarting network services, restoring the registry, changing bootloader configuration, and the like—require full control of the system. 🙂
warning
Incorrect or ill‑considered actions can disrupt the normal operation of your operating system or software, or lead to data loss. Neither the author nor the editorial team is responsible for any damage resulting from improper use of the materials in this article. Perform only those actions whose purpose and consequences you fully understand.
Locating and neutralizing in‑memory malware processes
Any piece of malware has to execute in RAM. It doesn’t matter how the code gets there—an EXE attached to an email, a script in a compromised HTML page, or even assembled purely from network packets, like the notorious early-2000s fileless worm Slammer, which hit thousands of servers within minutes. So the first order of business is to find and identify the malicious process in memory. The built-in Windows Task Manager won’t help. Why? Because even a novice Delphi coder can use functions to hide a running process from Task Manager’s view. And that’s before you consider malware that includes a rootkit to conceal its activity on the system.
So we’ll turn to some utilities—both standalone tools and comprehensive task managers. The first one we’ll look at is Process Monitor, a free tool from the SysInternals Suite. It essentially combines two earlier tools—FileMon (file system monitoring) and RegMon (registry monitoring). Process Monitor provides a powerful way to monitor file system activity, the Windows registry, and process activity in memory in real time.
The toolbar includes several handy buttons that let you filter processes and system events by the criteria you need:
- Show registry activity — view Windows Registry activity (key reads and writes)
- Show file system activity — view file system activity (file reads and writes)
- Show per-process network activity — view network activity by process
- Show processes and threads — view running processes and their threads
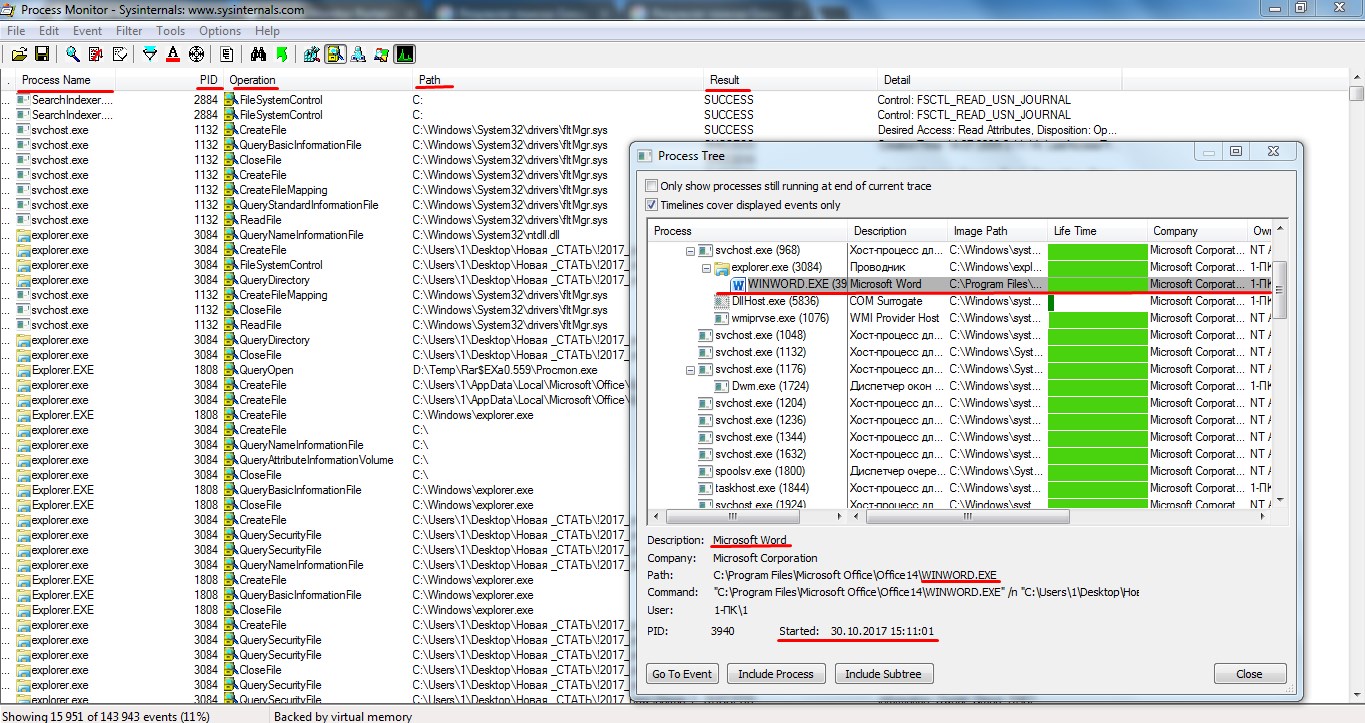
The second, more advanced tool is Process Explorer. It’s designed for monitoring system processes. It not only lets you track a process, but also see which files and folders it’s using. Its standout feature is that you can select a process and check it on VirusTotal with a single click, right from the main window.
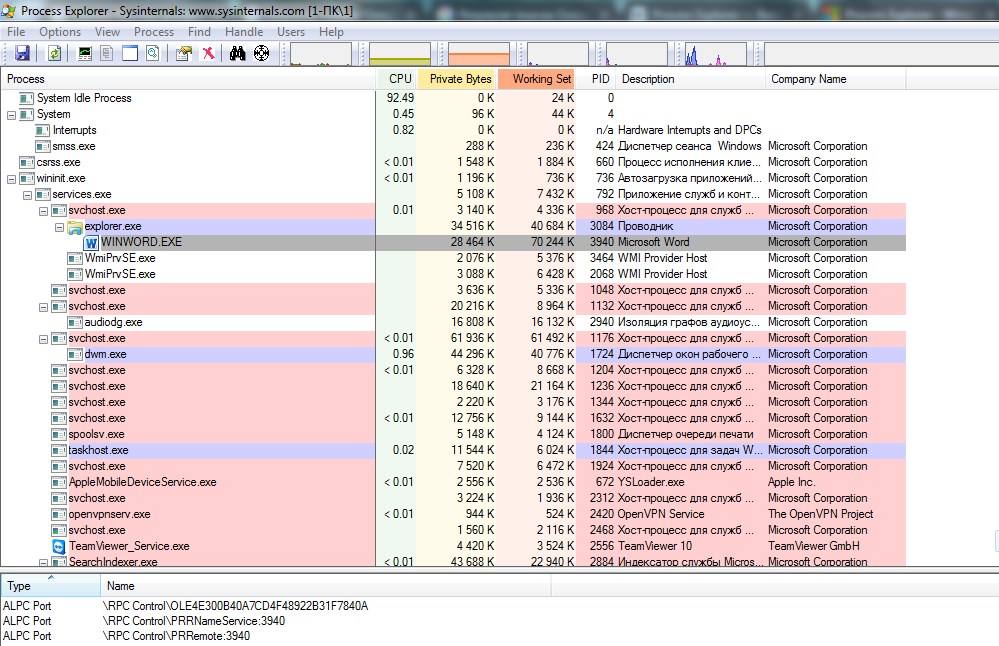
System Explorer, a favorite among malware analysts, monitors all running processes and shows detailed memory and pagefile usage, CPU activity, drivers, open network connections, and more.
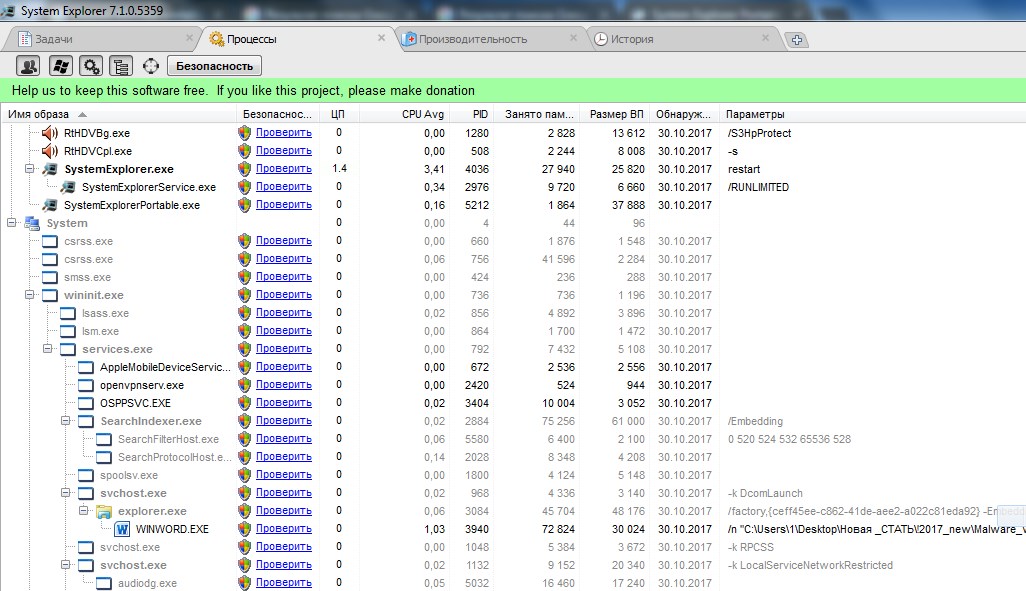
The tool has a built-in database—you can scan a specific file for malicious code and upload a VirusTotal report to the server.
