The Editorial Board decided to publish this material after reviewing a large number of articles in various periodicals, including technical ones. All these publications, with no exceptions, repeat the same trivial recommendations: “use a complex screen lock code”, “enable the fingerprint scanner”, “disable Smart Lock”, “make use of two-factor authentication”, and the most sarcastic recommendation for many Android users: “update your OS”. No doubt, all these steps make sense, but are they sufficient to make your phone secure? We believe not.
This material is based on an original story by Oleg Afonin, an expert in mobile forensics, ElcomSoft, published in Xakep.ru.
Editorial
You may set the strongest screen lock password, but if your phone uses full disk encryption (FDE) and you have not enabled the Secure Startup option, then, regardless of the lock code length (you are free to use a hundred characters), the encryption key would still be based on default_password. EDL exploits are readily available to grab (and decrypt) your data based on this setting.
Disabling Smart Lock is an essential step, but that alone is insufficient. Are you confident in the face scan technology installed on your device (provided that your phone has this feature)? Most phones out there save for the Apple products and a counted few Android devices implement this feature in the “face id me too but cheap price” fashion. Security? Never heard of it.
Are you aware that happens if the attacker breaks into your PC? Your cloud passwords are readily available with a push of a button; they can simply reset your lock screen password. (Fortunately, this trick no longer works with all devices, but some are still susceptible). Finally, you must understand that if somebody steals your cloud password (be it a Google, Apple or Samsung account), they won’t even need your phone to extract everything they want from the cloud, which most probably contains even more valuable data than the phone itself.
In this article, we’ll depart from the trivial advice everyone’s sick and tired of (yeah, turn on the screen lock and do the update) as you’ve already done that. Instead, we will address the techniques the law enforcement authorities and secret services may use on your phone to extract confidential information.
What’s the toughest situation for a forensic expert when it comes to mobile devices? It’s discovering a brick of a phone next to a corpse. In order to gain access to whatever information stored in that phone, the police will have to use The Tool (a bunch of them, actually) that exploits known vulnerabilities in the phone’s software or hardware. The police will pay the suspect a visit, analyze her computer, and extract the password caches in her e-mail clients and Web browsers. Then they would sign in to the cloud using the login and password found in the browser – and voila! In some cases, it is even possible to remotely reset the lock screen password (fortunately, most OEMs today no longer offer this option by default). They may connect your phone to The Tool (GrayKey, UFED or whatever is in fashion on that day). The tool will attempt to gain access to the data and try to decrypt it (by either exploiting a known vulnerability or using a decrypting bootloader) regardless of the phone’s screen lock password.
Can you protect your phone against some of these attacks? While the answer is “it depends”, you will at least become fully aware of protection techniques that can be used to safeguard your data, as well as the risks remaining even if you’ve done everything right.
Cracking your iPhone
A number of factors determine how difficult it is to crack an iPhone, including the iOS version (yes, they recommend you to install the latest updates for a reason), lock screen passcode complexity, and the device status (to be addressed in more detail below).
Speaking of the iOS version. Are you still using iOS 11? If that’s the case, I have some bad news for you: it is possible to brute-force its screen lock passcode or quickly extract all information through physical acquisition. The lock screen passcode complexity and device status (AFU, BFU, powered on or off, USB restricted mode or not, etc.) will affect the recovery speed, which is actually good news.
Cracking the iPhone: iOS 11
If the phone is turned off, the password recovery speed will be very low (one password in about ten seconds). If your screen lock code consists of six digits, the brute force will last forever. This situation is called “BFU”, or “Before First Unlock”.
If the phone is on and you had unlocked it at least once after turning on, the first 300,000 passcodes will be checked very quickly; the brute-force search speed is so high that it makes it possible to break a four-digit code automatically in half an hour. So, always use six-digit passwords! This situation is called “AFU”, or “After First Unlock”; we’ll use this term later.
