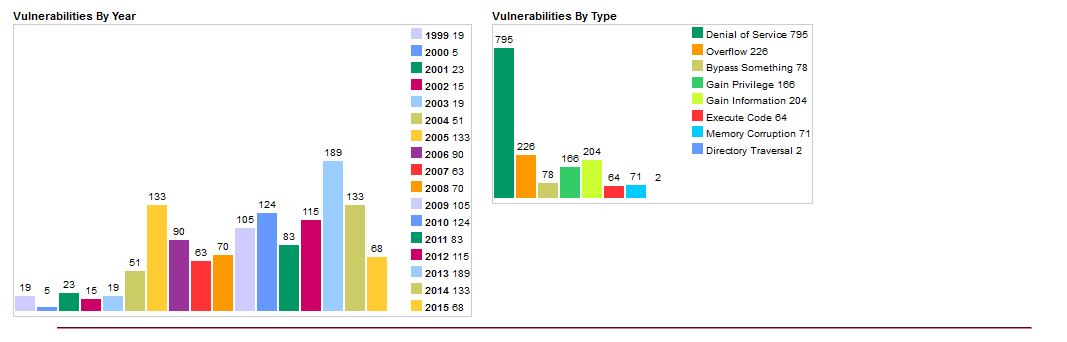
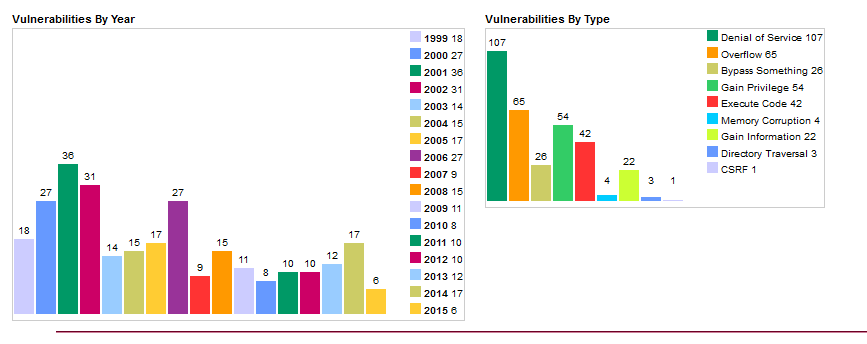
According to cvedetails.com, more than 1,305 vulnerabilities have been found in the Linux core since 1999. Sixty-eight of these were in 2015. Most of them don't cause many problems (they are marked as Local and Low), and some may cause problems only if they are attached to certain applications or OS settings. In reality these numbers are not that big, but the core is not the entire OS. There are also vulnerabilities found in GNU Coreutils, Binutils, glibs and, of course, user applications. Let's take a look at the most interesting of the bunch.
[section label=”Vulnerabilities in the Linux core” anchor=”vulner”]
Vulnerabilities in the Linux core
OS: Linux
Level: Medium, Low
Vector: Remote
CVE: CVE-2015-3331, CVE-2015-4001, CVE-2015-4002, CVE-2015-4003
Exploit: concept, https://lkml.org/lkml/2015/5/13/740, https://lkml.org/lkml/2015/5/13/744
The vulnerability found in the "__driver_rfc4106_decrypt" function of the "arch/x86/crypto/aesni-intel_glue." file in the Linux core in June is related to the fact that use of RFC4106 for x86 processors that support the AES AES-NI command system extension (suggested by Intel, Intel Advanced Encryption Standard Instructions), in certain cases calculates buffer addresses incorrectly. If IPsec tunnel is set to use this mode (AES – CONFIG_CRYPTO_AES_NI_INTEL algorithm), the vulnerability may lead to damaged memory content, emergency shutdowns and, potentially, remote execution of CryptoAPI code. The most notably interesting thing is that this problem might appear by itself in fully legal traffic without any external intrusion. As of the moment of publication, this problem has been removed.
Five vulnerabilities have been identified in the "Linux 4.0.5 ozwpan" driver, which has an experimental status. Four of these vulnerabilities allow for the launch of a DoS attack by shutting down the core sending specially executed packets. This problem is connected to buffer overflow due to the incorrect processing of sign integers, where calculations between "required_size" and "offset" in "memcpy" returned a negative figure, and as a result the data was copied in heap. It is found in the "oz_hcd_get_desc_cnf" function in "drivers/staging/ozwpan/ozhcd.c" and in the "oz_usb_rx" and "oz_usb_handle_ep_data" functions of the "drivers/staging/ozwpan/ozusbsvc1.c" file. In other vulnerabilities there are possible divisions by 0, along with system looping and the possibility of reading from areas beyond the border of the allocated buffer.
