Despite the fact that Russia (surprise!) is not among the leaders in computer infectioning by this method (three leaders are traditionally USA, Germany and the UK), we suppose it will be still useful to find out what makes many users in different corners of the world click on attachments in messages from unknown senders. Off we go!
Angry letter
Sender’s address (‘From’ field)
The first thing that the malefactor shall take care of when sending malicious spam is in whose name the mailout is conducted. Messages from individuals (except for mailout from the hacked mail account to address book recipients) are not effective enough, that’s why different companies, organizations and even judicial and governmental authorities are taken advantage of.
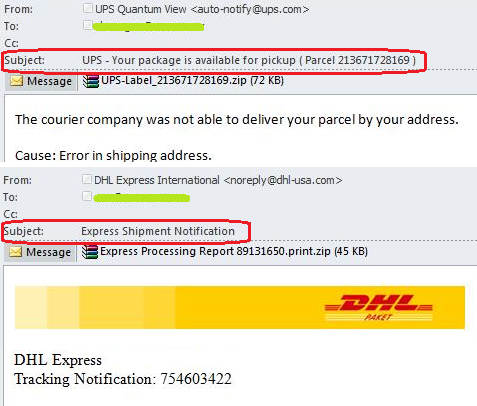
Lately, international delivery services (DHL, FedEx, United Parcel Service (UPS) or TNT) are especially popular. If you remember, Cryptolocker was spread in this way under the guise of a FedEx or UPS delivery report.
Malefactors solve the problem of sender’s address in ‘From:’ field it in several ways:
- hack the email of the required company and send messages from there (which is extremely complicated to realize and hardly feasible especially in case of a big and serious company);
- register a domain name, which is very similar to the name of the required company;
- use free mail service by registering there something like manager.fedex@mail.ru, admin.vkontakte@gmail.com or police.mvd@ya.ru;
- replace the real sender’s address (there are several ways to do so, starting from using different programs and Internet services down to scripts for sending messages).

Subject of the message (‘Subject’ field)
Subject of the message shall be attractive for the recipient and motivate him to open the message. Naturally, it shall correspond to the line of business of the organization in whose name the message is sent.
If the mailout is performed, for example, in the name of a delivery service, then the most popular message subjects will be:
- everything connected with sending, tracking or delivery of mail (shipment notifications, delivery status, shipment confirmation, shipment documentation, delivery information);
- order information and invoice;
- message and account notification (account creation and confirmation, receipt of new messages).
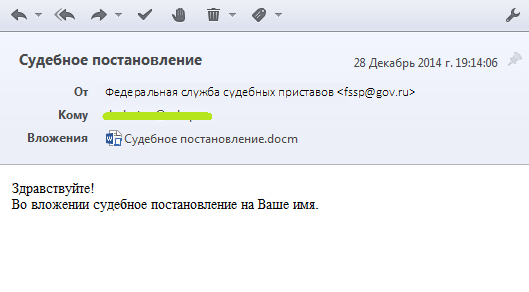
Mailouts from different state authorities are more typical for our country, and in this case malefactors choose corresponding topics e.g. ‘Judicial decree’ (in the name of court bailiff federal agency) or ‘Ticket for payment of fine for traffic violation’ (you may guess yourself in whose name such message is sent).
Message body and arrangement
To make messages credible, the malefactors actively use logos of companies under whose name they are acting, their contact information, links to official web-pages and other information.
In order not only to convince the recipient in message credibility, but give him/her also an impulse to open the attachment, mail delivery error notifications (wrong recipient address, absence of recipient, etc.), request to take actions with indication of possible sanctions for failure to perform or a phrase with indication of what is contained in the attachment (for example, ‘reconciliation report’, ‘consignment note’ or ‘invoice’) may be used.
Besides, different standard word-combinations typical for official mailout are commonly used (something like ‘please do not reply to this email’ or ‘this is automatically generated email’).
Types of malicious attachments
Executable file
Despite the fact that the majority of mail servers have not been letting pass executable files for a long time already, such type of malicious attachments still can be encountered. As a rule, such file is camouflaged as some harmless document (doc or PDF) or an image.
At that, the file is linked with a corresponding icon and gets a name, e.g. ‘consignment.pdf.exe’ (at that ‘exe’ extension often is separated from the file name with many spaces to make it less obvious).
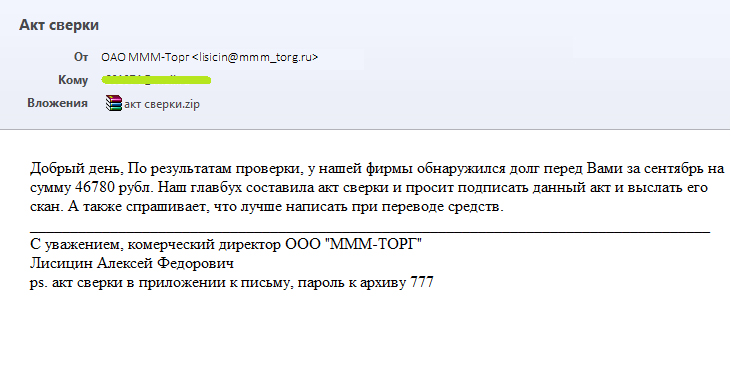
Attachments with password protected archive file
A password protected archive file allows bypassing all antivirus checks on mail servers, firewalls and security scanners. A malicious file itself, as in the first case, is camouflaged as something harmless.
The most important here is to motivate the recipient to enter the password, indicated in the message, unzip the attachment and open it.
Attachment as a document with exploit or malicious VBA-script
Such message can pass the prohibition against transfer of executable files, and in many cases also antivirus check on mail servers (especially, if exploit is fresh).
Security vulnerabilities for Adobe Acrobat Reader (CVE-2013-0640,
CVE-2012-0775), Adobe Flash Player (CVE-2012-1535) or MS Office (CVE-2012-0158,
CVE-2011-1269, CVE-2010-3333, CVE-2009-3129) are used most frequently.
Except for exploits, MS Office docs with malicious macros based on VBA can be used as malicious attachments (yeah, there are still people who do not prohibit execution of macros in Word and antiviruses not always react to such scripts).


Embedded HTML-documents
A message contains an HTML-document attachment with a code which performs a drive-by attack. In many cases this method allows bypassing antivirus filters of mail servers, as well as prohibitions, which blocks passing iframe.
Hyperlinks in message body
Such messages normally do not contain attachments, and message body contains several links to the same resource, which either contains exploit bundle or redirects to other malicious resource. All these links are camouflaged as links to decent and safe websites or plain text.
Conclusion
In spite of everything, spamming is still a very efficient way of spreading malicious code. It may be supposed that with decrease of software and hardware security vulnerabilities, this method will be used more and more often, assuming increasingly sophisticated forms in order to take advantage of the most vulnerable part of any informational system — its user.