Over four years have passed since the release of Windows 10, and throughout this entire period, user data have been ‘leaking’ to Microsoft servers. The problem has been further exacerbated by Microsoft repeatedly forcing a reset of the users’ privacy settings and reactivating Windows Update disabled by the user. In this article, I will discuss and compare several utilities developed to control Microsoft’s ‘spying’ activities, and test their efficiency on two Window 10 builds.
Microsoft had never made a secret of user data collection. In the past, the company had claimed that “some data are collected to enhance the user experience”. However, after the enactment of the EU General Data Protection Regulation and some other laws, corporate lawyers had to disclose the details. Here you can see what data are collected, where are they transferred, how Microsoft processes them, and when it discloses the collected information.
Microsoft claims that it allows users to control the type and amount of transferred data. All you have to do is install updates (if your build is older than 15063.0) and open the Privacy Screen. Ideally, this should be done during the installation.
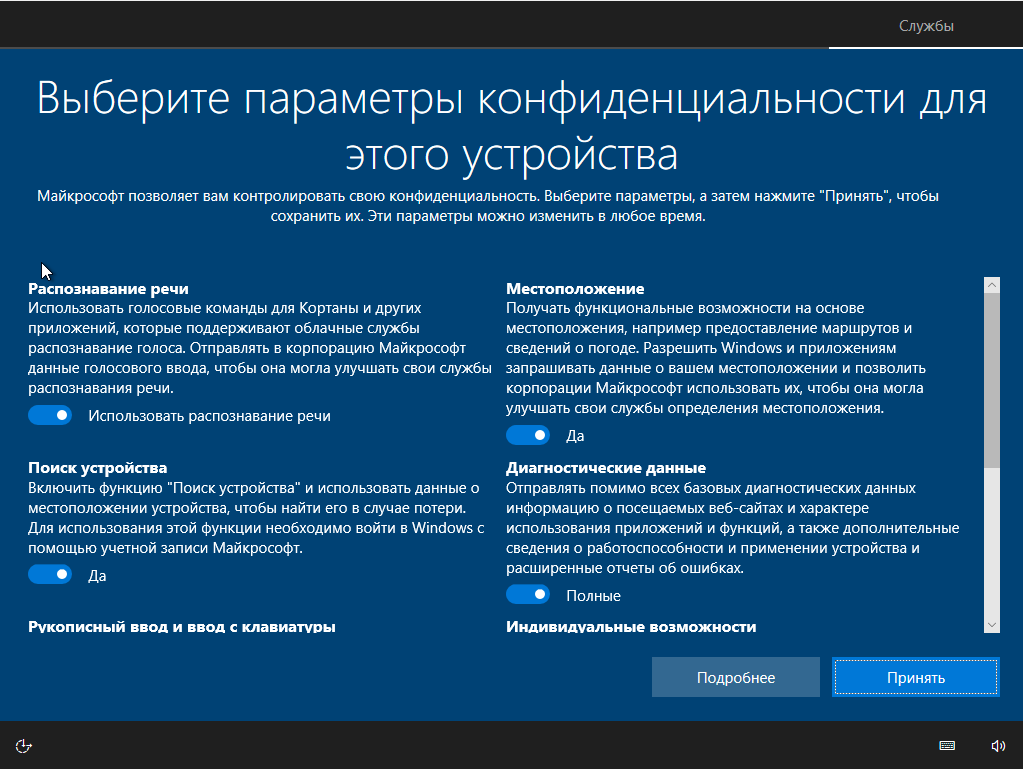
The security screen creates an illusion that if you disable everything, your data won’t be transferred at all. This is what IT security specialists call the “false sense of security”. Let us launch a sniffer and find out the truth.
Testing methodology
All tests were performed on two Windows 10 Pro builds: 1709 and 1803. To ensure identical testing conditions, each tool was run in a virtual PC image. If not specified otherwise, screenshots for build 1709 are on the left and for build 1803, on the right. The following supplementary utilities were used in the experiments: Wireshark 2.6.3 64 bit, TCPView v. 3.05, and Regshot v. 2.1.0.17.
In all tested programs, I adjusted the setting to ensure the maximum blocking level one can officially achieve. If some function or application remains unblocked, we have a collision: we cannot say if the data leak is caused by a missed option or the tool is unable to block some OS functions. The ideal result would be a network traffic dump containing no IP addresses belonging to Microsoft. Prior to the testing, let us check privacy management settings available in Windows 10.
Checking privacy settings
If you leave the default settings unchanged, the outgoing traffic to Microsoft addresses will be excessive.
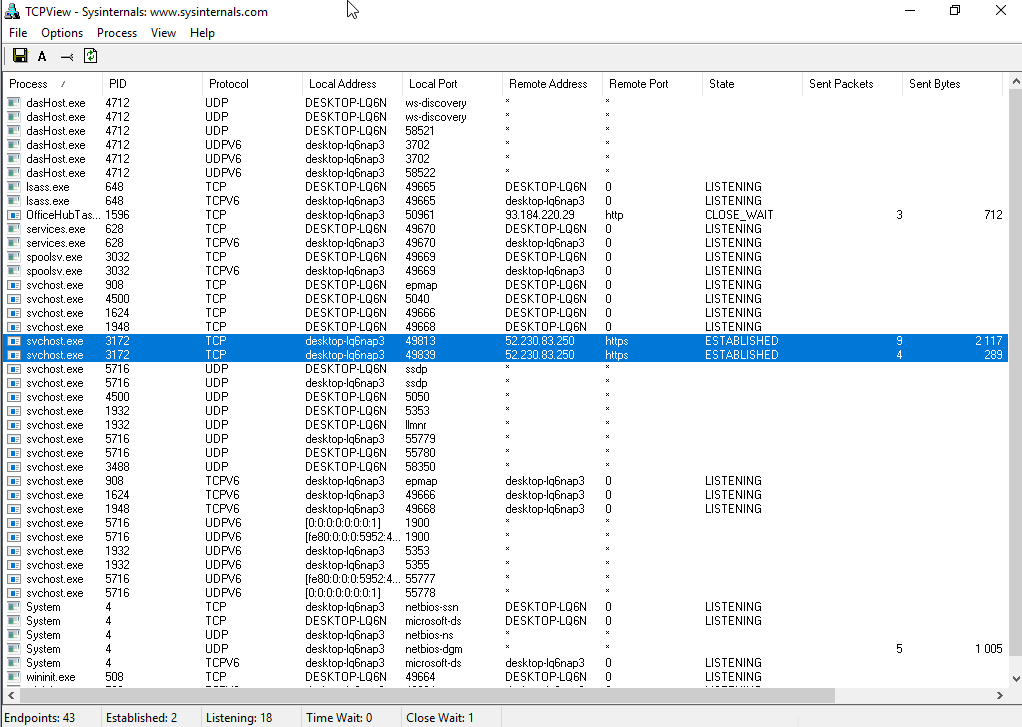
Turn off everything that can be turned off on the Privacy Screen. The result is impressive.
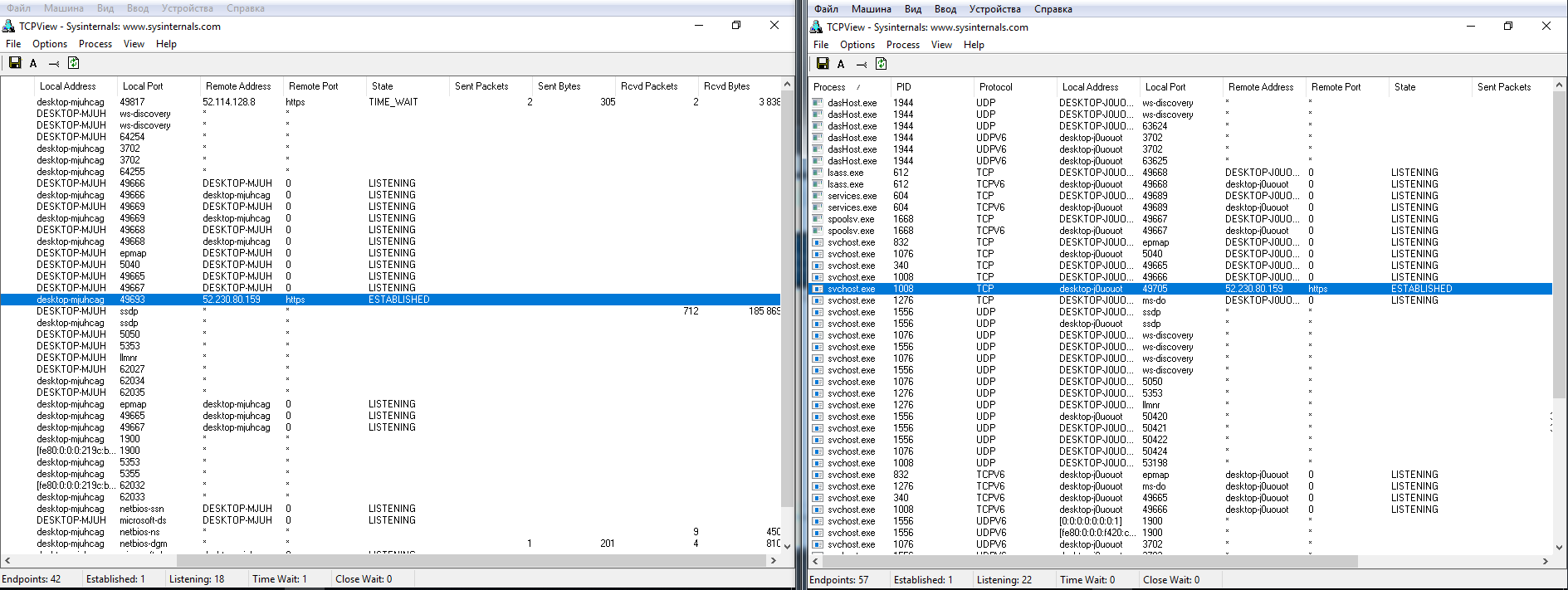
However, even after disabling all available options, some data are still sent to the Microsoft Azure cloud service located in… Singapore. Wireshark logs include IP addresses of network hubs belonging to Microsoft in many countries of the world. Apparently, this is how the corporate load balancing system works. These connections are not permanent (the computer establishes contact, transfers data, and disconnects). The address pool is extremely large. I checked these addresses and confirmed that almost all of them belong to Microsoft or its partners.
