I was considering wrapping up the series, but you keep sending me tools that you believe have been undeservedly forgotten on the pages of Hacker. As a result, today’s collection will almost entirely consist of tools submitted by readers, some of which I’ve already adopted myself. I believe you’ll find something useful for your toolkit as well. Let’s dive in!
File Management
Goful
Goful is a new dual-panel file manager written in Go. It supports many useful features such as batch renaming using regular expressions and search functionality. It includes an integrated terminal and several other useful tools.
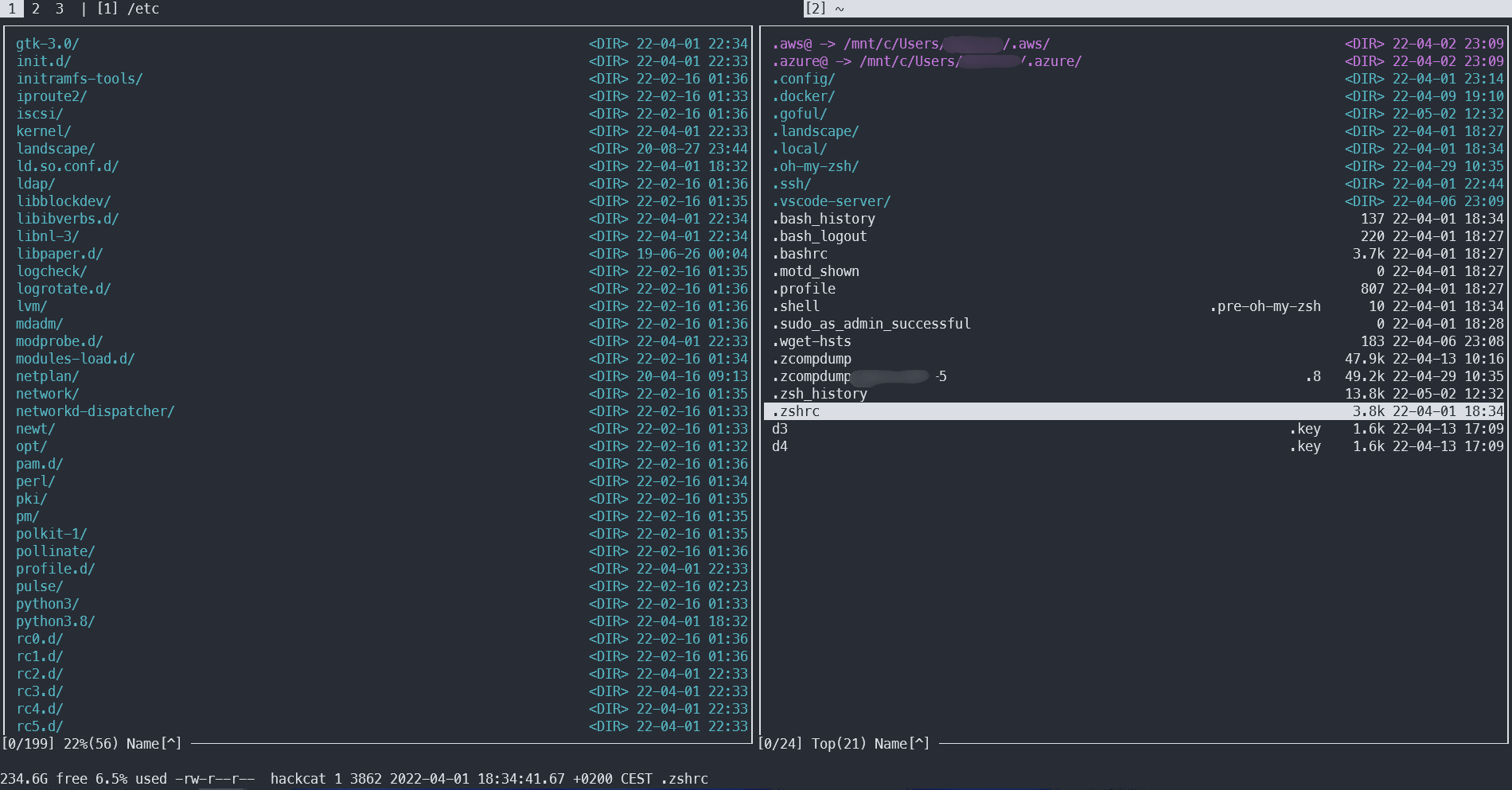
The interface might seem a bit unconventional, but it’s quite user-friendly: instead of using two or three-button shortcuts, you only need to press a single button. For example:
- Use the spacebar to select one or more files (similar to Ctrl-clicking in graphical environments).
- The
\key takes you to the root directory (slightly non-intuitive, because this uses a backslash instead of the forward slash typically used in Unix-like systems). - Press
ito view a file in the pager. - Press
bto bookmark a file. - Press
fto open the file search (usefto search within the current folder)./ - Press
Kto create a new folder. - Press
dto navigate to a specified path.
Of course, this is just a small portion of the commands. The full list is available in the repository’s README.