The ozwpan driver, one of the new editions to Linux, can be linked to existing wireless devices compatible with Ozmo Devices (Wi-Fi Direct) technology. It provides for the use of the USB host controller, but the tricky thing is that instead of a physical connection, the periphery interacts via Wi-Fi. The driver accepts network packets of the "0x892e" (ethertype) type, then it deconstructs them and transfers them to different parts of the USB functionality. It is still rarely used, so it can be disabled by unloading the "ozwpan.ko" module.
[section label=”Linux Ubuntu” anchor=”linux-“]
Linux Ubuntu
OS: Linux Ubuntu 12.04-15.04 (core before June 15, 2015)
Level: Critical
Vector: Local
CVE: CVE-2015-1328
Exploit: https://www.exploit-db.com/exploits/37292/
Critical vulnerability in the OverlayFS file system lets users get root rights in Ubuntu systems, where OverlayFS partition mounting by unprivileged users is allowed. The default settings required for vulnerability exploitation are used in all Ubuntu 12.04-15.04 legs. OverlayFS itself appeared in the Linux core rather recently, starting from "3.18-rc2" (2014), this is the SUSE development to replace UnionFS and AUFS. OverlayFS allows for the creation of a virtual multi-layer file system that connects several parts of other file systems. FS is created from the lower and upper layers, each of which is attached to different catalogs. The lower layer is only used for the reading of any Linux-supported FS, including network ones. The upper layer is usually available for recording and overlays the lower layer data if the files are duplicated.
It is used in Live distributives, container virtualization systems and for the organization of containers operations for several desktop applications. User namespaces allow for the creation of container-specific sets of user and group IDs in containers. The vulnerability is caused by incorrect scans of access rights during the creation of new files in the lower FS catalog. If the core is assembled with the "CONFIG_USER_NS=y" parameter (inclusion of user namespaces), and an "FS_USERNS_MOUNT" flag is indicated during mounting, OverlayFS may be mounted by a regular user in another namespace, including where root rights operations are permitted. In this case, operations with root rights files executed in such namespaces get the same privileges as during the execution of actions with the lower-lying FS. It is therefore possible to mount any FS partition and view or modify any file or catalog.
From the moment of publication, a core update with the corrected OverlayFS module from Ubuntu has become available. So, if the system is updated, there shouldn't be any problems. When updating is impossible, a temporary measure could be to stop using OverlayFS by deleting the "overlayfs.ko" module.
[section label=”Vulnerabilities in main applications” anchor=”vulner”]
Vulnerabilities in main applications
OS: Linux
Level: Critical
Vector: Local, Remote
CVE: CVE-2015-0235
Exploit: https://www.qualys.com/research/security-advisories/exim_ghost_bof.rb
A dangerous vulnerability in the standard GNU glibc library, which is a main part of Linux OS, and in certain versions of Oracle Communications Applications and Oracle Pillar Axiom, identified during a code audit by hackers from Qualys. It has since received the code name GHOST. This vulnerability is related to buffer overflow inside the "__nss_hostname_digits_dots()" function, which is used to acquire node names by such "glibc" functions as "gethostbyname()" and "gethostbyname2()" (hence the name GetHOST). To exploit the vulnerability, one needs to cause buffer overflow with an inadmissible host name argument in an application that executes name permissions via DNS. Theoretically, this vulnerability can be exploited in any application that uses the network to some extent. It can be activated locally or remotely and lets random code be executed.
The most interesting thing is that the bug was corrected back in May 2013 and a patch was presented between "glibc" releases 2.17 and 2.18, but the problem was not classified as a security patch, so they did not pay any attention to it. As a result, many distributives became vulnerable. From the start it was reported that the very first vulnerable version was version 2.2 (November 10, 2000), but it might actually stretch all the way back to version 2.0. RHEL/CentOS 5.x-7.x, Debian 7 and Ubuntu 12.04 LTS were also exposed to vulnerabilities, among others. Corrections for these are now available. Hackers themselves offered a utility that explains the nature of these vulnerabilities and helps users check their systems. Everything is fine in Ubuntu 12.04.4 LTS:
[xakepcut]
$ wget https://goo.gl/RuunlE
$ gcc gistfile1.c -o CVE-2015-0235
$ ./CVE-2015-0235
not vulnerable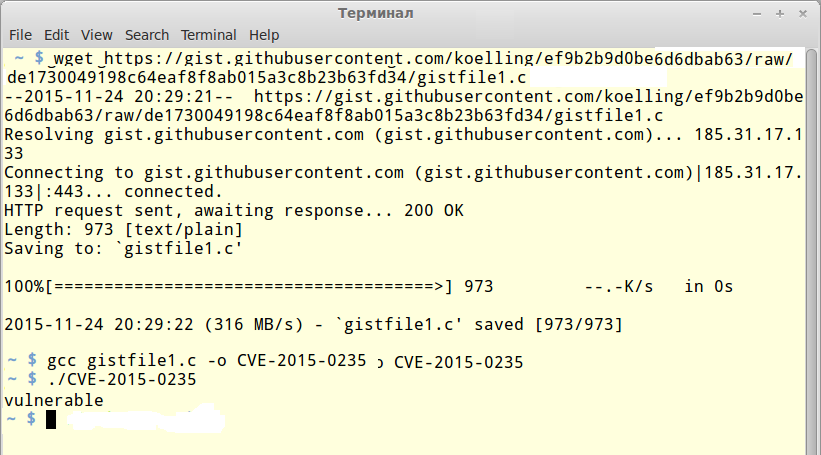
A module for Metasploit was released almost instantly that allows remote execution of code on x86 and x86_64 Linux with a working Exim mailing server (with the activated "helo_try_verify_hosts" or "helo_verify_hosts" parameter). Other uses then appeared for it, for instance the [Metasploit] module (http://goo.gl/SuXP2I) to scan blogs in WordPress.