Comparison of programs
The following anti-spyware programs were used: Blackbird 1.0.28, Destroy Windows 10 Spying 1.0.1.0, DoNotSpy10 4.0, O&O ShutUp10 1.6.1399, Disable Win Tracking 3.2.1, and WPD 1.2.940. All these utilities were created with the sole purpose to prevent Windows from collecting users’ data. Some of them have extra features, including Windows update blocking. Below is a general list of functions normally supported by anti-spyware programs:
- disable activity history;
- disable transmission of keyboard input data;
- disable transmission of handwriting input samples;
- disable telemetry;
- disable location tracking;
- disable Cortana and reset its user settings;
- disable Windows Media online DRM;
- block application access to the user account, calendar, messages, camera, microphone, and location; and
- disable Windows Update for other products (optional).
Of course, this is not the full list, but just a reasonable minimum of functions required to protect your privacy. In fact, all these changes can be done manually. However, the benefit of anti-spyware programs is that they make a hundred tweaks in only two clicks.
Most anti-spyware utilities perform the following actions:
- edit registry keys responsible for privacy settings;
- add URLs of known network hubs receiving our data to the file
%WINDIR%System32driversetchosts; - add restrictive rules to Windows Firewall to block the connection to known IP addresses belonging to Microsoft;
- block tracking services;
- delete ‘spying’ tasks in the Task Scheduler; and
- delete system files and catalogues responsible for ‘spying’ functions (in a hardcore variant).
[panel template=warning]
Attempts to set the maximum privacy level using the above programs may cause malfunction of essential OS components, disable Windows activation, and make the OS unstable or even unbootable. In addition to Windows backups, we strongly recommend using third-party software to create a full HDD image. This step guarantees that you can revert the system to its original state if anything goes wrong.
[/panel]
Blackbird 1.0.28
The program runs in the console. It has only three functions:
- scan the system and display issues it discovers;
- launch the app blocking manager; and
- backup Windows settings. (I would like to specially mention this function. Not every program allows you to restore the original settings if something goes wrong. The backup is saved in the program folder; after its creation, the Backup function changes into Restore Backup).
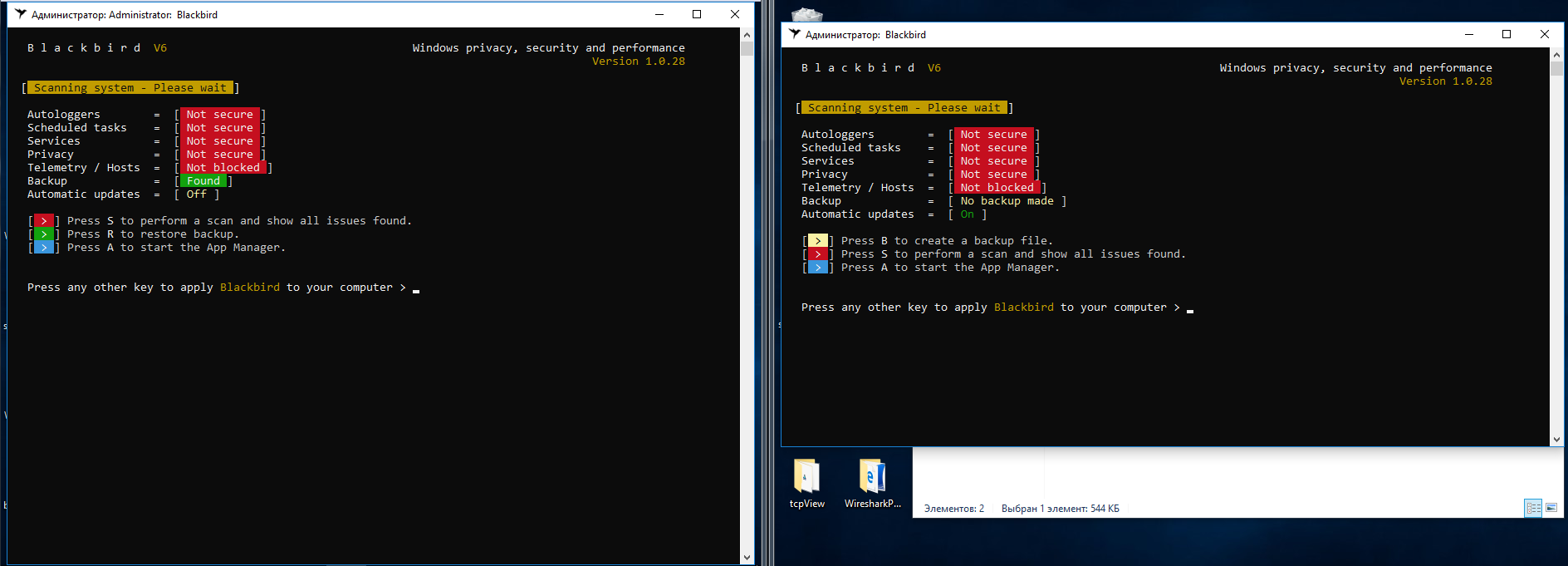
After the scanning, the program displays a long list of issues it suggests to be fixed.
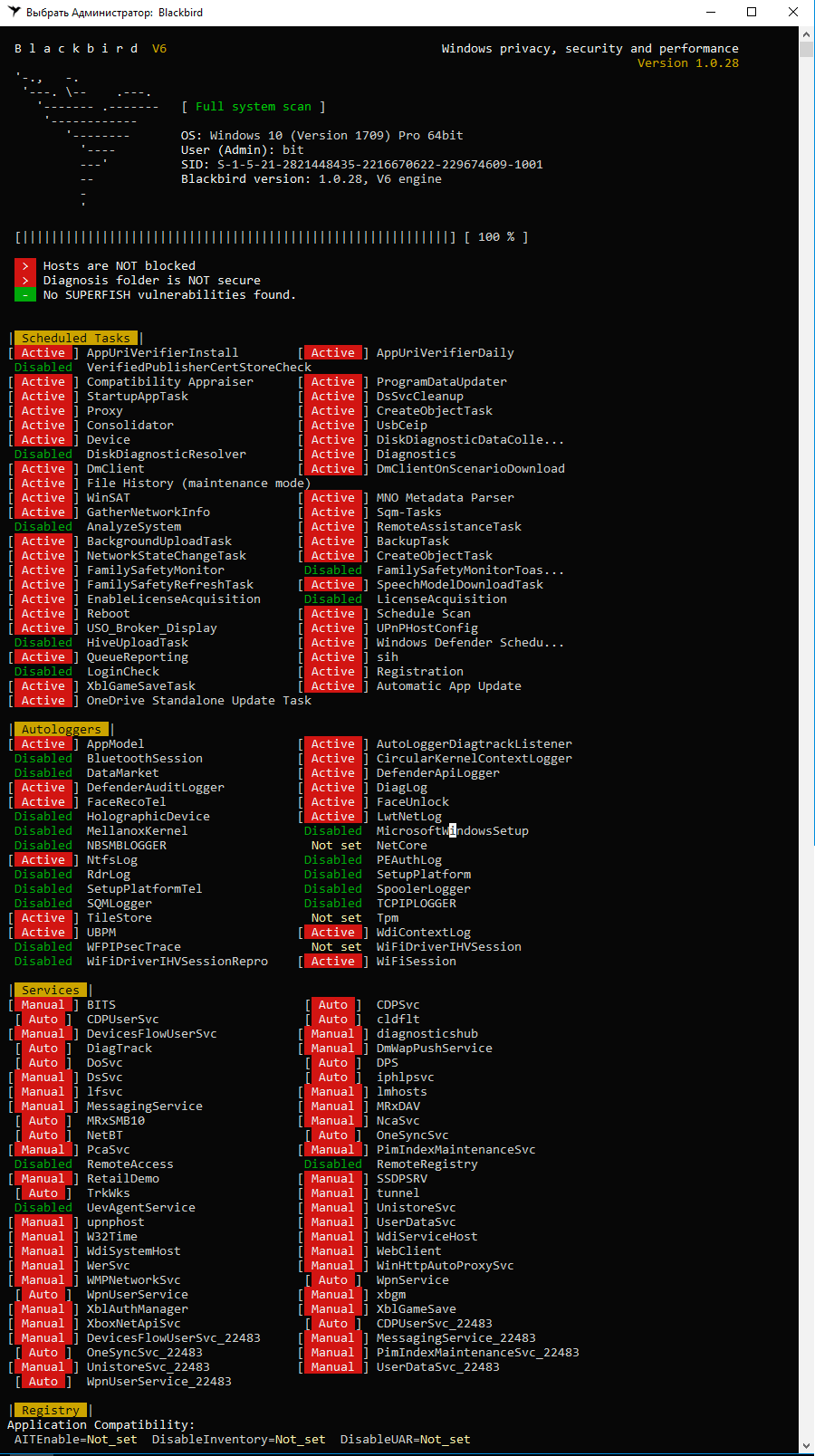
The list includes plenty of items, but some of them raise questions. Take, for instance, the blocking of W32Time. If the computer is part of a domain, then how are you supposed to synchronize time with the server?