If you have triggered the emergency SOS mode (by pressing and holding the power button and volume button), the phone switches back to the ‘slow passcode search’ mode just like devices in the BFU state (“falls back to BFU speeds” would be the technically correct, but difficult to understand term). A six-digit passcode is a great protection mechanism in that case.
With iOS 11.4.1, Apple has introduced the USB restricted mode making it impossible to crack the device using the brute-force method. Within an hour after the last unlocking, iOS blocks access to the USB port. To activate this protection feature, the USB Accessories toggle should be disabled (on the left). However, some of the tools available to the police are rumored to have a way to bypass this privacy safeguard. So, make sure to update your phone to iOS 13 asap! (Oh, there we go: “update your OS to the latest version”…)
Cracking the iPhone: iOS 12
The situation with iOS 12 is pretty interesting. On the one hand, Apple has fixed a number of vulnerabilities that made it possible to unlock iOS 11 devices by brute-forcing passcodes. Furthermore, the USB restricted mode has been enhanced: now the USB port (specifically, the ability to transfer data via the Lightning connector) is turned off as soon as the screen is locked. However, this works only if the phone was not connected to a PC, wired audio system or other accessories; otherwise, the behavior remains the same as before (i.e. the port is blocked in a hour). In addition, the USB port is now blocked when the emergency SOS mode is triggered (by pressing and holding the power button and volume button).
On the other hand, iOS 12 inherited some vulnerabilities from iOS 11. For instance, two significant flaws making it possible to get full access to the file system though privilege escalation, without a full-scale jailbreaking, had existed all versions of iOS up to iOS 12.1.2. Therefore, if experts get an unlocked phone with iOS 12.1.2 or older, they may easily extract data. iOS 12.1.3 patched some vulnerabilities, but only iOS 12.1.4 managed to safeguard the device from the known exploits. So, to reiterate: it might be a really good idea to update iOS to the latest version!
Now, how are they going to crack your iPhone with iOS 13?
The best scenario for you is if your phone is turned off. In that case, the experts won’t be able to use the brute-force method – at least, until somebody figures out how to bypass the USB restricted mode.
If the phone was turned on and unlocked at least once after that (but locked at the time of the attempted crack), it is nearly useless for the experts as well. Of course, they may try to connect the device to your PC and backup it to iTunes – provided that the USB restricted mode was not activated yet and you had connected your iPhone to iTunes at least once. How to protect it against this trick? Set a long and difficult backup password!

Of course, this password can be reset in all iOS versions starting from iOS 11 – but only from the iPhone and provided that the lock screen code is known to the expert. But even in that situation, you may additionally protect the iTunes backup password from resetting by turning the Screen Time Passcode on.
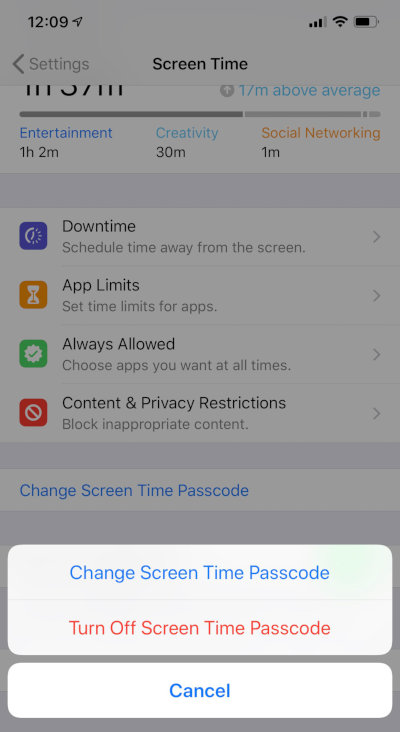
Screen Time Passcode is not a universal solution. In fact, this is a parental control tool, and protection against resetting the backup password is its secondary function. However, it cannot be bypassed even using the brute-force method: iOS will increase delays between the attempts until the search speed drops to one attempt per hour (starting from the tenth try).
