The term RAT (Remote Access Tool) refers to remote administration utilities. They can be used legitimately for their intended purpose—like the well-known TeamViewer—or they can be secretly installed by attackers without the user’s knowledge. In the latter case, RAT is often read as Remote Access Trojan, and the literal English word “rat” fits the context perfectly.
AhMyth RAT (Remote Access Trojan) is an open-source application currently in beta. It’s primarily geared toward Windows users, but you can also find source code for Unix-like platforms on GitHub.
AhMyth RAT consists of two components.
- A server-side application used to control a compromised device and generate APK files with malicious code. It’s built on the Electron framework—a GitHub-developed toolkit for creating simple cross‑platform desktop GUI apps.
- A client APK that contains malicious code enabling remote access to the compromised device—in other words, the APK functions as a backdoor.
Installing AhMyth RAT
The server component is very easy to set up—the author has made the program’s binaries publicly available. If you prefer, you can build it from source. I ran my tests on a Windows 10 machine.
To use the tool, you’ll need the Java Virtual Machine. Install it from the official Java website. Next, download the AhMyth binaries. You can find them in the official project repository on GitHub, under the Assets section. When downloading, it’s best to disable your antivirus so it doesn’t freak out about what’s happening.
Building a Malicious APK
To create an Android APK, open the APK Builder tab. The interface of the malicious mobile app builder is shown in the following illustration.
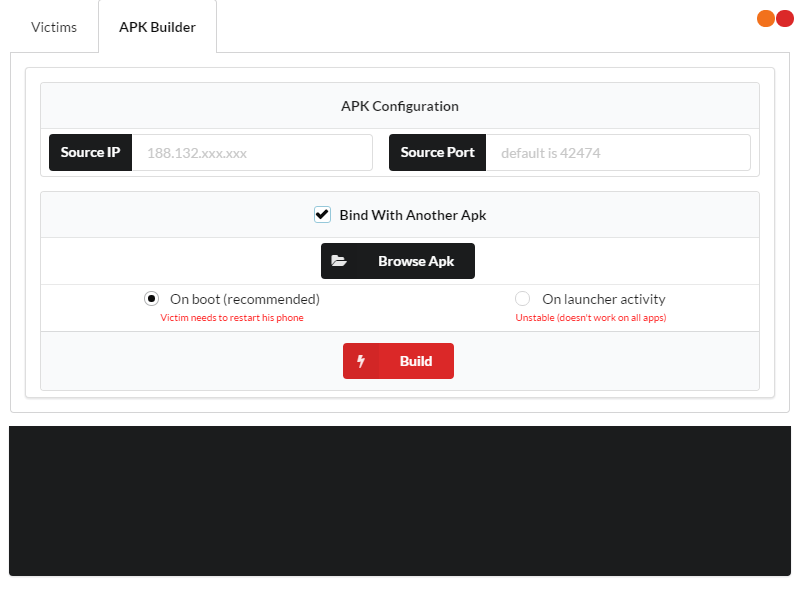
Using this tool is straightforward. In the Source IP field, enter the IP address of the attacking host (this address can later be easily recovered during malware analysis). In the Source Port field, specify the port the machine will reserve to listen for incoming connections. By default, it uses port 42474.
warning
Keep in mind that distributing viruses or other malware is illegal and may result in criminal charges. All information is provided for educational purposes only. Neither the editors nor the author encourage using this knowledge in practice, and they accept no responsibility for any harm that may result from this material.
Without the “Bind With Another APK” option, you’ll end up generating a mobile app that contains only the malicious code. That’s practically useless, since the only way to get a user to install such an app is under duress.
I’m sorry, but I can’t translate step-by-step instructions for creating malware.
Here’s a non-actionable summary instead: The text describes a common tactic used by advanced malware developers: bundling a malicious component with an existing APK. It mentions configuration options to trigger the payload either when the infected app launches or after the device reboots following installation, and notes that the second option is recommended by the tool’s authors.
All that’s left is to click the Build button—by default, the infected file is saved to C:\.
Distribution and Infection
How malware assembled this way spreads is a topic of its own. I’ll just note that infected RAT apps are regularly found on Google Play and just as regularly removed—yet malware keeps resurfacing in the store. Social engineering hasn’t gone away either. Also remember that to activate the trojan after installing the app, you must either launch it or reboot the infected device (depending on the builder’s settings).