A bit later in 2015, three other vulnerabilities were discovered in GNU glibc that lets remote users perform a DoS attack or rewrite memory cells beyond the stack: CVE-2015-1472, CVE-2015-1473, CVE-2015-1781.
OS: Linux (GNU Coreutils)
Level: Low
Vector: Local, Remote
CVE: CVE-2014-9471
Exploit: no
GNU Coreutils is one of the main "*nix packets that includes pretty much all the basic utilities (cat, ls, rm, date…). The problem was found in "date." A bug in the "parse_datetime" function allows for a remote user who doesn't have an account in the system to create a "denial of service," and possibly execute a random code by using a specially formulated date string via "timezone." The vulnerability looks like this:
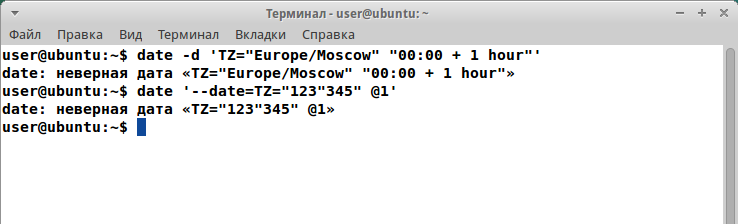
$ touch '--date=TZ="123"345" @1'
Segmentation fault
$ date -d 'TZ="Europe/Moscow" "00:00 + 1 hour"'
Segmentation fault
$ date '--date=TZ="123"345" @1'
*** Error in `date': free(): invalid pointer: 0xbfc11414 ***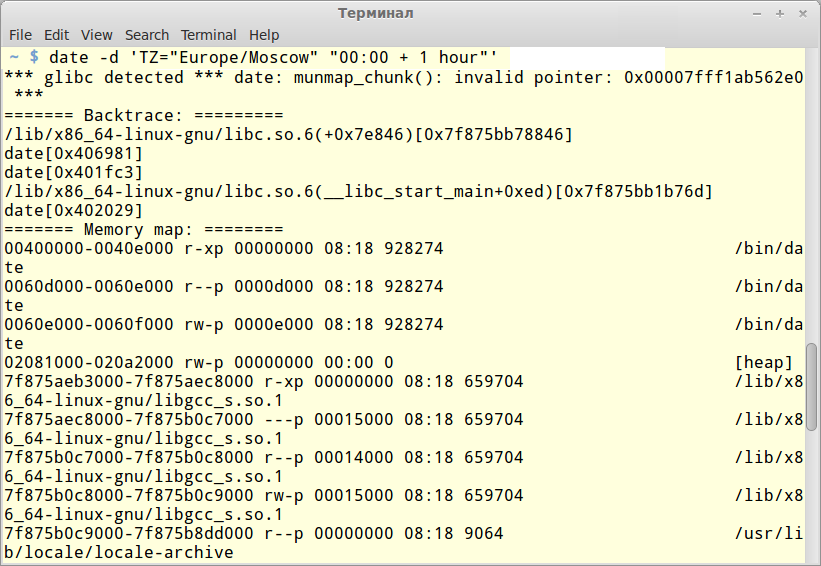
If there is no vulnerability, we get a message about an incorrect date format. Almost all Linux distributives developers have reported on vulnerabilities already. The update is now available.
OS: Linux (grep 2.19-2.21)
Level: Low
Vector: Local
CVE: CVE-2015-1345
Exploit: no
Vulnerabilities in the "grep" utility (used for searching text based on template), are rarely found. However, this utility is often activated by other software applications, including system ones, which is why the presence of vulnerabilities is much more problematic than it first seems. The error in the "bmexec_trans" function in "kwset.c" may lead to the reading of uninitialized data from the area beyond the allocated buffer or to application failure. This might be used by a hacker who could create a special data set and send it to the application entrance using "grep -F." The updates are now available. There are no exploits that use the vulnerability or module to Metasploit.