Why all of that does not matter if you’re using an older iPhone
So we’ve covered pretty much everything about iOS 11, 12 and 13. If you are using the iPhone Xs, Xs Max, Xr, or any model from the iPhone 11 generation, you’re good. Set a 6-digit passcode and you’re protected.
However, all iPhone and iPad models based on the Apple A5 through A11 generation SoC have a severe, unpatchable, hardware vulnerability in their bootloader. This vulnerability allows experts to extract information from AFU devices quickly and efficiently, even without attacking the passcode. Built-in encryption will not allow experts accessing data in BFU devices just as easily; a brute-force attack must be performed against the iPhone’s screen lock passcode.
As a result, a long and complex passcode will protect your data, but only if your phone is in the BFU state (Before First Unlock, i.e. powered off or just rebooted). If your data is highly confidential, upgrading to the latest iPhone is the only solution.
[xakepcut]
What if they take your unlocked iPhone
In theory, the police would use sophisticated devices to crack your smartphone. In reality, they will try to extract as much information as possible in a minimum time frame. Officers will ‘kindly ask’ you to unlock the phone, seize it, and bring it to a room in the back; this is particularly common for routine border inspections. Let us see what iOS can do to protect your privacy.
So, what happens if iPhone gets into the wrong hands unlocked?
First, the policemen may manually review data that are of major interest: your social network activities (particularly, your selfies with guns over soldier’s bodies), your messages, both text and iMessages, and, of course, your photos and videos.
In certain cases, the Health app data would be closely reviewed as well. This app shows your activities at any specific time (e.g. whether you were walking or running). In many situations, a routine arrest results in detention and lodging of criminal charges on the basis of information found in the smartphone.
Your defense strategy is to never surrender the unlocked device to the police. Refusing to unlock your smartphone is your right (except for some special cases, e.g. border crossing; a shady law enforcement practice that is being questioned in the US at the time of this writing). Note that even if the iPhone is unlocked, the screen lock passcode of your face/fingerprint are still required in order to view iCloud Keychain logins and passwords. The passcode is required to disable Find My iPhone, reset the iTunes backup password, or connect the phone to a computer.
Second, the expert may connect your phone to a GrayKey or UFED box. Older iPhones (up to and including the iPhone 8/8Plus and the iPhone X) can be imaged with or without a passcode, while newer devices (the iPhone Xs and 11 generations) require a lengthy attack on the passcode.
Finally, they can try extracting the data via an iTunes-style backup. To do so, the iPhone must be connected to a computer, which in turn requires the screen lock passcode. The experts may try to bypass this using a lockdown file from your computer; in turn, you can specify both the backup password and a Screen Time passcode, which serves as an additional security level (but can in turn be extracted from iCloud).
Cracking your Android smartphone
Similarly to ‘the iPhone case’, police officers may request you to unlock the device. If you just did, sit back and relax: there’s nothing else you can do to hand over the most of your data. Unlike iOS trying to protect your privacy, Android enables the investigators to retrieve the following information from an unlocked smartphone:
- The contents of the device’s internal storage, including photos and videos;
- Mail, chats, and text messages;
- The full list of passwords saved in Chrome (sometimes the password to your Google Account is stored there, too);
- Detailed location history;
- Google Fit data (can also be exported); and
- Calls and contacts.
Cracking the passcode
So can you crack a screen lock passcode to that Android phone? We’d love to give a definite answer, but that would not be possible due to the sheer number of Android devices, chip sets and even manufacturers. There’s no one to tell whether they can crack that phone’s passcode; their best answer is “plug it in and check it out”.
Does a screen lock passcode really secure your data? In the case of Android devices, the answer is “it depends”. For many models, especially older ones (think 2018 and older), the screen lock passcode has very little to do with encryption.
The real answer depends on the encryption algorithm of a specific device. Android smartphones released with Android 6 or newer must be encrypted once you’ve set them up. However, there are different grades of encryption. Many olded devices use Full Disk Encryption (FDE). In FDE mode, the user partition is encrypted with device credentials. The encryption key is based on hardware seed and a fixed password default_password.
