Numerous times you used to help your friends and people when their PCs fell to onslaught of malware. So did we. But we got pretty sick and tired of all that and pulled out a trump card by instead compiling a full guide that you can just hand off to the injured party and thus guarantee your non-involvement. Take it and put it to good use!
Tip one. What can we do with the help of Live CD
using emergency repair discs from antivirus companies
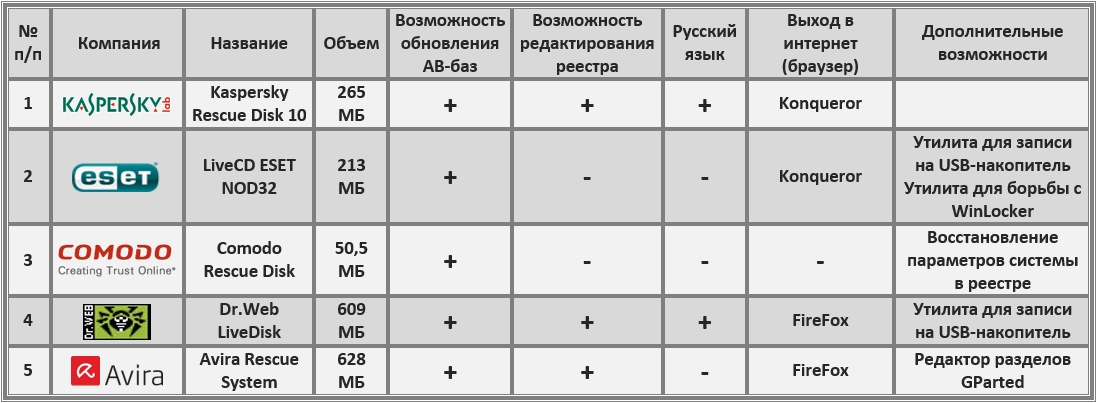
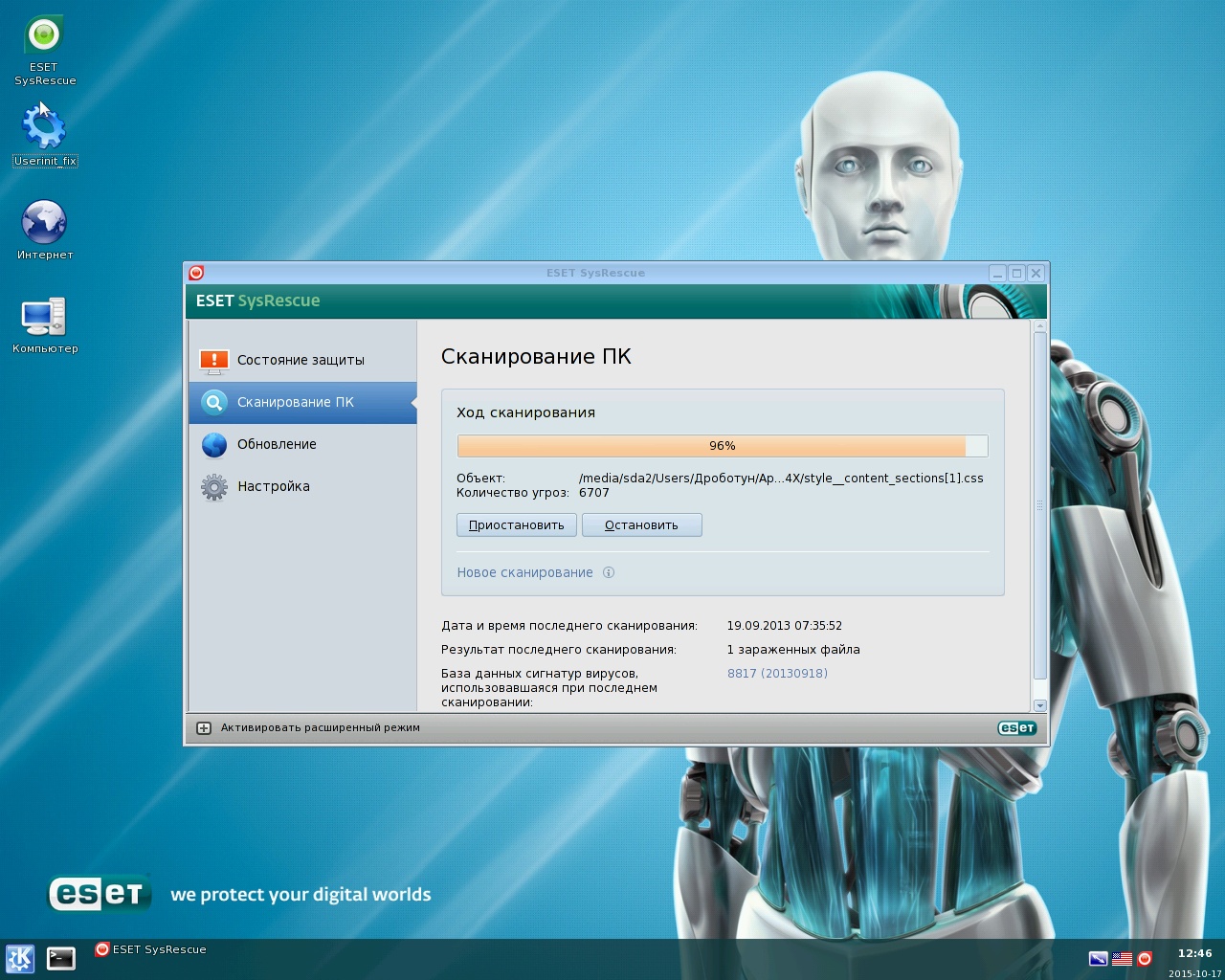
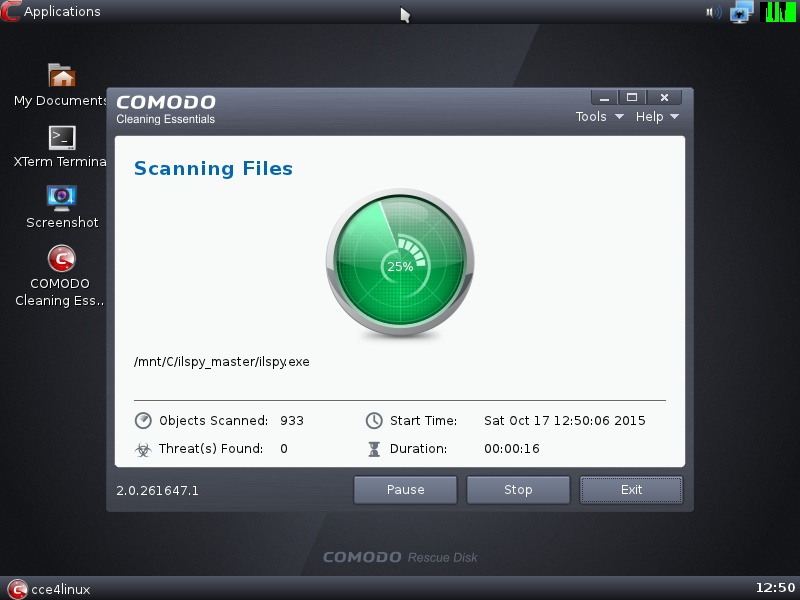
Antivirus Live CDs can be used to recover your system once it is rendered unusable by computer viruses. Almost every antivirus company offers this product for free.
The CD is most often a Linux-based boot drive containing scanning and disinfecting utilities along with Linux components. These Live CDs also typically contain additional software tools (registry editing and recovery utilities, disk partition editing utilities, network configuration utilities, etc.).
See chart 1 for a brief description of Live CDs from the most popular Russian antivirus providers.

