DDoS attacks have become a real scourge of the modern Internet. They are countered by both organizational methods (we wrote about them in our magazine more than once) and technical means. The latter are usually either ineffective…
CONTINUE READING 🡒 Category: Stuff
Using synctool for server configuration management
The problem of managing a large number of systems is not new, but it has become particularly acute following the spread of clusters and cloud services. A variety of tools has been designed in order to solve…
CONTINUE READING 🡒 How to find vulnerabilities in routers and what to do…
Often, the manufacturers of routers do not particularly care about the quality of their code. As a result, the vulnerabilities are not uncommon. Today, the routers are a priority target of network attacks that allows to steal…
CONTINUE READING 🡒 Hackbook #197. Set up Cisco as server, SOP bypass for…
Set up Cisco as server, SOP bypass for Flash and other
CONTINUE READING 🡒 Oracle DB vulnerabilities: the missing pentester handbook
Today, I would like to discuss the attack vectors used at various stages against the Oracle databases: how to probe the database weaknesses from outside, how to gain a foothold inside and how to automate all this…
CONTINUE READING 🡒 Dive into exceptions: caution, this may be hard
Modern versions of OS impose security-based restrictions on executable code. In this context, the use of exception-handling mechanism in injected code or, say, in the manually projected image may become a non-trivial task, that is, if you…
CONTINUE READING 🡒 Full kit of a Security Officer for $100
Our goal is the carry-on gadgets that justly could be included in the usual of a hacker, a young-gun detective or an info security officer. Today we are going to talk about usage and modify of different…
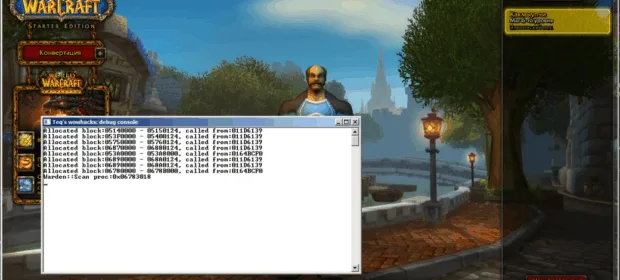
CONTINUE READING 🡒 Deceiving Blizzard Warden
Nowadays, embedded process and its environment tracking system designed to prevent various unauthorized code modifications is no surprise to anyone: almost any somewhat popular multi-player game project has something similar. In this article we will analyze the…
CONTINUE READING 🡒 In the Depths of iCloud Keychain
The secure storage of passwords and their synchronization between devices is definitely not a simple task. About a year ago, Apple introduced to the world the iCloud Keychain, its centralized password store for Mac OS X and…
CONTINUE READING 🡒 Malware oddball: key aspects of atypical malware
We've long forgotten about assemblers as everyone's used to the fact that most malware is written on C++, C# or even VB. However, anti-virus developers report that virus makers of the XXI century not only use classic…
CONTINUE READING 🡒 Stuxnet DIY: malware for industrial automation concepts
It all started when we came across PLC Delta DVP–14SS211R. And things started moving… Well, what should a hacker do with a programmable logical controller? I’ll say, investigate and try to write an exploit. In one of…
CONTINUE READING 🡒 Using DroidBox for dynamic malware analysis
Malware for Android develops rapidly, and antivirus programs are not always effective against it. Aside from harmful applications, even actual legitimate software sometimes requests privileges which in theory is not needed. How can you find out what…
CONTINUE READING 🡒