Yes, you read it right. The data in your Android smartphone can be encrypted with default_password. Does that mean just anyone can decrypt it then? Not really. The encryption key is generated inside the Trusted Execution Environment (TEE) based on a hardware-bound key that is unique for each device. That key never leaves the TEE. If you remove the memory chip from the phone and copy the data you won’t be able to decrypt it without the TEE key. Therefore, one must not only retrieve the data (e.g. via EDL mode), but to also crack the TEE or replace the bootloader. Decrypting bootloaders exist; for instance, Cellebrite makes tools covering the entire chipsets. In other words, no access without the tools, but easy access with the right tool.
Even if your phone uses the obsolete FDE protection, you may safeguard personal data by enabling Secure Startup. In that mode, the encryption key will be re-encrypted with a hardware key and your screen lock passcode (instead of the default_password). This method has a drawback: the phone won’t boot until the user enters the lock screen passcode; if the phone accidentally restarts, you won’t be able to answer a call until the boot-up is completed.
The above drawback is eliminated in new File-Based Encryption (FBE). FBE devices use user credentials (i.e. the screen lock code) to encrypt most data. However, the apps and some databases required for the startup are encrypted using device credentials (i.e. the hardware key). FBE devices do not have Secure Startup.
Cracking the screen lock passcode is only required in two cases. First, the passcode is required if you want to decrypt information stored in FDE devices with Secure Startup enabled. Second, you also need the passcode to decrypt all FBE devices. The specific procedure may differ depending on the chipset, but the general principle is the same: connecting to the USB port and launching a brute-force attack.
Decrypting FDE devices in standard mode without Secure Startup does not require the user’s passcode.
Of course, smartphones have built-in protection against such attacks. Qualcomm TrustZone and the Trusted Execution Environment (TEE) only allow trustlets (small applets signed with manufacturers’ private keys). The Gatekeeper subsystem performs passcode authentication and limits the brute force speed at the hardware level to a crawl. As a result, even a four-digit passcode will not be recovered quickly, while a six-digit passcode can take years to break. The Gatekeeper also limits the speed of password recovery on FDE devices with Secure Startup as well as on FBE devices.
As usual, there are vulnerabilities, exploits and workarounds allowing to bypass many of these security measures. As an example, older Qualcomm SoC’s (up to and including Snapdragon 821) had a vulnerability allowing to execute unsigned trustlets and bypass brute-force limitations. Other vulnerabilities exist in modern SoC’s, many of which are exploited by forensic analysis tools such as UFED or Oxygen Forensic Suite. However, Android smartphones are built using hundreds of different chipsets (literally), and each model requires dedicated research and development. The chance that the law enforcement authorities will need to crack that particular phone are rather low, making many known vulnerabilities unfeasible to exploit.
The following data extraction techniques can be applied to flagship smartphones based on Qualcomm processors:
- Old models (up to and including Snapdragon 821): exploits; except Secure Startup;
- Old models with Secure Startup or FBE: GateKeeper limits the brute force speed. On some devices, it is virtually impossible to perform a cold boot attack except for some popular models;
- Newer models (Snapdragon 835 and up), EDL and TEE exploits are unavailable. In rare situations when the FDE encryption is used, it is pretty difficult to decrypt the data partition (although possible in certain cases); and
- Newer models (Snapdragon 835 and up) with FBE: no generic exploits; some models can be decrypted in a limited number of cases without a passcode; others require brute-forcing the passcode; the speed will be slow (GateKeeper).
Protecting your smartphone from unlocking and physical data acquisition
First, check the encryption system your smartphone uses. To do so, enter the following command in Android Debug Bridge (ADB) command-line tool:
$ adb shell getprop ro.crypto.type
If the command line displays the word “file”, your smartphone uses the FBE system. If File-Based Encryption is used, then:
- Set the screen lock passcode of at list six digits;
- Disable the USB Debugging option.