This tool lets you terminate any process or a group of related processes that are slowing down the system or an application, and view the activity history for any program. It supports plugins. The interface is organized into tabs, each focused on a specific task. System Explorer allows you to manage startup items, view and quickly uninstall installed applications, manage Windows services, and much more.
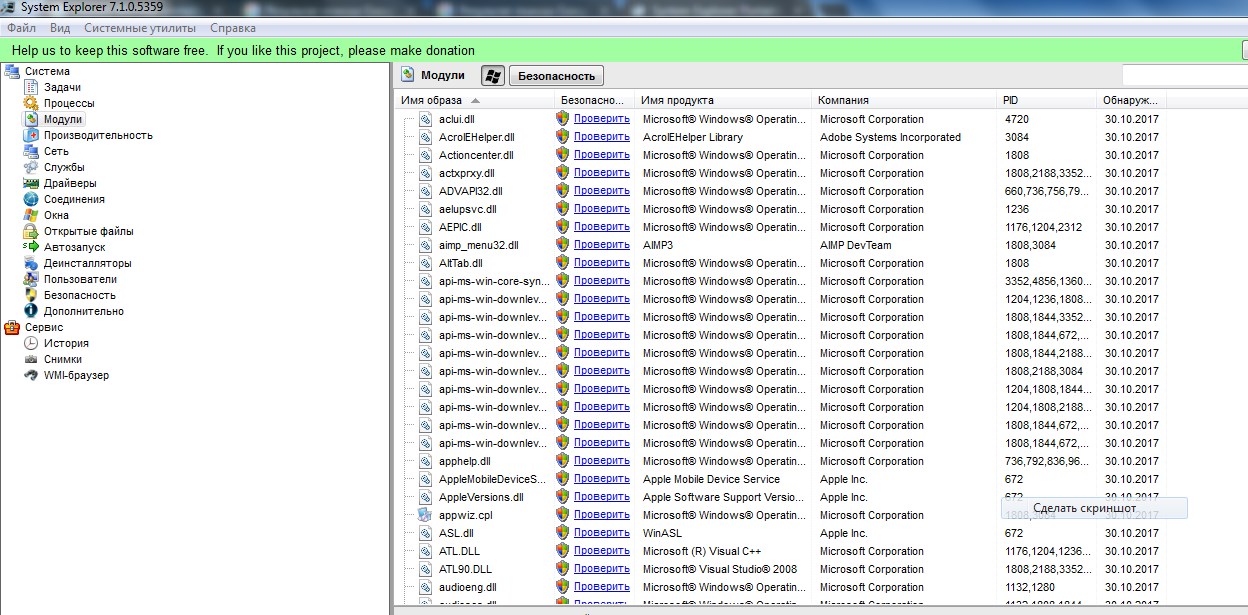
The fourth tool is AnVir Task Manager, a full-featured task manager that lets you monitor everything running on your PC and offers handy utilities for system configuration. It lets you manage startup items, running processes, services, and drivers, and can replace the default Task Manager.
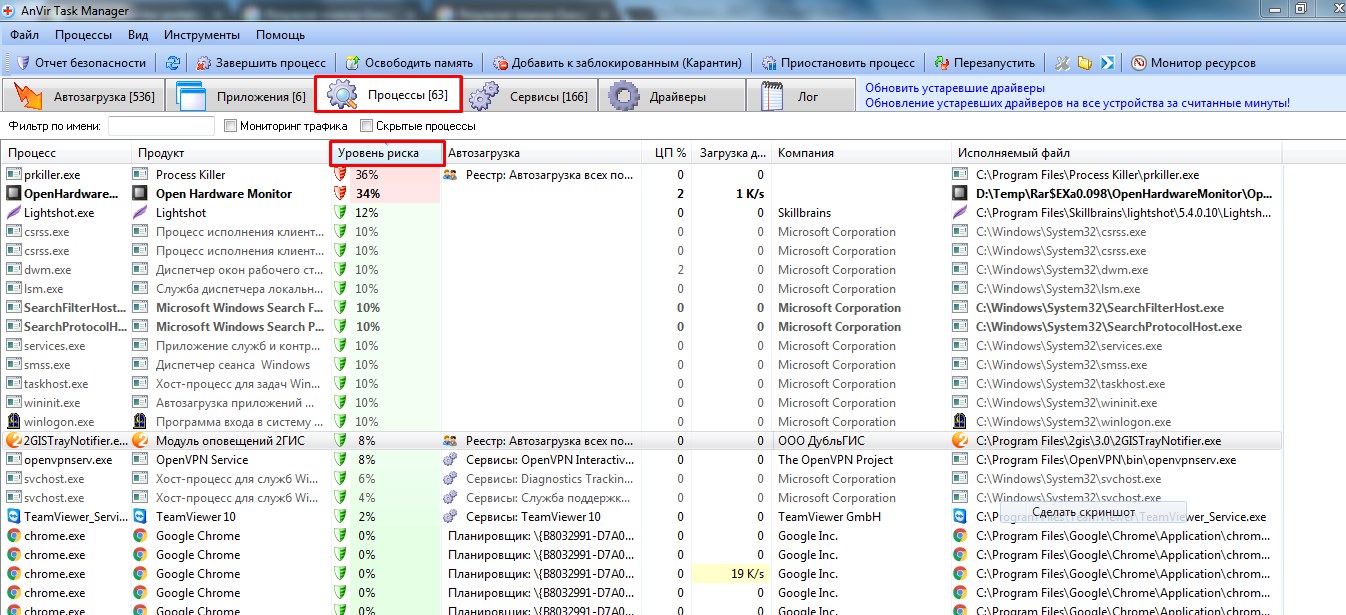
In the simplest case, a process name matches the name of the executable that was launched. So the easiest way to find malware is to review the list of running processes and focus on anything suspicious. But there are trickier scenarios, where malware authors use system-sounding names—like system services such as Svchost.exe—or, worse, don’t create a new process at all and instead inject the malicious code into a legitimate one. If that process has some of its functions terminated, the OS may become unavailable, or you might even get an RPC error that triggers a reboot. That technique was used by the notorious Blaster worm. You won’t spot a malicious process by eye in cases like this—you’ll need more capable tools.
The AVZ utility, developed by Oleg Zaitsev, will come to the rescue. It’s not an antivirus, but it includes signatures for many well-known worms, backdoors, and rootkits.
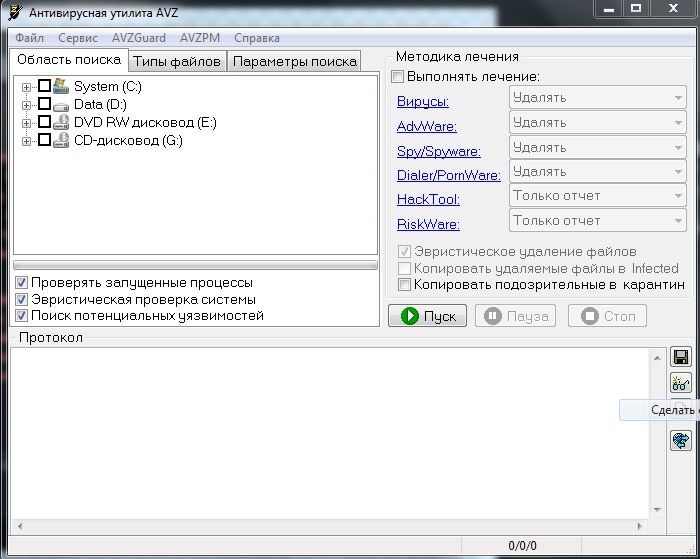
So the tool can scan RAM and detect compromised processes. It also packs a number of solid features: a kernel‑mode driver for detecting rootkits, keyloggers, and trojanized DLLs; raw disk access to handle locked files on NTFS volumes, including quarantining them; a TCP/UDP open‑port analyzer to spot RATs; a Winsock SPI/LSP analyzer to validate network stack settings; a cleanup/diagnostics module for Internet Explorer junk settings; plus an integrity checker for the system registry, BHOs, IE and Explorer extensions, and an analyzer for all available autostart mechanisms.