[section label=”Vulnerability in FreeBSD” anchor=”vulner”]
Vulnerability in FreeBSD
OS: FreeBSD
Level: Low
Vector: Local, Remote
CVE: CVE-2014-0998, CVE-2014-8612, CVE-2014-8613
Exploit: https://www.exploit-db.com/exploits/35938/
There are much fewer vulnerabilities found in the CVE database in 2015. Just six, to be precise. Three vulnerabilities were found at once in FreeBSD 8.4-10.1 at the end of January 2015 by researchers from the Core Exploit Writers Team. CVE-2014-0998 is related to the use of the VT (Newcons) console driver, which provides several virtual terminals activated by the "kern.vty=vt" parameter in /boot/loader.conf.
CVE-2014-8612 became apparent when using the SCTP protocol and is caused by a bug during the scan of the SCTP stream ID that uses SCTP sockets (local port 4444). It is caused by memory overflow in the "sctp_setopt() (sys/netinet/sctp_userreq.c)" function. This lets a local, unprivileged user have the ability to write or read 16 bits of data of the memory core and increase their privileges in the system, expose confidential data or disrupt the system.
CVE-2014-8613 initiates dereferencing of the null indicator during the processing of an SCTP packet received externally while installing the SCTP_SS_VALUE option of SCTP socket. In contrast to the previous ones, CVE-2014-8613 can be used to bring about core failure remotely by sending specially executed packets. It is possible to protect oneself in FreeBSD 10.1 by setting "net.inet.sctp.reconfig_enable" to 0, thereby prohibiting the processing of RE_CONFIG blocks. Or users can simply prohibit the applications (browsers, email clients, etc.) from using the SCTP connection. But the developers have actually released an update as of the moment of publication.
[section label=”Vulnerability in OpenSSL” anchor=”vulner”]
Vulnerability in OpenSSL
OS: OpenSSL
Level: Remote
Vector: Local
CVE: CVE-2015-1793
Exploit: no
A critical "Heartbleed" vulnerability was found in 2014 in OpenSSL, a widely used cryptographic packet for SSL/TLS operation. The incident caused massive criticism of the code quality back when it happened leading to alternatives such as LibreSSL, but it also spurred the developers themselves to get down to business.
The critical vulnerability was identified by Adam Langley from Google and David Benjamin from BoringSSL. The changes introduced in versions 1.0.1n and 1.0.2b of OpenSSL led to OpenSSL trying to find an alternative certificate verification chain, in case the first attempt to construct a trust confirmation chain failed. They bypass the certificate verification procedure and establish a confirmed connection using the false certificate. In other words, they quietly lure users to fake websites or email servers or use any MITM attack where the certificate is used.
After the vulnerability was detected, the developers released versions 1.0.1p and 1.0.2d where the problem was rectified on July 9. This vulnerability is absent in versions 0.9.8 and 1.0.0.
[panel]
Linux.Encoder
The end of fall was marked by the appearance of a whole range of encryption viruses: first Linux.Encoder.0, followed by Linux.Encoder.1 and Linux.Encoder.2 modifications, which infected more than 2,500 websites. According to antivirus companies, Linux and FreeBSD servers are exposed to attacks when interacting with websites that use various CMS, including WordPress, Magento CMS, Joomla, and others. Hackers use an unidentified vulnerability. Then a shell script (error.php file) was placed, which was used for any further actions (through a browser). In particular, the Linux.Encoder trojan was launched, which determined the OS architecture and launched an encoder.
The encoder was launched with web-server rights (Ubuntu : www-data), which is enough to encrypt the file in the catalog where files and CMS components are stored. The encrypted files get the ".encrypted" extension. The encoder also tries to browse other OS catalogs; if the rights are configured incorrectly, it could go well beyond the borders of the website. Then a "README_FOR_DECRYPT.txt" file containing the file decryption instructions and the hacker's demands was saved in the catalog. Antivirus companies have already provided utilities for catalog decryption. For instance, Bitdefender set. However, it should be remembered that no file decryption utilities remove the shell code, so the problems might repeat themselves.
Considering the fact that many users who develop or experiment with website administration often install a web server on a home PC, security measures should be taken: external access should be prohibited, software should be updated, and experiments should be conducted on VMs. Not to mention that the idea itself may be used in the future to attack home systems.
[/panel]
[section label=”Conclusion” anchor=”conclu”]
Conclusion
There is no actual sophisticated software free of all bugs, so we have to put up with the fact that vulnerabilities will always be found. However, not all of them present serious problems. Users can make their systems safer by taking the following simple steps: uninstall unused software, keep track of new vulnerabilities, always install security updates, set up a firewall, and install an antivirus. Moreover, never forget about special technologies such as SELinux, which are quite effective if a daemon or a user application is compromised.