If FDE is used, enable Secure Startup as follows:
- Settings > disable screen lock passcode;
- Create a new screen lock passcode. The system will prompt to enable Secure Startup.
- Disable the USB Debugging option.
Can you change the encryption type from FDE to FBE? Generally speaking, you can’t. Some Google devices (e.g. the Pixel C tablet) could be switched from FDE to FBE while FBE was still in development. Modern devices do not have such a possibility.
General recommendations
Most articles dedicated to Android security repeat a number of recommendations: set a strong screen lock passcode or a complex pattern, turn Smart Lock off, update Android, and turn two-factor authentication on. These recommendations are reasonable but way too bubbleheaded. Bear in mind that for many Android phones, the length of the screen lock passcode does not affect security in any meaningful way; turning off Smart Lock is useless if the user enabled (or forgot to disable) the USB Debugging option, while checking for Android updates makes no sense if the OEM skimped on updates (like most of them do).
So here is our own list of recommendations followed by additional details below.
- The screen lock passcode. It must be enabled, and it must have at least six digits. Check the encryption type is used on your smartphone, FDE or FBE. If it is FDE, enable Secure Startup.
- Disable the USB Debugging option. If it is enabled, other security settings are is pointless.
- An unlocked bootloader is a large security breach. If the OEM Unlock option is present in Developer Settings and you are not going to unlock the bootloader any time soon, disable the setting.
- If your phone allows to select the connection mode after connecting to a computer, select the Charge Only option. Otherwise, the content of your memory card, including photos and videos, could be copied from a locked phone. Check what happens after the connection. The majority of modern devices have the Charge Only option set by default. If the default mode of your phone is File Transfer or MTP, change it or forget about security.
- Of course, having the latest Android version is a good thing, and up to date security patches are absolutely mandatory. The problem is that most producers release updates with huge delays, leaving known vulnerabilities unpatched for months and even years. If your phone is not the current flagship, you can forget about speedy updates.
- Smart Lock is an absolute evil from the security perspective. Disable Smart Lock including Face Unlock. If your phone is equipped with a 3D face scanner with infrared flood lighting, disregard this recommendation.
- Turn off the screen lock timeout on your phone: Settings → Security & Location → Automatically lock → Immediately.
- Beware of apps from unknown sources. The Unknown Sources switch must be disabled; otherwise it makes your phone vulnerable. By the way, this option is absent in Android 8: permissions are given to specific apps. Use the Special App Access setting to administer it.
- Some iPhone apps record user’s actions and transmit screenshots for analysis, including personal information, passports, and credit cards. In Android, any app with the “Draw over other apps” permission or launched as an Accessibility service can do this. Make sure that you do not have any dubious apps with these permissions running.
- Never forget about the list of Device Administrators. Apps from this category may be used to remotely reset the screen lock passcode, lock/unlock the device, and revert it to factory settings. If the list includes Google Find My Phone or Exchange Admin apps installed by your employer, everything is fine. But make sure that there is nothing extra there.
- Some OEMs include free backdoors in their phones. The device firmware may include tools collecting information for analytical purposes. Sometimes, this information includes your contacts and passwords. There is little you can do about it. While you can try to limit the transmission of analytical information using local VPN services, the best course of action is just getting rid of that phone. Oh, and your personal information had already leaked anyway.
- Some Play Store apps request (and usually receive) some absolutely crazy permissions. For instance, you could grant Angry Birds access to the camera, microphone, and contacts (you know, just in case), permit the Calculator app to track your location, and authorize a photo gallery to read and send SMS messages. Review the list of permissions; a simple analysis of granted permissions may result in a big surprise.
- Never store your Google Account password in Chrome.
- Enable two-factor authentication.
Lock screen timeout
A long time ago, typing the screen lock passcode was the only, slow and inconvenient way to unlock the phone. Some users did not like the need to repeatedly enter the password and gave up security for the sake of convenience. Both Google and Apple offered a solution for this problem: the lock screen timeout.