Hunting the Unseen
Detecting and neutralizing rootkits is one of the hardest problems in fighting malware, because they leverage low-level system features—intercepting and modifying system functions, tampering with system calls, and running in kernel mode with the highest privileges—which lets them bypass many security controls.
Manual detection is largely ineffective here, so specialized utilities are essential. In some respects, anti-rootkits operate like antivirus engines—they can use signature-based and heuristic detection—but they aren’t antivirus software in the conventional sense. Let’s review a few of the best-known tools that are widely used in practice.
- RkUnhooker is one of the most powerful tools for detecting rootkits and tackling other malware. It can detect and remove SSDT and code hooks, reveal hidden drivers, processes, and files. It also lets you delete files locked by running processes, optionally overwriting them with empty data to prevent them from running again. You can capture process memory dumps and analyze them as well.
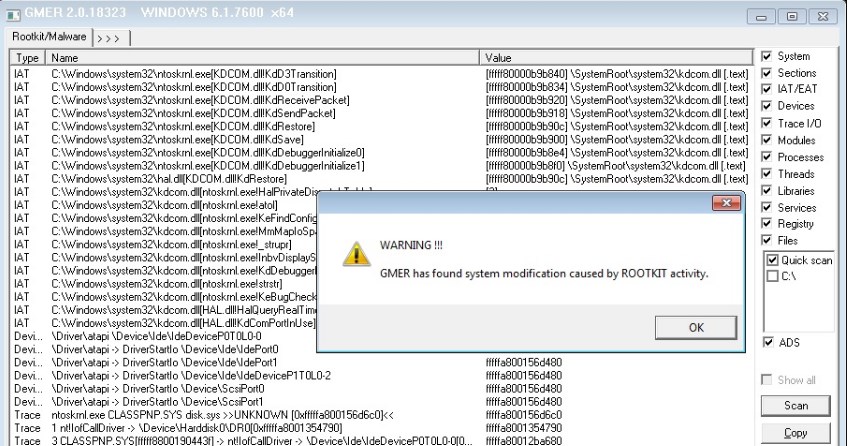
- GMER (http://www.gmer.net) — a well-known utility that, beyond its core function, bundles tools like a powerful registry editor that reveals hidden keys, a raw disk editor, and a startup entries manager.
- RootRepeal (https://www.bleepingcomputer.com/download/rootrepeal-rootkit-detector/) — often used alongside GMER — analyzes all loaded drivers and running processes, looking for anomalies and other telltale signs of malware.
- UnHackMe — a well-known tool for detecting and thoroughly removing modern trojans that leverage rootkit techniques. According to the developers, it uses unique detection methods. It also looks for unwanted search hijacks in browsers and checks startup/autorun entries for suspicious programs.
- HijackThis — a lightweight tool for detecting and removing basic forms of malware. It’s now distributed under the GPLv2 and owned by the antivirus company Trend Micro.
- TDSSKiller (https://support.kaspersky.ru/viruses/disinfection/5350) — a Russian-made anti-rootkit utility from Kaspersky Lab. It was originally created to clean systems infected with the Rootkit.Win32.TDSS family. Today, the tool can detect and remediate well-known rootkits such as TDSS, SST, Pihar, ZeroAccess, Sinowal, Whistler, Phanta, Trup, Stoned, Rloader, Cmoser, Cidox, as well as rootkit anomalies.
- SpyDllRemover — an effective tool for detecting and removing spyware from your system. It uses its own scanning engine to quickly uncover hidden rootkit processes and flags suspicious DLLs across all running processes. Processes are color‑coded by risk level, making it easier to spot malicious DLLs.
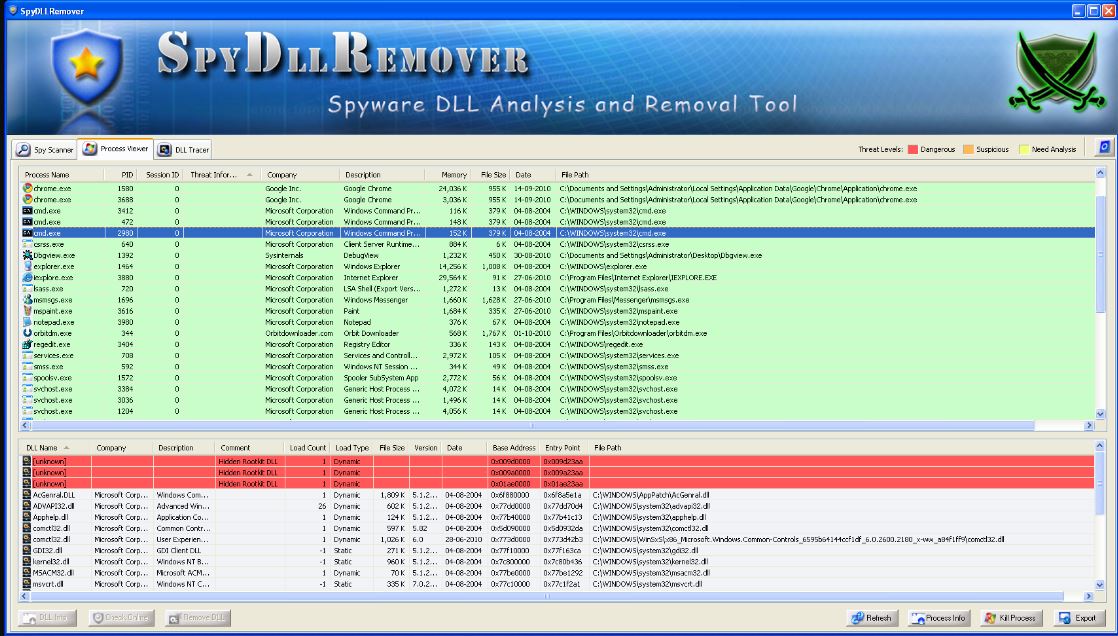
Clean up startup items
One of the key goals of malware is to ensure it relaunches after a shutdown or reboot. The most common approach is to register the malicious executable for startup. There are several ways to do this: changing the target path in a shortcut that’s already in Startup at %USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup, creating an automatically running task in the Windows Task Scheduler, or adding autorun keys in the system registry:
- [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce] — programs that run a single time at the next user sign-in (machine-wide).
- [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] — programs that run when the current user signs in.
- [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce] — programs that run only once when the current user signs in.
What tools do we have for this? First up is Autoruns, which lets you manage Windows startup. It shows all programs, services, drivers, and command files that will launch with the system, and lets you disable them if needed.
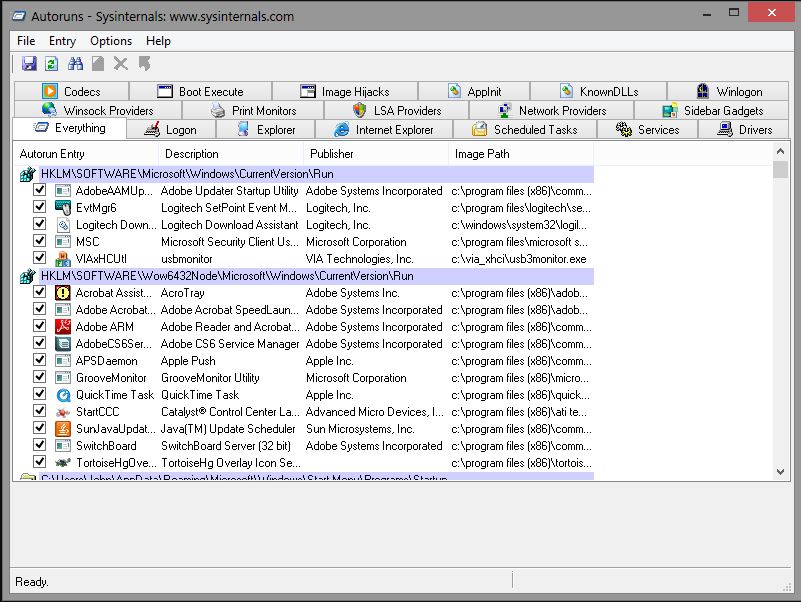
Let’s say a few words about the interface and the tabs:
- Everything — shows all auto-start entries that run when Windows boots
- Logon — all programs that launch automatically at user logon
- Explorer — Windows Explorer shell extensions and other items that auto-start with Explorer
- Internet Explorer — all installed add-ons and extensions for Internet Explorer
- Scheduled Tasks — items triggered automatically by Task Scheduler
- Services — service executables that start automatically at system boot
- Drivers — all driver files that load automatically (kernel and device drivers)
Restoring the Windows Registry
Since the earliest versions of the OS, the Windows Registry has remained a critical system component—essentially a database for storing configuration parameters and settings for the user environment, installed software, and Windows itself. It follows that any malfunction or corruption of the registry can render the OS unusable. The registry, which you open with the built-in regedit utility, is physically stored as several files under %SystemRoot%\System32\config. These files—SYSTEM, SOFTWARE, SECURITY, SAM, and DEFAULT—have no extensions and are accessible only to system processes such as NT AUTHORITY\SYSTEM and LocalSystem. When viewed through the editor, however, they appear as a large hierarchical tree.
