The topic of hacking and stealing cars using the Flipper Zero has once again made headlines in the global media. This time, hackers claim to be selling “secret firmware” for the gadget that supposedly can be used against Ford, Audi, Volkswagen, Subaru, Hyundai, Kia, and a number of other brands. The Flipper developers explain that this is not true.
At the end of last week, the outlet 404 Media reported on the underground trade in modified firmware for the Flipper Zero that allegedly allows people to break into and steal cars.
Journalists spoke with a hacker named Daniel, who allegedly lives in Russia, as well as his partner Derrow, who have developed and sell special Unleashed firmware for the Flipper Zero on the dark web.
Daniel said that he bought and obtained various fragments of source code needed to build the firmware from other people. According to him, these firmware builds may indeed be used for stealing cars, but they are also popular among technicians at auto repair shops.
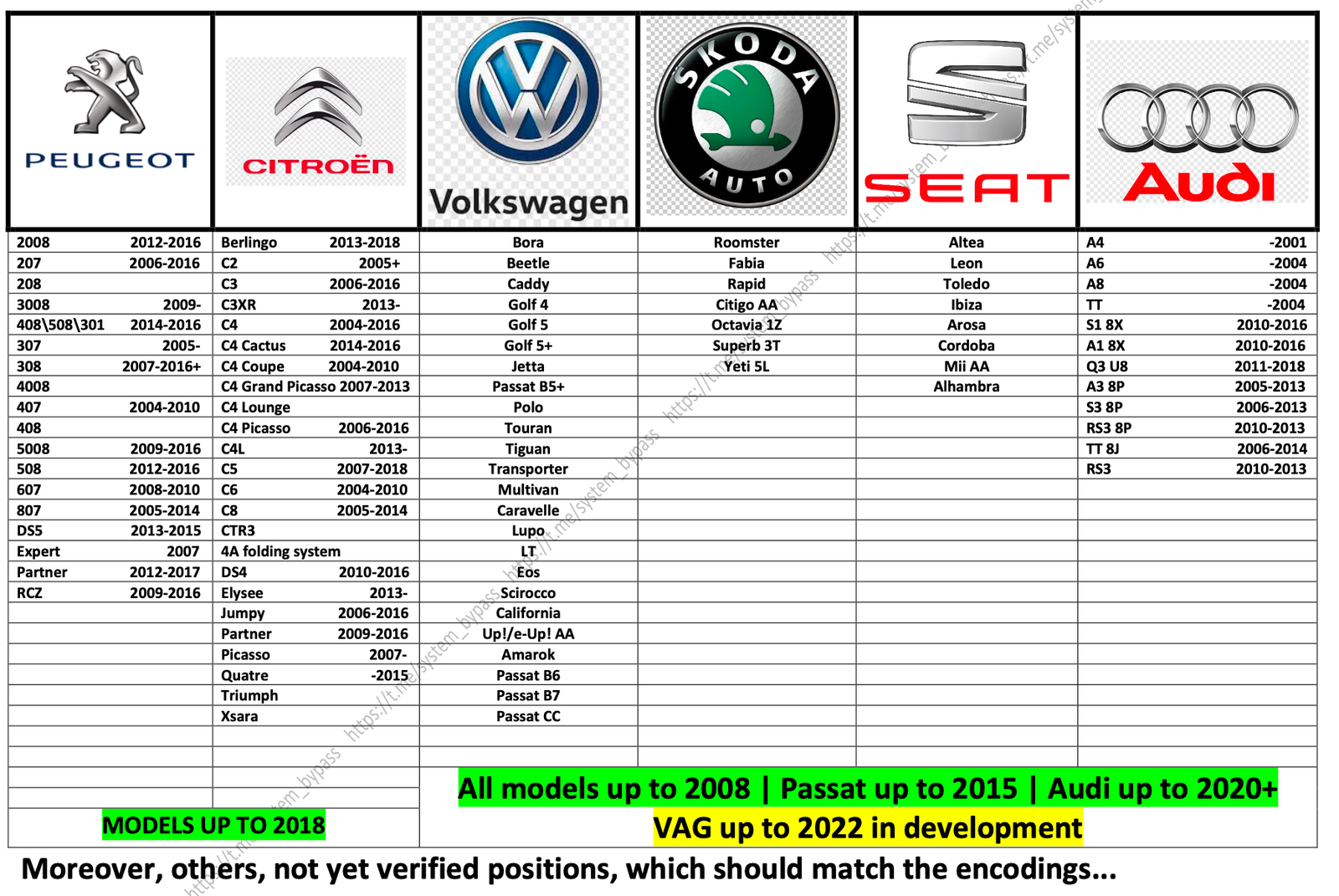
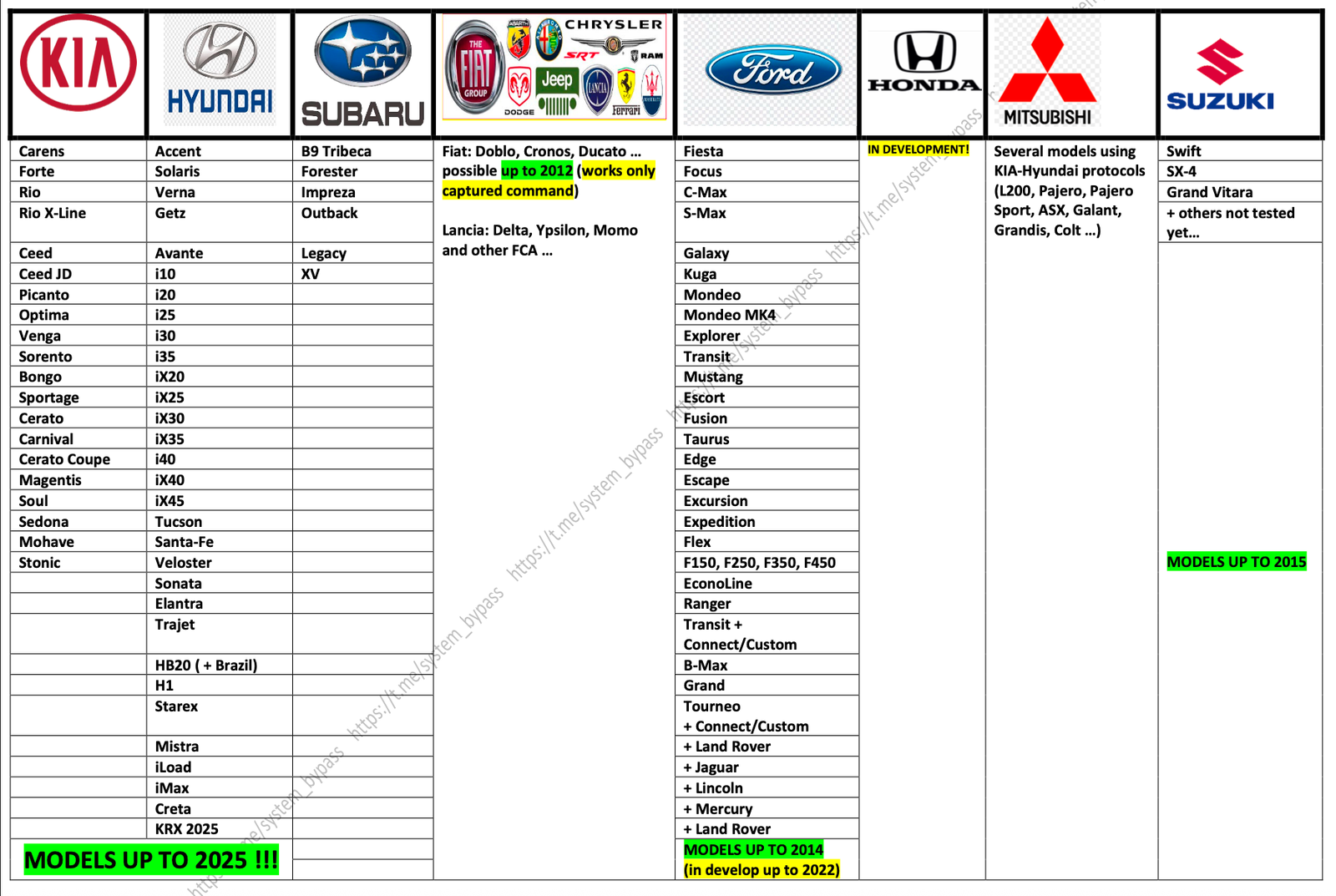
Hackers claim that a modified device can intercept key fob signals and compute the next code to unlock the car, creating a “shadow copy of the original key.” According to the provided documentation, such attacks work against nearly 200 car models, including 2025 model-year vehicles from Ford, Audi, Volkswagen, Subaru, Hyundai, Kia, Fiat, Mitsubishi, Suzuki, Peugeot, Citroën, and Skoda.
