warning
All information is provided for informational purposes only. Neither the editorial team nor the author bears responsibility for any potential harm caused by the materials in this article.
Debuggers
Debugging an application is an integral part of the research process, a tool that reverse engineers always have at their disposal. In today’s world, a debugger must support both Intel architectures—x64 and x86—and that will be our starting point.
We also need the ability to debug code that’s running in kernel mode. This need arises periodically, especially if you’re planning to find zero-day vulnerabilities in the OS kernel or reverse-engineer virus drivers. There are two main contenders for the job: x64dbg and WinDbg. The first debugger operates in user mode, while the second can debug code in kernel mode.
x64dbg
This modern debugger, featuring an intuitive interface, is a worthy successor to OllyDbg. It supports both x64 and x86 architectures and comes with a plethora of highly useful plugins.
Yes, it certainly has its drawbacks – there are still a few annoying bugs. However, it is actively maintained and developed. Of course, since the debugger operates in user mode, it remains vulnerable to many debugging detection techniques. But this downside is somewhat offset by the variety of plugins available to conceal the debugger.
x64dbg comes equipped with a built-in decompiler and supports code visualization in graph form. It allows setting breakpoints for read, write, execute, and access operations. There’s also an integrated tool for import reconstruction for both x64 and x86 architectures. In summary, this debugger has been discreetly used within niche circles to crack the infamous Denuvo game protection, and it handles this task effectively!
Why Not OllyDbg?
OllyDbg wasn’t included in the selection because it’s seriously outdated. It doesn’t support modern operating systems or the x64 architecture. Although the official website announced a 64-bit version and even mentioned development progress, the site hasn’t been updated since 2014. Undoubtedly, OllyDbg represents an entire era, but it seems that era has ended. Additionally, kernel mode debuggers have also dwindled; developers have abandoned the Syser Kernel Debugger, which was once the successor to SoftICE.
WinDbg
If you need to debug the kernel or a driver, there’s nothing quite like WinDbg. This debugger is supported by Microsoft and is included in the Windows Driver Kit (WDK). Currently, it is the most up-to-date and powerful tool for debugging kernel code. While it lacks the user-friendly interface of tools like x64dbg, our options are limited—other debuggers don’t operate in kernel mode.
WinDbg supports remote debugging and can download debugging symbols directly from Microsoft servers. To expedite kernel debugging within virtual machines, there’s an add-on called VirtualKD. While starting your reverse engineering journey with WinDbg is not recommended, once you gain some experience and start exploring more complex tasks, it becomes an essential tool.
WinDbg is a powerful tool that allows you to easily view various system structures and disassemble NTAPI functions. While it can also be used to debug “regular” applications, I personally prefer to keep such a mighty tool reserved for when it’s absolutely necessary! 🙂
Disassemblers
It’s hard to imagine reverse engineering without tools for static code analysis. Currently, disassemblers have made only modest advancements compared to debuggers, but some frontrunners in the field can still be identified. The recognized standard in antivirus laboratories is the disassembler IDA Pro. The second most popular tool is the reverse engineering framework Radare2, although many argue that Radare2 is on par with IDA.
IDA Disassembler
There are two versions of IDA: the paid version (Pro) and the free version (Starter). The free version is limited by the number of supported architectures, as it only understands x86, and it doesn’t support plugins. The paid version doesn’t have these limitations: it supports a wide range of processor architectures and allows the use of extensions.
IDA includes a built-in debugger, which is quite basic in terms of features, but you might need some time to get used to its unique interface. Additionally, IDA can be enhanced with the Hex-Rays add-on, which decompiles application code into C code. This is an invaluable tool that significantly speeds up program analysis.
Overall, IDA is a powerful and exceptionally refined tool that has been developed over many years. The only downside is that the professional version costs between 1000, depending on the type of license, and it isn’t sold to just anyone. As a result, those who aren’t eligible for purchase have to find alternative solutions. 🙂
Radare2
Radare2 was initially intended as a simple hex editor, but today it has evolved into a full-fledged framework that can assist in debugging and disassembling a wide range of code, including device firmware, viruses, and cracked software.