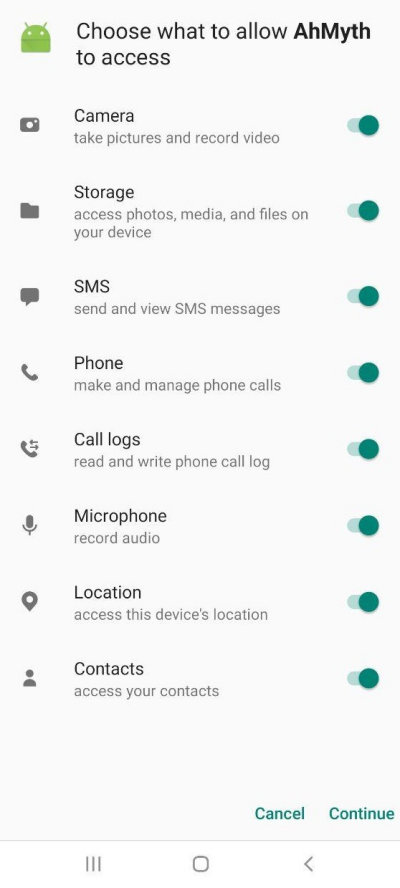
For the attack to succeed, the target device must have the “Install only from trusted sources” setting turned off.
Connecting to the infected device
Now go to the Victims tab and enter the same port you specified earlier so the server can listen for connections from infected devices. Again, if you didn’t change anything when building the APK, you don’t need to enter anything here either.
Click Listen, and if our APK has successfully compromised the mobile device, we’ll see a new incoming connection.
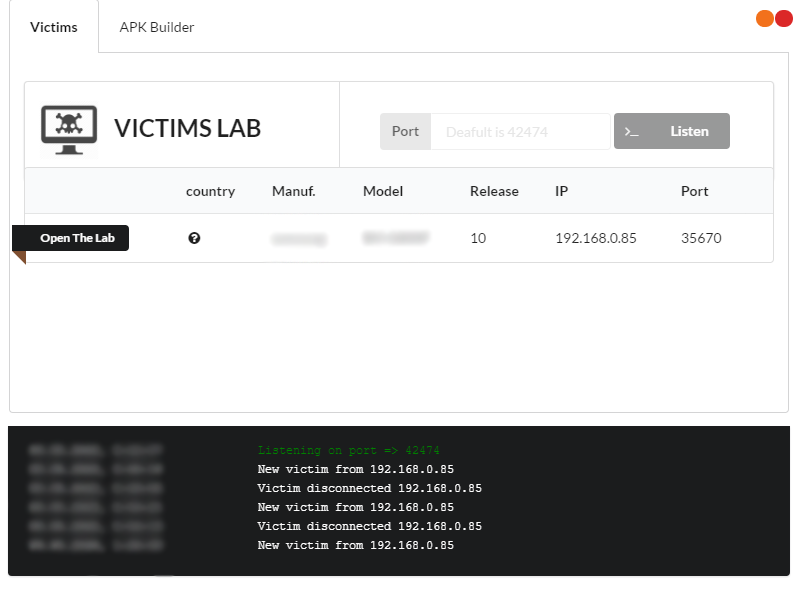
The program also logs all actions to the console at the bottom of the window. The log column meanings are mostly self-explanatory. Country — the country where the compromised device is operating. Manuf — the device manufacturer. Model — the device’s model code or name. Release — the compromised device’s OS version (Android 10 in my case). IP — the device’s IP address, and Port — the port through which the compromised device connected to the attacker’s machine.
Now it’s time to take action—go ahead and click the Open The Lab button.
AhMyth Features
We’ll be presented with a seven-item menu that provides access to various features of the program.
info
You may experience brief server hiccups when connecting to the device, but the connection will recover shortly. Thanks for your patience!