There are two ways to install Goful. The first method is to simply download and run the binary release from the GitHub repository. The second method requires Go to be installed on your machine:
go install github.com/anmitsu/goful@latest
Goful already looks good, but it can be further customized: you can change controls, colors, the built-in command line interpreter, editors, and viewers. There isn’t a configuration file; instead, you can edit main. and then reinstall it using the go command.
Nnn

Nnn is one of the most minimalist console-based file managers. Its main advantage is its simplicity and low resource requirements, although the latter has become less relevant in a world where home computers often have 32 GB of RAM.
In Ubuntu, you can install nnn directly from the repository:
sudo apt install nnn
Now, just type nnn anytime, and you can effortlessly navigate through directories! You can access the built-in help at any time by pressing the question mark key.
Ncdu
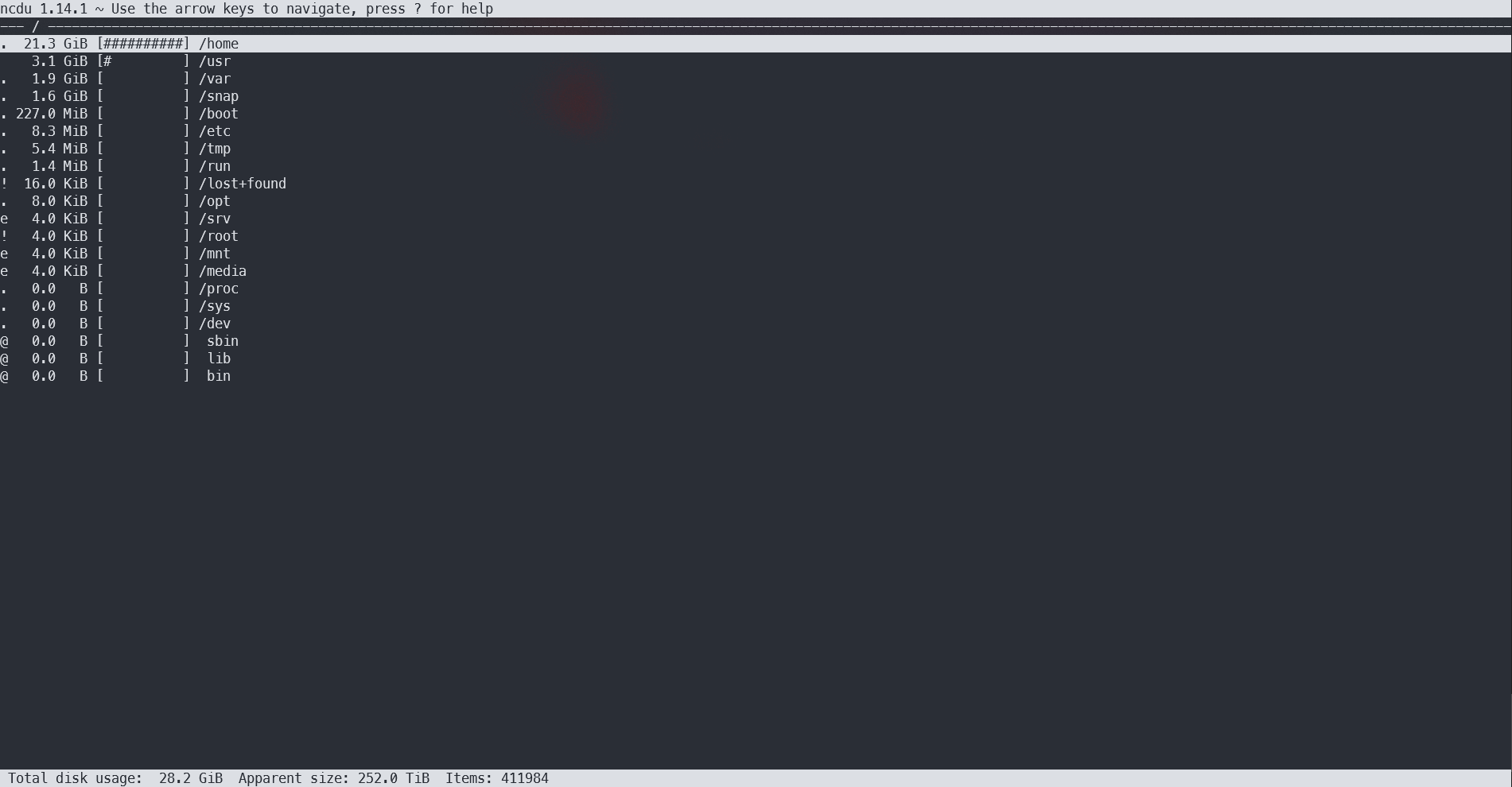
Ncdu (NCurses Disk Usage) is an enhanced version of du that displays disk usage with a user-friendly text-based graphical interface.
With ncdu, you can not only see how much space files are taking up in a directory, but also easily navigate between them. If you decide to delete something unnecessary, just press the “d” key. Of course, the program won’t delete anything accidentally—it’s equipped with a modern telepathic analyzer that will check your intentions by asking for confirmation.