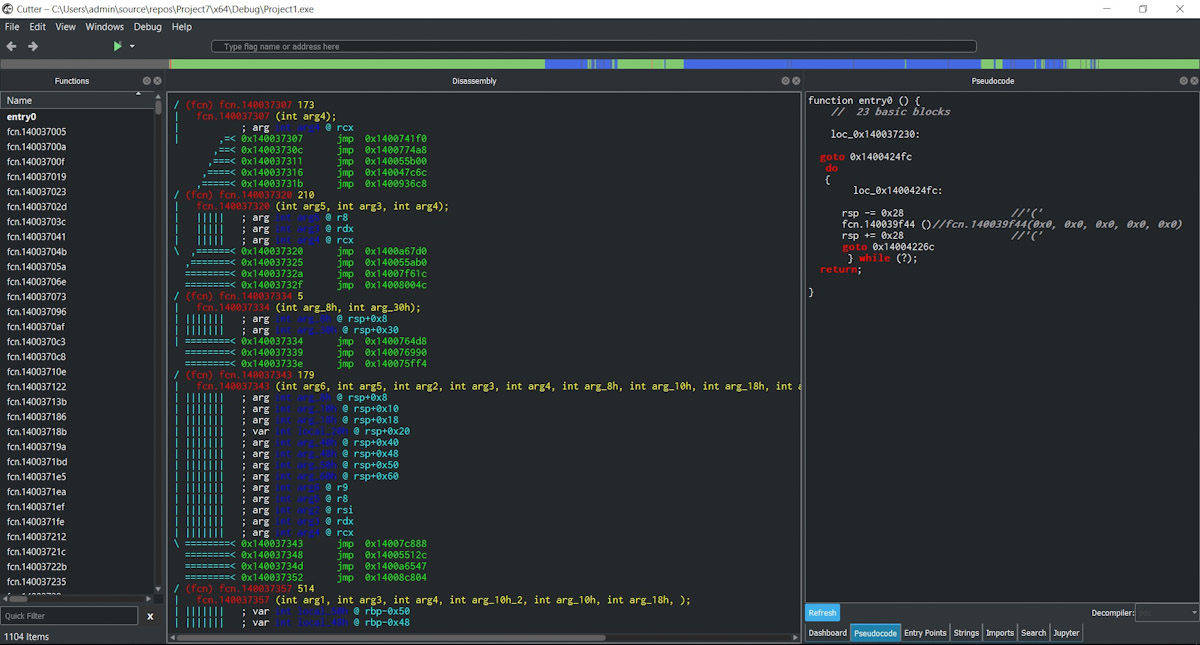
Radare2 is a suite of command-line tools that includes a debugger, disassembler, decompiler, hex editor, its own compiler, binary file comparison utility, and much more. For a graphical user interface, there’s an extension called Cutter. It significantly enhances the appearance and usability of the Radare framework.
The framework supports a wide range of processors and platforms, making it a viable competitor to products like IDA Pro. A significant advantage is that its source code is open, the product is completely free, and it is backed by a dedicated community.
Utility Tools
We’ve covered the basic tools, but reverse engineering is hard to imagine without packer analyzers, network monitors, hex editors, and a host of auxiliary utilities. Let’s take a closer look at some of the key ones.
Detect it Easy (DiE)
This program is excellent for identifying packers and offers a wide range of useful features. For instance, it allows you to view file section entropy, which helps visually detect encryption.
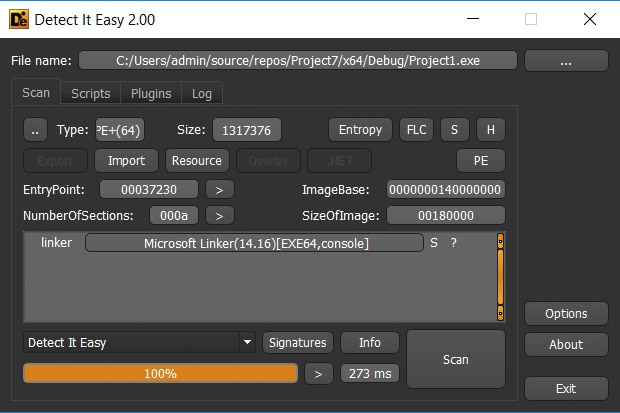
It also includes a resource viewer with the ability to dump data onto the disk. Users can easily browse the import table, and it supports extensions and scripts. It also offers configuration options for signature scanning methods, a file header viewer, and full support for PE and PE+ formats.
