OSINT (Open Source Intelligence) is the collection and analysis of information from publicly accessible sources. This involves gathering data about individuals or organizations from publicly available databases. Special agencies and services conduct OSINT, as do companies (for employee background checks or competitor analysis), and everyday people who want to learn more about their internet contacts and ensure that “heartbreaker888” is not a dangerous psychopath.
We have compiled a list of services that can assist with this. The focus is on sites geared towards Russia, as data formats vary across countries and this can complicate searches.
warning
Unauthorized collection of personal information is a violation of law. Neither the author nor the publication bears any responsibility for any consequences arising from the use of information provided in this article. All information is presented solely for the purpose of informing the reader.
We hope this collection will help the reader uncover a lot of useful information and possibly even avoid issues. However, if you have any doubts about the legality of your actions, remember that it’s never too late to stop. Ultimately, you are acting at your own risk.
Email Search Tools
Emailsherlock.com — an automated email lookup tool. It can identify which websites are linked to a specific email address.
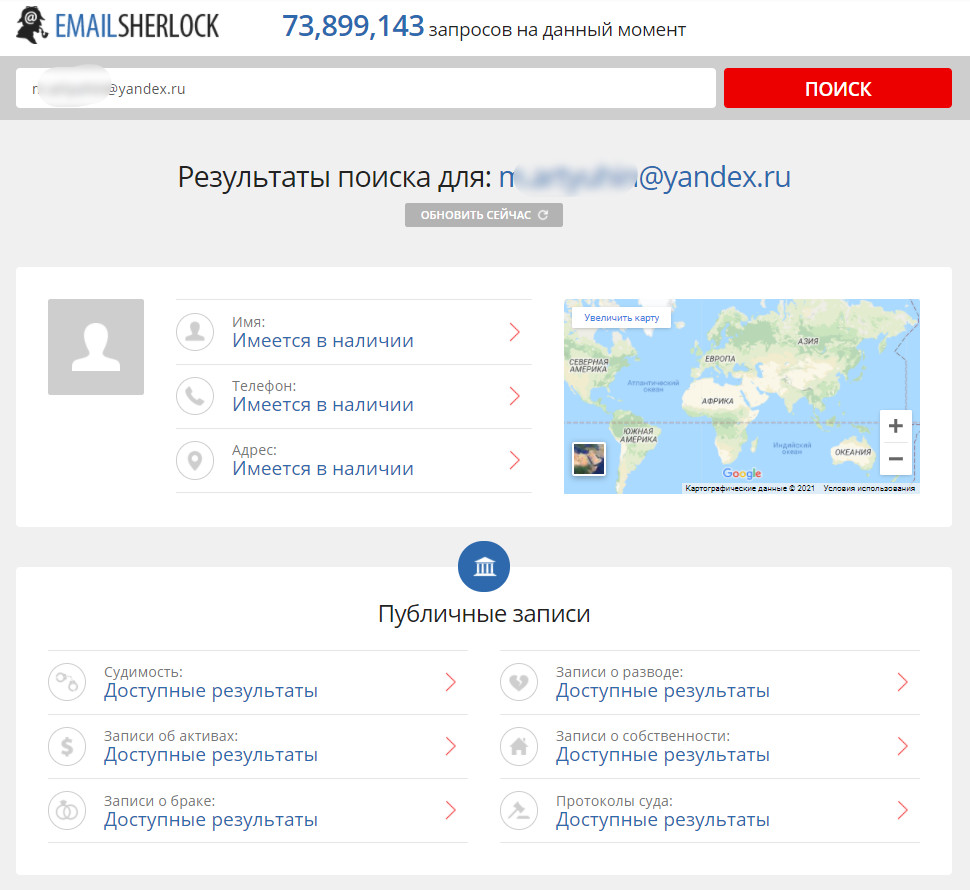
Checking multiple email accounts didn’t yield as many results as hoped. The search is limited to only the most popular websites, like social media. Another downside is that the site heavily promotes third-party services, not all of which are even operational, and almost all require payment.
Emailrep.io is capable of identifying which websites have accounts registered with a specific email address.
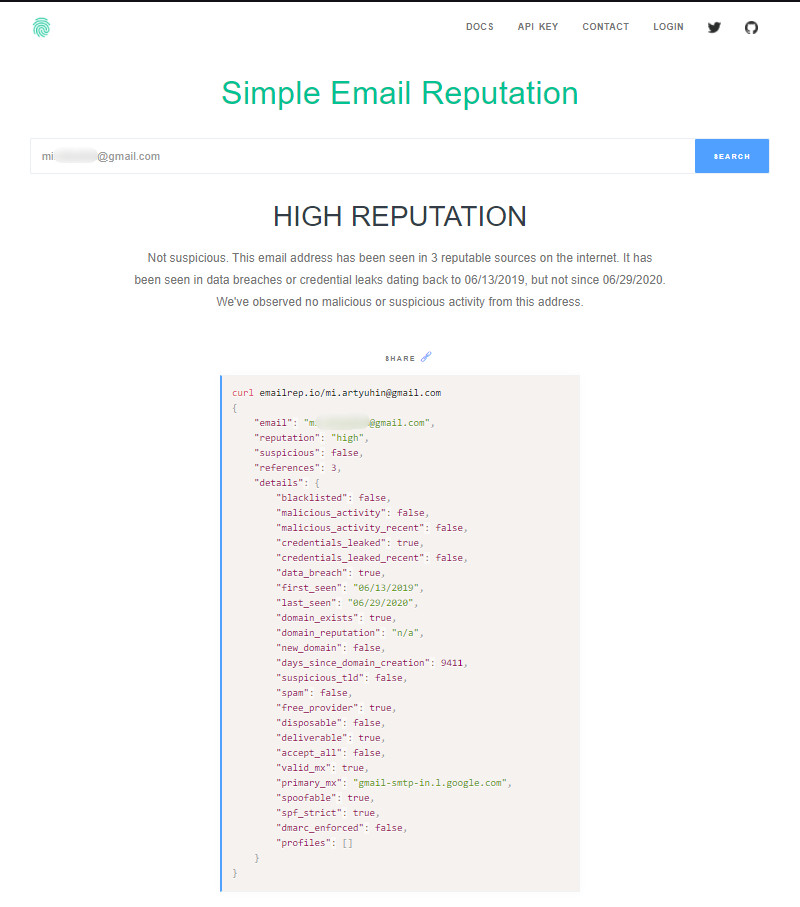
Additionally, based on checks against spam databases and malicious activity databases, the service also assesses the reputation of the account: specifically, whether it has been involved in any data breaches.