To view the list of apps that can be blocked, press A on the program main screen. The following picture is displayed:
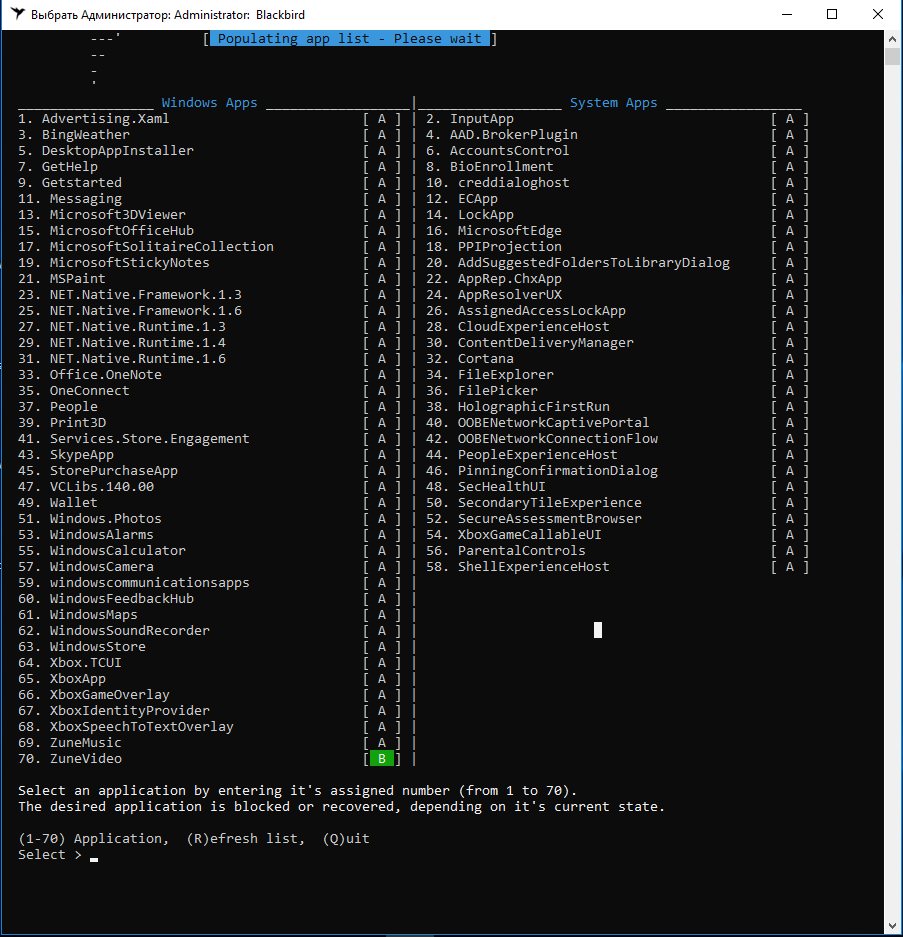
Please note that build 1803 includes some new functions; as a result, its blocking list consists of 78 items, not of 70 as in build 1709. This is the reason why I was testing two different builds of Windows 10.
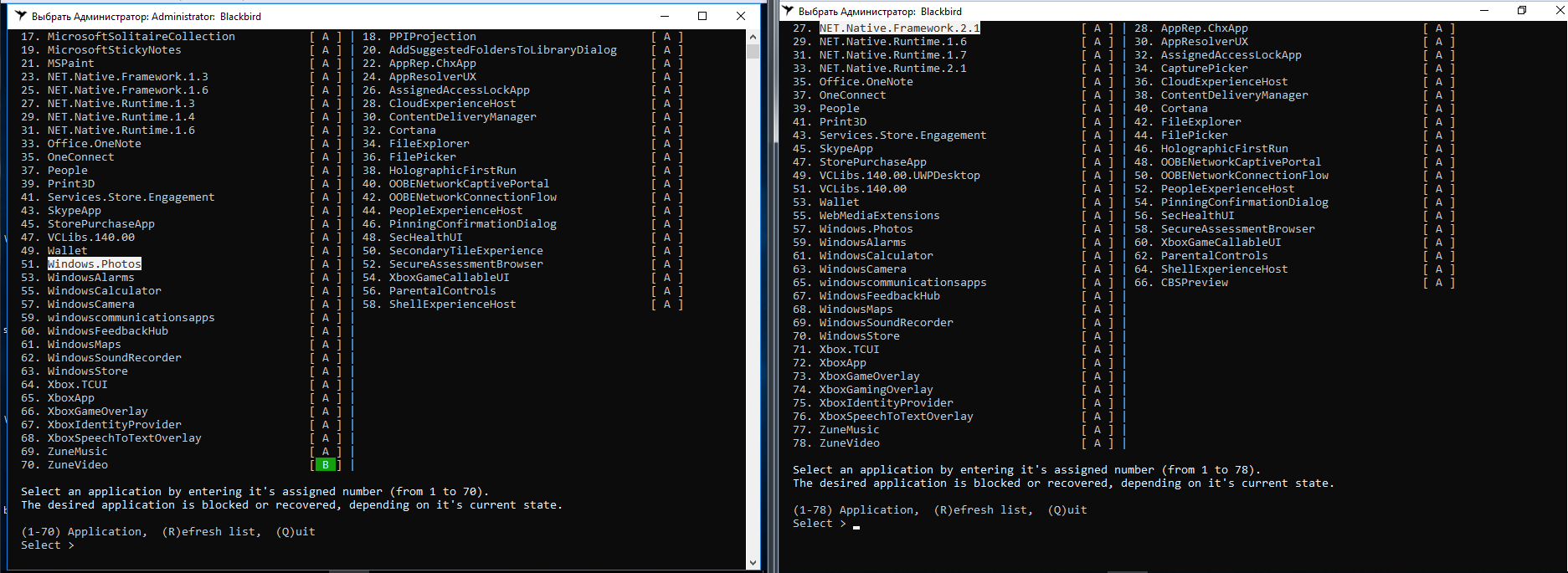
Windows Update is not on the Blackbird blocking list. The blocking mechanism is inconvenient: there are no preset profiles, and each item has to be selected separately.
Blackbird managed to block all ‘spying’ functions in build 1709. However, it failed to disable one function in build 1803, and somehow, their total number increased to 79.

Two days of monitoring have shown that Blackbird reduces the outgoing traffic by several times. However, the virtual machine with build 1803 had continuously transmitted data to IP 104.25.219.21. According to Shodan, it belongs to Cloudflare, Inc., a well-known cloud service provider. As far as I know, Microsoft leases servers from Cloudflare to store its collected statistical data. Aside from downloading updates, no other unwanted network activities were registered.
Overall, Blackbird managed to block the spying functions, but both test systems became completely broken. The Start menu does not open, Edge and IE cannot be launched, App Store and Mail try to run but immediately close; the notification panel shows messages that cannot be opened… The damaged OS became unusable. At least, the updates were installed without any issues.
The situation did not improve after I restored the system from the backup created by Blackbird. In build 1709, Windows lost activation, and two errors appeared in the registry. The problems persisted after a restart. Build 1803 failed to launch Blackbird for backup restoration due to an alleged error in the file system (even though it was OK).