The only downside is that the software is rarely updated. However, it’s not abandoned, as a new version was just released recently!
info
You can check out examples of working with DiE in my previous articles: “Manual Unpack: Cracking a Custom Packer with Ransomware GlobeImposter 2.0” and “The Art of Unpacking: Dissecting the Protection of the Tricky Banker GootKit.”
ExeInfoPE
This is yet another detector for packers and protectors. It has a rather unique interface that might not appeal to everyone. However, the program is frequently updated, packed with interesting features, and offers user-friendly hints for unpacking.
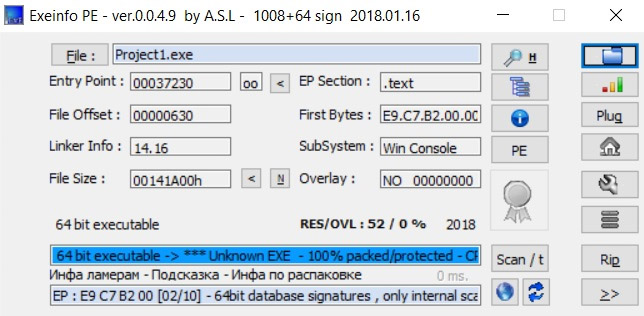
Overall, I would recommend ExeInfoPE to beginners. It comes with a library of automatic unpackers, and the program itself will suggest which tool to use for removing protection layers.
Of course, it includes all the standard features: a file header viewer, section viewer, hex viewer, and even a few small built-in utilities like TerminateProcess and more. Plus, it supports plugins.
HxD
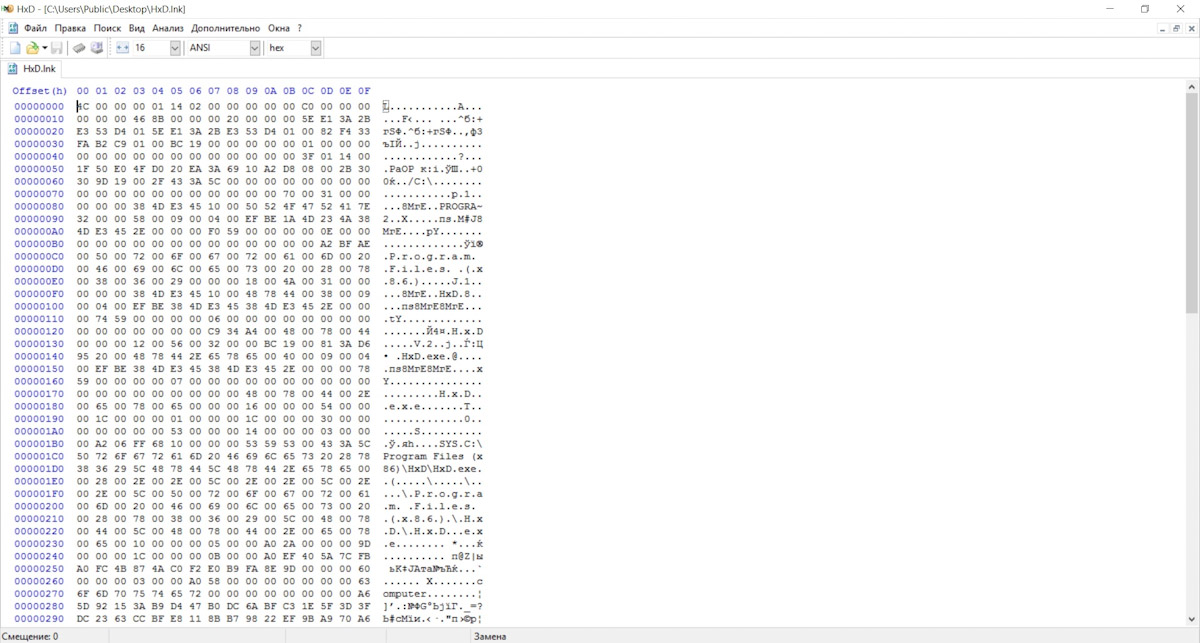
There are often situations where you need to access the hard drive, memory, or an application in binary mode. This is where hex editors come into play, with HxD being a standout example. It’s free, frequently updated, supports popular formats, offers strong search capabilities, and has a user-friendly interface. It also comes with useful features, such as secure file deletion (overwriting files with zeros). Additionally, HxD has a portable version, making it easy to carry on a USB stick.