Searching by Username
Searching by email often doesn’t yield many results. In such cases, it’s worth trying to search by username (the part before the @)—this usually uncovers significantly more information.
WhatsMyName is more than just a service; it’s a comprehensive tool that searches across 280 platforms!
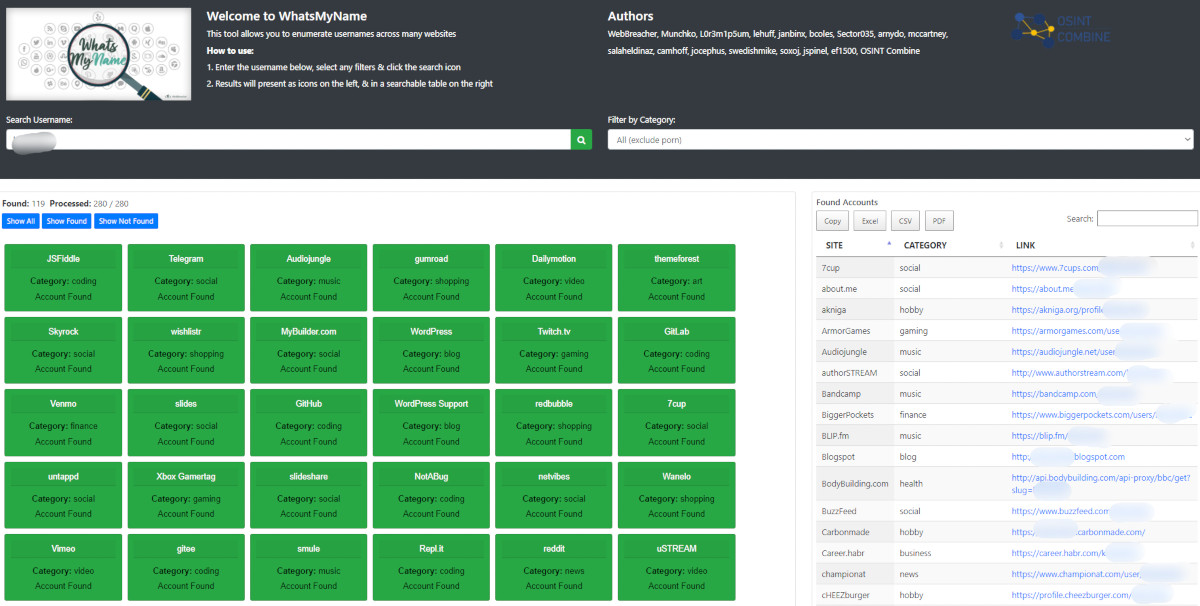
Here, you can sort services by category and also have the option to export the search results (URLs of found profiles) in various formats.
The Usersearch.org service allows you to search not just through popular social media platforms but also on specialized forums and dating websites.

The service is convenient because it not only provides a list of services with links to the accounts, but for each service there is also a direct link to the page for account deletion, just in case it happens to be your account. Additionally, the service can perform searches based on phone number, email, and checks against the Have I Been Pwned database.
SuIP.biz is a continuously updated and extensive database of services with user-friendly results. The verification takes about one to two minutes. The downside is the lack of category sorting.
