Trap Bots
To use this method of deanonymization, a bit of social engineering is required. The technique operates similarly to phishing: the target accesses a bot, and to continue using it, they are prompted to send their phone number (a built-in feature of the messaging app). After that, depending on the creativity of the bot’s creator, the bot may either ignore messages or perform some useful functions, but the key point is that the bot’s owner obtains the user’s phone number.
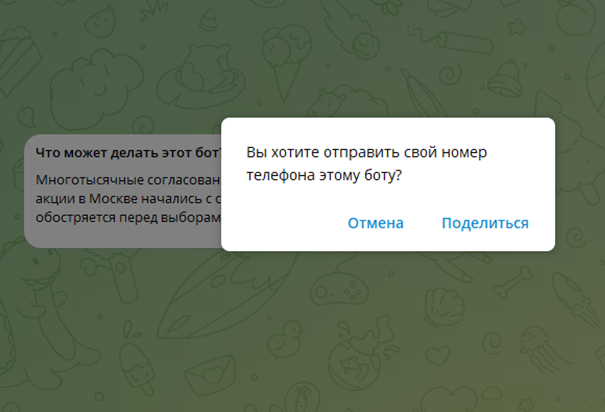
The most interesting part is that there’s no need for you to build a bot from scratch, as there are already ready-made solutions available. For instance, you can use @protestchat_bot or @Checknumb_bot.
You can obtain the result by entering the target account ID in the @TgAnalyst_bot.
Here, you can also check an ID against a database compiled using the same method by other users and the project founders.
However, it’s certainly better to write a bot yourself, and there are resources for that—repositories on GitHub. You can use them without needing to edit, which allows you to immediately create several fully functional bots “out of the box.” You can also choose from several themed bot options: boosting Instagram followers, online dating, game donations, and phone number information lookup.
warning
Collecting information about individuals’ private lives without their consent is illegal, keep this in mind. This article discusses using open source intelligence (OSINT) to find data that people have publicly shared themselves. Regardless, it’s crucial to comply with legal requirements and respect individuals’ rights to privacy. The information in this article is provided solely for informational purposes. The authors and the editorial team do not bear responsibility for any potential damage caused by the use of materials from this publication.
But remember that the main goal is to get the user to share their phone number, so there needs to be a motivation for them to do so. We tailor the motivation to each specific objective, which means the bot’s theme will likely vary. One person might share their phone number to get an appraisal of their used car, another could do it to find an interesting movie, and someone else might be interested in downloading a video from YouTube. Therefore, different bots need to be created for each case, though the core code can be reused from the referenced repositories.
Acquiring Location Data
In 2019, Telegram introduced a new feature called “People Nearby.” This feature allows users to share their location to find contacts and chats nearby. Although the ability to share exact locations was later removed, users can still share their location within a 500-meter radius.
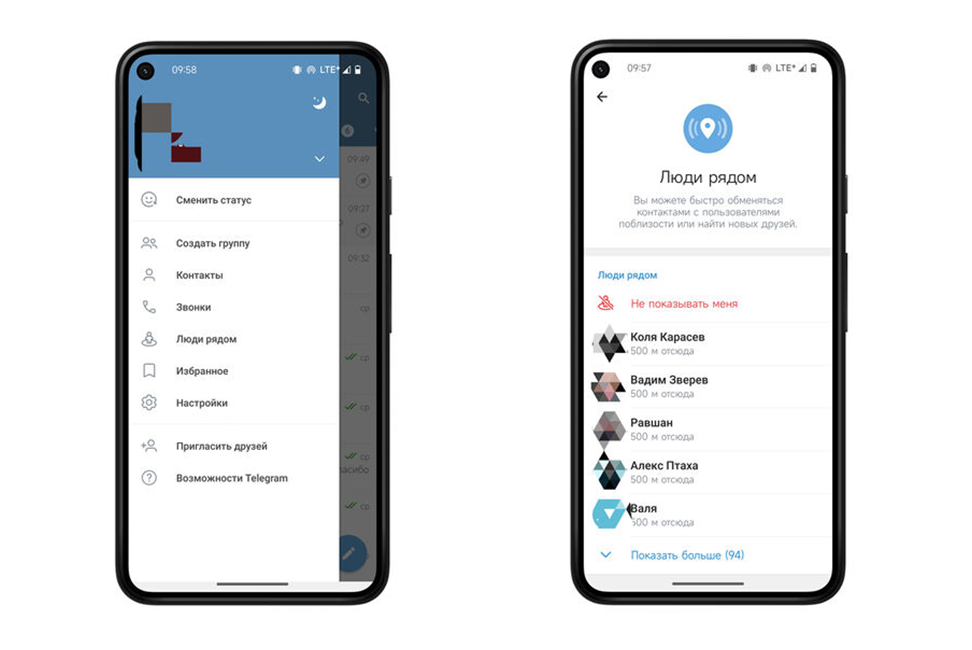
Of course, OSINT specialists didn’t miss this intriguing opportunity and developed several tools to exploit the feature. Here’s how they work.