The installation is as easy as pie:
sudo apt install ncdu
When you run ncdu, it will scan the current folder and display the results. You can specify a different path to scan as the first argument:
ncdu /
The tool operates at an impressive speed, which is quite satisfying.
Diffoscope
When a regular diff isn’t enough, diffoscope might come in handy. This tool can compare not just text files, but also directories, archives, binaries, ISO images, PDF documents, and much more—supporting around 70 different file types. You can find the full list in the output of diffoscope .
Installation on Debian and Ubuntu can be done with a single command:
sudo apt install diffoscope
However, during the installation on a clean Ubuntu system, 1124 packages were downloaded, totaling around one and a half gigabytes because the dependencies include Python, Java, and an X server. Why a command-line utility would need these is unclear.
There is a Docker version available:
docker run --rm -t -w $(pwd) -v $(pwd):$(pwd):ro registry.salsa.debian.org/reproducible-builds/diffoscope
There’s also a browser-based version of diffoscope available at try.diffoscope.org (as shown in the screenshot).
Eget
Eget is a handy tool that allows you to install software from GitHub repositories where the authors have provided releases with binaries.
If you could install eget using eget, you would simply need to write
eget zyedidia/eget
If you don’t have eget yet, you’ll need to use either the release or the installation script:
curl https://zyedidia.github.io/eget.sh | sh
Networking
Wireproxy
If you need to use Wireguard but for some reason don’t want to set up a full-fledged client, consider using wireproxy. It connects to a peer via the Wireguard protocol but doesn’t create a new network interface. Instead, it establishes a SOCKS5 proxy that you can configure in your applications.
Installation boils down to three lines in the terminal:
git clone https://github.com/octeep/wireproxy
cd wireproxy
go build ./cmd/wireproxy
If you don’t have Go, that’s no problem. Simply download the compiled release.
The execution requires just one parameter:
./wireproxy -c <config file>
The configuration is standard for Wireguard, but you need to add two sections (comments are included for clarity):
# TCPServerTunnel is a tunnel listening on wireguard,# and it forwards any TCP traffic received to the specified target via local network.# Flow:# <an app on your wireguard network> --(wireguard)--> 172.16.31.2:3422 --> localhost:25545[TCPServerTunnel]ListenPort = 3422Target = localhost:25545# SOCKS5 creates a SOCKS5 proxy on your LAN, and all traffic would be routed via wireguard.[Socks5]BindAddress = 127.0.0.1:25344# SOCKS5 authentication parameters, specifying username and password enables# proxy authentication.Username = ...# Avoid using spaces in the password fieldPassword = ...For more detailed information about wireproxy, check out the project’s repository.
Ssh-tools
Ssh-tools is a small suite of utilities designed for those who frequently work with SSH. The most useful among them appear to be the following:
-
ssh-ping— check the SSH service status (focus on the SSH daemon, not the machine itself); -
ssh-diff— compare files on different machines; -
ssh-facts— gather basic information about the remote system; -