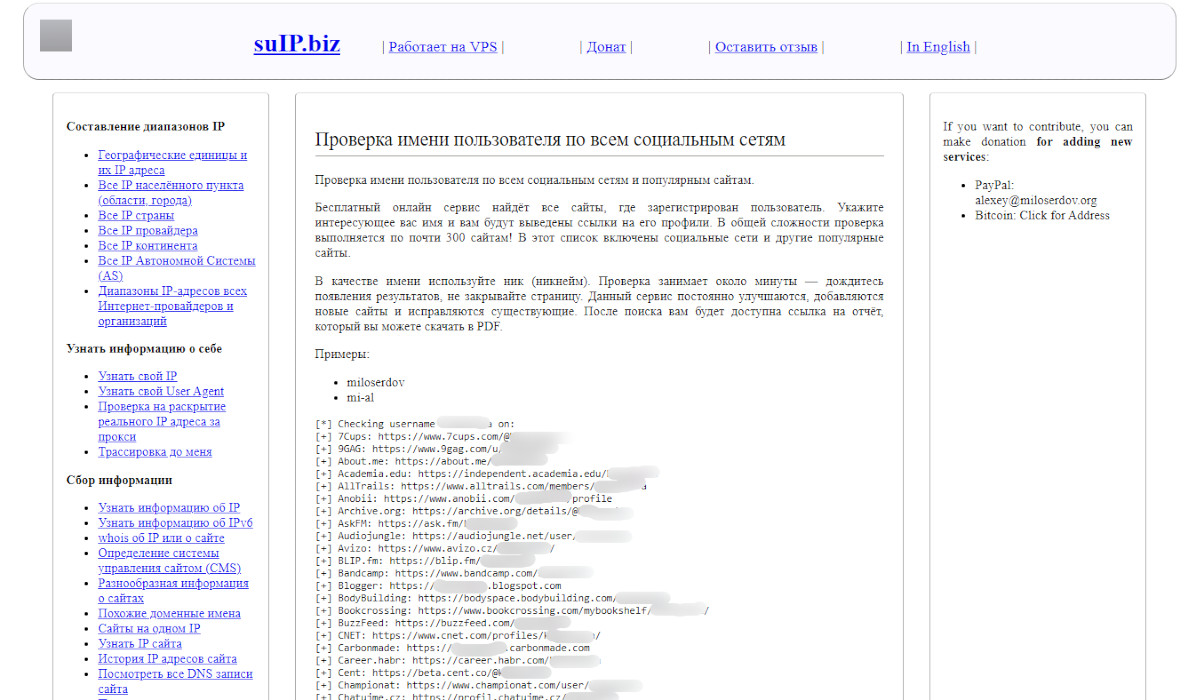
Once the search is complete, you can download the report in PDF format.
Instant Username Search is a service that quickly checks username availability on both well-known and niche platforms. It includes databases from interesting thematic sites like MyAnimeList and Last.fm.
Checkuser is a tool that searches through a limited selection of websites and also lets you check the availability of a domain name.
The search process itself takes about a minute. It’s not possible to get a unified list of links from the results.
Namecheckup utilizes a comprehensive list of services for its checks, which, by the way, don’t take much time to complete.
It’s not possible to obtain all the links at once here either.
Namecheckr offers a small list of web services, but the checks are extremely fast. Most of the services are popular or less-known social networks, and it also checks some domains.
There is a similar service called Namech_k. It checks for the availability of specific usernames across dozens of websites. Additionally, the service provides an API that can be called from scripts.
In the repository of our fellow countryman (and author of an article in “Hacker”), Soxoj, there is an extensive list of checks that can be valuable for online investigations and username search services—thanks to him! This includes tools like Sherlock, Maigret, Snoop, sherlock-go, and Investigo, each of which has proven to be an effective tool for finding and collecting open data.
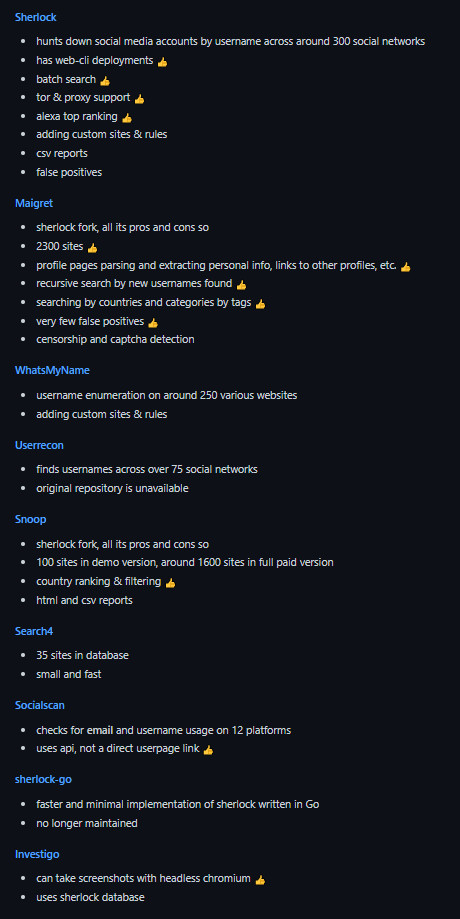
I would like to specifically highlight and mention the tool Maigret.