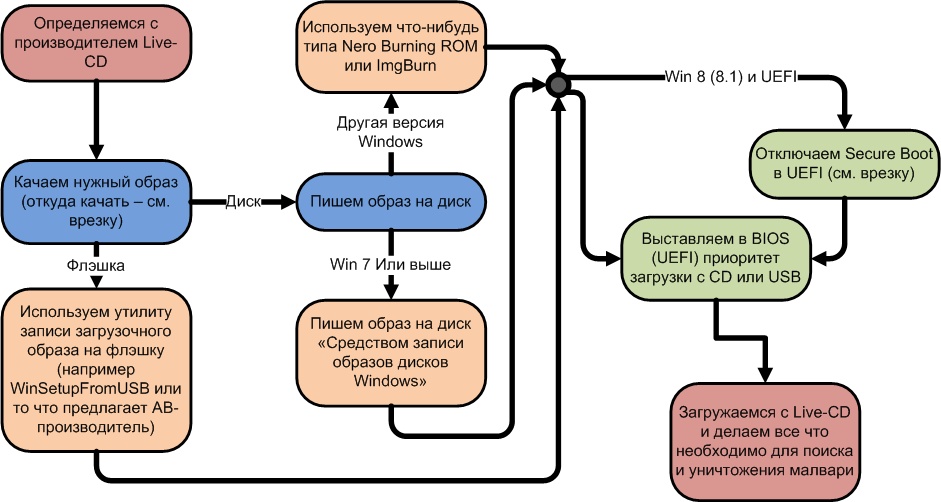
The selected Live CD image can be written either on a disc (CD or DVD) or on a memory card. If you're using Windows 7, the image can be written using the bundled software. You just have to right-click the icon, choose "Open with", then "Windows disc image burner". Older versions required special software to write disc images, e.g. Nero Burning ROM or its free counterparts like Img Burn or Ashampoo Burning Studio.
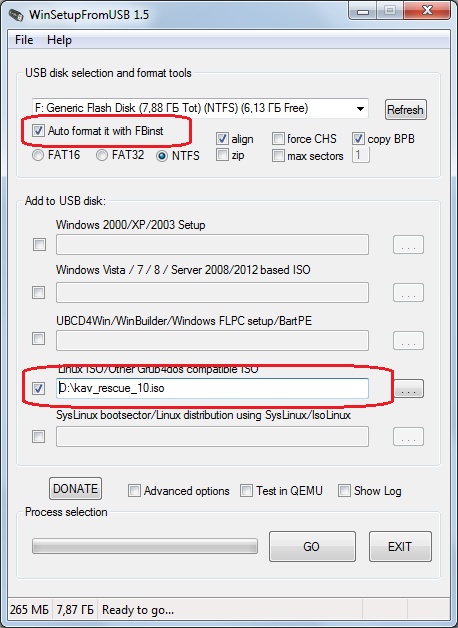
To write a boot image to a memory card you can use the special utilities supplied by antivirus software providers along with Live CD or WinSetupFromUSB. Select the correct USB memory card and the image file, check "Auto format it with FBinst" and then start the process.
If your PC or laptop is a little behind the times and didn't come pre-installed with Win 8 or higher, then system booting using a boot drive is as easy as 1-2-3. Enter BIOS setup (boot the PC and when the firmware starts running press "Del" or "F2"), change the boot source priority to CD-ROM or USB-memory card (except not all PCs support booting from USB) and wait for it to boot up.