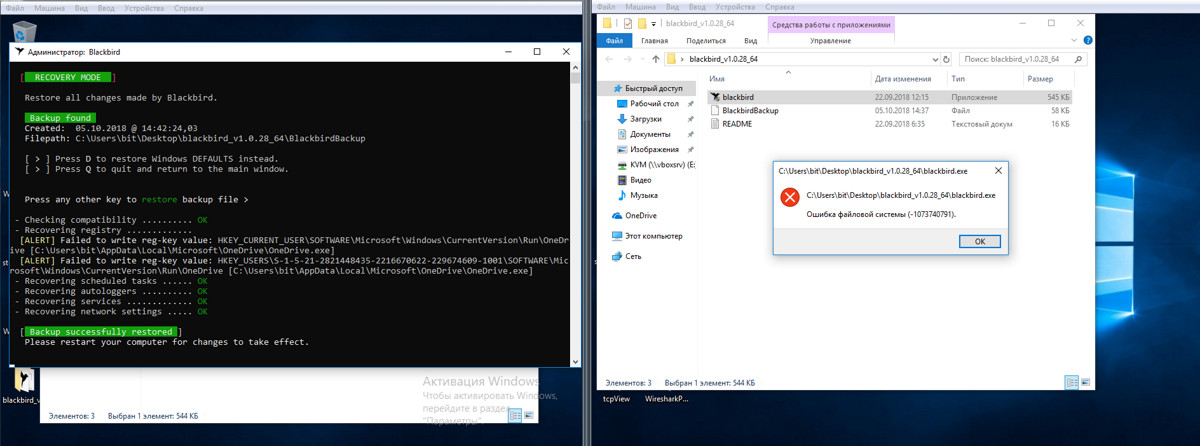
The conclusion is obvious: Blackbird is not our choice.
Destroy Windows 10 Spying 1.0.1.0
https://github.com/Nummer/Destroy-Windows-10-Spying
Destroy Windows 10 Spying is a pretty popular tool. Reportedly, its developer has changed after the release of version 1.0.1.0, and new versions have an embedded Trojan. Therefore, I will use the last official version released by Nummer.
Version 1.0.1.0 was created in April 2018. It successfully launched on my builds and identified them correctly. In addition, the program has a function for disabling Windows Update, and I turned it on.
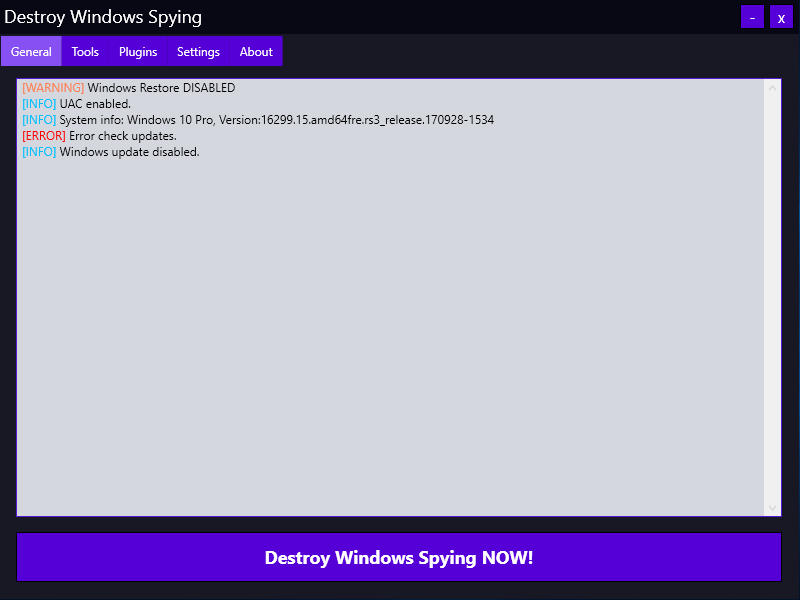
All changes are made by pressing the single big button “Destroy Windows Spying NOW!”. The program operates in three stages: it disables ‘spying’ services, adds known IP addresses to the firewall rules, and adds URLs of Microsoft statistics collection servers to the hosts file. Then the computer restarts, and the changes are applied.
Frankly speaking, DWS disappointed me.
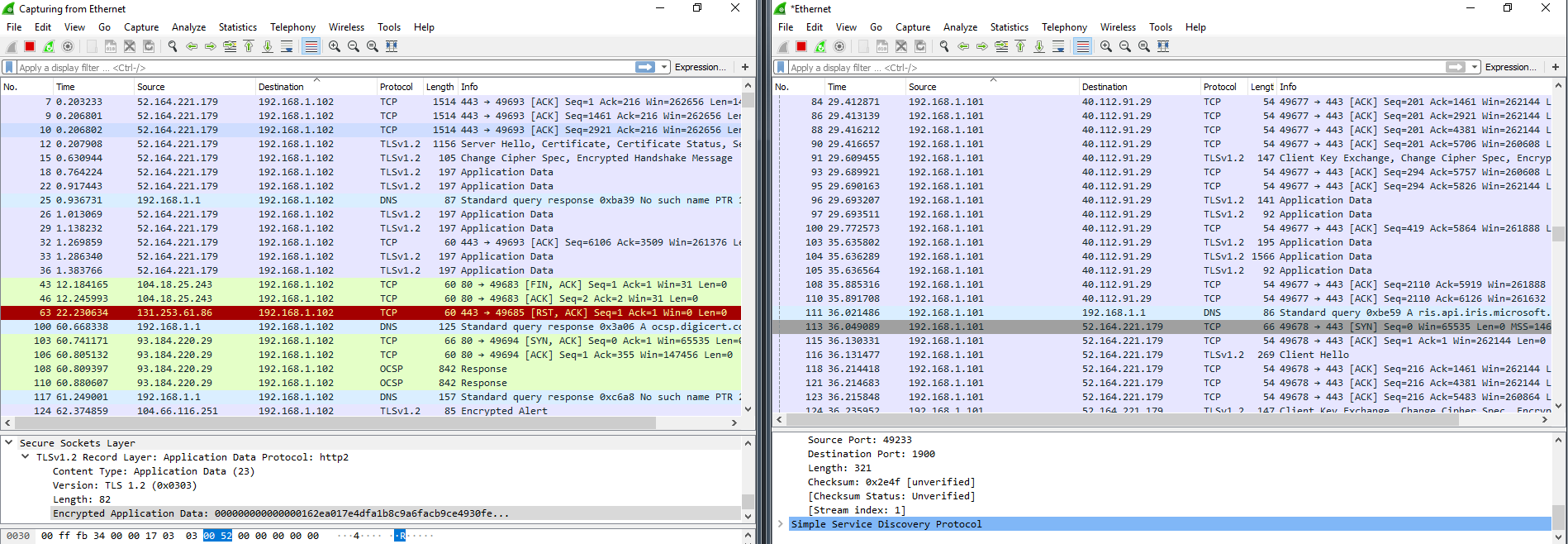
The outgoing traffic to unwanted IP addresses decreased, but the test virtual machines continued active communication. The tool is now obsolete and does not perform its functions properly on new Windows builds. A good thing is that, unlike Blackbird, the utility does not damage the OS. My virtual computers survived DWS. No software problems were identified within three days. Immediately after the restart, build 1709 had crashed a few times, but ultimately, everything restored to the normal state.
The Windows Update block turned out to be ineffective. After four or five restarts, svhost appeared again in TCPView logs and continued downloading updates as if nothing had happened. I also noted intense communication between build 1709 and an IP address of a server belonging to Akamai Technologies, Inc. collaborating with Microsoft, and a significant increase in the number of SSDP packets. Perhaps, Windows was checking reserve communication channels because its own servers were unavailable?
[xakepcut]
DoNotSpy10 4.0
https://pxc-coding.com/donotspy10
DoNotSpy10 is a popular program with a convenient interface. The developer provided a brief description for each item, so the utility is easy to use. Just check the required boxes, and voila!