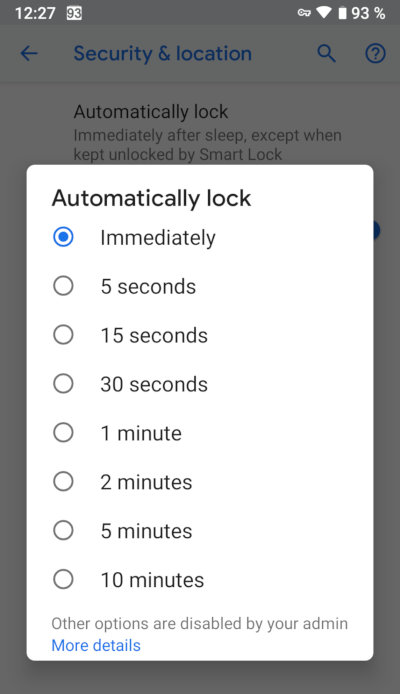
If this option is on, you may turn the phone display off, then turn it on again and access the home screen without tapping the screen lock passcode. The timeout can be set depending on your preferences. A delayed screen lock catastrophically compromises your security.
There is a similar setting in iOS: Settings → Touch ID & Passcode → Require Passcode. Its purpose is the same, but there is an important difference from Android smartphones: if you use Touch ID or Face ID, the only option available to you in modern iOS versions is Immediately (i.e. locking the phone immediately after turning the display off). However, if you disable biometrics, other options become available as well, including Never (requesting the screen lock passcode only after the first startup and from time to time pursuant to ever-changing Apple policies). Important: some options may not be available if an external security policy is installed.
Smart Lock
Why do we hate Smart Lock so much? Because it allows to unlock the phone using techniques having nothing to do with security. Below are a few examples.
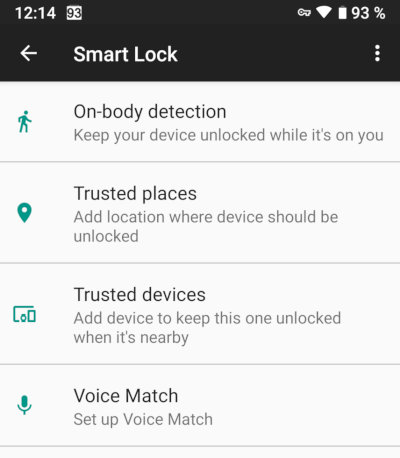
Face Unlock. This Smart Lock function has nothing to do with biometric authentication. It just compares the user’s image with a photo taken with the phone’s front facing camera. Such “face unlock” can be easily cheated with a simple print.
An exception from this are the few phones with real, biometric-grade face unlock function such as the Xiaomi Mi 8 Pro. However, I would not rely on any of those, as neither the regular Mi 8 nor the successor Mi 9 are equipped with proper face unlock (their single-camera emulation is a bad joke).
Trusted places. Your phone is automatically unlocked in the vicinity of places you frequently visit. If the device is stolen from your pocket near your home, the thief won’t have any problems unlocking it.
Trusted devices. The phone may be automatically unlocked when connected to a trusted Bluetooth device. Believe me, policemen are intelligent enough to use your smart watch or tracker to unlock your smartphone.
Voice Match, On-body detection. Somewhat experimental options enabling the user to enter the screen lock passcode more rarely.
If Smart Lock is so unsafe, why does it still exist in Android phones? In fact, this function is a legacy of the times when the lock screen passcode or pattern were there the only ways to unlock your phone. Many users did not want to spend the time and effort unlocking (mind you, the trick was virtually impossible in gloves). As a result, people had left their phones unprotected. To accustom users to the screen lock protection, Google had to lower the security bar significantly: new options delaying the screen lock by 10-15 minutes since the last unlocking have been introduced. Smart Lock is part of the same story. Neither it nor the lock screen timeout are really necessary nowadays: modern scanners recognize user’s fingerprints instantly, and face unlock is pretty fast and secure as well.