The first thing that comes to mind is, of course, to back up these files and, if needed, simply replace any corrupted ones with the backups. But you can’t do that by just copying them from a live OS, and exporting data with regedit may produce an incomplete result. So let’s look at tools that can help with this.
Windows built-in tools for registry recovery
Out of the box, Windows unfortunately doesn’t include a dedicated tool for backing up the registry. All Windows offers is the long‑obsolete NTBackUp from the Windows XP/2003 Server era, or in newer OS versions (Windows 7, 8, 10) its reincarnation as the “Windows Backup and Restore” utility, which only lets you create a full system image (the entire system—not the registry!). So we’ll look at a small example of steps in the recovery console that let you restore the registry manually. Essentially, you replace corrupted files on an infected system with the original registry hives from a previously created backup.
After booting in Live CD mode from the installation disc or from a locally installed Recovery Console (for XP/2003), run the following commands, as described by Microsoft:
// Create backups of the system registry
md tmp
copy c:\windows\system32\config\system c:\windows\tmp\system.bak
copy c:\windows\system32\config\software c:\windows\tmp\software.bak
copy c:\windows\system32\config\sam c:\windows\tmp\sam.bak
copy c:\windows\system32\config\security c:\windows\tmp\security.bak
copy c:\windows\system32\config\default c:\windows\tmp\default.bak
// Delete corrupted files from the OS system directory
delete c:\windows\system32\config\system
delete c:\windows\system32\config\software
delete c:\windows\system32\config\sam
delete c:\windows\system32\config\security
delete c:\windows\system32\config\default
// Copy working registry files from the shadow copy
copy c:\windows\repair\system c:\windows\system32\config\system
copy c:\windows\repair\software c:\windows\system32\config\software
copy c:\windows\repair\sam c:\windows\system32\config\sam
copy c:\windows\repair\security c:\windows\system32\config\security
copy c:\windows\repair\default c:\windows\system32\config\default
That’s it—reboot the machine and check the result!
Advanced Registry Recovery Techniques
As we’ve established, Windows doesn’t offer a decent registry management tool. So let’s see what third-party vendors have to offer.
Registry Backup is a free backup utility that uses the Windows Volume Shadow Copy Service to back up the system registry. It lets you create registry backups and restore from them. Registry Backup • Windows Volume Shadow Copy Service
WinRescue isn’t free, but it’s still worth mentioning. Its primary function is a full Windows restore after a system crash. It can also back up critical system files and other user data. Despite its dated, 90s-style interface, the tool does its job well. WinRescue
- ERUNT — this tool is quite capable. It lets you restore the Windows registry even if the OS won’t boot. After launching, select the registry hives you want to include in the backup and wait for the process to complete. To restore an unbootable Windows 7 system, you’ll need an external rescue disk such as BartPE or the Alkid Live CD; you can also use the Windows Recovery Environment. In those cases, the program must already be installed on the hard drive and a registry backup created beforehand. A good walkthrough of making a registry backup is in this manual: http://itpotok.ru/vosstanovlenie-reestra-windows-7-s-pomoshhyu-utilit-regedit-i-erunt/.
Protect your MBR, and it’ll protect you.
Let’s talk about the MBR. Remember what that is? We won’t dive too deep into theory. In short, the MBR (Master Boot Record) is the block of code and data used to kick off the boot process from a hard drive. That’s why, in Russian, it’s often referred to simply as the boot sector(s). The MBR hands off control to the partition on the disk that should execute the next stage—in our case, loading the operating system.
Why does this matter? Because since the MS-DOS era of the 1990s, malware has been able to infect not only executables but also boot sectors, ensuring it runs at system startup. To defend against such attacks, BIOS even introduced a Boot Virus Detection option that protects the hard drive’s boot sector from modification at the firmware level of the basic input/output system. If the malware’s routine had bugs, the MBR could be corrupted, making the system unbootable. And there were also strains that intentionally wiped boot sectors.
The point is that the MBR resides in a “hidden” area of the disk, and not every standard backup tool will include it.
Repairing the MBR in the Recovery Console
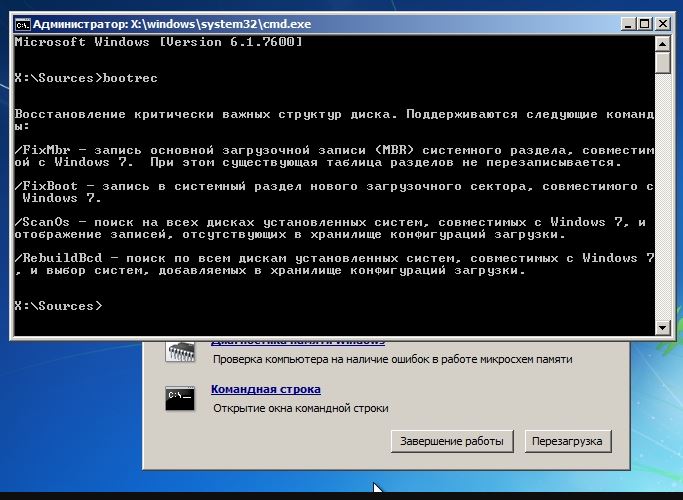
Back in the Windows XP era, the Recovery Console was often used to repair a system without reinstalling the OS. You could install it onto the hard drive and select it as a boot option at startup, or run it from the OS installation CD. The console was especially useful when you saw the NTLDR is missing error on boot, or when system files like bootfont.bin, ntbootdd.sys, ntdetect.com, and boot.ini were corrupted. Regardless of the cause, you would typically enter a sequence of commands in the console.
Fixmbr
Fixboot
The fixmbr command could detect and automatically repair errors in the MBR. The fixboot command marked the partition as bootable, wrote the NTLDR boot code to the boot sector, copied the required system files to the partition, and generated boot.ini. On the next boot, the system would typically return to a working state.
Advanced MBR Recovery Tools
A universal way to protect the MBR is to create a backup and, if necessary, restore it to the production system. Since, as we’ve already noted, boot sectors can’t be edited from within a running OS, you’ll need to use specialized tools.
Comodo Backup is a free utility designed to create images of hard drives, their partitions, and the MBR. For our purposes here, we’re specifically interested in the MBR.
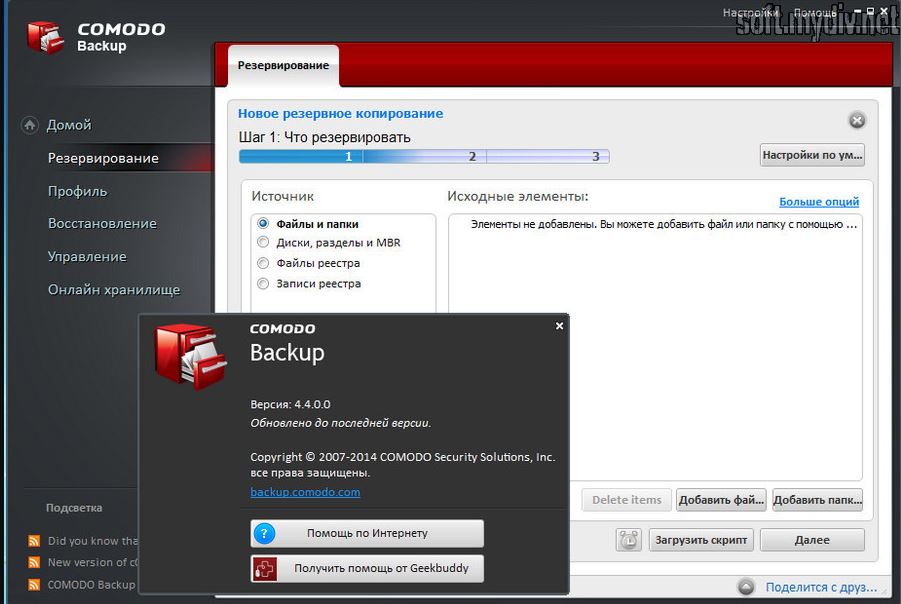
Launch the tool in Live CD mode, choose the MBR backup option, pick a destination, and your backup is ready. If the bootloader on the infected machine gets corrupted, you can simply restore it—the whole process takes just a few minutes.
If you use Linux as your OS, you can use the built-in utilities. There’s also a solid guide to backing up the MBR on Linux using Ubuntu as an example.