HIEW
A hex editor with a long history that’s still actively maintained by its developers. It offers both a free version and a paid version (200 with lifetime updates). The interface resembles Norton Commander, which might be intimidating for younger users at first, but it’s easy to get accustomed to. One particularly nice feature is the ability to operate it entirely from the keyboard, using hotkeys for all functions.
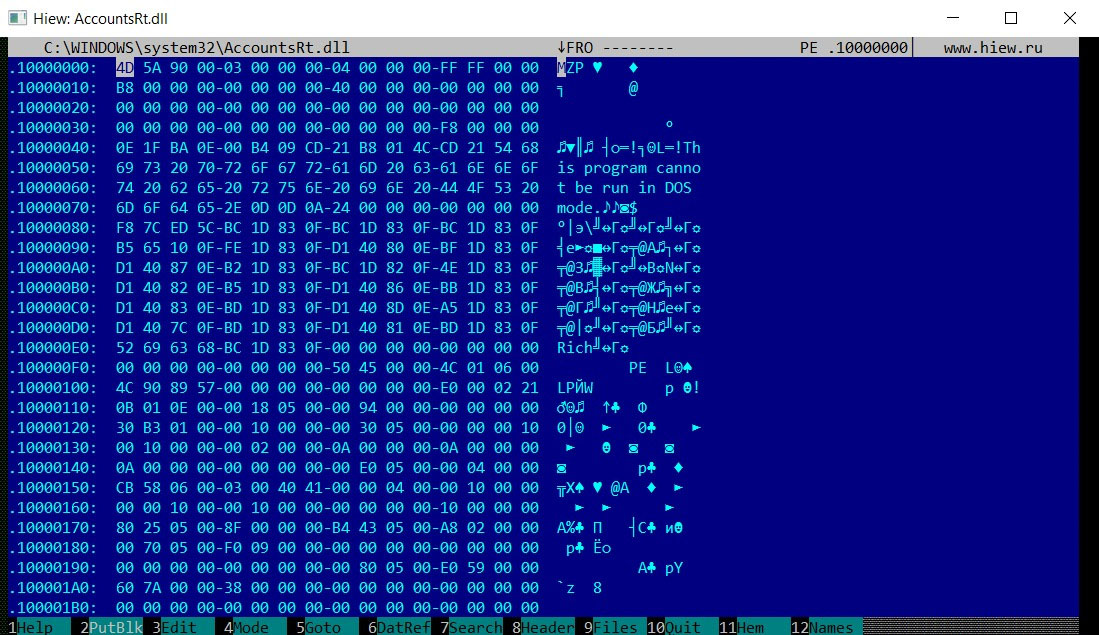
Pestudio
This is a useful tool designed for malware analysis. It automatically scans an uploaded file sample on VirusTotal, provides a detailed display of the application’s import table functions, reveals signs of malicious activity, shows the libraries used, and provides information about the PE file header. You can also work with resources within the program. In other words, it’s a multifunctional antivirus suite for the initial analysis of samples.