ssh-force-password— bypass key-based authentication and log in using a password (if the server permits it); -
ssh-keyinfo— display information about SSH keys.
All the utilities in this set parse the ~/. file, allowing you to use the pre-configured host names from there.
The package is available in the repositories of all popular distributions, so you can simply install the ssh-tools package.
Nala
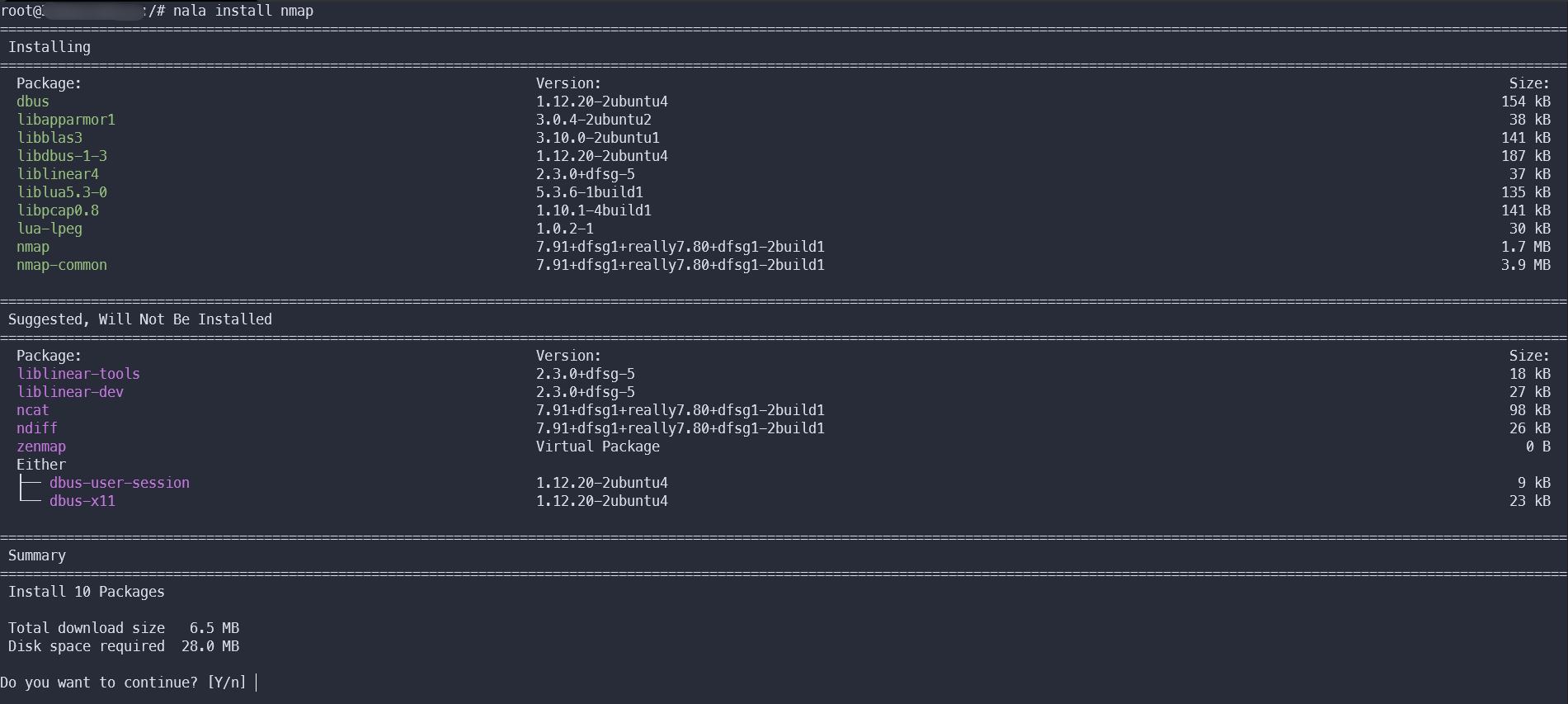
Nala is an excellent interface for APT. It can do everything that the standard apt can do, plus it supports history and downloads packages in parallel.
Nala is not yet available in the official repositories, but you can add a third-party repository and install it from there:
echo "deb http://deb.volian.org/volian/ scar main" | sudo tee /etc/apt/sources.list.d/volian-archive-scar-unstable.list
wget -qO - https://deb.volian.org/volian/scar.key | sudo tee /etc/apt/trusted.gpg.d/volian-archive-scar-unstable.gpg > /dev/null
sudo apt install nala
After that, you can simply use nala instead of apt (e.g., nala ).
Iptables-tracer
With iptables-tracer, you can check if traffic passes through the desired iptables chains. It does this by inserting special marker rules (-j ) into each chain, which will trigger when a packet passes through the chain.
It looks like this:
$
14:42:00.284882 raw PREROUTING 0x00000000 IP 192.0.2.1.36028 > 203.0.45.41.443: Flags [S], seq 3964691400, win 29200, length 0 [In:eth0 Out:]
14:42:00.287255 mangle PREROUTING 0x00008000 IP 192.0.2.1.36028 > 203.0.45.41.443: Flags [S], seq 3964691400, win 29200, length 0 [In:eth0 Out:]
14:42:00.288966 nat PREROUTING 0x00008000 IP 192.0.2.1.36028 > 203.0.45.41.443: Flags [S], seq 3964691400, win 29200, length 0 [In:eth0 Out:]
14:42:00.290545 mangle FORWARD 0x00008000 IP 192.0.2.1.36028 > 198.2.100.8.443: Flags [S], seq 3964691400, win 29200, length 0 [In:eth0 Out:eth1]
14:42:00.292123 filter FORWARD 0x00008002 IP 192.0.2.1.36028 > 198.2.100.8.443: Flags [S], seq 3964691400, win 29200, length 0 [In:eth0 Out:eth1]
14:42:00.293164 mangle POSTROUTING 0x00008002 IP 192.0.2.1.36028 > 198.2.100.8.443: Flags [S], seq 3964691400, win 29200, length 0 [In: Out:eth1]
14:42:00.293780 nat POSTROUTING 0x00008002 IP 192.0.2.1.36028 > 198.2.100.8.443: Flags [S], seq 3964691400, win 29200, length 0 [In: Out:eth1]
You’ll need Git and Go installed. Here’s how to set them up:
git clone https://github.com/x-way/iptables-tracer
cd ./iptables-tracer/
go build
Let’s get started:
./iptables-tracer -f "-s 1.3.5.7 -p tcp --dport 22" -t 90s
The -f parameter allows for filtering specific traffic to display according to iptables syntax, while the -t parameter sets the duration after which tracing will stop.
It’s important to remember that after stopping the tracing process, the auxiliary rules created in iptables won’t be automatically removed. You’ll need to delete them manually using this command:
./iptables-tracer -c
Visual Tools
Picocrypt
Picocrypt is a simple yet powerful tool for file encryption. Unfortunately, it only comes with a graphical user interface, but this is unlikely to be a significant issue.
Picocrypt not only encrypts but also generates strong passwords and edits file metadata. If you want, you can even completely remove this metadata, but the idea of misleading potential investigators with false trails seems more intriguing.