From MBR to UEFI and GPT
In 2010, a new technology called UEFI replaced the long-standing legacy BIOS, bringing boot-process changes that nudge us away from MBR and toward GPT. UEFI is essentially a wrapper or interface between the OS and the firmware baked into the motherboard’s chips. As a result, during boot initialization UEFI uses GPT rather than the classic MBR. We won’t dive into the theory here; for those who want more detail, see “Сравнение структур разделов GPT и MBR.”
Since GPT’s layout differs from a classic MBR, you can’t back it up using the method described above. The solution is to create a full system image—for example, with the built‑in utility “Windows Backup and Restore”, the free suite Paragon Backup & Recovery Free Edition, or the commercial Acronis True Image. We’ll discuss system backup procedures in more detail a bit later.
System File Recovery
Malware often corrupts system files—either because of its own bugs or while resisting removal—leaving the OS unusable. Reinstalling the OS isn’t our preferred option here: it takes much longer and, importantly, wipes application settings and other valuable data. Instead, the system should be repaired surgically, targeting exactly the areas that were damaged.
Checking and Repairing Windows System Files
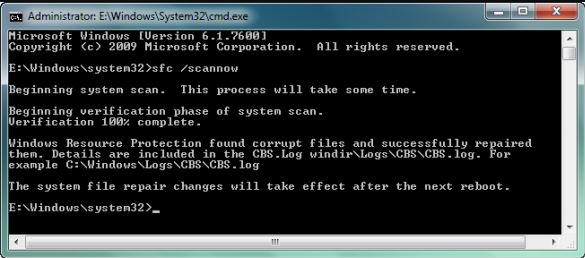
The built-in SFC.EXE (System File Checker) utility has been included in all versions of Windows since Windows 2000. It’s designed to verify and repair system files. Protection mechanisms for critical system components—typically executables (.exe), libraries (.dll), and driver files (.sys)—check file integrity and, if any are damaged or missing, restore them to their default state.
In practice, you can check the integrity of Windows system files using a console command.
sfc /scannow
However, sfc / may fail to fix errors in system files. In that case, as an alternative, you can enter the following in the Command Prompt:
findstr /c:"[SR]" %windir%\Logs\CBS\CBS.log >"%userprofile%\Desktop\sfc.txt"
This command will create a text file sfc. on your desktop listing the files that couldn’t be repaired. You can review it and, if needed, manually copy the required files from another computer with the same version of Windows or from the original OS installation media.
Most critical system files:
- Ntoskrnl.exe — the kernel image for the Windows NT family of operating systems.
- Hal.dll — the Hardware Abstraction Layer (HAL), a system component that sits between the physical hardware and the software running on the machine.
- kernel32.dll — a core dynamic-link library in all versions of Microsoft Windows. It exposes fundamental Win32 APIs, including memory management, I/O, process and thread creation, and synchronization primitives.
- NTLDR (and later IA64ldr and Winload) — the boot loader for Windows NT–based operating systems.
- ntdetect.com — a component used during the boot process of Windows NT up through version 6.0 (Vista).
Quick driver restore
Malware can install its own drivers—for example, to intercept keystrokes or to hide its presence on an infected system. In doing so, it might remove the original driver or try to patch it and break it. Here, we’ll cover how to quickly restore drivers running on the system to their original, known-good state. The best approach is to create a baseline (golden) set of drivers from a healthy system and, when needed, restore them all at once instead of poking at each one individually. We’ll use a few tools to achieve this.
- SlimDrivers — one of the best driver-management utilities. It can scan for and update device drivers, and restore them from backups.
- Double Driver (https://double-driver.en.softonic.com/) — a lightweight, free utility for backing up drivers. All you need to do is create a driver archive from the source system, save it somewhere safe, and later open it in the same program to restore the drivers back into the system. That’s it.
Fixing File Explorer and Other System Errors
Even after you restore the system and remove the malware, you can be left with unpleasant residue—the aftereffects of the infection. For example, file associations may be broken, the built-in Windows Task Manager might be blocked, the Registry Editor (regedit) disabled, or the Control Panel inaccessible. What can you do? The good news is that nearly all of these changes are reversible. You could dig through the registry by hand, hunt down the relevant configuration keys, and reset them to their defaults, but instead we’ll lean on specialized tools built for exactly this job. So, let’s get started!
Fix for Windows — a collection of universal fixes and patches for Microsoft Windows. The utility bundles multiple problem areas under one roof; for example, fixes are grouped into categories like Boot, Speed, Desktop, LAN, Other, and so on. As you switch between categories, you can tick checkboxes next to the items you want to tidy up—such as fixing encoding and font issues, restoring the language bar, enabling/disabling UAC, or showing hidden files.
Microsoft Easy Fix — a free native Windows troubleshooting tool that addresses issues interfering with normal OS operation. It helps detect and resolve common problems with both Microsoft and third‑party software that can affect system stability and functionality. https://support.microsoft.com/ru-ru/help/2970908/how-to-use-microsoft-easy-fix-solutions
- FixWin 10 — a free utility that can automatically fix many annoying errors and other Windows issues (not just Windows 10). It offers modules with self-explanatory names to tackle common problems:
- File Explorer — fixes Explorer-related issues (e.g., desktop won’t load after sign-in, WerMgr/WerFault errors, CD/DVD drive not working, and more).
- Internet and Connectivity — addresses network problems (reset DNS, reset the TCP/IP stack, reset the firewall, reset Winsock, and similar).
- System Tools — repairs issues launching Windows system tools (e.g., Task Manager, Command Prompt, or Registry Editor disabled by an admin), re-enables System Restore, and restores security settings to their defaults.
- Windows Repair Portable Free — a free, portable utility for fixing a wide range of system issues. It can reset Windows settings to their defaults, which often resolves many problems, such as incorrect file permissions, Windows Update failures, issues with the built-in firewall, and more.
danger
There’s no such thing as a completely secure system. No matter what security measures you take, there’s always a chance a threat will materialize. Malware can exploit a zero-day vulnerability or undocumented OS features that you can’t proactively defend against. Your best safety net is to make regular data backups.
Resetting the Network Stack
Depending on its built-in algorithms, the malware can tamper with system network settings—altering traffic routing, spoofing DNS resolution, and so on. As a result, some hosts, websites, and cloud services may become unavailable or behave incorrectly. The malware’s code may also contain bugs or misfire, which can ultimately bring our entire network down.
Restoring the hosts file
Malware loves to tamper with the hosts file located at %SystemRoot%\. It’s just a plain text file that stores a local mapping of domain names to IP addresses. When resolving a hostname or website, this file is checked before the DNS servers configured on the network adapter. Attackers modify it to block access to antivirus vendors’ sites and to repositories that host updated AV signatures.
Another scenario is abusing this file for phishing—redirecting requests for legitimate services like social networks or online banking to their fake look-alikes. The fix is straightforward: replace the tampered hosts file with the original (e.g., from a backup), or even with an empty file that has the correct name and resides at the correct path. It’s also wise to verify where the hosts file is expected to live on this system instance, since any default location can be changed. You can find the exact path in the registry key at HKEY_LOCAL_MACHINE\.
Restoring Windows network services
The second thing to check when restoring network functionality is the status of running Windows network services. There are cases where malware deliberately stops a network service or pauses it for its own purposes, and then fails to restart it or does so incorrectly. As a result, network communication gets blocked. There are a couple of ways to check. You can go to Control Panel → Administrative Tools → Services, or quickly launch the same console with Win + R and typing services.msc. You’ll see a list of all Windows services; in this case we’re only interested in a few network-related:
- DHCP Client
- DNS Client
- Web Client
- WWAN AutoConfig
- IPsec Policy Agent (if you use VPN tunnels)
- Windows Firewall (if you use the built-in firewall)
- Remote Procedure Call (RPC) Locator
- Routing and Remote Access (you’ll know if you actually need it)
These services should be in the Started (Running) state. If they aren’t, click each listed item to open its properties window and use the appropriate button to start or restart the service.
The truly professional approach is to use the console. Open CMD, type net or net , and you’ll see which services are currently running.
To start a service from the console, just run: net . You don’t need to memorize all service names—use sc to view detailed information, or check the ready-made list here: готовый список тут.
From the command line, you can start any service with net ; for example, to start the DNS service:
net start DNS
So we’ve got the services sorted, but the network is still down or intermittently failing? Let’s keep going!
Fix the routing and check the ports
Malware can add dynamic routes to the local Windows routing table and thus change how network traffic is exchanged with other hosts. For example, if your machine gets all its network settings via DHCP, a malfunctioning DHCP service can leave you without internet access. Time to dive back into the console!