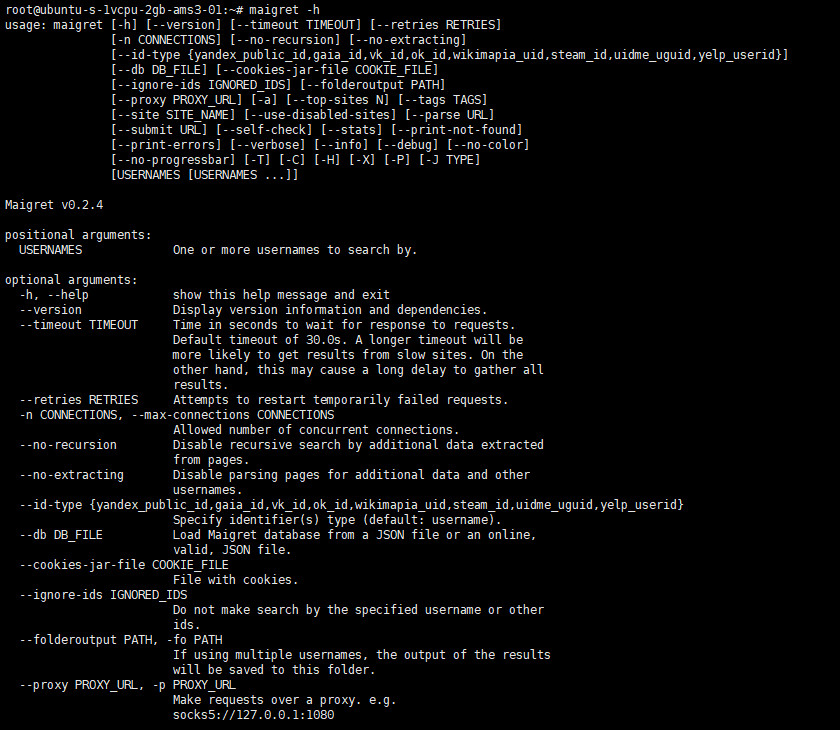
It allows you to compile a dossier on a person by their username by checking for accounts on an extensive number of websites (over 2,300) and gathering all available information from these pages. It doesn’t use any API keys. Incidentally, it’s a fork of another OSINT tool, Sherlock. Note that by default, the search does not run across all sites, but only on the 500 most popular ones.
Phone Number Lookup
SpravkaRU.Net is a comprehensive phone directory that also allows searches by full name.
Unfortunately, not many people use landlines anymore, and phone directories are primarily based on them. As a result, the amount of information they contain isn’t very impressive.
Microsoft allows you to verify the association of a phone number with an account on the account.live.com website. This feature is available for use!
Email2phonenumber aggregates data from account recovery pages across various services to discover phone numbers.
In addition, the tool can generate a list of numbers and scan through services to check if a phone number is listed in a profile.
The bot last4mailbot can retrieve the last four digits of a Sberbank customer’s phone number.
The search is conducted exclusively by email. Testing with a few email accounts known to be linked to Sberbank confirmed that the bot indeed provides accurate information.
Search by Name
Vk-express can monitor a VK account. Once you add a profile link to the site’s database, it will track available avatars, likes, comments, friends, groups, and more.
It also searches for hidden friends and user comments.
Vk-photo.xyz is designed to search for private photos on accounts, but the site’s database is quite limited. Still, it occasionally turns up intriguing content, like photos with other people or in interesting places. What if an FSB officer accidentally leaks a photo from their workplace?