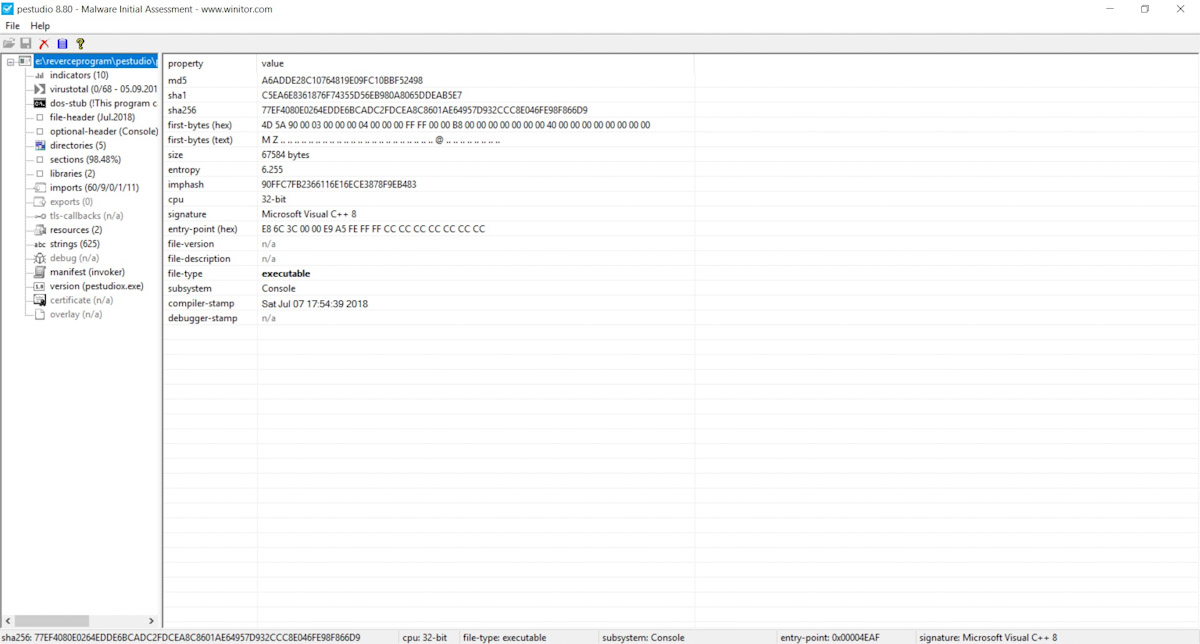
PE-bear
Here’s another interesting viewer and editor for PE and PE+ file formats. It includes a packer and protector analyzer, displays information about file headers, resources, and sections. If desired, you can view the hex representation of data sections and disassemble them into standard assembly mnemonics.
PE-bear has a user-friendly interface and a handy utility for file comparison. The only downside is that the program is rarely updated, even though it’s open-source. So, if you find a bug, you can always fix it yourself.
Fakenet-NG
This program is essential for emulating network interactions. When studying malware samples, it’s often necessary to monitor all network activity: tracking DNS and HTTP requests, sniffing traffic, and identifying the IP addresses of command-and-control servers (as in the case of ransomware bots, for example). For obvious reasons, the virtual machine should be disconnected from the internet, and if the virus notices this, it won’t behave as it normally would.
Fakenet-NG is regularly updated and maintained, ensuring compatibility with the latest operating systems.