To remove the new routes and restore the routing table to its original state, run the following commands accordingly:
route print
route delete *
Sometimes that’s not enough, and you need to reset the settings to their defaults. Run the following commands.
netsh interface reset all
netsh winsock reset
netsh firewall reset
netsh winhttp reset proxy
These commands overwrite the registry keys with their default values (as after a clean Windows reinstall):
SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
SYSTEM\CurrentControlSet\Services\DHCP\Parameters
If the system obtains its network settings via DHCP, the following commands will come in handy. For example, if the DNS server isn’t responding or the server’s DNS address can’t be resolved, you can reset just DNS with this command:
ipconfig /flushdns
If that doesn’t work, you can resort to more drastic measures by running…
ipconfig /release
// wait a few seconds or minutes
ipconfig /renew
These commands will fully refresh the network configuration assigned to your machine by the local DHCP server.
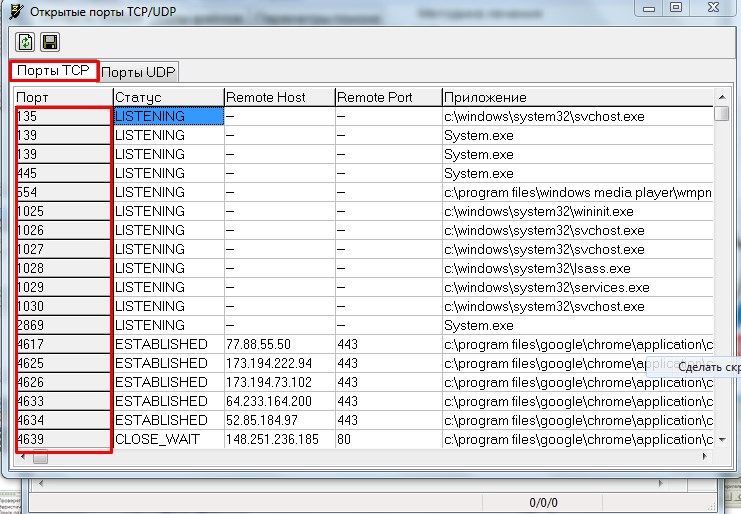
Now we need to talk about ports—the interfaces through which packet exchange actually happens. It can happen that malware has locked a critical system port or is listening on an open one for commands coming from the outside. The list of the most important system ports is fairly short; you can just memorize it:
- SSH 21;
- DNS and DHCP 53, 67, 68;
- Email 25;
- Web 80, 81;
- RPC 135, 443, 445.
You can find a complete list of network ports in any reference. In most operating systems, you can view the status of network services using the command
netstat -an
Netstat command options:
-
-a— show all connections and listening ports -
-o— show the numeric process ID (PID) owning each connection -
-n— show raw IP addresses and port numbers instead of resolving DNS/service names
The output shows the current state of the connection:
- ESTABLISHED — the TCP connection is up; either a remote host connected to you or you connected to a remote host.
- LISTENING — the machine is waiting for incoming connections on that port; a process has the port open and is listening.
- TIME_WAIT — a recently closed TCP connection is waiting out a timeout to ensure any late packets are handled before the socket/port is fully released.
The output shows a long listing with IP addresses and port states. Unfortunately, it doesn’t map sockets to a process in memory, so you have to resolve that manually. The value after the colon (:) is the PID of the process bound to that IP/port (i.e., the port is open or a connection is established). Next, look up that PID in the process list with tasklist and identify which application owns that network connection from the output. Alternatively, if you’d rather not use tasklist, you can use Task Manager: press Ctrl + Shift + Esc to open it, go to the Processes tab. In the View menu, choose Select Columns and enable the PID column. Then find the process by that PID value.
If you’d rather not work in the console, you can use GUI tools for visualization such as Process Explorer, TCPView, and Nirsoft CurrPorts.
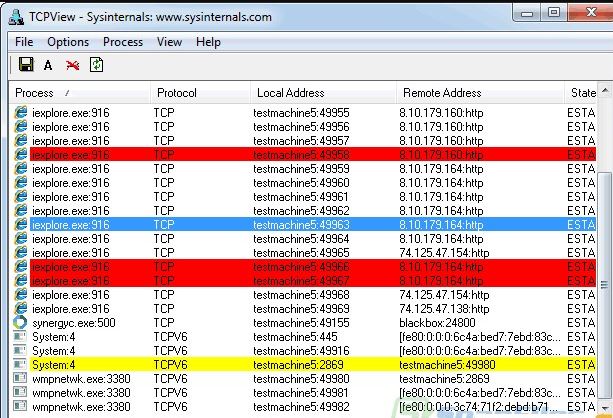
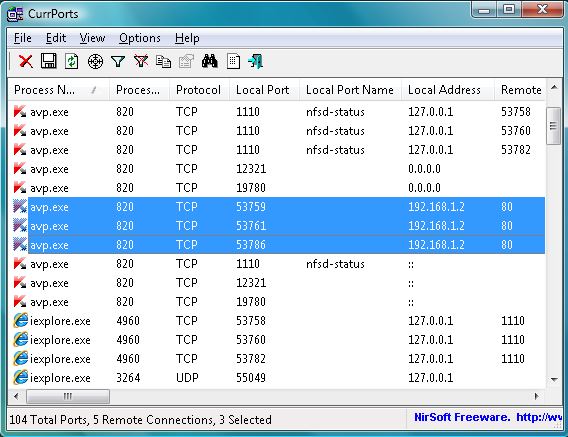
You can find the list of network services and their corresponding port numbers for NT-based systems in the file %SystemRoot%\ — it’s essentially a plain text file with no extension that you can open with any text editor.
Finally, for everything described above that we did by hand, you can use tools—for example, WinSock XP Fix. This utility restores the system’s network-related registry keys to their default values. In addition, it also:
- Checks the hosts file to ensure the localhost entry is correct (it must point to 127.0.0.1).
- Creates a backup of the current system settings (if the user opts in).
- Disables all network adapters and resets their configuration.
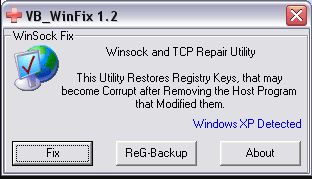
The native GUI tool we mentioned, Microsoft Easy Fix, performs the same actions as running netsh int ip reset and netsh winsock reset. A similar utility, Reset TCPIP, bundles all the console command combinations we described into a single GUI.
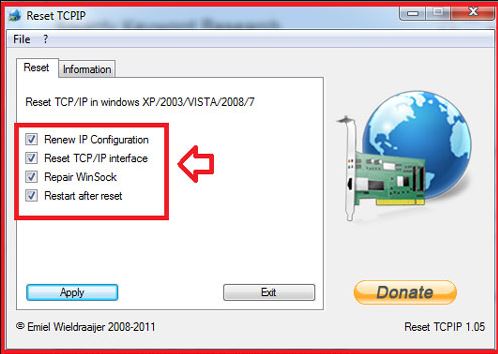
NetAdapter Repair is another solid free tool designed to fix a wide range of network- and Internet-related issues in Windows. A brief list of its features:
- Clean up and repair the hosts file
- Enable Ethernet and wireless network adapters
- Reset Winsock and the TCP/IP stack
- Flush the DNS cache, clear routing tables, and remove static IP configurations
- Restart NetBIOS

Live CD to the Rescue
Staying on topic, we couldn’t ignore Live CD builds aimed at system recovery. Originally, the Live CD was positioned as a tool for administrative tasks: prepping hard drives, quickly accessing data stored on disks, and so on. Today, Live CDs are more like a universal lifeline for bringing a system back to life after various crashes, including post‑malware incidents. Their main advantage is that all the tools come bundled under one roof and can run in parallel. The downside: to boot into a Live CD environment you have to reboot the machine, which in some cases is a nonstarter.
Every major antivirus vendor offers a free bootable recovery disk for system repair. We’ll give them a quick once-over without diving into details—after all, we agreed at the outset to stick to tools that aren’t straight-up antivirus software.
Antivirus Vendors’ Live CDs
- Kaspersky Rescue Disk (http://support.kaspersky.ru/viruses/rescuedisk) — as you’ve probably guessed, this is a Gentoo-based Linux live rescue disk from the Russian vendor Kaspersky Lab. The recovery environment includes a web browser, a file manager, and a Windows Registry editor. It can also update Kaspersky’s antivirus definitions.