Two firmware versions are offered for sale: a basic one for $600 (current version only) and an extended one for $1000 (with future updates and support), with payment accepted in cryptocurrency. The firmware is allegedly tied to a specific device via its serial number to prevent unauthorized distribution. To that end, buyers are asked to provide photos of the Flipper Zero box showing the device’s serial number, as well as a photo of a specific part of the gadget’s settings.
Daniel told reporters that over two years he sold this technology to about 150 buyers. Derrow, meanwhile, claims that “sales are through the roof.”
In the article, the journalists expressed concerns that if this technology becomes widespread, it could lead to a surge in car thefts. The outlet writes that in 2026 “Kia Boys could become Flipper Boys,” referring to the well-known trend of youths stealing Kia and Hyundai vehicles.
In response to numerous media reports, one of Flipper Zero’s creators, Pavel Zhovner, published a lengthy post on the official blog.
“Some darknet marketplaces have begun selling so-called ‘private’ firmware for Flipper Zero, claiming it can be used to hack countless cars. Allegedly, information leaked online about new vulnerabilities that allow breaking dynamic protocols such as KeeLoq.
In reality, all these methods were published more than 10 years ago. Nothing new. The authors of such firmware are simply reworking known vulnerabilities and passing them off as ‘new hacks.’ And importantly, these vulnerabilities have nothing to do with real car thefts, because they do not let you start the engine,” Zhovner writes.
The developer explains that KeeLoq was developed in the 1980s and was mainly used in older access systems (for example, garage door openers and early car alarms). It is a rolling code (also known as hopping code) system, where each transmission uses a new unique signal encrypted with the manufacturer’s 64-bit key.
According to Zhovner, the manufacturer key is the weak point of KeeLoq. The problem is that car makers often used the same key for an entire model lineup. If this key leaked, attackers could intercept signals from any remote key fob of that brand.
“The authors of these ‘hacker’ firmwares are simply distributing old keys stolen from various automakers. There’s nothing new here; such vulnerabilities were described in detail back in 2006,” explains the creator of Flipper. “Since then, automakers have moved to more modern radio protocols with two-way authentication, where the car and the key exchange messages to verify authenticity.”
After that, Zhovner reiterates the points that the Flipper Zero creators explained in detail in 2024, when the Canadian government announced it intended to ban the sale of Flipper Zero and similar devices in the country, claiming they could allegedly be used to steal cars.
In particular, he points out that real car thieves usually target keyless entry and ignition systems. They use relays and transmitters that relay the signal from the legitimate key fob, making the car believe the real key is nearby.
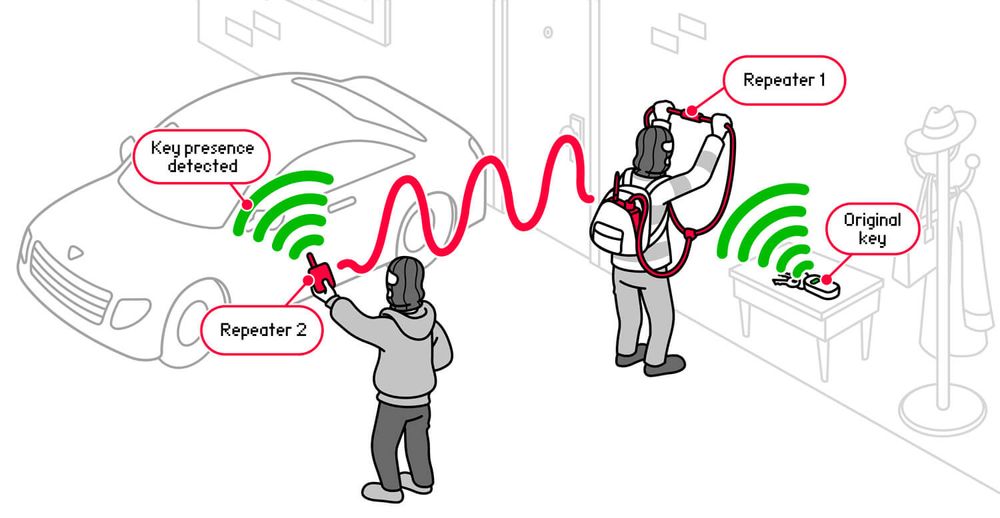
“If your car can be attacked with a Flipper Zero, it can just as easily be hacked with a piece of wire,” Zhovner sums up.