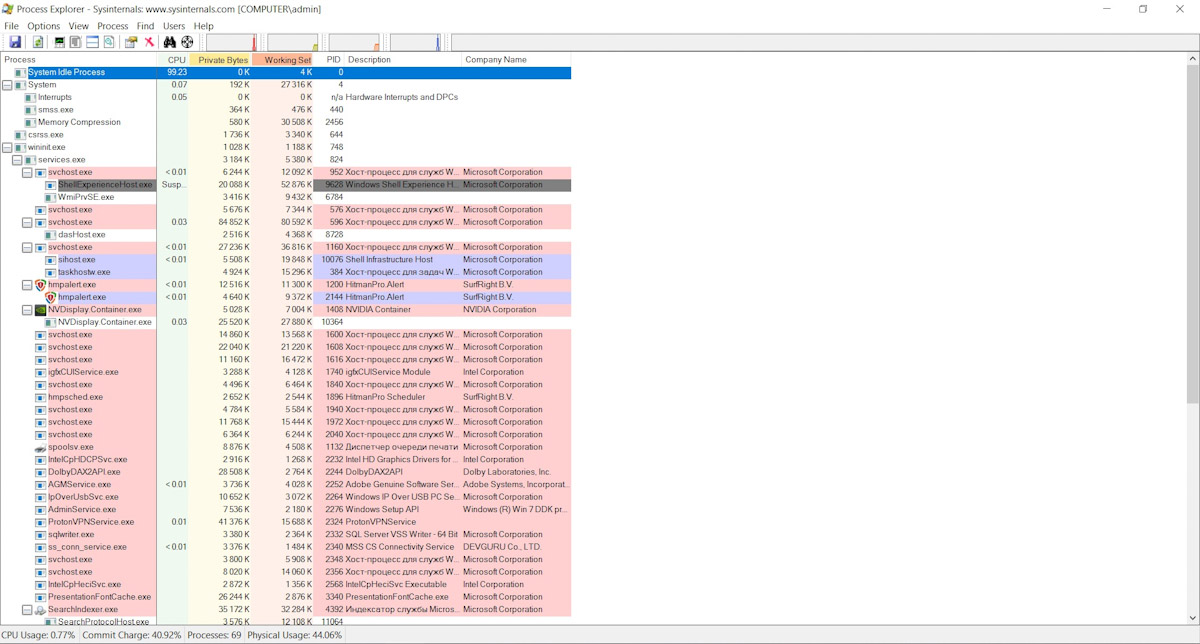
ProcessExplorer
It would be difficult to manage without Sysinternals programs, which monitor file system and process activities. ProcessExplorer displays all processes in the system in a hierarchical tree format, making it easy to see the order in which they are spawned. Additionally, it provides information about which dynamic libraries are loaded into processes, process priorities, digital signatures, CPU usage, and much more.
RegShot
A convenient program for monitoring registry changes. RegShot takes snapshots before and after you run the application you’re interested in, and then shows you where changes have occurred.
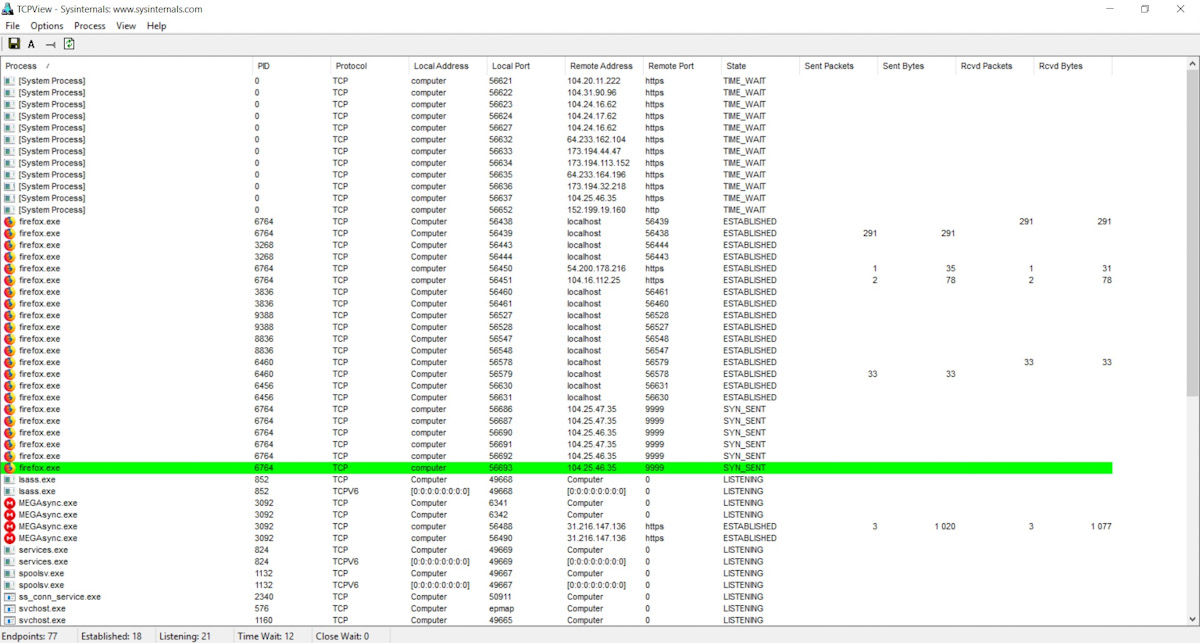
TCPView
A small program designed to monitor the network activity of applications. It allows you to see which ports an application opens (both local and remote), as well as protocols, process identifiers, and packet transfer counters. Overall, it’s one of the most useful tools in any hacker’s toolkit!
