At first, it is worthwhile to give a brief list of main software components included in the kit:
- core 3.12 — it is rather fresh, even though new core versions are being coined now nearly every month;
- Vidalla 0.2.21 with Tor 0.2.4.21 — it is also the latest product;
- GNOME 2.30.2 — yes, Tails still has not abandoned the old good second GNOME;
- as a browser, Iceweasel is used with standard plugins for anonymity — Torbutton, FoxyProxy, Adblock Plus, and NoScript.
Let’s discuss a start-up. It takes about 15 seconds and, if you are attentive, you can notice the ‘Debian 6.0.9’ lettering; hence, the package system in the distribution kit is deb. Right upon starting, you can set a required interface language and then have a look on additional settings, if you wish, where you can set a root password (otherwise, it will be impossible to perform certain tasks), some Tor options, and, yes — Windows XP camouflage.
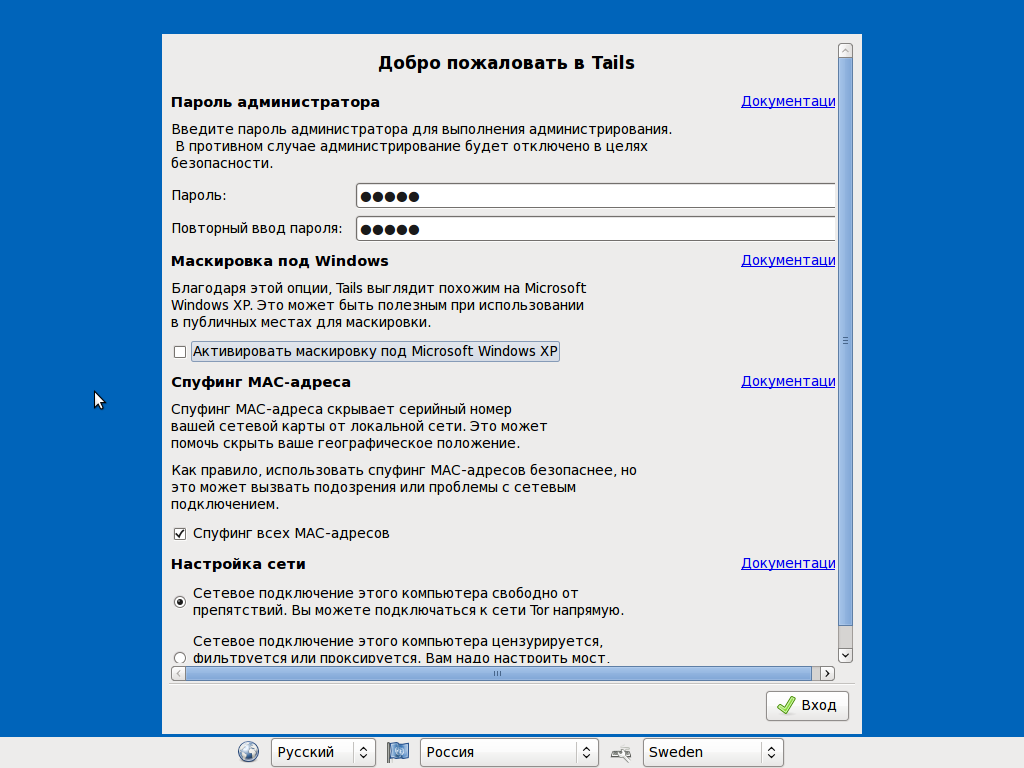
The camouflage should be discussed in somewhat greater detail. Very realistically looking if you take a superficial glance, it is but the same XP’s green wallpaper, windows design, and imitation of a task bar, which is not quite successful (just look at Start button, when you set Russian language, and keyboard layout indicator). Only a blind man will not notice non-conformity with XP when attempting to open the Start menu. All in all, this option can be useful only among extremely careless people.
Upon logging, you will see a warning message on system time and if you launch it in virtual environment — a warning on possible data interception. Looking conventionally without camouflage, the pop-up messages in the top right part of the screen seem suspicious, with camouflage enabled.
In addition, after launching you will have to wait for some time until Tor starts, which depends heavily on synchronization with NTP server. It is only now that you can start working.