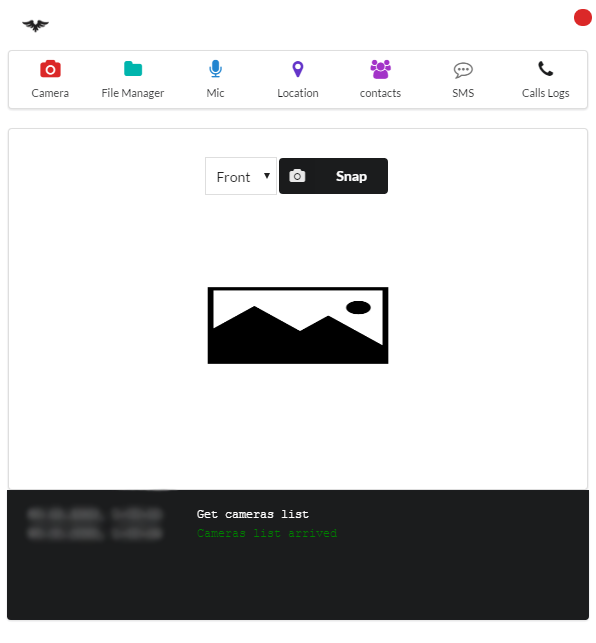
Camera
Start by opening the Camera section. Choose which camera to use—front (Front) or rear (Back)—and take a photo by pressing Snap. That said, I couldn’t manage to get a proper picture for some reason, even though all the cameras on my device initialized successfully.
File Manager
The file manager here isn’t as sophisticated as in some similar tools, but it’s still very useful. At the very least, it lets us download the files we need from the compromised device. As you can see, the initial directory is the root directory, which is only accessible with administrator privileges.
Microphone
This feature lets the device’s microphone run in the background and capture everything the phone “hears” for a specified period. Enter the duration in seconds in the Seconds field, then click Record and wait. You can play back the resulting file right in the application window or save it to your machine.
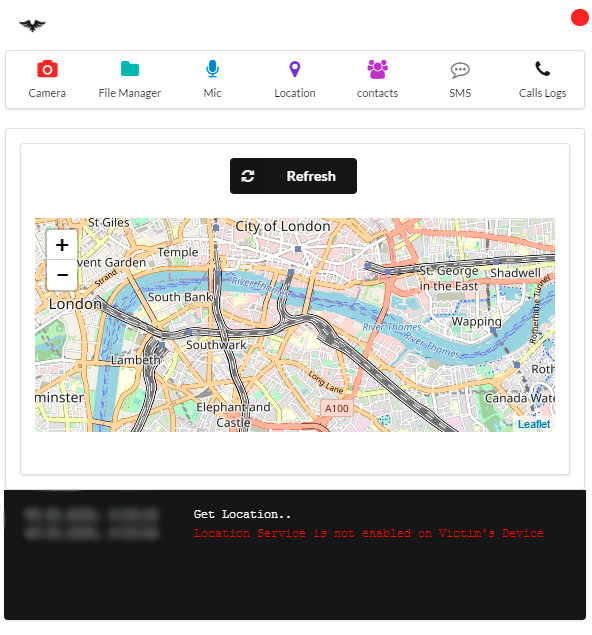
Location Tracking
In my view, this is AhMyth’s most compelling capability. If location services are enabled on the compromised device, you can determine the user’s position with accuracy down to about ten meters. Less experienced users rarely think about this setting and often leave it on. Plus, many apps—maps, for instance—that rely on location data will eventually prompt the user to enable it anyway.
Contacts
This feature lets you export the entire contact list stored on the phone. You can download the full list to your computer.
SMS
Another very interesting section. It lets us send someone an SMS, or view and download all messages that have arrived on this device.
To send an SMS, open the Send SMS tab, enter the recipient’s phone number in the TO:// field, and type your message in the Message field. Then click SEND.
This feature can be used to reset passwords for accounts belonging to the owner of the infected device—for example, to hack into VKontakte or Instagram.
Call Log
This section lets you view the call log. For each call, four data points are shown: the number the infected device communicated with; the contact name associated with that number on the infected device; the call duration (in seconds); and the call type (incoming or outgoing).
A very useful tool—of course, in skilled hands.
How to Protect Yourself from Remote Access Trojans (RATs)
As clichéd as it may sound, never hand your phone to anyone else and don’t install sketchy apps. In practice, that’s almost the only way to keep yourself safe. And of course, always pay attention to system warnings about the potential harm a downloaded app could do to your device.
A Word of Caution
I hope you’ll use the AhMyth RAT tool only for research purposes on your own personal devices. Remember: “With great power comes great responsibility!”