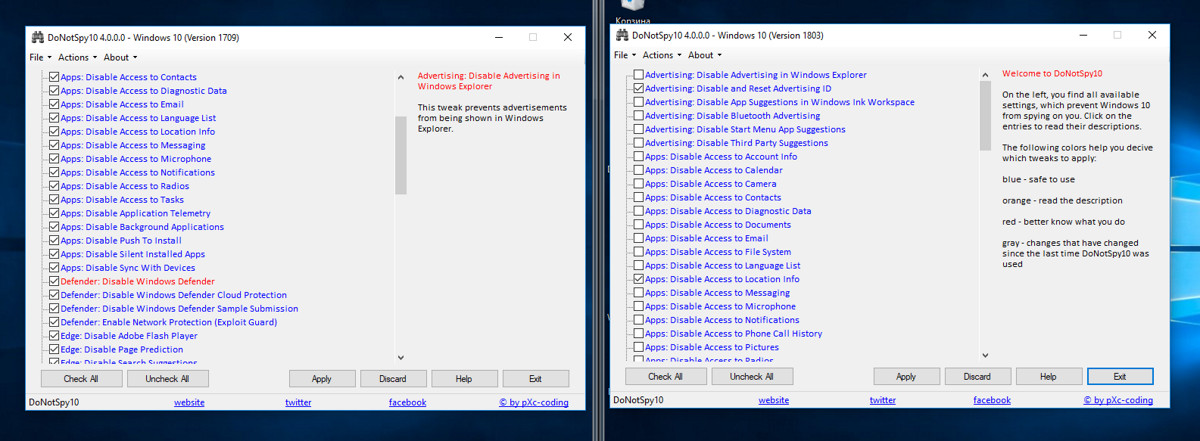
DoNotSpy10 makes it possible to create a system restore point prior to applying the changes (and I mean, the full system restore point). In my opinion, the program has way too many functions. I applied everything to the maximum, and the result surprised me. After four hours of idling, the systems began restarting. It turned out that the ‘blocked’ updates have quietly installed themselves. Wireshark has detected almost 400 thousand packets in an hour – such things never happened with other programs. The majority of the packets were addressed to servers supposedly blocked by DoNotSpy10. Furthermore, Windows activation status was reset on both builds.
Verdict: DoNotSpy10 is definitely not for everyone.
O&O ShutUp10 1.6.1399
https://www.oo-software.com/en/shutup10
This program developed by Germany-based O&O Software features a convenient interface and several preset profiles. You can apply recommended settings or all of them in one click. Other advantages include the possibility to import and export registry parameters. As experience shows, this is a very important feature. Help pops up every time you click on a function do disable it.
The program window includes a column with the heading “Recommended?”. Some items on the list are marked “No” (i.e. not recommended to be blocked/disabled). First, you think that these tweaks are highly dangerous; however, they include, for example, the automatic updates.
Interestingly, the utility suggests to make 97 changes in build 1709 and 100 changes in build 1803. The three additional items relate to Application Confidentiality and restrict access to documents, pictures, and videos.
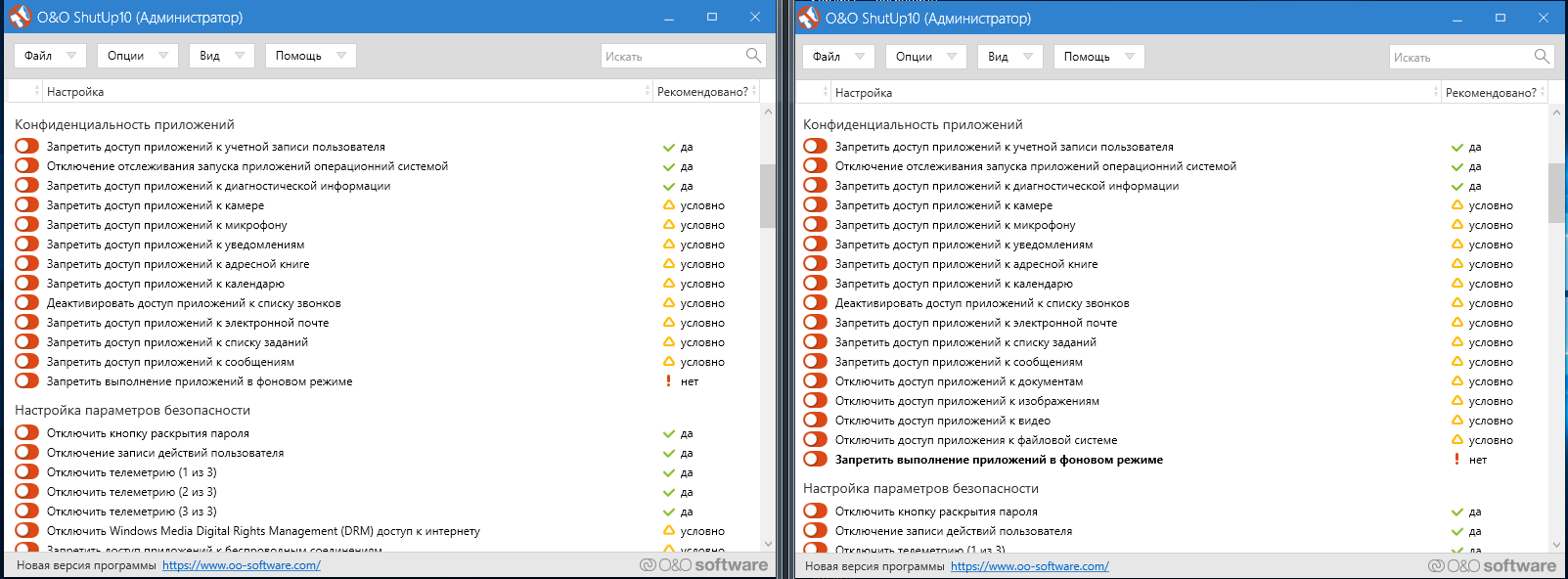
After selecting the first ‘spying’ function, the program has warned me that the restore point creation function is turned off.
Similar to previous tests, I applied everything to the maximum. Prior to closing, O&O ShutUp10 told me that if Windows updates are installed (apparently, the developers believe that their installation is inevitable), I have to launch the program again and restore the settings. Why not simply block the updates?
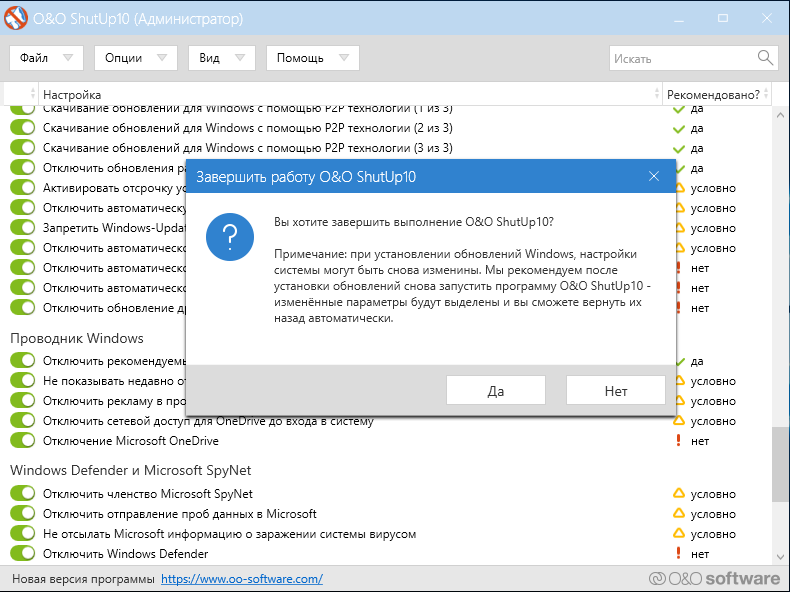
Another funny moment (yes, this is a cavil, but my internal perfectionist is outraged): after the warning, the program offers to restart the PC, but cannot do so, neither on build 1709 nor on 1803. In both cases, I had to reboot the computer manually.
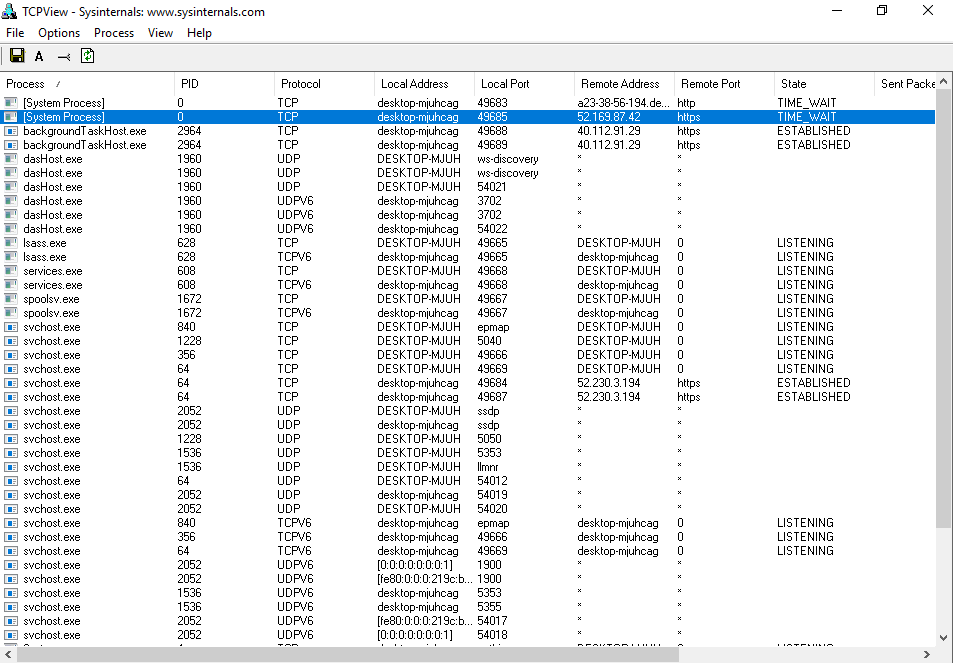
Surprisingly, after the next boot-up, TCPView shows that system processes still communicate with Microsoft servers.