Vk5.city4me is a somewhat suspicious but functional tool for collecting statistics on VK user activity. Its interface bears a suspicious resemblance to vk-express. It displays login statistics, the devices used, friends, and comments, and occasionally might even show the user’s groups. As a bonus, it can reveal hidden friends of the targeted anonymous user.
220vk is purely an analytical service. According to the creator (and based on my limited experience), it can determine the average age of your friends, identify some hidden ones, reveal their cities, account registration dates, and other intriguing yet typically non-essential metrics.
It also reveals friends who have hidden the searched profile on their end, indicating they have, for some reason, concealed their connection with the specified account.
The service is capable of searching for a user’s likes and comments, which can help identify connections between accounts and real people. Once such a link is established, it becomes possible to physically locate the person.
“Here They Find“ sometimes shows profile information from a few years back. Occasionally, this can be useful.
Let’s smoothly transition to searching through international services: if you need to find a person’s profile on Facebook, Instagram, or Twitter using their first and last name, PeekYou is a great choice. It effectively searches a wide range of different services. It immediately suggests potential email addresses based on the username and verifies them as well. Additionally, it provides results for people with similar names and their addresses.
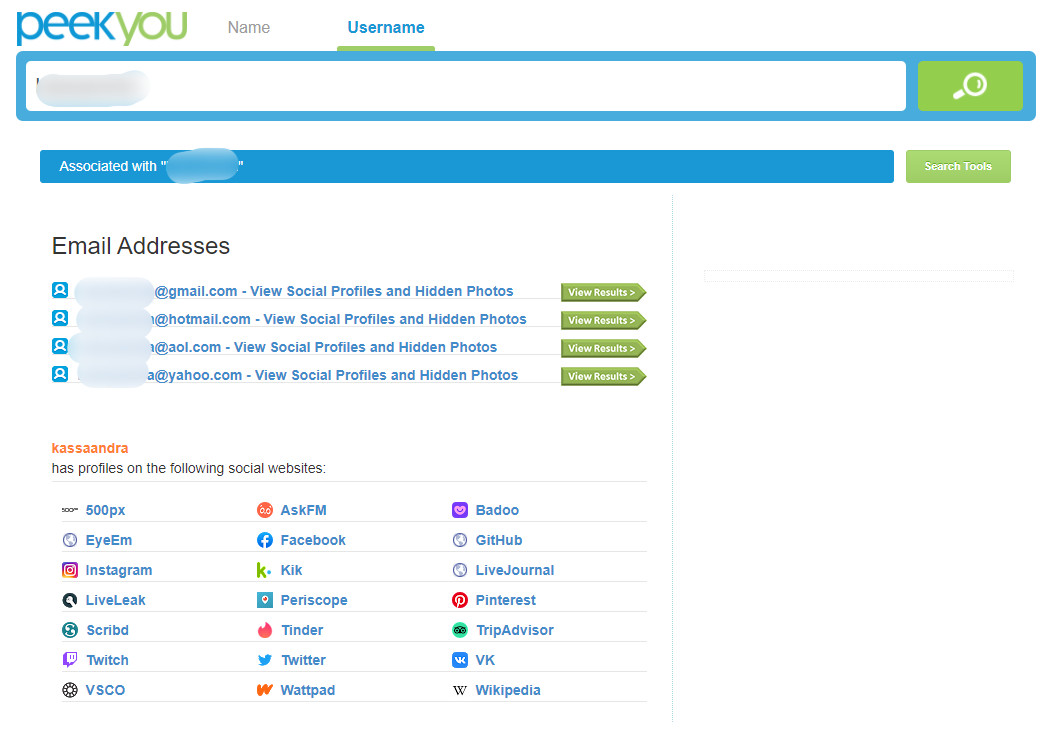
Analyzing Accounts on International Platforms
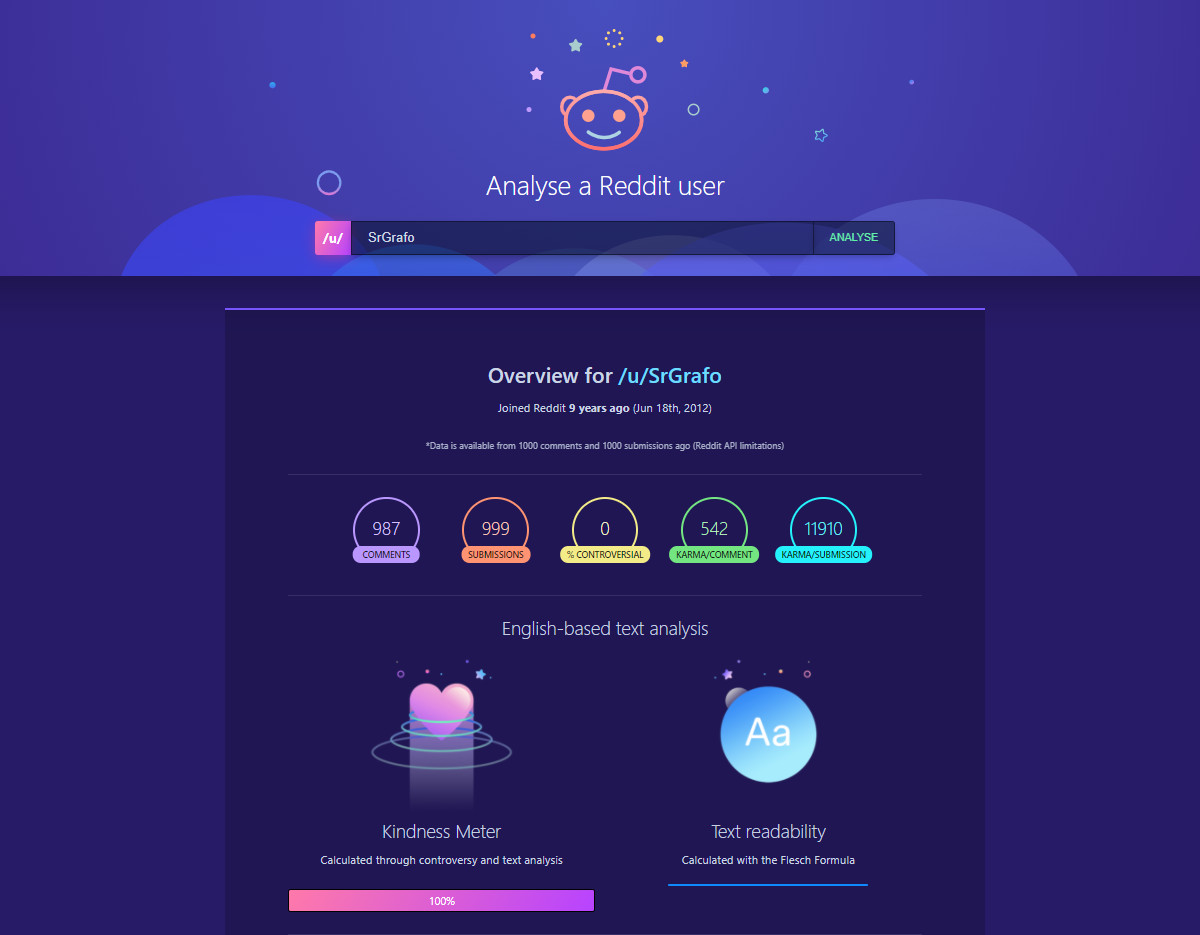
Reddit-user-analyser, as the name suggests, analyzes public data from a Reddit account. It displays the registration date, the number of comments, karma, subreddits, and also generates activity charts, highlighting the best and worst comments.