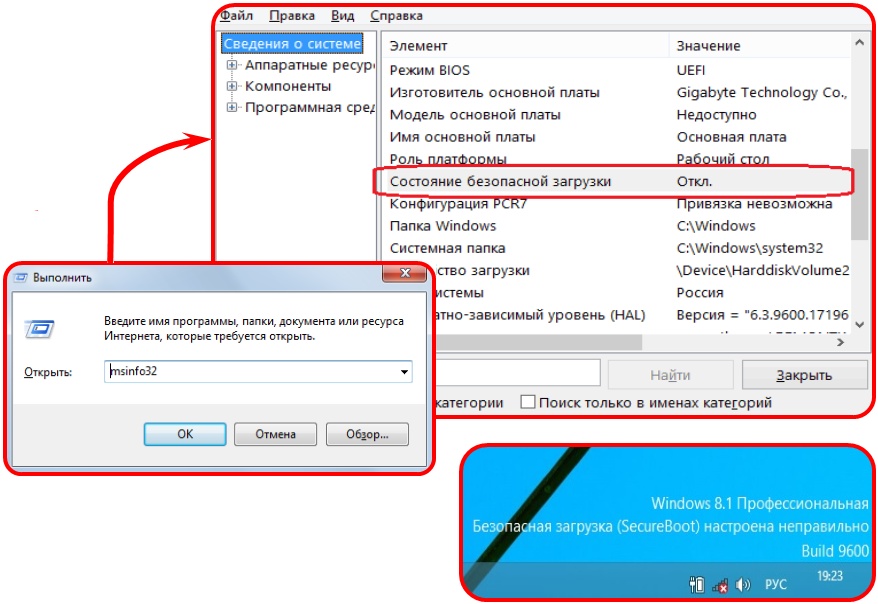
If your PC has Win 8 or higher, you might face certain problems in UEFI mode (in the vast majority of cases). You might find it difficult to enter BIOS setup, and you will have to disable Secure Boot in order to boot from Live CD.
[panel]
What is Secure Boot
Secure Boot is a UEFI option meant to protect PCs from bootkits, low-level exploits and rootkits. The UEFI boot manager in Secure Boot mode will only run code verified in its own database by a digital certificate.
You can use msinfo32.exe to find out the status of this option. Or rather you can simply read the note in the bottom right corner of the display:
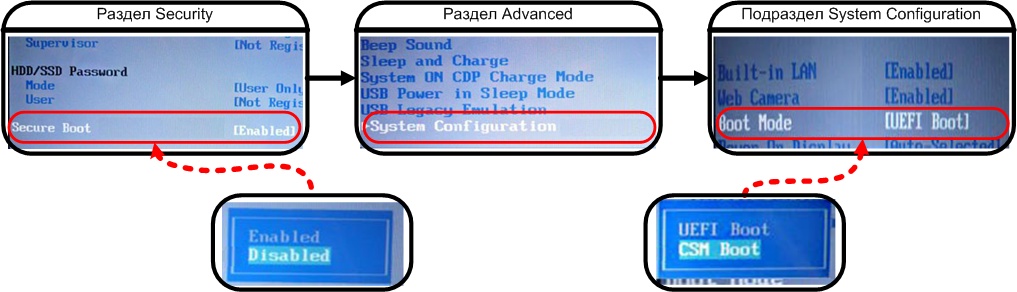
How to disable Secure Boot
This all depends on your brand of laptop or motherboard, although for the most part the process doesn't differ much. The Secure Boot option can be found either in Security, System Configuration or Boot; you will have to check "Disabled" once you locate it. Then you will have to enable OS compatibility mode. Different manufacturers assign it different names: Launch CSM, CMS Boot, UEFI and Legacy OS or CMS OS. It can be found under "Advanced" in the main menu, then "BOOT MODE" or "OS Mode Selection". Don't forget to save the changes.