In the README, the author praises their creation as one of the best encryption solutions for almost anything. It features open source code, a small size, a modern algorithm, and even data corruption protection. You can view the full comparison table below or in the project’s repository.
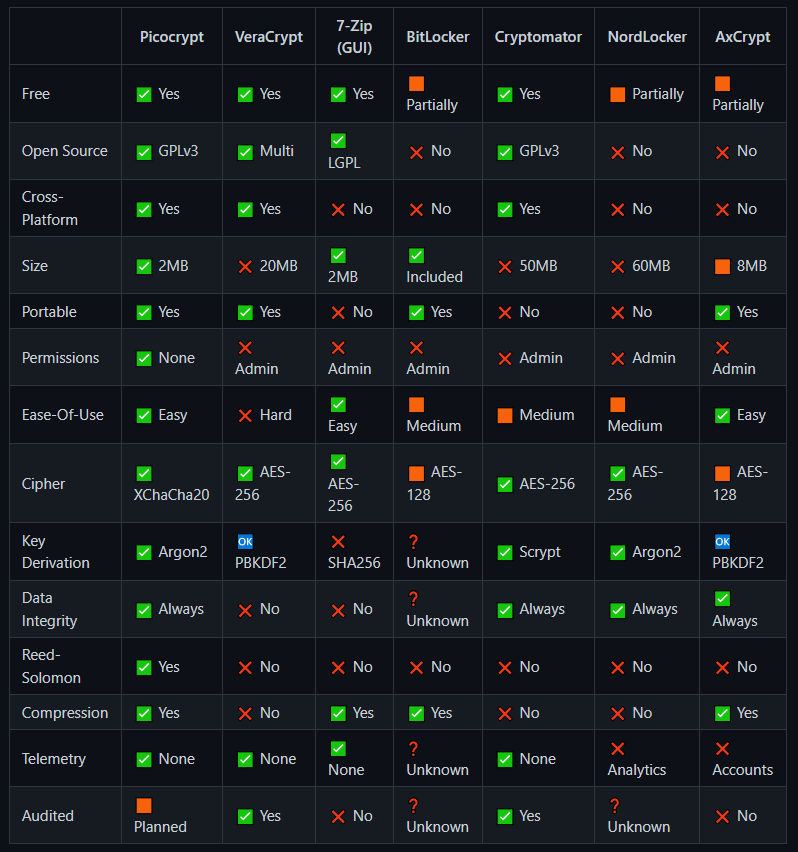
Installing on Windows involves downloading the compiled binary from the releases page, while on Linux, it can be installed via Snap.
snap install picocrypt
If Snap is not installed, you first need to install it using sudo .
Dockeye
If you suddenly need a UI for Docker, try dockeye. It’s a graphical client for managing Docker that stands out from other similar tools.
There are builds available for Linux and macOS, which can be downloaded from the releases page.
Sysmontask
If you’ve been missing the Windows Task Manager, with sysmontask, you’ll feel right at home on Linux!
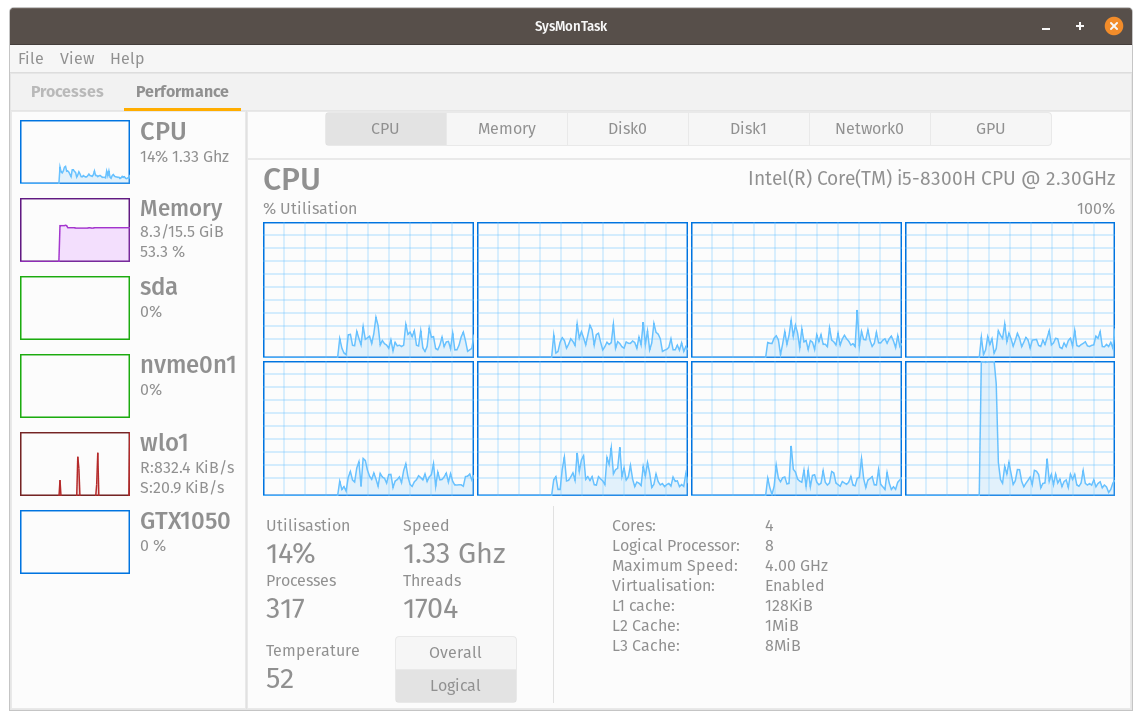
I think it’s pointless to explain what it does, so let’s just install it and you can check it out for yourself:
sudo add-apt-repository ppa:camel-neeraj/sysmontask
sudo apt install sysmontask
// Execute only on Ubuntu <=20.04
sudo pip3 install -U psutil
The author recommends running the initial launch from the console using the command sysmontask.