The Wireshark dump also demonstrates a sad picture: a session is established and data transferred, even though the number of packets is not high.
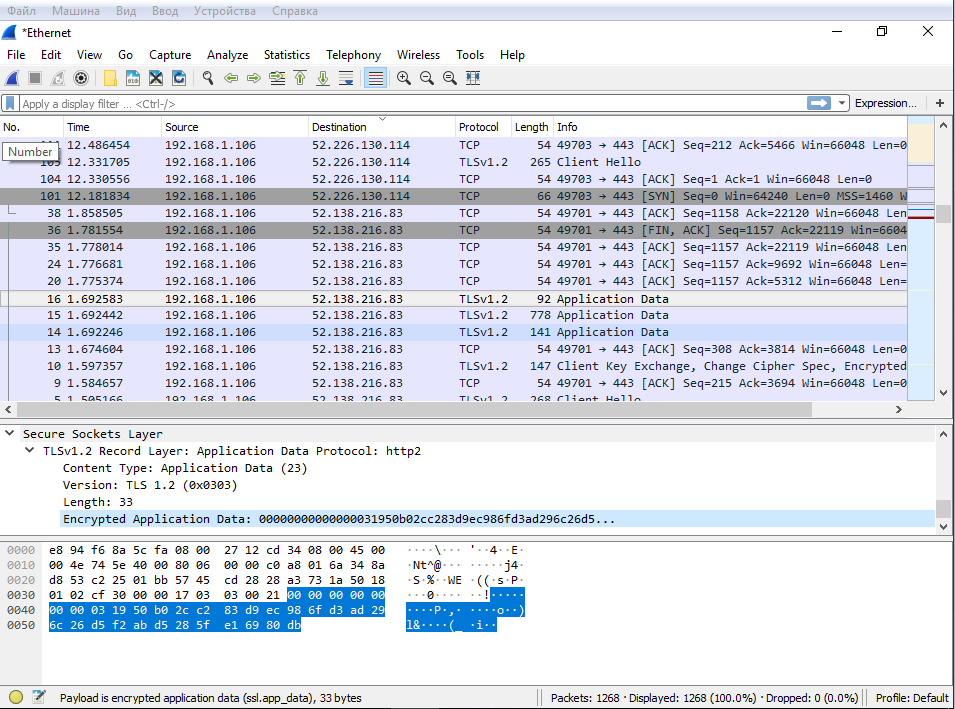
Svhost expectedly downloads updates, although I turned them off in O&O ShutUp10 by disabling two items related to Windows Update.
Several hours later, the system went offline, and I had to restart the network adapter to restore the Internet. The next check for updates resulted in a failure.
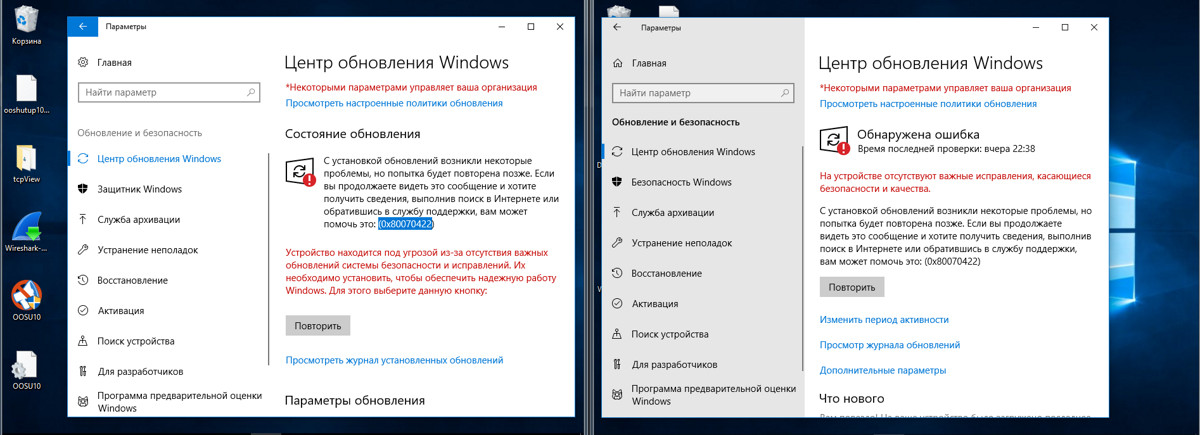
Twenty-four hours later, two earlier blocked parameters (background apps and telemetry (3 of 3)) have mysteriously resumed. No such things happened on build 1709.

After two days of testing, everything seems more or less OK. Sometimes, addresses of Microsoft servers located in various countries pop up in the network traffic. On build 1803, backgroundTaskHost, dasHost.exe, and svhost are the most frequent offenders (svhost maintains a stable connection all the time); in build 1709, the only offender is svhost. In addition, in build 1803, the option that restricts apps’ background activities is disabled after each program start, and some parameters that were disabled or blocked by O&O ShutUp10 restore their default settings. In other words, the utility managed to take control over Windows 10 1709, but build 1803 is beyond its capacity yet.
At the end of the experiment, I restored the original settings without any problem.
The OS in both virtual machines worked smoothly after the installation and use of O&O ShutUp10. I was even pleasantly surprised a few times by the better performance, especially taking the scarce resources allocated for one host and two guest operating systems in my experiment.
Disable Win Tracking
https://github.com/10se1ucgo/DisableWinTracking
Disable Win Tracking 3.2.1 is another simple utility with a minimalist interface. The last updates were released more than seven months ago; no support information for various Windows builds is available.
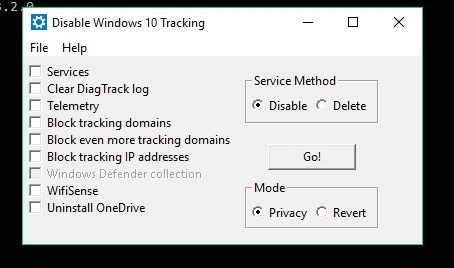
The interface offers to either disable or delete services (I chose to delete them). My actions affect two services: DiagTrack (Connected User Experiences and Telemetry, formerly Diagnostics Tracking) and dmwappushsvc (WAP Push Message Routing Service). Everything is clear and simple. When you check certain boxes, the utility warns that some application may stop working after the blocking of respective functions.
[panel template=info]
Initially, DiagTrack was distributed as an optional update KB 3022345. The installation of this ‘spying’ service was not mandatory and it could be removed using Windows tools. However, in late 2015, Microsoft engineers have renamed it into Connected User Experiences and Telemetry and included in the system as an integral element.
[/panel]
I press the GO! button; the program performs requested operations and displays a detailed report. How did it fare?
After three days of testing, new updates have been installed. The dmwappushsvc service appeared again (although disabled). The network monitoring has shown that addresses belonging to Microsoft and Akamai are still present in the logs. Both Windows systems contacted them on a regular basis; however, the traffic decreased. Disable Win Tracking had not affected the system stability, but Skype stopped working. The interventions into the system were minimal: some additional rules for the built-in firewall and a few changes in the registry.
Windows Privacy Dashboard
The last utility for today is WPD 1.2.940. At the time of the writing, the last version was dated October 11, 2018, although blocking rules used in it were dated September 16. Officially, the program supports Windows 10 builds up to and including 1809. Its functions are divided into three groups: privacy management, firewall rules, and removal of installed programs (the developers call them “Microsoft Store garbage or any other app”).
The privacy management function disables scheduler entries and some services, and makes changes in the registry. Firewall rules are created based on the selected privacy mode: Spy or Extra. If the Extra mode is selected, then OneDrive, Skype, Live, etc. are blocked (the program warns about this). As always, I used the utility to the maximum, except for the appx uninstaller.
After four days of testing, no issues were detected in the test systems: both of them were running smoothly. In my opinion, this program is as good as O&O ShutUp10. After the installation and use of Windows Privacy Dashboard, the logs list very few of connections with servers belonging to Microsoft and its partners.