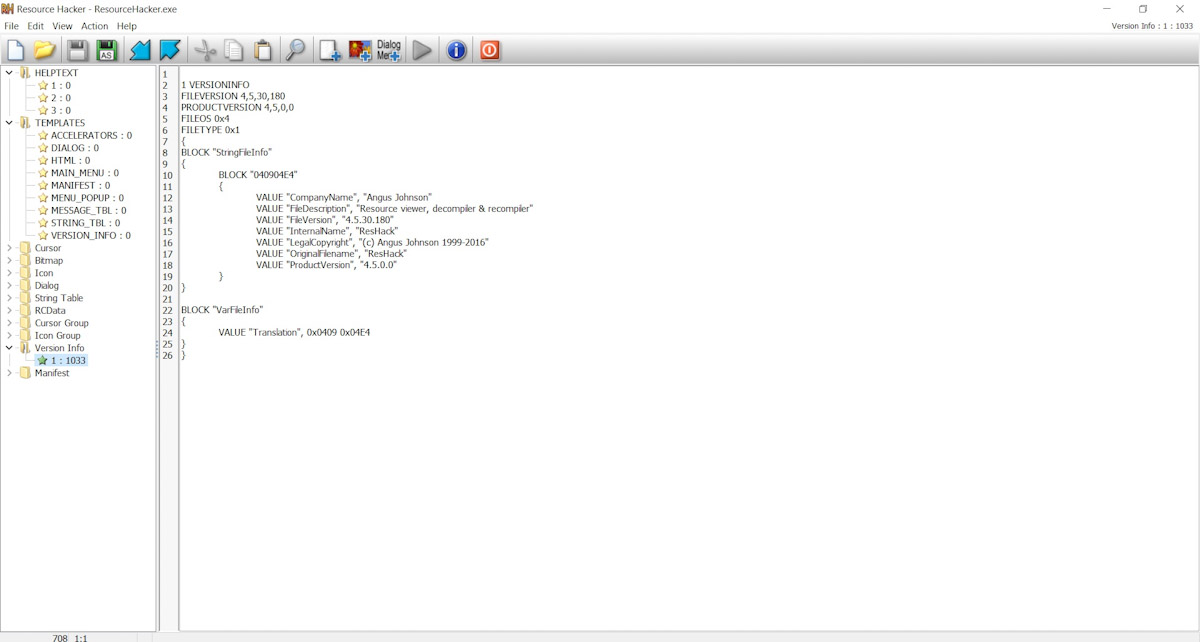
Resource Hacker
A popular software for resource editing. It allows users to modify manifests, icons, text dialog strings, cursor information, and much more. While editing application resources isn’t a frequent requirement, having the right tool at your disposal is convenient when the need arises.
Summary
We’ve covered the main set of tools used to tackle most reverse engineering tasks. I believe these applications will be sufficient for a beginner in reverse engineering. As you gain more experience, you’ll naturally expand your own toolkit over time.
Many reverse engineers are gradually realizing the need to develop their own specialized tools, plugins, and scripts. There aren’t always ready-made solutions available for every task. If you’re aware of such tools or want to share links to other useful programs, feel free to leave a comment!