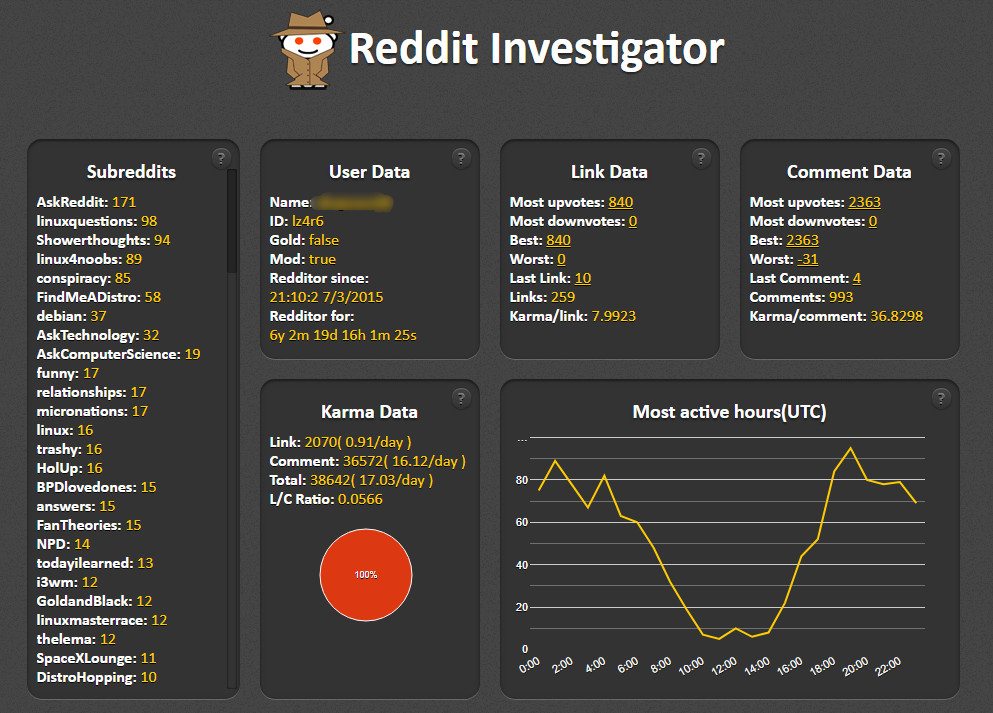
The service redditinvestigator.com compiles a comprehensive dossier on a Reddit account. It includes subreddits the user has participated in, their registration time, an activity schedule (which can help determine their location), as well as a variety of charts and hypotheses based on the information collected from the account.
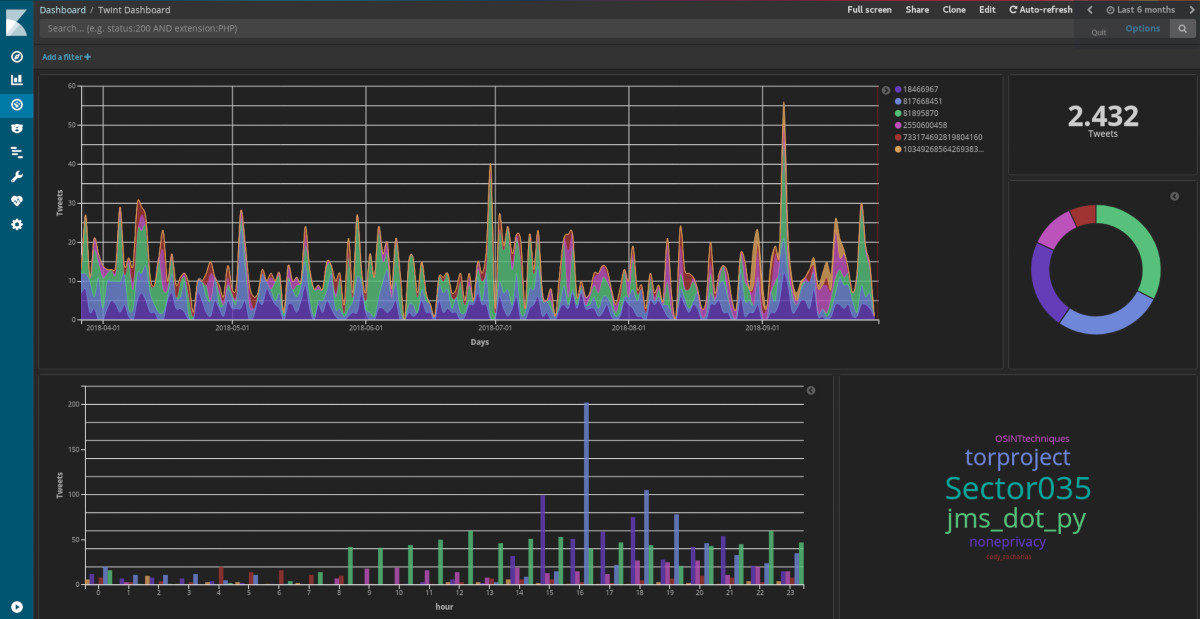
Twint is an advanced tool for analyzing Twitter accounts that operates without relying on the official Twitter API. Unlike the previously mentioned web services, Twint runs locally and requires installation. It gathers general account information, tweets related to specific topics, and hashtags; it can also uncover sensitive information from tweets, such as email addresses and phone numbers.
Whopostedwhat.com is a tool for discovering posts on Facebook. It helps you quickly locate public content created by a specific person.