[/panel]
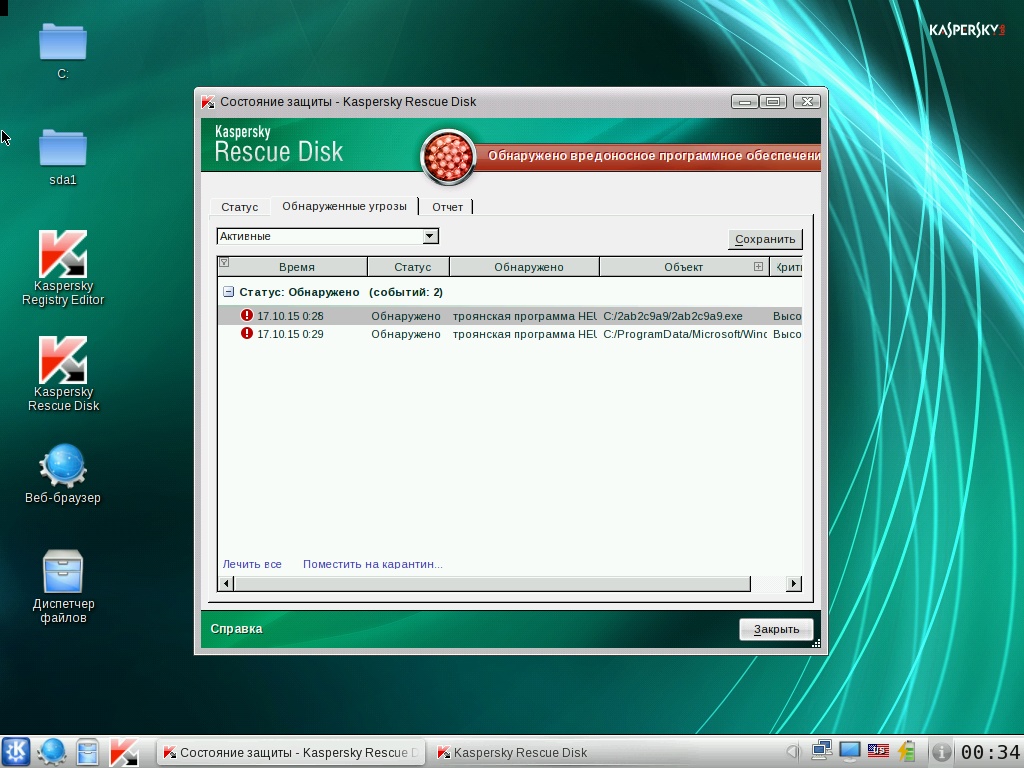
After you manage to boot your computer, you can scan and clean it. Usually this occurs without any prompting. Some Live CDs contain registry editing utilities. This is extremely helpful for analyzing registry autorun legs (most malware uses registries to autorun when the system is booting) or to revise some of the system parameters manipulated by the malware.
[panel]
Some registry locations malware prefer
Autorun
HKLMSOFTWAREMicrosoftWindowsCurrentVersionRun
HKLMSOFTWAREMicrosoftWindowsCurrentVersionRunOnce
HKLMSOFTWAREMicrosoftWindowsCurrentVersionRunOnceEx
HKLMSOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionRun
HKLMSOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionRunOnce
HKLMSOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionRunOnceEx
HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun
HKCUSOFTWAREMicrosoftWindowsCurrentVersionRunOnce
HKLMSystemCurrentControlSetServices
HKLMSOFTWAREMicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects
HKLMSOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects
System parameters
In order to prevent debunking, certain types of malware change the registry to disable the task manager, command prompt and registry editor. It's also possible there might be unauthorized UAC.
The key
HK?USOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystemDisableRegistryTools parameter:
- 0 – enable registry editor;
- 1 – disable registry editor;
DisableTaskMgr parameter:
- 0 – enable task manager;
- 1- disable task manager;
EnableLUA parameter:
- 0 – enable UAC;
- 1 – disable UAC.
The key
HKCUSoftwarePoliciesMicrosoftWindowsSystemDisableCMD parameter:
- 0 – enable command prompt;
- 1 – disable command prompt;
- 2 – enable scripts run.
[/panel]
Tip two. The right way to ask for help
calling on the collective mind of virusinfo.info
[xakepcut]Virusinfo.info is where malware-worn users can go for help that is in most cases 100% free (don't treat this as an advertisement, we have no affiliation with this resource).
If you want help there, you will need reports from two utilities: HijackThis by Trend Micro and AVZ by Oleg Zaytsev.