On a work account, the “People Nearby” feature is activated, and the coordinates where the target is likely located are set. Every 25 seconds, Telegram will send the TDLib data to all users near the specified point. This data includes the distance of each nearby user from your location. By using distances from three different points, you can triangulate and determine the location of the nearest user.
Only Telegram users who have the “People Nearby” feature enabled will be found. By default, this feature is turned off. And of course, to start, you need to have at least a general idea of the location of the person you’re interested in. You can perform searches in multiple areas if the initial area is too large.
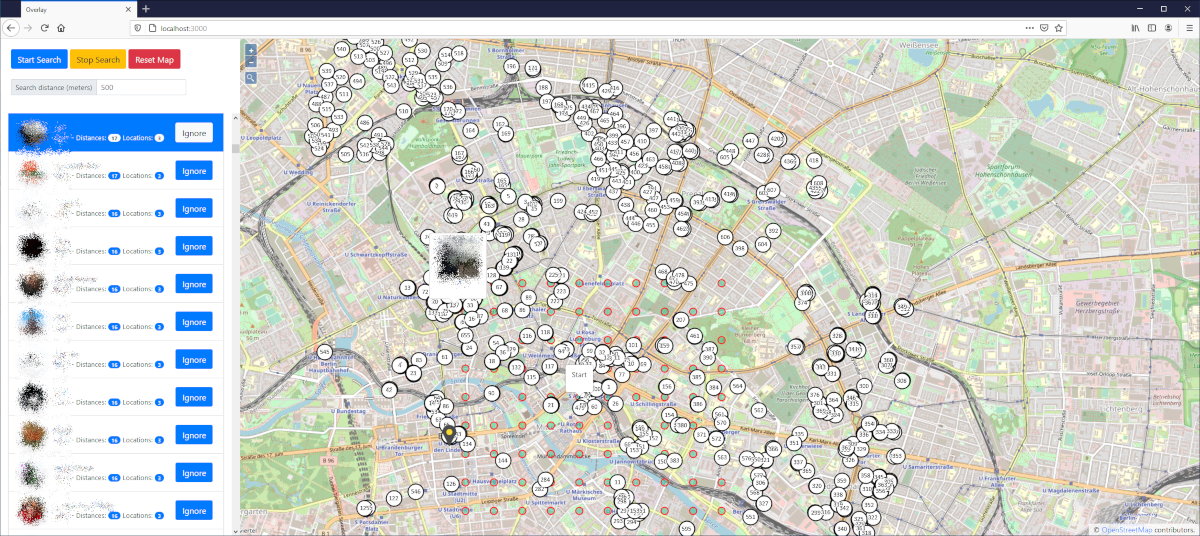
I found three such services, and they all operate on the same principle:
Even More Search Engines
In a previous article, I discussed search engines capable of scouring chats and channels on Telegram. By entering a username, nickname, or user ID, you might find mentions of these identifiers that could provide additional information. Since these services draw from different databases, it’s worthwhile to search each one. That’s why I decided to expand this list.
- Tgstat: Originally designed for administrators of Telegram channels, but often used as a search engine.