Neofetch
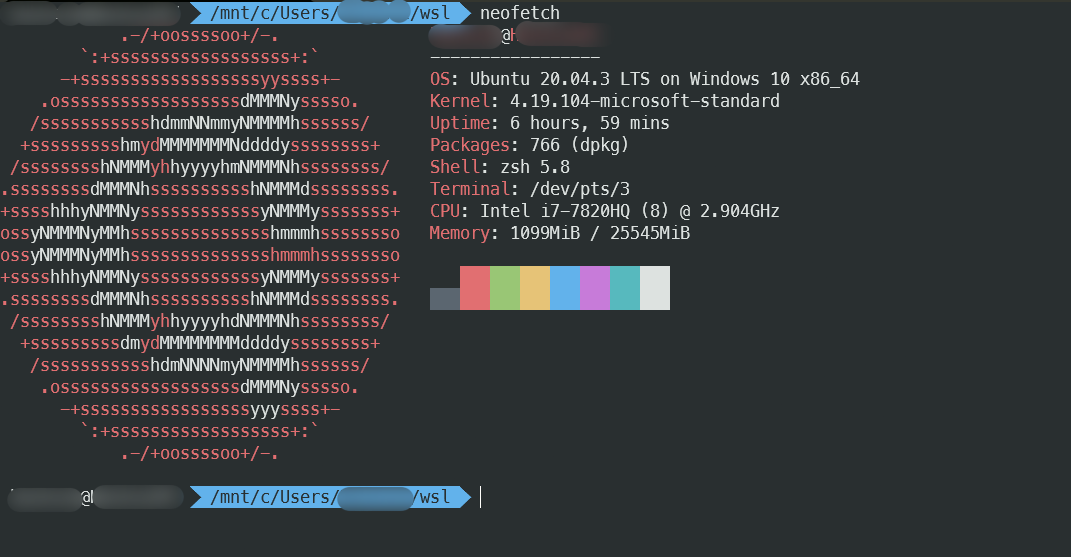
Neofetch is a tool that visually and attractively displays statistics about your computer. It will show the operating system distribution (with a large logo!), kernel version, memory and processor information, shell, desktop environment (if available), window manager, active theme, and much more.
Neofetch is available in the Ubuntu repository:
sudo apt install neofetch
If you’re also using WSL, you can install a similar program called wslfetch, which is included in the distributions assembled by Microsoft. Its output looks slightly different and it operates noticeably slower, but I felt it was important to mention the pre-installed alternative.
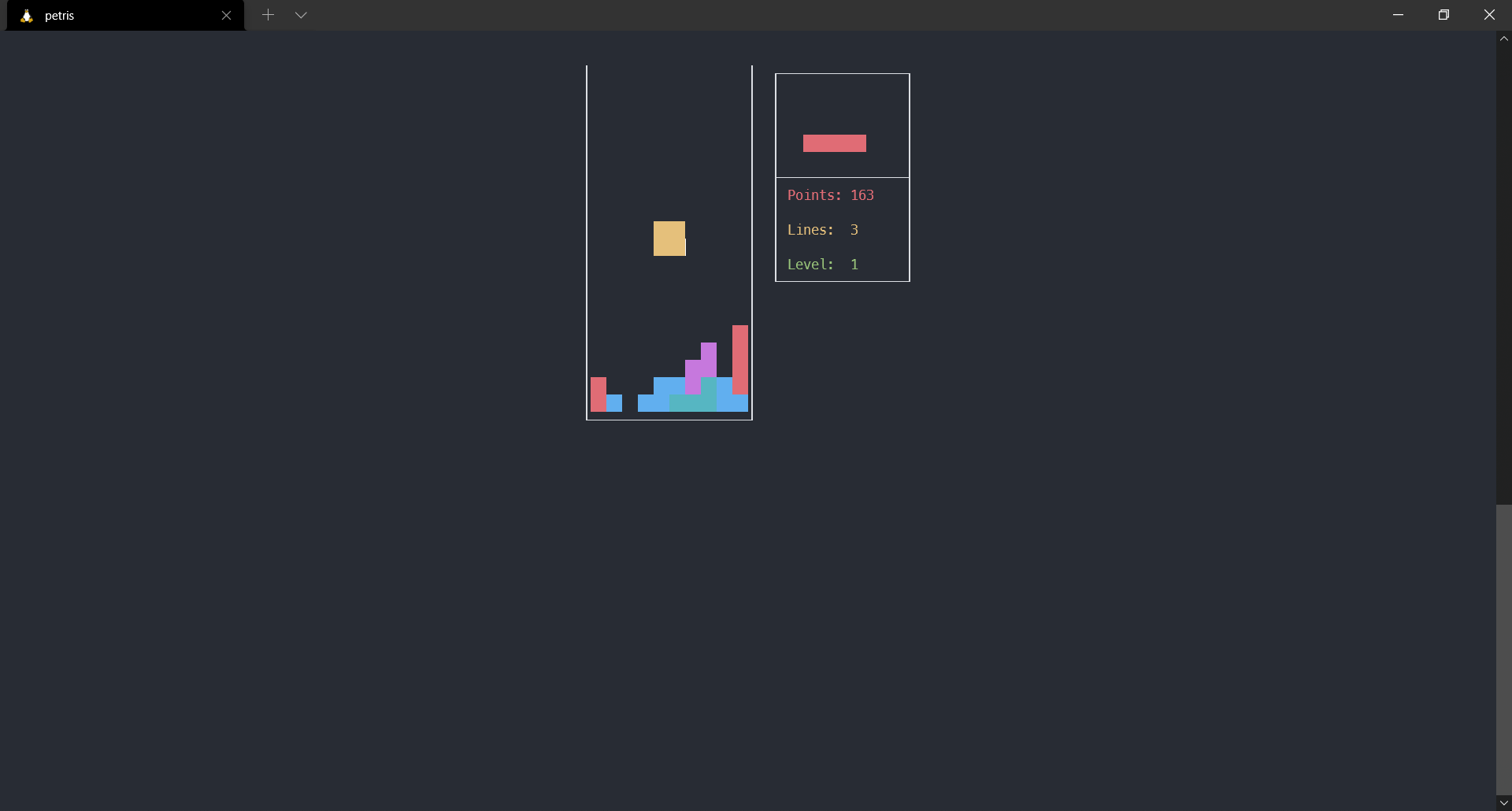
TTYgames
The most important part of this article is the collection of console games. While it might seem anachronistic in the 21st century, why not? These games might even go unnoticed at work. The release of this article was delayed because I found a fantastic Tetris (as shown in the image) and couldn’t tear myself away from it.
For Scripting
HttpX
HttpX is a versatile tool for automating HTTP tasks. It is particularly useful for identifying HTTP servers from scan results, gathering service fingerprints, and exploring subnets during penetration testing.
It’s particularly useful to combine httpX with other tools.
subfinder -d hackerone.com -silent| httpx -title -tech-detect -status-code
__ / // / / / / ///
projectdiscovery.io
Use with caution. You are responsible for your actions
Developers assume no liability and are not responsible for any misuse or damage.