Use the Help! feature first. If you are absolutely certain your computer is infected and you see every indication that this is indeed the case, but your antivirus software won't help much, get registered on the site and do as follows:
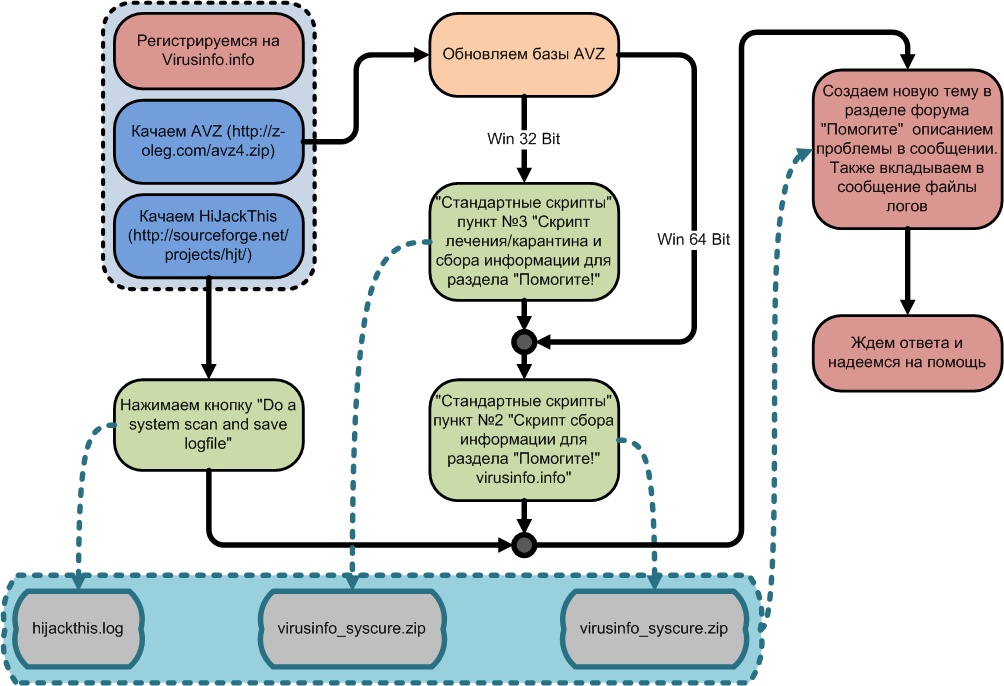
File menu, Ordinary Script in AVZ. These two utilities produce log files (for AVZ they are saved in the LOG folder located in the program folder, for HijackThis the log file is saved in the program folder). Attach these files to your message on the forum.
If you have to run a script in order to cure the PC, you will have to copy its text directly from the forum message, then in the AVZ File menu choose "Run script", and then paste in the copied text. Click "Start".
If there is no indication of an infection, yet you've still got a feeling that your PC is out of sorts, VirusDetector is what you need to be using. You don't have to register to use it. Just do as follows:
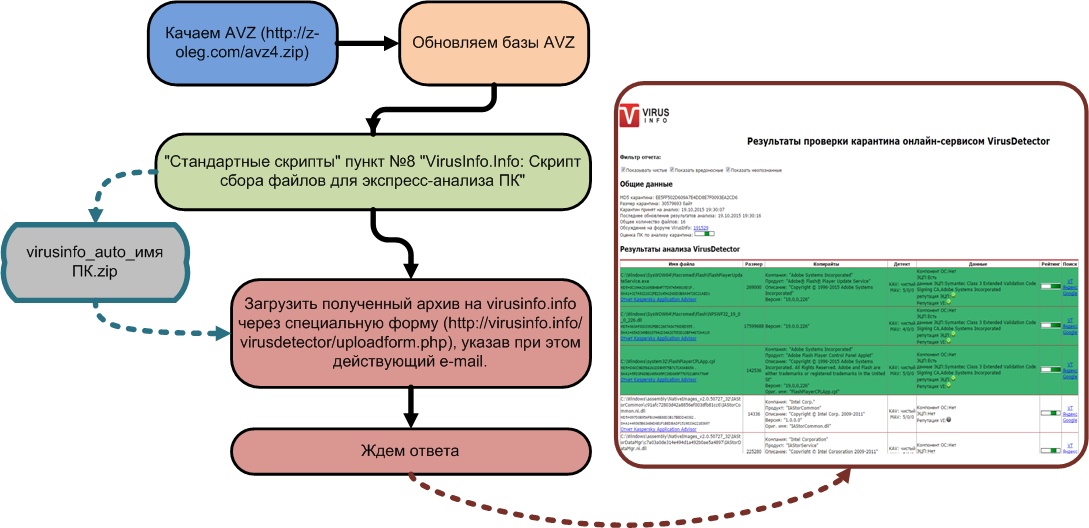
In no time at all (mine came after twenty-five minutes) you will get a detailed report on your system emailed to you with possible hardware violations.