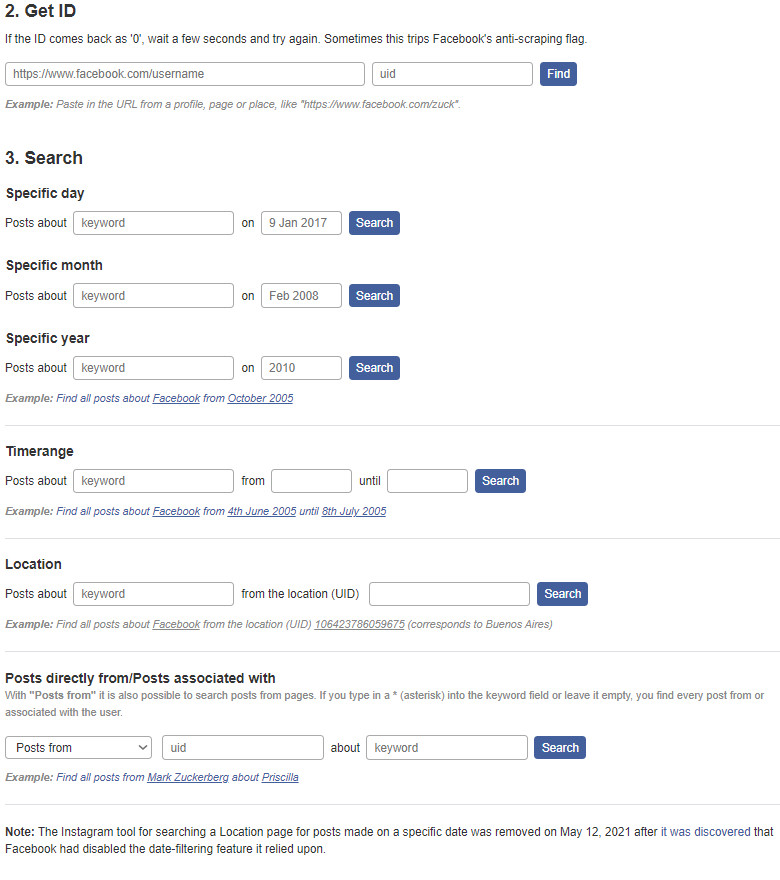
The website provides a feature where you can input a profile link to retrieve a user’s ID. Once you have the ID, you can search for their comments globally and their own posts. The service allows searches by specific date or date range and can also search using keywords. It even supports location-based searches, although I haven’t figured out how to use that feature yet.
HIBP News
As we previously reported, the breach aggregator Have I Been Pwned has already included the massive Facebook account leak in its database. Unfortunately, you could only search by email address, which was available in just 2.5 million out of the 533 million records in the leak.
Since that news was published, things have changed a bit, and now it’s possible to search by phone number as well.
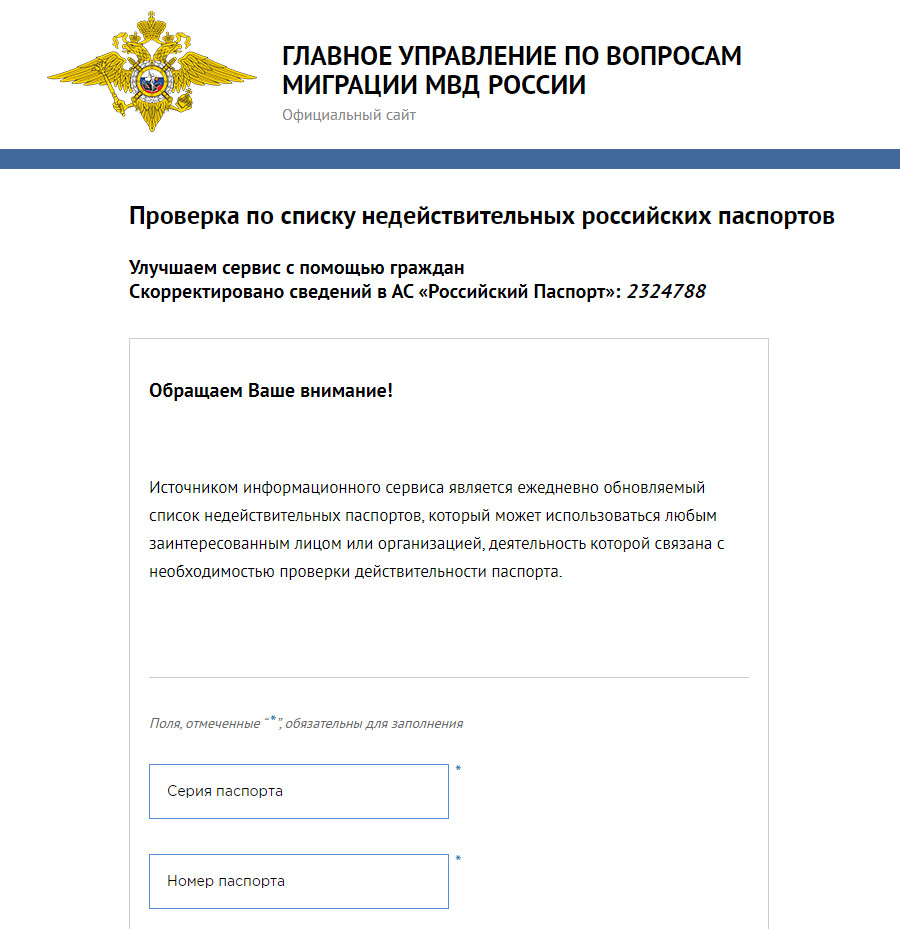
Passport Verification
The Main Directorate for Migration Issues of the Ministry of Internal Affairs offers a service where you can verify the validity of a passport. The database is updated daily, making it extremely useful for HR personnel.
Business Entity Search
This includes services for checking businesses for debts, company registration, and more.
The Egrulbot on Telegram can find all available information in the Unified State Register of Legal Entities (EGRUL) about Russian companies and individual entrepreneurs.