https://mta-sts.managed.hackerone.com [404] [Page not found · GitHub Pages] [Varnish,GitHub Pages,Ruby on Rails]
https://mta-sts.hackerone.com [404] [Page not found · GitHub Pages] [Varnish,GitHub Pages,Ruby on Rails]
https://mta-sts.forwarding.hackerone.com [404] [Page not found · GitHub Pages] [GitHub Pages,Ruby on Rails,Varnish]
https://docs.hackerone.com [200] [HackerOne Platform Documentation] [Ruby on Rails,jsDelivr,Gatsby,React,webpack,Varnish,GitHub Pages]
https://support.hackerone.com [301,302,301,200] [HackerOne] [Cloudflare,Ruby on Rails,Ruby]
https://resources.hackerone.com [301,301,404] [Sorry, no Folders found.]
I couldn’t install the program from source due to issues with Go, but eget easily fetched the binary release, which can, of course, also be downloaded manually.
The program has a lot of flags, but I suggest you explore them on your own. They are highly specific, and each one is well-documented in the help section.
Xj
Those who have tried working with HTML from shell scripts are familiar with the pain of attempting to parse it using regular expressions. For you, there is xj — a utility that converts an HTML page into JSON for further processing. Handling JSON in scripts is very convenient with the help of jq.
$ wget -qO- https://stedolan.github.io/jq/ | xj | jq '..|select(.title?)[][]'
"jq"
A great tool for simple parsers, especially when you want to avoid programming for some reason.
Topalias
Topalias generates aliases for the commands you use most frequently. This tool provides statistics, suggests abbreviations, and shows you how to register them.