Tip three. What else can we use besides antivirus software
using system analysis utilities
Autoruns
Malware is known to autorun when the system is booting, so it can reside there. There are lots of locations and places it can hide in Windows. To get to know all these locations you will have to use Autoruns, a very famous software in certain circles and a part of Sysinternals utilities.
This utility shows all programs, features and libraries that start up together with the system. It can also delete any of them from the list for a certain period of time or forever.
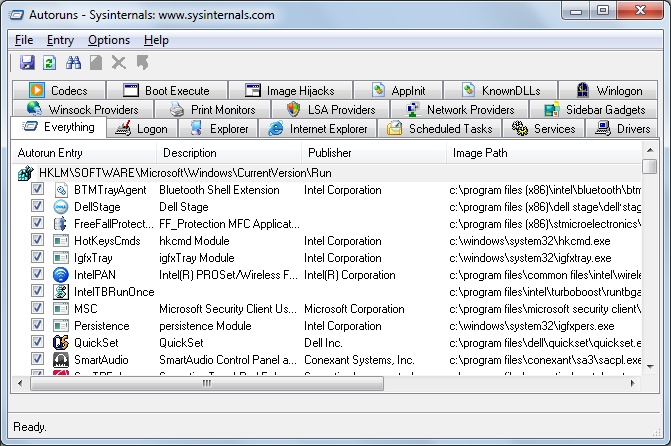
It should be noted that some malware scan the startup location and reset all the entries that were deleted. That is why after you delete all suspicious programs you need to refresh the list by clicking "Refresh" or "F5" to find out whether they are back or not.
[panel]
What are some other ways to enter BIOS (UEFI) in Windows 8 (8.1)
Method 1
In command prompt enter:
shutdown.exe /r /oMethod 2
Click "Settings" in the right panel, then "Change PC settings -> Update and Recover". Open "Recovery" and choose "Reboot now" in Advanced startup. Then choose "Diagnostics" and press "More" and "UEFI firmware settings". After that press "Reboot".
Method 3
Click "Shutdown" on the sidebar, then hold down "Shift" and press "Reboot". After that you can see the same Advanced startup as in Method 2. Then follow those same steps.
[/panel]
If the program is back on the autorun list, you can be sure it is malware (practically no other program would ever constantly check its own autorun and repair itself). In order to delete it, you will have to try and shut it down using the task manager. But most malware resists this process, so the ordinary task manager won't be of any help. But certain unconventional task managers like Process Hacker might help.
Process Hacker
Process Hacker is a free utility with open source code that monitors any system services and processes started. It is a powerful tool that helps manipulate processes and services in order to monitor and analyze them (including DLL). It includes:
- process termination (there are seventeen different ways and can terminate almost any started process);
- process suspension and restarting;
- viewing process statistics and history;
- view process memory dump;
- view traffic, environment variables and handles;
- read and edit security descriptors for processes and traffic;
- track hidden processes;
- exporting DLL;
- view and close network connections
and many other options.