Face unlock
How secure is face unlock? We did not touch this aspect in the chapter dedicated to the iPhones: Apple products use systems with an extremely high level of security. In Android smartphones, face unlock modules can be miss or… miss. With very few exceptions such as the Mi 8 Pro or very few Samsung phones (we won’t name the models just to confuse things) feature face unlock systems that might be secure. To confuse users mode, these “me too!” faux Face Unlock systems were short lived and coincided with the lifecycle of the iPhone X, which pioneered the technology. The 2019 generation of Android phones tends to use dumbed down schemes based on photos taken on the front facing camera or 2D infrared photos. Too bad, an increasingly popular trend of the day is: “My phone can do everything your iPhone does at 1/10 the price”. Well, for that price you’re getting 1/10 of the security.
The legal aspect of the face unlock function is a separate topic. A number of precedents regulating the right of the police to unlock the phone by scanning the suspect’s face have been created in the USA. There are both positive precedents (the permission to perform the face unlock was granted) and negative ones (the permission was not granted or granted illegitimately); as a result, a rather straightforward legal framework has been established, and police officers keep within it.
It is up to you whether to use the face unlock function or not.
Securing the insecure
What can be done if your phone is full of ‘security holes’, or its bootloader is unlocked, or it is a Chinese model reflashed by enterprising vendors? Of course, at this point the actual security is out of the question in this situation, but can you make the thing just barely usable?
If the OEM does not have any updates, but the phone you bought on sale from Amazon bundles one or more malicious programs in the firmware, can you do anything? From my point of view, recycling is the right thing to do. Retail stores are obligated to safely dispose electronic devices; the procedure is safe for the environment and does not cost you a dime. If you want to actually use the thing… oh well, I have no good news for you.
What if your computer is seized
After addressing the security of your smartphone, let us see how the analysis of you computer can affect the security of your mobile devices. If an expert has got access to your computer and you do not use full disk encryption (e.g. with BitLocker), a simple utility and a few mouse clicks will extract all logins and passwords to all your accounts. The passwords can be stored in the database of your favorite browser: Chrome, Mozilla, or Microsoft Edge. If you use a password manager and are considered a suspect, breaking in to the password manager is the first thing they’ll try.
What happens after the passwords are extracted? Depending on your smartphone model, the expert may launch another tool to retrieve all information from your Apple, Google, or Samsung cloud. (For your information: if you use a Samsung phone, be aware that its cloud stores plenty of data even if you had never used it consciously.)
If you use an iPhone, the following info can be extracted from the cloud:
- iOS cloud backups;
- Synchronized data: contacts, notes, calendars, Safari bookmarks, etc.;
- Photos (including recently deleted ones if the iCloud Photo Library option is turned on);
- Call history and browsing history;
- Some payment card data; and
- If the experts know your lock screen passcode or password to your Mac computer, they can get access to your passwords from the iCloud Keychain, Health app data (log of your everyday activities), text messages and iMessages.
Using Android? Google collects more data than Apple; accordingly, the list of retrievable information is longer:
- Backups and application data (by the way, Android stores the call history, SMS, and some authentication tokens in this category);
- Synchronized data: contacts, notes, calendars and more;
- Chrome and some Android passwords (unlike iOS, they have no additional protection);
- Detailed location history for the last few years. Experts would likely be interested in it in the first place;
- Browser and search history;
- Google Fit data; and
- Your Gmail.
The Google cloud analysis often brings more interesting findings than the smartphone analysis because Google collects data from all devices (including computers) that signed in to the Google Account.
If you have a Samsung phone, some information can be retrieved from the Samsung cloud. Most probably, many readers are unaware that Samsung has its own cloud service storing their data, but it does. The following information can be discovered:
- Backups (interestingly, Samsung stores APKs as well);
- Photos (if you had not manually turned off the photo sync);
- Samsung Health data; and
- Backups of Samsung watches or trackers.