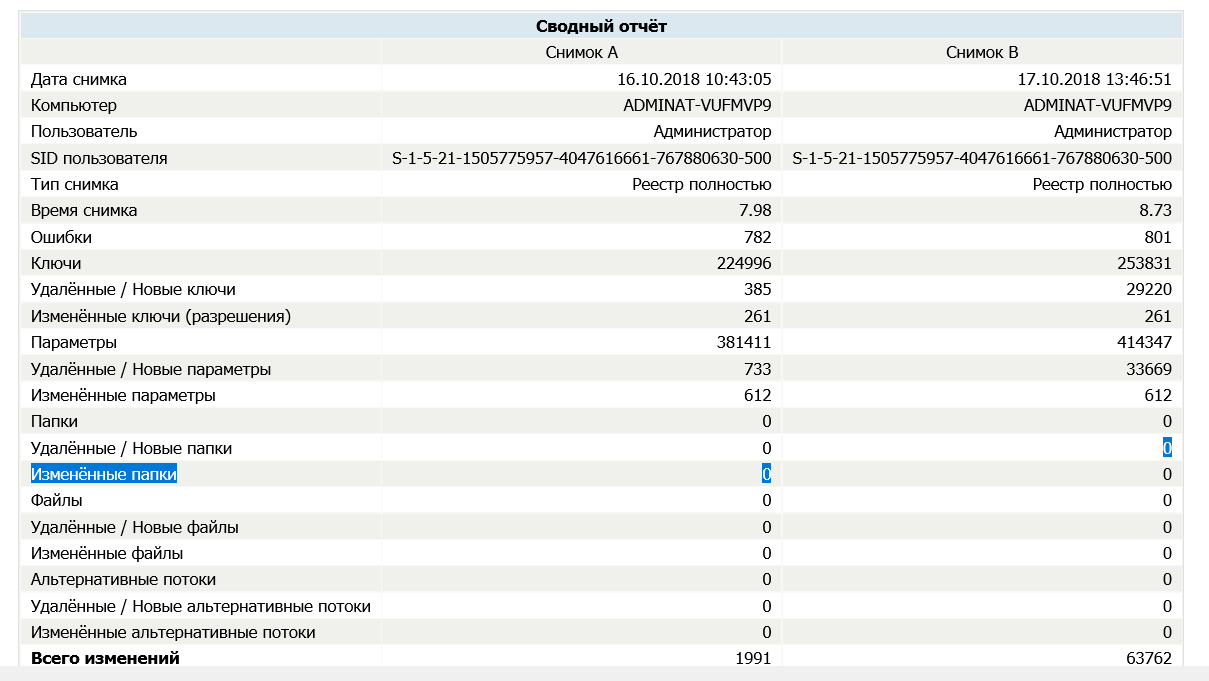
The majority of the changes made by WPD affect the registry. The results of its work on Windows 1803 are shown below.
I compared the registry snapshots using Regshot utility. The list of changed keys is long, and zeros shown in the line “Deleted/New Parameters” are self-explanatory.
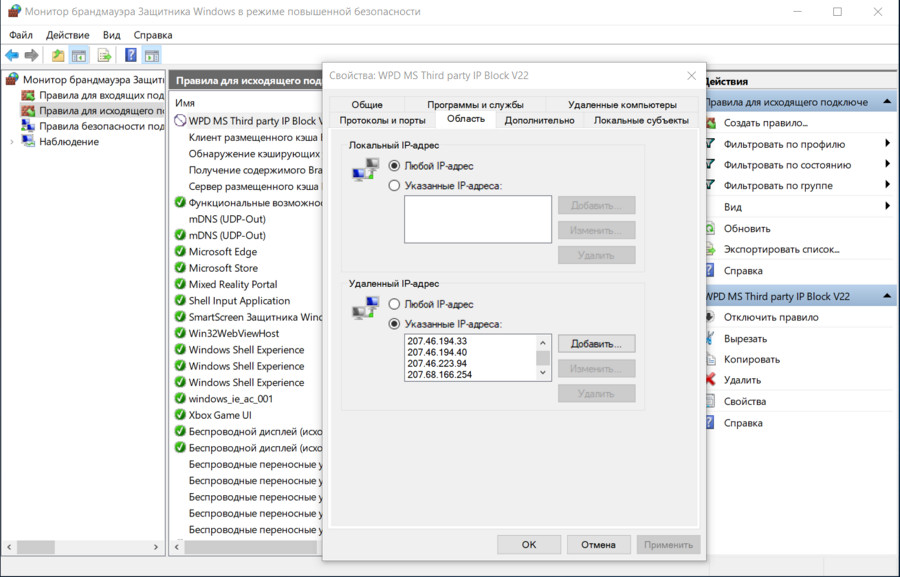
The program created one firewall rule and added a range of IP addresses.
Overall, WPD has done a good job.
Disabling spying manually
Let us try to manually implement some of the security functions featured by the above programs. I will try blocking the main ‘spying’ mechanisms described earlier in this article. Important: everything you do is your own risk and peril. I strongly recommend creating a backup copy prior to making changes in the registry.
Disabling activity history
Timeline is a Windows 10 function that shows the history of activities you have performed. Launch regedit and open to the following key: HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsSystem. Create here 32-bit DWORD EnableActivityFeed and set its value to 0.
Disabling keylogger
This refers to the above-mentioned dmwappushsvc service. Open HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesdmwappushsvc and set the value of dmwappushsvc to 4 (you can disable DiagTrack there as well).
Disabling telemetry
Keep in mind that modern Windows builds do not allow to completely disable telemetry without losing important system functions. There are three available telemetry levels: Basic, Enhanced, and Full. The fourth option is Security, but it only exists in the Enterprise version. You can set the lowest possible telemetry level in the registry: HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsDataCollection (if the DataCollection parameter does not exist, it has to be created). Then create 32-bit DWORD AllowTelemetry and set its value to 1.
Disabling location tracking
Open the key: HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionDeviceAccessGlobal{BFA794E4-F964-4FDB-90F6-51056BFE4B44} and assign the value Allow to this key.
Disabling Cortana
Navigate to HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindows Search, create 32-bit DWORD AllowCortana, and set its value to 0.
Disabling OneDrive
Follow HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsSkydrive, find or create 32-bit DWORD DisableFileSync, and set its value to 1.
Disabling telemetry transmission in task scheduler
In addition to telemetry, the Task Scheduler includes multiple jobs consuming resources and running without your knowledge. These jobs collect telemetry data for the “Customer Experience Improvement Program” and SmartScreen cloud-based antiphishing and antimalware service.
To disable these services, you have to enter the following commands:
schtasks /Change /TN "MicrosoftWindowsAppIDSmartScreenSpecific" /Disable
schtasks /Change /TN "MicrosoftWindowsApplication ExperienceProgramDataUpdater" /Disable schtasks /Change /TN "MicrosoftWindowsApplication ExperienceMicrosoft Compatibility Appraiser" /Disable
schtasks /Change /TN "MicrosoftWindowsAutochkProxy" /Disable
schtasks /Change /TN "MicrosoftWindowsCustomer Experience Improvement ProgramConsolidator" /Disable
schtasks /Change /TN "MicrosoftWindowsCustomer Experience Improvement ProgramKernelCeipTask" /Disable
schtasks /Change /TN "MicrosoftWindowsCloudExperienceHostCreateObjectTask" /Disable
schtasks /Change /TN "MicrosoftWindowsDiskDiagnosticMicrosoft-Windows-DiskDiagnosticDataCollector" /Disable
schtasks /Change /TN "MicrosoftWindowsMaintenanceWinSAT" /Disable
schtasks /Change /TN "MicrosoftWindowsNetTraceGatherNetworkInfo" /Disable
schtasks /Change /TN "MicrosoftWindowsShellFamilySafetyMonitor" /Disable
schtasks /Change /TN "MicrosoftOfficeOfficeTelemetryAgentFallBack" /Disable
schtasks /Change /TN "MicrosoftOfficeOfficeTelemetryAgentLogOn" /Disable
Disabling data transmission to Microsoft servers
Plenty of online resources publish lists of Microsoft servers and update them on a regular basis. For instance, such a list is available on aeronet.cz. The easiest way to block these addresses is by adding them all to the hosts file or creating firewall rules.
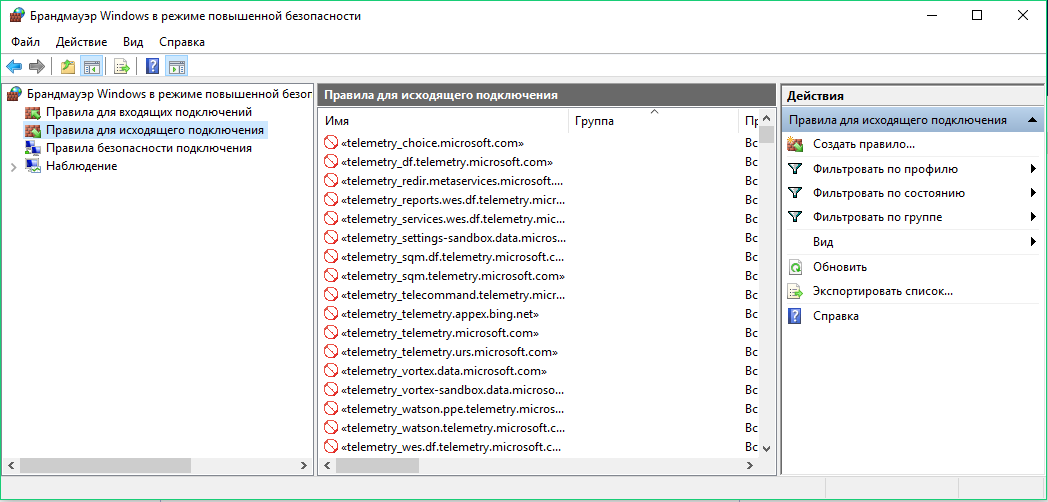
I used both methods. Windows managed to contact one of the blocked addressed within an hour , but the network packet size was zero.