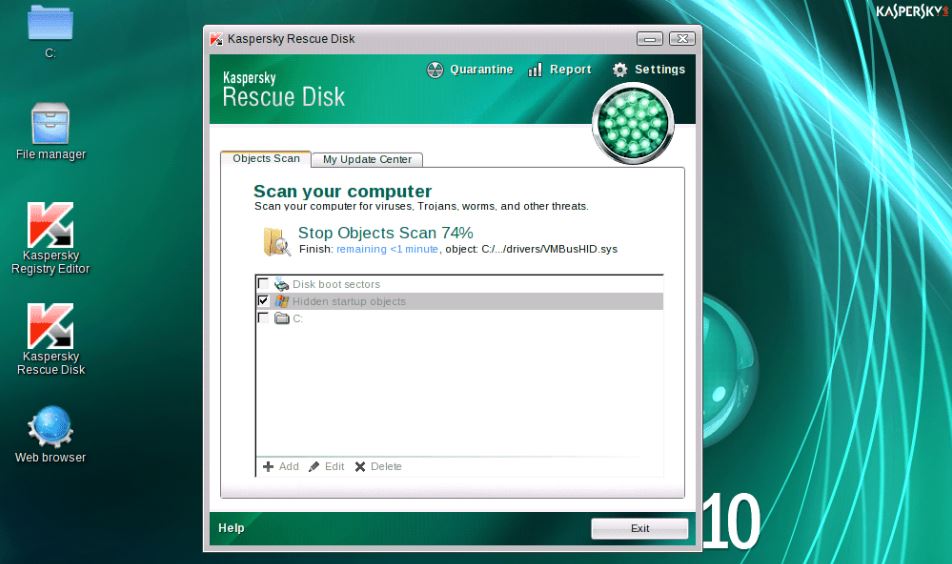
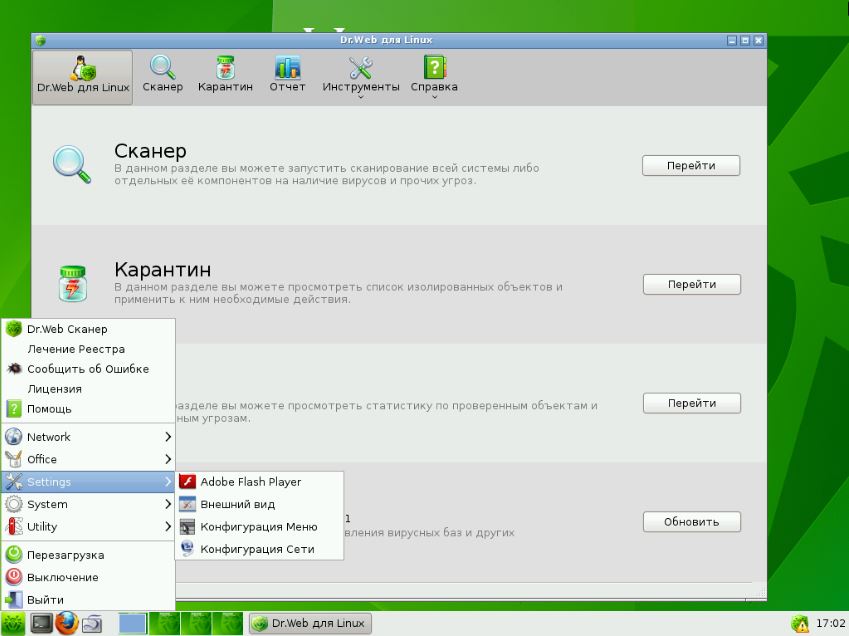
- Dr.Web Live CD (http://www.freedrweb.com/livedisk/) — a Gentoo Linux–based live CD from Dr.Web. The toolkit includes a RAM diagnostics utility, a Windows Registry editor, antivirus signature updates, internet access via Mozilla Firefox, two file managers, and the Dr.Web CureIt! on‑demand antivirus.
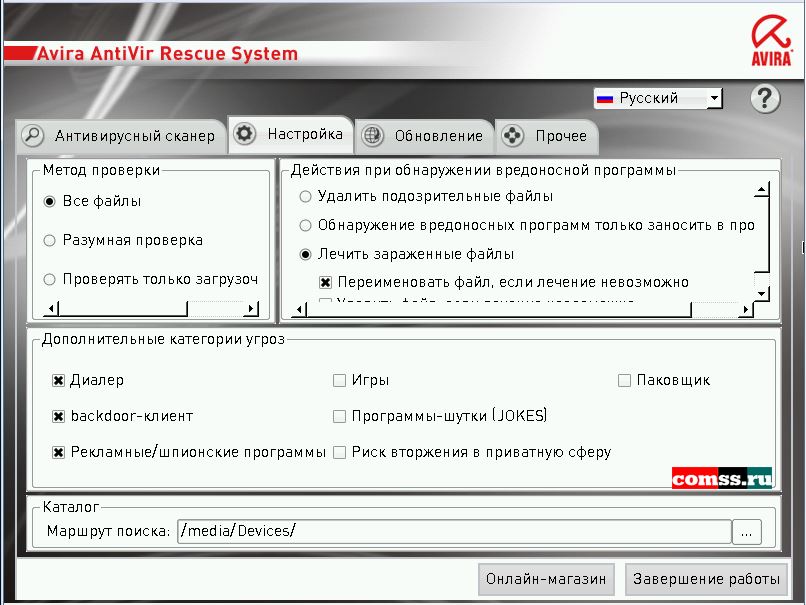
- Avira Antivir Rescue System — a Live CD from the German vendor. A solid toolkit: access your data via a file manager, use the Avira Registry Editor, and browse the web with Mozilla Firefox. It also includes TeamViewer for remote sessions and GParted for disk repartitioning.
General-Purpose Live CDs
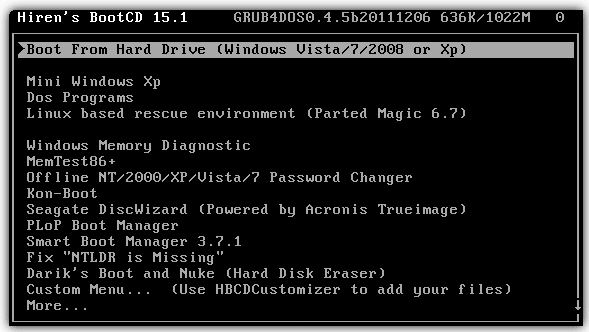
- Hiren’s BootCD is a compilation disc that bundles a wide range of utilities, including ones that run in DOS mode. The distribution includes not only a bootable ISO image, but also a tool to burn it to an optical disc and the HBCDCustomizer utility for creating custom bootable images.
- SystemRescueCd (http://www.system-rescue-cd.org) — a well-known, general-purpose recovery environment based on Gentoo Linux. It includes tools for disk work—partitioning, diagnostics, and partition backup/restore. It can mount Windows NTFS partitions with read/write support. It also provides network configuration and service tools, rootkit detection utilities, and an antivirus.
- Alkid Live CD and USB — a feature‑packed, versatile Windows XP–based bootable recovery environment. Boots from virtually any media—CDs, USB flash drives, USB hard disks, and more. Includes up‑to‑date antivirus tools; disk and image utilities; backup and system repair; data and password recovery; creation of new administrator accounts; rollback to system restore points; and much more.
How to Stay Malware-Free: Essential Tips
Don’t run as a local administrator. Enable UAC.
It’s obvious, but we’ll keep repeating these simple truths until at least 15% of users start treating them as actionable guidance. 🙂
Keep your system up to date: install security patches promptly
Here they are, our old and new friends: WannaCry, Petya, Conficker, and the (new) Bad Rabbit.
They actively exploit vulnerabilities in both system software and applications. Keep your applications up to date—especially your browser. Remember that malware targets not only the OS but also browser engines and their components.
By the way, if you think this advice is dumb, here’s something to chew on: there are people around you—tens of thousands of them—running computers with software that still contains decade-old (!) vulnerabilities.
The numbers don’t lie: software vulnerabilities found many years ago may still be unpatched, and on Windows 10 it’s possible to exploit a bug discovered all the way back in 1997. Things aren’t much better with browsers and mobile platforms.
Harden your browser
Set it up right
A useful browser setting is “Warn about unsafe sites,” which will alert you whenever you’re about to visit a suspicious (compromised or malware-infected) website. Similarly, the browser will notify you if a site is using the insecure HTTP protocol instead of HTTPS. Many browsers can also detect when you reuse a password in web forms and remind you why using the same password across services is a bad idea.
You can find a solid guide to security settings for various browsers here. And here are examples of hardened security configurations for the latest version at the time, Internet Explorer 11.
Ditch the Scripts
To harden the browser, minimize the amount of active code that can run—for example, disable Java execution. Ad blockers for ads, banners, and pop-ups, such as AdBlock and Adblock Plus, are also very helpful.
Install browser extensions
Helpful browser extensions can reduce the risk of infection. Below are extensions for the three most popular browsers worldwide: Chrome, Opera, and, of course, Internet Explorer—since many users still run older versions of Windows where IE is the default.