How to protect yourself against cloud attacks? The most popular recommendations repeated in numerous articles are, in fact, the most useless ones. You may set a long and complex password, but it will be extracted from the storage embedded into Chrome exactly as quickly as a short and simple one. You may enable two-factor authentication (still, please do!), but an expert may easily bypass it by taking the SIM card out of your phone and using it to get the one-time password. Furthermore, if the browser is logged in to your Google Account, it is possible to retrieve cookies with authentication tokens. In that case, neither a one-time passcode, nor the password, and nor even the login are required. This does not mean that two-factor authentication is useless; it is quite effective against remote hacking attacks. However, you cannot rely on these precautions if your computer is analyzed by skilled experts.
Only multilayer security can help.
First, ensure the physical security of your computer by turning on the system disk encryption with BitLocker. By the way, make sure that BitLocker Recovery Key has not ‘leaked’ to OneDrive (you can check this here) and was not saved in Active Directory.
Passwords to cloud accounts constitute the next protection layer. Use unique passwords to Google, Apple, and Samsung cloud services; these passwords must not resemble the ones saved in the browser. Run your favorite, not-so-favorite, and never-loved browsers and make sure that they store none of the above passwords. If you use Chrome, log out of the Google Account, delete the browser cache, and close all windows. Now your are protected from cloud attacks for some time (until the next signing in to the Google Account).
This precaution will make the everyday use of your machine slightly less convenient, but will significantly raise the security level.
Lockdown
iPhone users incur an additional risk: the lockdown files (also known as iTunes pairing records). Such files are created when an iPhone or iPad is connected to a computer with iTunes; they are required to synchronize the device with the computer via iTunes without entering the screen lock passcode every time. On the one hand, the pairing record is a convenience. On the other hand, it is a vulnerability. For instance, ElcomSoft tools make it possible to use lockdown files to back up the phone even if its screen is locked (but the phone was unlocked at least once since the last boot-up), while GrayKey is able to make a full file system image.
How to protect yourself? Of course, you can delete lockdown files from your computer. Windows stores them in the folder C:\Users\<username>\AppData\Roaming\Apple Computer\MobileSync\Backup (if you have installed iTunes from the Apple website) or C:\Users\<username>\Apple\MobileSync\Backup (if you use an iTunes version from Microsoft Store).
However, you cannot delete these records on the iPhone; you can only reset the list of all trusted computers by using Settings → General → Reset → Reset Location & Privacy. By the way, to do so, you will have to enter the screen lock passcode. Another way to remove the trusted records is to Reset Network Settings. Please note that Resetting All Settings does not affect the trusted records in any way (although resets the backup password).
How real are the risks associated with the computer analysis? According to our sources in the police, computers are analyzed pretty rarely. Experts routinely encounter the following obstacles:
- Legal issues: the warrant permits the personal search and evidence analysis but does not permit the residence search;
- Time limits: experts are very busy. In routine cases, they cannot spend a month, two weeks, or even a few days analyzing all of the available evidence;
- The BitLocker password is very strong. Brute-force attacks are useless unless the experts manage to extract the encryption key using, for instance, the FireWire Attack;
- Shallow analysis: due to tight time frames, the hard drive is checked only for specific file types (photos and videos, correspondence, messenger databases, etc.)
- Even if the full analysis has been performed, the browser cache often does not contain the required passwords; and
- Even if the required passwords are available, the suspect’s cloud may contain no backups (or no recent backups). Such situations are typical for iOS: if the default settings are left unchanged, the mere 5 GB of free cloud space get packed with synchronized photos in no time, and no space remains available for backups. Android users will likely have some free space left because standard-quality photos do not count toward the generous quote of 15 GB allocated to them, and backups are quota exempt.
Conclusions
We overviewed and discussed the potential risks and security settings far beyond the scope of standard recommendations. Setting a screen lock passcode and enabling two-factor authentication are a must, but there are far more things to configure if you want anything barely resembling a secure device. We hope you now have a better understanding of the threats associated with the many settings in your iPhone or Android device.