Starting from flash drive and using Tails
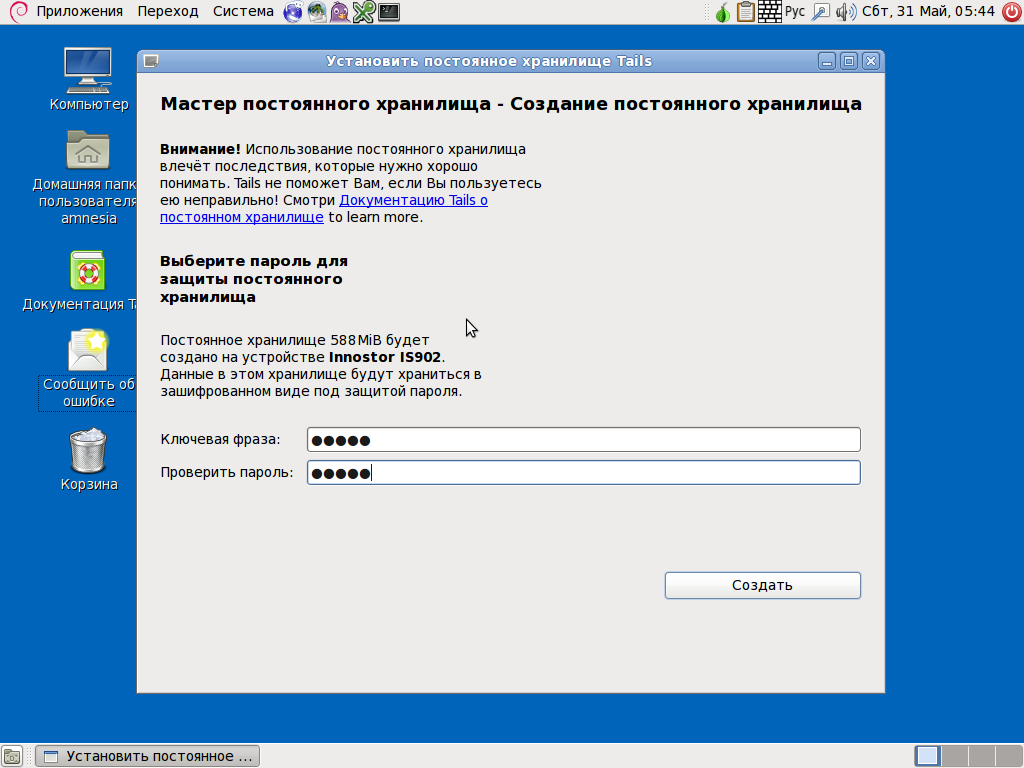
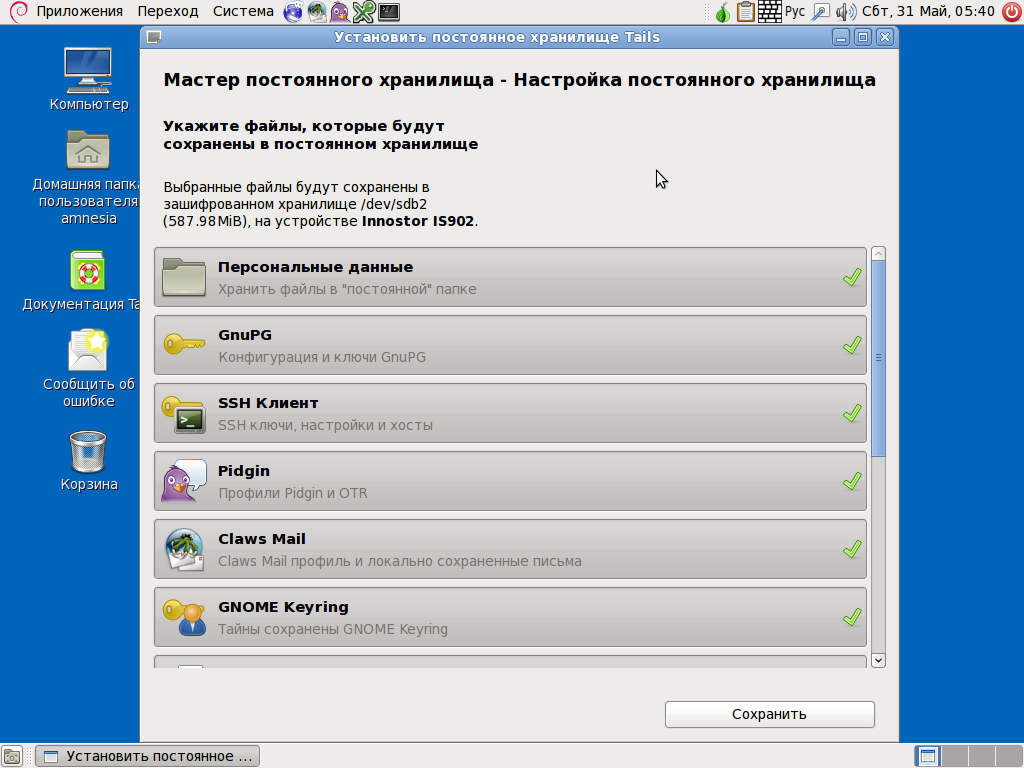
Tails also supports installation on memory sticks. This can be useful, e.g., if you are planning to launch it on netbooks with no drives for CD reading. To create a bootable flash drive, select ‘Applications -> Tails -> Tails Installer’ and the required option. After installation and start-up, you can create a persistent storage on a memory stick. Of course, it will be encoded. The principle of persistent storage can be detailed as follows.