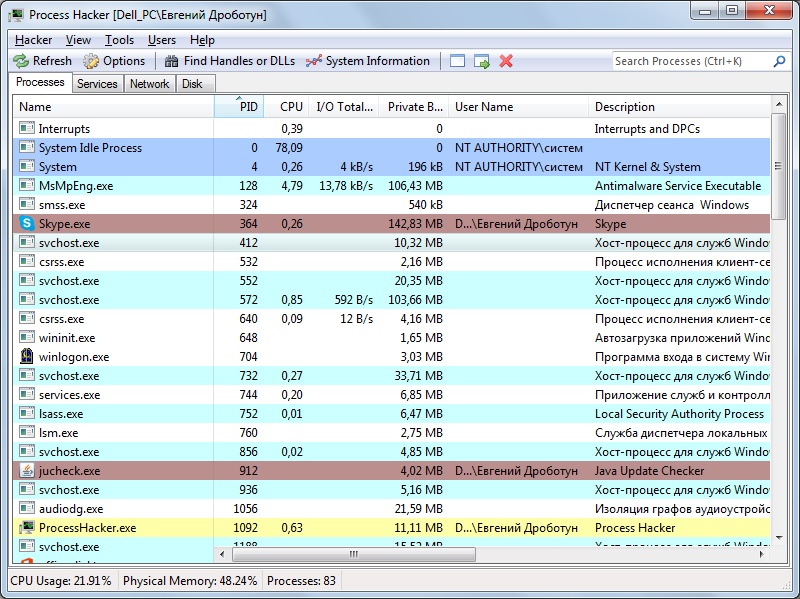
In order to suspend a suspicious process, right-click and choose "Suspend". In order to terminate it, right-click on it and choose "Miscellaneous", then "Terminator", then choose a termination method (or you can use all of them, at least one of them is bound to work) and press "Run Selected".
After that you can delete the entry in Autoruns and it won't reappear. Then you can delete the malware file. The path to it can be found in Autoruns.
You can also use Process Explorer from the same Sysinternals, however, it doesn't have such a wide range of capabilities.
Anvir Task Manager
This utility combines the autorun manager and process manager. It lets users analyze programs and services that start together with the system and receive complete information on the started processes, including
- tracking the started processes: the path, command prompt, memory, disc and processor usage, DLL downloaded, used files, created windows, streams and handles, performance counters, file version information;
- running Windows autorun areas: disable, edit, track and block all program attempts to add themselves to the autorun list;
- speeding up Windows boot by disabling unnecessary programs using pending start, selecting process priority automatically or using template-driven termination;
- analyzing information on processor and hard disc utilization.
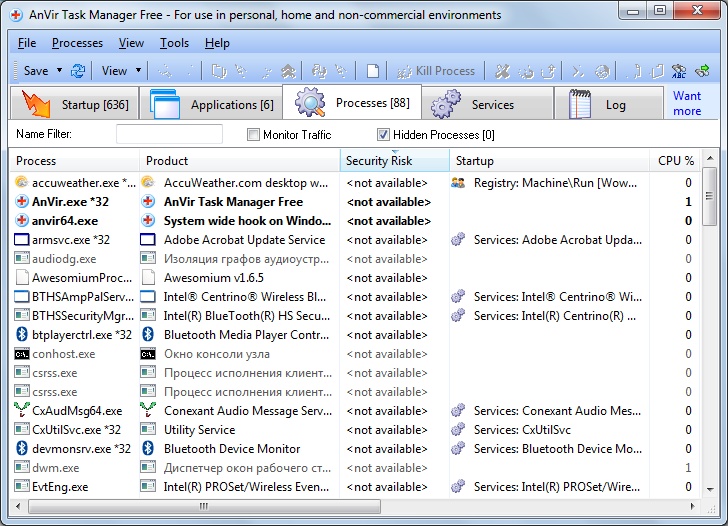
There is a commercial (Anvir Task Manager Pro) and free (Anvir Task Manager Free) version of the program, the latter having slightly less functionality.
[panel template=www]
Links to Live CD images from this article:
Kaspersky Rescue Disk 10
Live CD ESET NOD32
Dr.Web LiveDisk
Comodo Rescue Disk
Avira Rescue System
Links to HijackThis and AVZ:
Links to other utilities:
Autoruns and Process Explorer
Process Hacker
Anvir Task Manager (free version)
WinSetupFromUSB
[/panel]