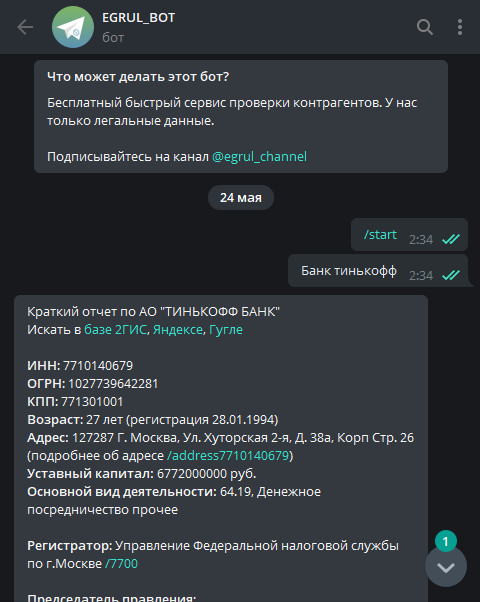
vKarmanebot allows you to search by company tax ID or name. It provides the status, tax ID, registration dates, and address of the organization.
Vehicle Information Search
This includes services that provide information on vehicle registration, VIN number decoding, insurance, accident history, mileage, and more. Such services are useful when buying a car, and they can also help identify the jerk who almost hit you at the pedestrian crossing yesterday.
The VIN01 website allows users to search by vehicle registration number or VIN and provides a history of registrations, accidents, mileage, insurance details, and much more.
The website vinformer offers services for checking Vehicle Passports (ПТС) and conducting VIN searches.
Cyber Reconnaissance
Services and tools designed to analyze data such as IP addresses, SSIDs, file metadata, DNS records, and anything where the subject of analysis is a component of IT infrastructure, whether it’s a website or an IP address.
An interesting option is a tool called Xinit.ru. Here’s a partial list of its features:
- Domain or IP address lookup via WHOIS.
- Retrieving snapshots from Google Cache and data from the Wayback Machine.
- Services and protocols running on the server.
- HTTP response headers.
- Links from the site’s pages on the host.
- Domain’s email addresses.
- Checking the site with virustotal.com.
- Revealing the real IP address behind Cloudflare.
- DNS infrastructure of the site.
Urlscan.io examines who the TLS certificate is issued to and what IP addresses are associated with the site. It also identifies the technology stack used on the site.
Wigle can display the SSIDs and BSSIDs of Wi-Fi hotspots on a map and also allows you to search for them.
PublicWWW stands out by searching through the source code of web pages. It can locate usernames, references within the code, and match site favicons to identify duplicates. Additionally, it can find similar mentions of identifiers or phrases, wallets, tokens, and can even identify advertising widget providers, among many other capabilities.
With Metadata2Go, you can view all the metadata of a file.
Jeffrey’s Image Metadata Viewer extracts EXIF data from photos and images.
PDFCandy provides the capability to extract and modify PDF metadata, such as the title, authors, and creation date.
HostHunter is a tool designed to find domain names associated with a set of IP addresses. It’s particularly useful when you need to quickly gather intelligence on a target subnet. My team found it incredibly valuable during The Standoff 2021 event!
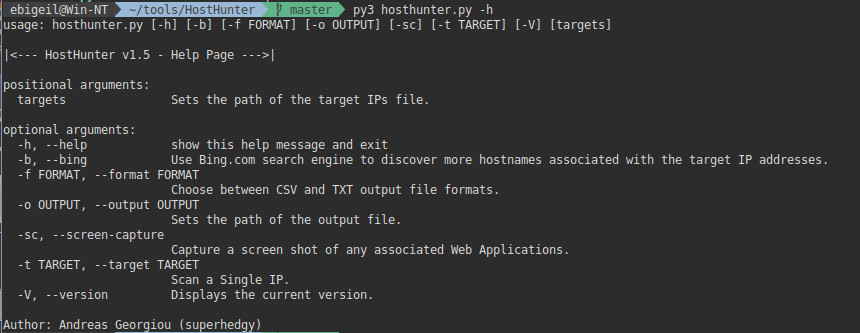
The service is very convenient for processing large lists of IP addresses. It also offers the option to export results to a CSV or plain text file.
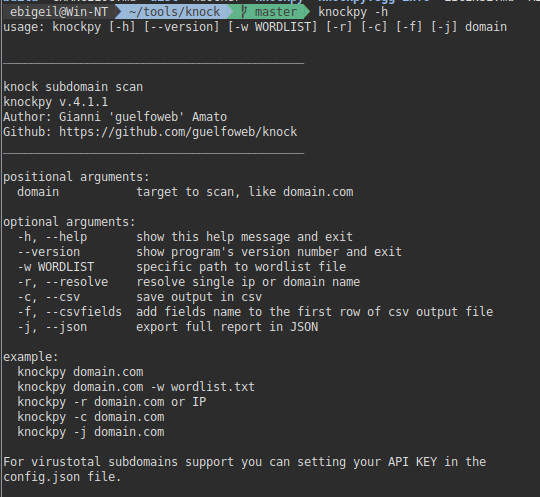
Knock Subdomain Scan uses brute force to enumerate subdomains on a target domain and can generate an output file with the results.
Summary
“Seek and you shall find,” says ancient wisdom. If something ends up on the internet, it’s there to stay. The question is just how much effort it will take to find it.
Today, we focused on useful services, prioritizing those that are freely accessible (read: free). We might have unintentionally overlooked something important, but don’t judge too harshly—there’s a comments section below where you can contribute any additional helpful insights to this article.