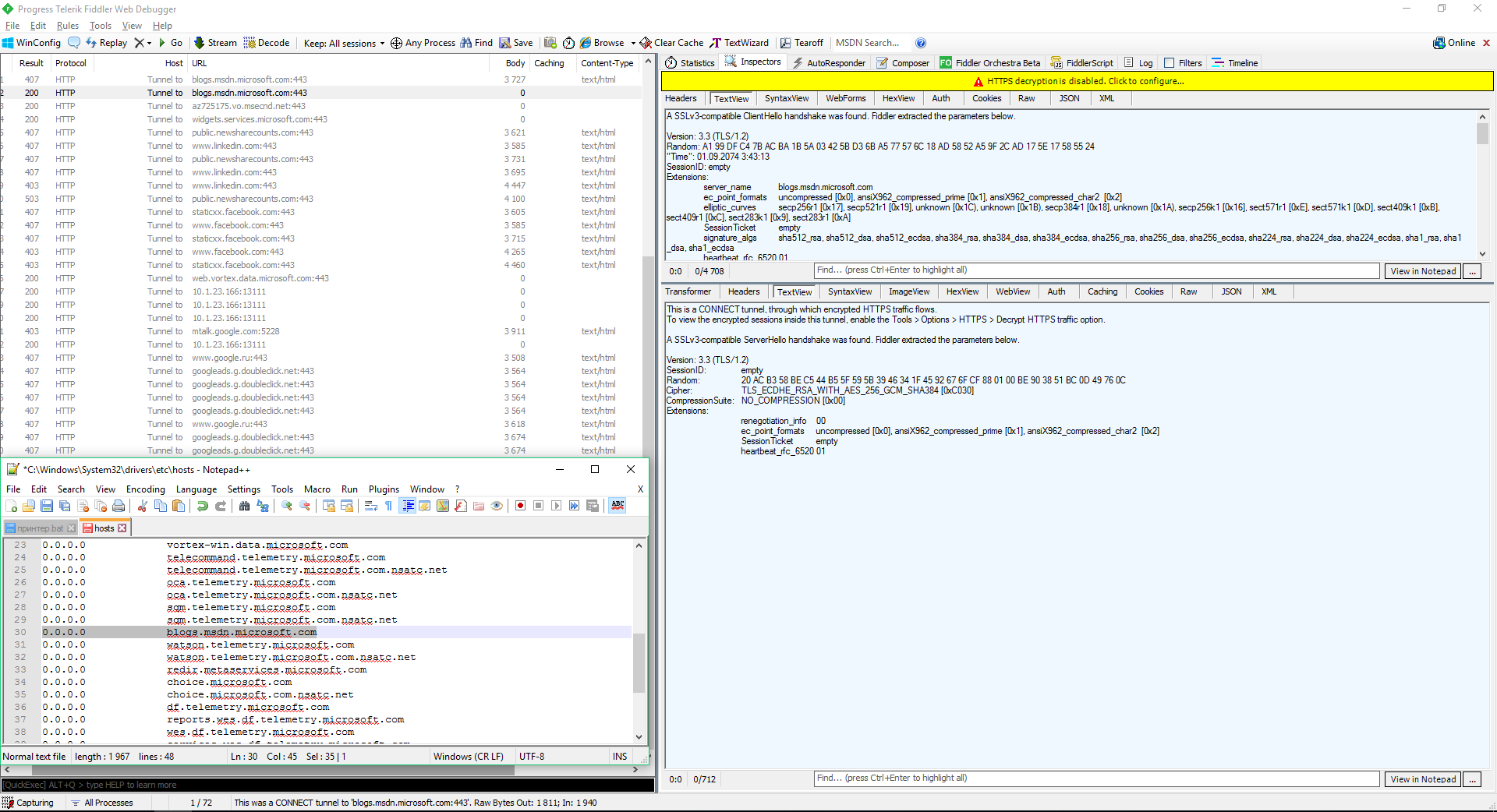
Some security experts believe that Windows system processes (including ‘spying’ ones) can bypass blocks in the hosts file and built-in firewall. In theory, the URL blocking in hosts can be bypassed by directly addressing the IP address, while the IP blocking in the Windows Firewall can be bypassed via dnsapi.dll by intercepting the protocol creation function at NDIS level. However, I did not notice any unwanted traffic during my experiment. After blocking the IP addresses in the hosts file and applying restrictive firewall rules, the computer continued attempts to contact the ‘spying’ servers. However, no incoming packets were detected, while outgoing packets had zero size.
Blocking updates
As a dessert, I would like to present StopUpdates10 2.0.32. This small utility has a sole purpose of blocking Windows updates. Note that most other tools failed to block them despite their claims.
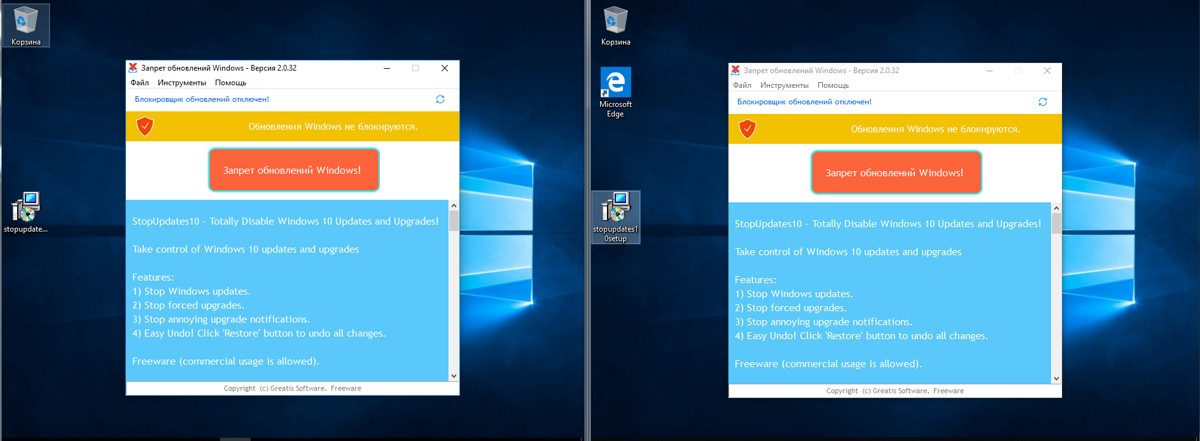
The user interface is limited to a single button. Press it and restart the computer.
The testing continued for two days. During this period, the utility had successfully prevented the download of updates even thought Windows persistently tried to find them. Error messages displayed by the OS were annoying.
After two days of testing and a dozen of restarts, I checked for updates manually and could not find any. The list of installed updates included only those downloaded prior to the program installation.
Conclusions
Six antispyware programs have been tested. In fact, there are many more tools like that. Their authors copy each other’s findings (Fork me on GitHub!) trying to make the lists of tweaked parameters and blocked addresses as long as possible. They rarely bother with thorough (and lengthy) testing. OS-related problems often arise in a while after using the tool. In other words, such tools are literally time bombs.
The development of many anti-spyware tools for Windows 10 has stopped in 2016-2017 as a result of the continuous ‘arms race’. Microsoft frequently changes IP addresses of its servers, leases cloud servers from Cloudflare, and redirects a portion of the traffic to its partner Akamai Technologies. It owns a dynamic pool of IP addresses and a number of major networks. It is simply impossible to track and block everything. In addition, the same URL is often used for connection to different IP addresses or multifunctional servers required for the operation of ‘clean’ (i.e. not ‘spying’) Windows components.
It is possible to add the addresses of Microsoft data collection servers manually; their lists are available on GitHub and other forums. You’ll have to download these lists, merge them together, edit, verify (the most time-consuming stage), and then apply the resulting ‘blacklist’. In other words, it’s a lot of work for a stable result. Next day, Microsoft releases a new update, a bunch of new IP addresses appear, your blacklist compiled with so much pain becomes obsolete, and you have to start over.
Of all the tested programs, only O&O ShutUp10 and WPD have performed their functions more or less satisfactory. Some privacy settings can be tweaked using Windows tools, although not all of them are shown in the user interface. If an anti-spyware utility can change some additional and underlying settings, it makes sense to try it. However, such experiments require caution: one has to carefully select the parameters to block, and make backups prior to applying any changes.
[panel template=www]
- Official list of connection endpoints for telemetry data
- How to configure diagnostic data collection in Windows 10 Enterprise and Windows Server
- Microsoft Privacy Statement
[/panel]