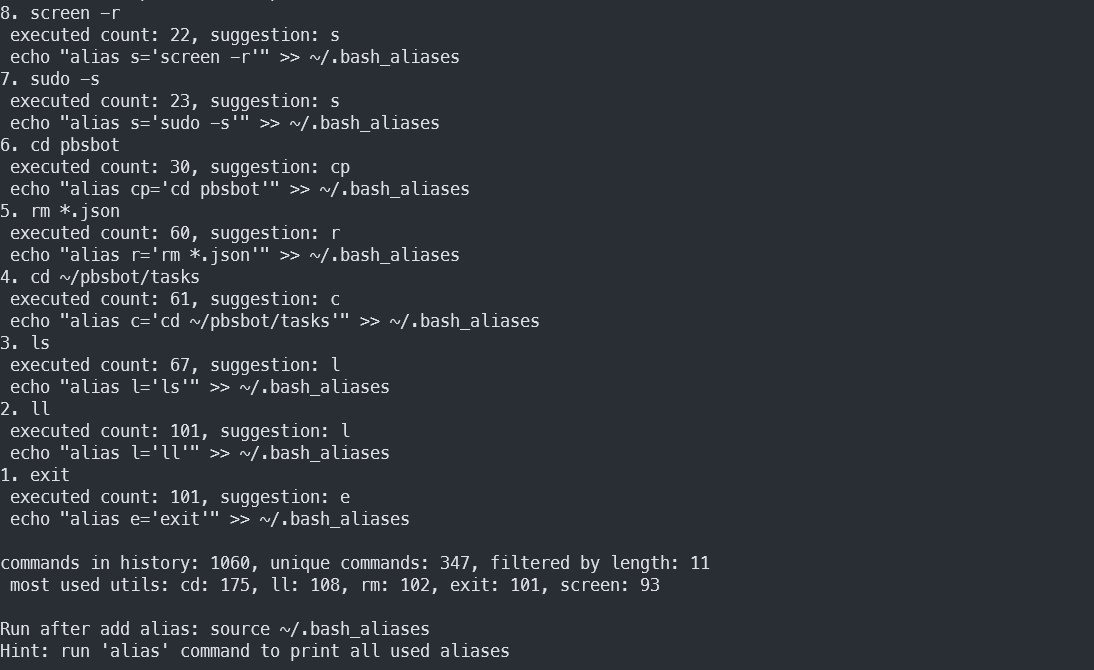
The screenshot above illustrates a clear problem: the utility doesn’t recognize that some suggested aliases share the same names as programs already installed on the system, including system programs. For instance, the command cd has the alias cp suggested, and if applied, you won’t be able to use the cp command to copy files anymore.
Another issue is the broken dependency during installation. The suggested installation method is as follows:
pip3 install -U --user topalias
When you try to run the utility, it immediately crashes with an obscure error and doesn’t even allow you to view the help documentation. This can be fixed by installing an older version of the click package:
pip3 install -U --user click==7.1.2
Only then will everything work properly.
Miscellaneous
Jrnl
For regular terminal users, there’s jrnl—a command-line tool for taking notes.
The installation is done via pipx, and the author of the utility warns about potential issues if this package manager is installed incorrectly. I installed pipx using APT (even though the author does not recommend this method) and did not encounter any issues, but be aware that problems can occur.
Let’s assume you already have the “correct” version of pipx. In that case, installation is done with just one command:
pipx install jrnl
To use jrnl, you can either pass the note as a command line argument or launch jrnl and input everything directly in the tool itself, which is convenient if your note is lengthy.
You can add titles, tags, timestamps to your notes, and even encrypt your journal.
The notes file is in plain text, so you can view it in various ways. Additionally, the program offers the --short flag (which will display only the headers) and the --export flag (which will output the entire log file).
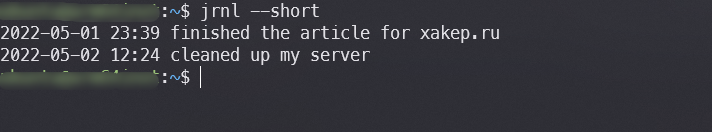
The utility may appear minimalist, but it actually offers quite a few features. You can find a detailed description of them on the developer’s website.
Android Notifications on Linux
Android2Linux Notifications is a method to display Android notifications on a Linux desktop using libnotify.
Both the computer and the phone must be on the same network, as a direct connection is established between them for each new notification. However, it’s possible to create this connection remotely using a VPN tunnel, such as Wireguard.
First, the server is installed on the computer, followed by the installation of the application on the phone. The server can be installed using the following commands:
git clone https://github.com/patri9ck/a2ln-server.git
cd a2ln-server
sudo make install
If you encounter any issues, install the dependencies using pip. You’ll find the list of required packages in the requirements. file.
After that, you can start the server with the command a2ln to listen on port 50505. Of course, you can change this port as you wish, but remember that ports below 1024 require root privileges. Also, don’t forget to add the server start command to the autostart using any convenient method, so that notifications continue to come through after a system reboot, if you ever restart your machine.
To set up the app on your phone, download the client application from F-Droid and input the server’s IP address and port. If you have a Huawei, Samsung, Xiaomi, or any other phone with aggressive power saving features, you’ll need to whitelist the app to prevent the system from terminating it. You can learn how to do this by visiting dontkillmyapp.com or checking relevant forum threads.
[Bonus: Linux Journey
Linux Journey is an interesting platform for enhancing and testing your Linux knowledge. This free Linux guide could have been quite helpful to me back in the day. It might be useful for you or someone you know!
