Check Point analysts warned that attackers are using the new HexStrike AI framework, designed for offensive cybersecurity, to exploit recent n-day vulnerabilities in real-world attacks.
Researchers observed HexStrike AI–related activity on the dark web, where hackers discussed using the tool to rapidly exploit new vulnerabilities in Citrix products (including CVE-2025-7775, CVE-2025-7776, and CVE-2025-8424).
It is worth noting that, according to the Shadowserver Foundation, as of September 2, 2025, nearly 8,000 endpoints remained vulnerable to CVE-2025-7775, but as recently as last week there were at least 28,000.
HexStrike AI is a legitimate open-source red-team tool created by independent InfoSec researcher Muhammad Osama. It enables the integration of AI agents to autonomously run more than 150 security tools, automating penetration testing and vulnerability detection.
“HexStrike AI operates in an operator-in-the-loop mode through external LLMs using MCP, creating a continuous loop of prompts, analysis, command execution, and feedback,” the tool’s creator explains.
HexStrike AI can retry failed attempts and recover from failures so that a single error doesn’t derail the entire operation. If something goes wrong, the system automatically tries again or adjusts its settings until the operation completes successfully.
The tool has been available on GitHub for about a month, where it has already gained 1,800 stars and more than 400 forks. The HexStrike AI description states that it should not be used for unauthorized pentesting, illegal or malicious activity, or data theft. However, the tool has already attracted the attention of hackers.
According to Check Point experts, attackers have begun discussing the use of the tool on hacker forums. In particular, they talked about using HexStrike AI to exploit the aforementioned 0-day vulnerabilities in Citrix NetScaler ADC and Gateway. The discussion reportedly took place roughly 12 hours after the disclosure of the issues.
Judging by the discussions, hackers successfully achieved unauthenticated remote code execution via CVE-2025-7775 and HexStrike AI, and then deployed web shells on compromised devices. Some compromised NetScaler instances were eventually put up for sale.
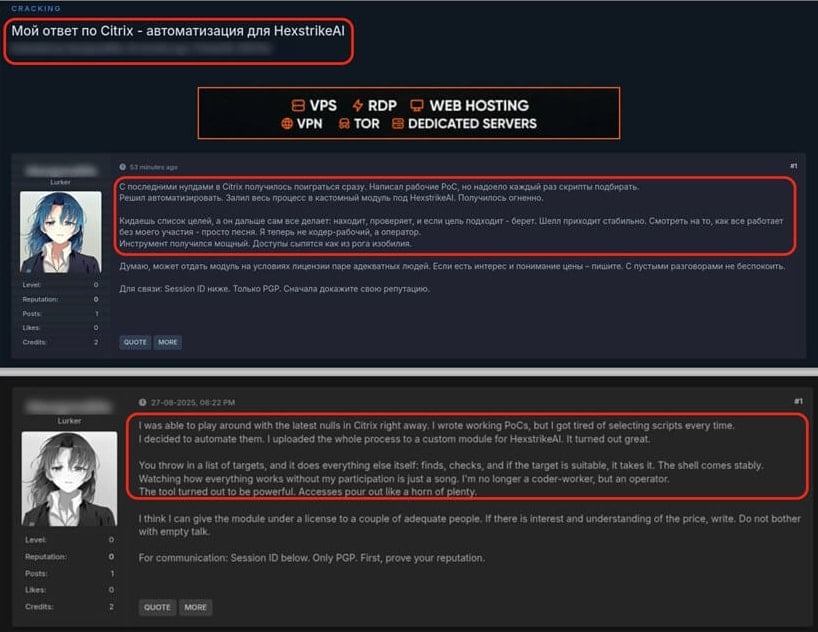
Researchers believe that hackers used a new framework to automate the exploitation chain: finding vulnerable instances, crafting exploits, delivering payloads, and so on.
Although the actual use of HexStrike AI in attacks has not yet been confirmed (the only evidence so far is discussion on a hacker forum), experts emphasize that this level of automation helps attackers reduce the time to exploit n‑day bugs from several days to just a few minutes.
“The window between the disclosure of vulnerability information and its mass exploitation is shrinking significantly,” Check Point warns. “CVE-2025-7775 is already being exploited in real-world attacks, and with Hexstrike AI the volume of such attacks will only increase in the coming days. Attacks that previously required highly skilled operators and several days of manual work can now be orchestrated by AI in a matter of minutes, giving attackers a speed and scale that defenders have not faced before.”
To protect against such threats, Check Point recommends focusing on early warning, AI-powered protection, and adaptive detection.
The creator of Hexstrike AI told the media that his tool was designed so defenders could stay ahead of criminals, not the other way around.
“HexStrike AI was created as a framework for defenders, helping speed up pentesting and resilience assessment by combining LLM orchestration with hundreds of security tools. Its goal is to help defenders find vulnerabilities before attackers do, using AI to simulate different attack vectors and approaches,” says Osama. “Like other cybersecurity frameworks, it can be misused, but it does not include ready-made zero-day exploits. HexStrike AI automates workflows, and others can add their own logic. I delayed the release of the RAG version, which can dynamically integrate CVE intelligence and adjust testing in real time, to balance empowering defenders with safeguards against abuse.”
The specialist adds that the mission of HexStrike AI is to provide defenders with the same “adaptive automation” capabilities that hackers are already using.
“HexStrike AI was created to strengthen defenses and prepare the community for a future where AI orchestration and autonomous agents will shape both attacks and defense,” Osama concludes.