- Telegramd: A search engine for the Telegram messenger.
- Kribrum: A free tool from a major service for monitoring media and press.
There are also search engines developed by enthusiasts using Google’s capabilities. These engines search specific Telegram resources that contain messages and posts:
Archives
Now let’s move on to another aspect of investigations on Telegram—identifying the owners of Telegram channels. It’s quite common for a channel author to share certain personal information in posts, descriptions, or titles. Essentially, any details that might aid in an investigation. Later, they might delete this information due to, say, a shift in the channel’s focus or it could have been posted accidentally.
Therefore, a researcher should have tools that can save channel content and provide access to copies. In some cases, well-known online archives can assist with this:
- Archive.org – The largest web archive in the world. By the way, to conveniently download data from there, you can use the utility waybackpack.
- Archive.today – An alternative option.
- Archive.eu – A former European archive that recently relocated. Specify the date when searching to view archives.
- Webcitation – An archive that provides access to pages saved by other users.
You should also check out cached copies. Additionally, there are tools specifically designed for Telegram analytics. For instance, the website Tgstat lets you view the history of channel names, descriptions, links, and feeds. It’s an incredibly useful tool.
If you can’t find anything intriguing on Tgstat, you might want to browse through the feed of posts on alternative platforms:
De-anonymizing via Stickers
If you use stickers on Telegram, be aware that each sticker contains the author’s ID. You may have noticed that many channels create their own branded sticker packs. By having access to a sticker pack, we can determine the creator’s ID from the code of an element. The process of extraction is automated through the bot @SPOwnerBot; simply forward a sticker to it.
The obtained ID may not necessarily belong to the channel owner or someone they know; it’s possible that the sticker pack was commissioned from an external designer. This is important to keep in mind.
Exploring Hidden Content in Channel Descriptions
Finally, here’s another interesting feature. This method is useful when you have a link to a private channel that you can’t join. The only thing available to you in that situation is a preview in the browser.
However, Telegram often hides part of a channel’s description, which might contain useful information. In preview mode, you only see an incomplete version of the channel description. In reality, the full details are present but concealed within the element’s code. To view it:
- Right-click your mouse.
- Locate the
tgme_page_descriptionelement. Its location varies depending on the browser, so you might need to expand different sections of the code to find it. For instance, in Yandex Browser, you’ll find it here:
body > div.tgme_page_wrap > div.tgme_body_wrap > div > div.tgme_page_description
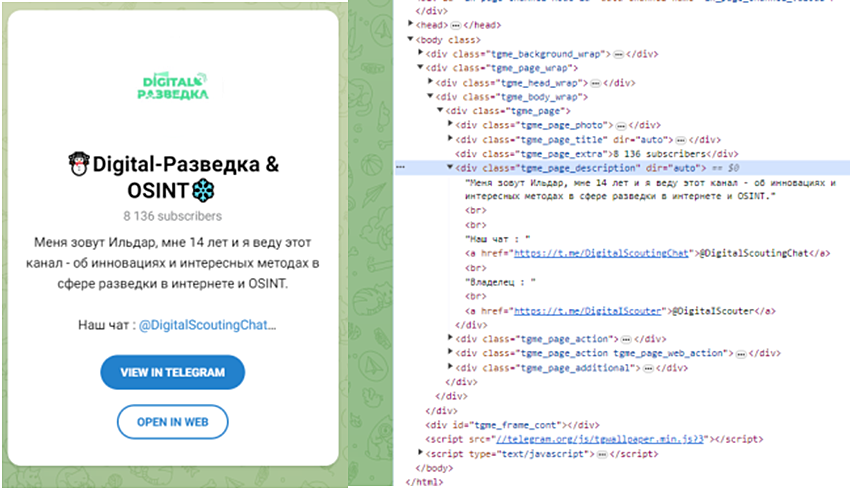
This element contains a complete description of the channel, unlike the user-defined version.
Conclusions
The methods mentioned offer intriguing possibilities for de-anonymizing users and channels. However, it’s essential to remember: collecting information on individuals is illegal. Be cautious when handling personal data and do not use the information to cause harm.