For Chrome
AdBlock — a popular blocker for intrusive banner ads. On compromised sites, malicious code often hides in innocuous-looking banners and links masquerading as pop-ups. AdBlock gets rid of all that.
Flash Block — some sites use Flash for “creative” cookie harvesting and tracking. Installing Flash Block gives you manual, per-page control — you decide whether to allow Flash content to load.
ScriptSafe — an extremely useful extension that gives you control over sites using JavaScript.
BugMeNot — ever forced to hand over your email to register for a site or forum, or just to read an article? BugMeNot offers a safe, anonymous alternative.
KB SSL Enforcer — an extension that forces the use of SSL (HTTPS).
WOT (Web of Trust) — a toolkit for safer browsing. It can also warn you about risky sites that scam users or spread malware or spam.
For Opera
- HTTPS Everywhere — a browser extension that rewrites website requests to enforce HTTPS. It encrypts connections, making your browsing safer.
- Avira Browser Safety — Avira’s browser web filter with safe search, safe browsing, anti-tracking, and an AdGuard-powered ad blocker.
- McAfee WebAdvisor — a free plugin from Intel Security that protects against malicious, phishing, and scam sites, as well as malicious downloads.
- uMatrix — an interactive point-and-click firewall for the browser that lets you block scripts, frames, plugins, ads, and other request types.
- Netcraft Extension — an extension that protects against phishing, online fraud, and cross-site scripting, and provides comprehensive information about the websites you visit.
For Internet Explorer
- LastPass — a password manager. It offers the same capabilities you’d expect from standalone desktop password managers, including password generation and secure storage.
- Web of Trust warns you if a site is potentially unsafe to visit.
- FavBackup — a tool for backing up and restoring your Internet Explorer profile and settings.
Don’t be surprised to see IE here—we don’t recommend anyone use this highly vulnerable browser, but until quite recently it was required by some online banking systems.
Use a VPN
Beyond the obvious anonymity benefits, a VPN also helps ensure that if your traffic is intercepted, an attacker won’t be able to get what they’re after. If you’re considering free VPN options, you can use OpenVPN as the client and fetch connection configs from FreeVPN. But honestly, we all use paid VPNs, and we wouldn’t recommend chasing free ones. 😉 Here are some noteworthy commercial VPN services:
Private Internet Access — One of the top VPN services (judging by its award count). PIA’s key selling point is that it not only encrypts traffic but also anonymizes it and masks your geographic location. You get access to roughly a thousand servers across ten countries. PIA follows a strict no-logs policy, doesn’t block any protocols or IP addresses, and doesn’t store records of user activity. Pricing starts at $7 per month, and you can connect up to five devices.
CyberGhost VPN — A long-standing, well-regarded VPN provider that, like the others on this list, advertises a no-logs policy and no restrictions on protocols or traffic types. You can choose from hundreds of servers in 23 countries. Plans start at $7 per month; connecting more than one device requires an additional fee.
ZenMate — A well-known VPN with a rich feature set: AES-128 traffic encryption, built-in browsing acceleration, and high-speed servers worldwide. Pricing starts at $5 per month, with a seven-day free trial.
These are just a few examples of VPN providers. You can check the rankings and choose for yourself.
How to deal with annoying pop-ups?
It happens all too often: you close a page on some sketchy, vulnerable site—and a flood of full-screen pop-ups opens, with no standard way to dismiss them. Sometimes mouse control gets blocked, too. What can you do?
- Minimize the window with Win+Home or Win+D, open the standard Windows Task Manager using Ctrl+Alt+Del, and terminate the process. Note: any unsaved data will be lost.
- Press Shift+Esc to open your browser’s task manager; this lets you kill only the thread used by the pop-under malware without terminating the parent process.
Use a Secure DNS Resolver
It’s a good idea to configure your router or network adapter to use DNS servers that block malicious content:
- Yandex.DNS with IP addresses
- Cisco OpenDNS
- Norton ConnectSafe, supported by Symantec
Lock Down Removable Media and Disable AutoRun
The autorun.inf issue should have been put to rest years ago, so permanently disable Autorun.
It’s best to check any untrusted USB flash drives in a clean virtual-machine sandbox, or mount the storage volume in Linux, where they’re far less of a threat. Untrusted USB flash drives are real trouble; in my experience, about 80% of them are infected. 🙂
Configure your firewall
A properly configured firewall helps reduce your attack surface: it closes unused ports, kills stray or unsolicited TCP/UDP sessions, and monitors applications that initiate outbound connections. Linux users traditionally favor iptables, which you can configure from the command line or via a familiar GUI. Windows has a built-in firewall that you can manage through the native interface or with a more flexible GUI wrapper like Windows Firewall Control.
Forget attachments and suspicious links
Nothing to add here. If you’re really curious, open it in a Linux virtual machine :). To check whether a site is blacklisted and whether it has dangerous redirects and suspicious scripts, you can use free online scanners like Sucuri, ReScan.pro, and the well-known VirusTotal. Also see: are there dangerous redirects on it.
What gets a sysadmin in trouble? Not having backups. That applies to you too.
Commercial backup solutions are getting all the buzz right now, offering impressive capabilities—everything from protecting data against ransomware to backing up your social media content. Free options aren’t as convenient, but they’re still very much alive and kicking.
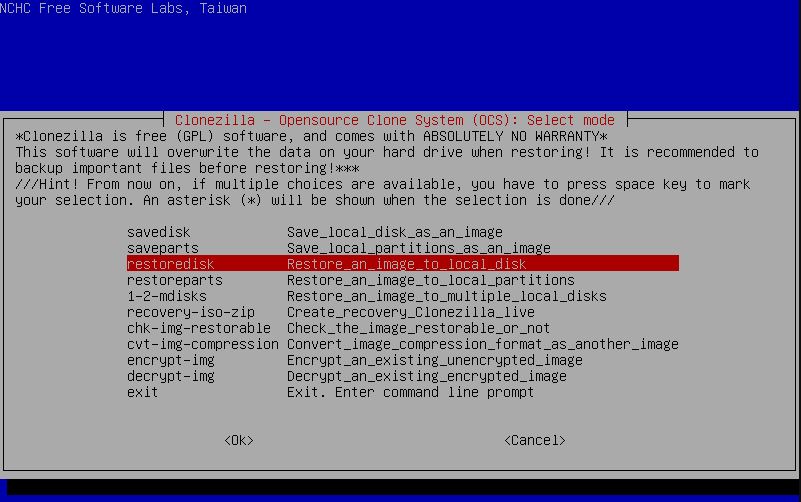
- Clonezilla is free and open-source software. The tool uses a step-by-step, wizard-driven workflow and runs mostly in a text-based environment (no GUI). It’s well-suited for cloning entire disks or individual partitions, and for creating backups and performing disaster recovery.
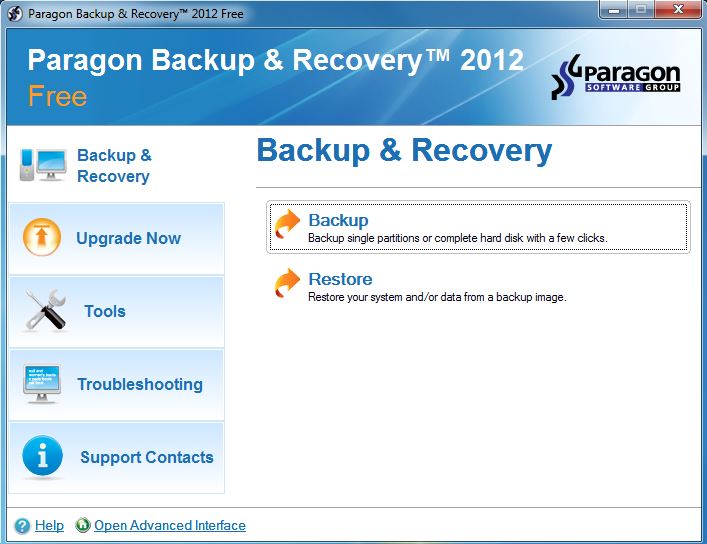
- Paragon Backup & Recovery 16 Free Edition (https://backstage.paragon-software.com/free/br-free/) — a suite of utilities from Paragon Software that lets you create, format, and delete partitions; hide or unhide them; assign drive letters and change volume labels; and run file system integrity checks. Notably, backups can be stored in a dedicated Backup Capsule—a hidden partition that the operating system cannot mount or even see.
Outro
Modern malware exploits every trick and vulnerability to compromise a victim’s system. Defending against it requires a blend of all the countermeasures discussed here. Relying on a single tool won’t cut it—only by deploying the full arsenal do you stand a real chance of pushing back effectively.