The creation takes place as follows: at first, it is verified if the distribution is started from a memory stick, if it is created using the Tails installer, if there has been a persistent storage created already… If all conditions are matching, tails-persistence-setup program then assigns all free space left in memory stick to Luks container with TailsData label, formats it to ext3 (selected because logging mode, by default, affects metadata only; hence, if a life cycle of a memory stick would reduce it, the effect will be insignificant), and transmits the rights of ownership to a standard Tails user. As an encoding algorithm, AES-CBC-ESSIV is used, a currently considered standard algorithm for Luks, with SHA-256 hashing.
Upon creation of crypto volume you will be asked: What data are you really going to store in it? And only after rebooting you will be able to select, whether to use it or not, and if yes, whether to use it as read-only, or as read and write. By the way, the backend, tails-persist, supports connection to several persisting storages whereas GUI does not support this.
After the work with the data to be published, you must make a cleanup in order to delete any data related to you — in this case, I don’t mean stylistic elements (though they are also implied, because otherwise there is a risk of de-anonymity), but metadata, which also contain a lot of sensitive information. This task is performed by Metadata Anonymisation Toolkit. It supports (in full or in part) deletion of metadata from the following files:
- JPEG — deletion of exif and data written by Photoshop;
- Open Document — deletes meta.xml file;
- MS Office documents (unfortunately, the stated support only concerns the up-to-date formats, e.g., docx);
- PDF — deletion by re-rendering using Cairo;
- archives (TAR and ZIP) — repacking;
- MP3 — deletion of ID3 tags;
- FLAC and Ogg — deletion using mutagen (Python module).
As stated, Tor shall be used for network access. Despite the possibility to use Unsafe Web Browser, this is highly undesirable. To reduce the probability of IP address determination through a compromised application (sending command ‘GETINFO address’ to the management port), this port is only accessible to vidalla user, in the name of whom Vidalla is started. However, there is a filtering proxy server and, therefore, certain operations, e.g., change of Tor user can be accessed from unauthorized programs, too.
As it is well-known, DNS does not work via Tor because of lacking UDP support in it. Nevertheless, Tor has a resolver functionality limited by requests of type A. But, you know, programs can bypass the system resolver! So, Tails developers have made provisions for this by disabling any outgoing traffic to UDP port 53, if the traffic has been initiated by undefined user. Moreover, there is ttdnsd in the distribution kit, which processes requests of other types by transmitting them to OpenDNS, in the form of TCP packets, through Tor. The only reason why ttdnsd is not used as a resolver by default is that even now it still contains flaws.
A separate mention should be made of iptables settings. Being configured through Ferm front-end, it rates DNS requests, enables Tor and I2P (by the way, UDP traffic can be encapsulated in the I2P packets), while taking into account UID. Since IPv6 Tails is not supported, its traffic is dropped.
When deleting files from Nautilus, they are destroyed using its extension, Nautilus Wipe, which, in its turn, uses utilities from secure-delete package. Remember that their correct operation is not guaranteed on logged file systems (in particular, on ext3).
As a mail client, Claws Mail is used, which, in addition to rating, is configured so that Message-ID heading does not contain sensitive information. Moreover, HTML is disallowed in messages by default.
Pidgin is configured so that it does not make records in the log and submits but minimum information about itself, using for that as little plugins as possible — virtually, there are only IRC and Jabber available among all available protocols. When logging to the system in the case of IRC, an arbitrary nick is selected to be used in future. In addition, it is possible to use OTR over Jabber, OTR being a protocol add-on which ensures communication security. One of its features is deniability of encoding based on deniable encoding mode AES — CTR; deniability of this mode consists in the possibility of message spoofing (“I am not me, the cow is not mine”).
There is no swap support as such — a pad is placed instead of /sbin/swapon.
It is also worth telling about one more Tails feature – RAM rewrite to prevent content restoration. This is ensured as follows: upon regular switching power off (using shutdown) or physical removal of Tails media, kexec functionality starts another core, with sdmem utility being called from this core. Tails uses the fastest method of rewriting, when memory is padded with zeros only once — the developers state that it’s more than enough. In this case, if you remove a memory stick, a harsh shifting to this core will take place instead of normal closedown.

Conclusion
The distribution kit developers have done enormous work to put together a vast variety of anonymity-providing tools. However, perfection has no limits. Right now, one may specify two features which it would be nice to have implemented in the kit.
First, ‘hidden’ containers but designed in such a way that a record to an ‘open’ container would lead, with a large degree of possibility, to damage of the ‘hidden’ one (by some evidence, a similar technology has been used by military intelligence: careless development of captured photos inevitably led to elimination of the second, hidden layer).
Second, it would be useful to have options for selecting the degree of ‘persistent storage’ destruction — super quick (rewrite of Luks volume heading only), quick (rewrite of a volume heading and several tens of randomly selected sectors), normal, and paranoid.
Nevertheless, the distribution kit is ready for work right now, as confirmed by Snowden’s experience. A matter of primary importance here — you must use your brain first and only after that you may rely on technological tools.
