As you are aware, any penetration test starts from information collection. You have to find out what operating system is running on the remote host, and only then you can start looking for vulnerabilities in it. This article presents seven useful tools used inter alia for OS detection and explains their operation principles.
The inventory of programs used by pentesters and hackers is truly impressive. It’s not a secret that reconnaissance and intelligence collection constitute the most important stage of any security research; so, let’s examine the utilities used at this stage in more detail.
If you read HackMag on a regular basis, you have likely encountered the names of these programs in our articles and probably know the term “TCP/IP stack fingerprinting” that defines their operation principle.
This article presents the most actual utilities used for OS detection and examines their specific features and capacities.
In lieu of a preface
Seasoned pentesters and hackers may skip this section because it explains the very basics. At the very beginning of the intelligence collection stage, the remote host is a ‘black box’ for you. In the best-case scenario, you know its IP address, and that’s it. You have do find out what ports are open on the target machine, what operating system is running on it, and what networking software is installed. Only after obtaining this information, you will be able to start searching for vulnerabilities.
OS detection techniques are divided into passive and active ones. In the first case, you use sniffing tools (e.g. Wireshark) and analyze the intercepted traffic. In the second case, the pattern principle is applied: each OS has a distinctive set of open ports you can knock on, check their availability, and make some important conclusions. In both cases, you analyze parameters constituting the unique OS fingerprints; accordingly, this class of techniques is called “fingerprinting”.
The majority of passive traffic analysis techniques examine the TCP/IP stack on the remote PC. Packet headers include fields whose values are different on different operating systems. For instance, the TTL (Time To Live) value of 64 is typical for Linux and FreeBSD. If the DF (Don’t Fragment) flag is not set in the header, you are likely dealing with OpenBSD. Other indirect indicators include the window size, MSS (maximum segment size), window scaling value, and status of the sackOK flag. Using the exclusion method, you can identify the OS running on the target host. The utilities presented below will assist you in this.
Nmap
- Official website: nmap.org
- Platform: GNU/Linux, macOS, Windows (x86)
Nmap is a popular cross-platform tool with a great functionality. Its capacity goes far beyond fingerprinting.
The actual version 7.80 features an intuitive graphical interface and also supports the command line mode (the command syntax is nmap -O -PN [URL] where URL is the address of the target host). Old-school hackers can compile Nmap from binaries available on the official website.
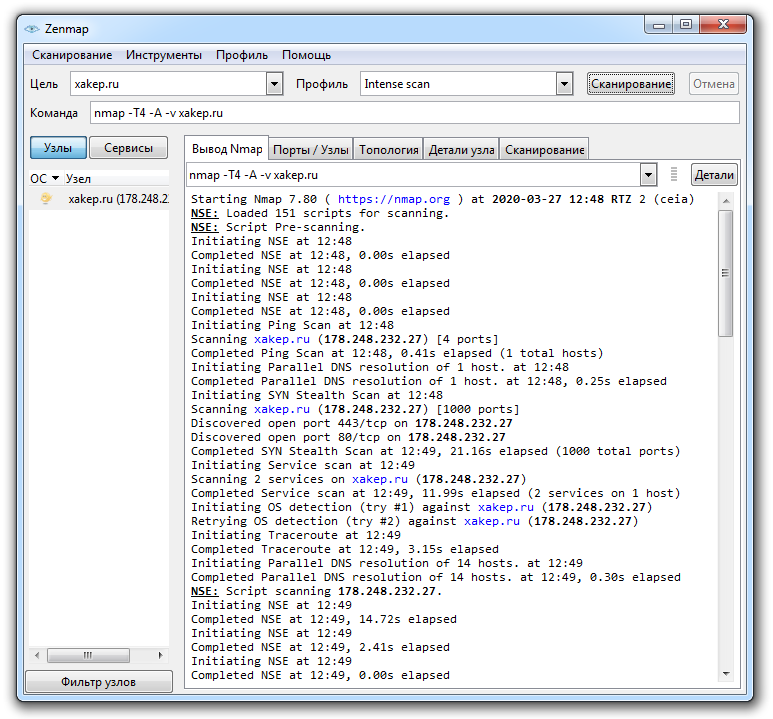
Nmap diagnoses the host OS with the 90% probability and even higher. In most cases, this is sufficient to define the attack vector.
In addition, the program provides information about the server version, open ports, DNS requests, IP and IPv6 addresses, and classless inter-domain routing (CIDR) data. Nmap can also perform reverse DNS lookup and has plenty of other useful functions. This great tool supports several scanning modes whose selection depends on your goals.
Detailed documentation is available on the official website as well. HackMag has recently published an article about NSE scripts that can significantly boost the capacity of the scanner. The utility is so powerful that it even allows to bypass firewalls and perform DoS and other attacks. Overall, Nmap is a must have for any ethical hacker.
[xakepcut]
NetworkMiner
- Official website: https://www.netresec.com/index.ashx?page=Networkminer
- Platform: GNU/Linux, Windows
NetworkMiner is essentially a traffic analyzer, although the developers present it as an open-source Network Forensic Analysis Tool (NFAT). The program uses passive remote host analysis techniques, thus, leaving no traces and enabling you to act covertly.
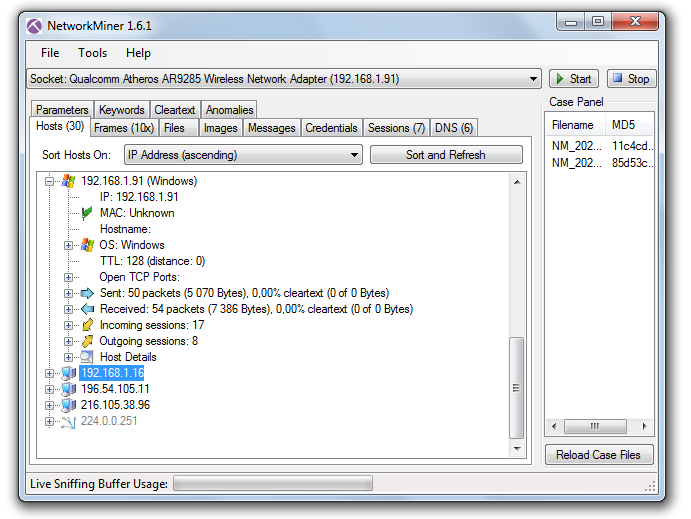
The utility can be downloaded from http://sourceforge.net/projects/networkminer, while its source code is available on the developers’ web page.
NetworkMiner allows to track the established connections; it analyzes transmitted packets and extracts information about hosts communicating with your PC. The input data used for the analysis include the content of the TTL field, frame sizes, and flags in packet headers.
NetworkMiner can analyze individual frames as well. On the Frames tab, you can find information on the frame size, IP addresses and ports of the sender and receiver, and other useful data. In addition, it is possible to analyze daemon banners. The collected information allows to reconstruct the network structure; this is especially useful when you deal with an unknown wireless network.
In addition, NetworkMiner can extract files from traffic transmitted using the following protocols: FTP, TFTP, HTTP, HTTP/2, SMB, SMB2, SMTP, POP3, and IMAP. In other words, this tool allows you to intercept files sent by e-mail or FTP, through a local network, or even via the user’s browser. Also, NetworkMiner retrieves X.509 certificates from encrypted traffic.
Overall, it must be admitted that this sniffer is extremely powerful, and fingerprinting/OS detection is only one of the aspects of its versatile functionality.
p0f v3
- Official website: https://lcamtuf.coredump.cx/p0f3/
- Platform: GNU/Linux, Windows, macOS
This popular sniffer analyzes intercepted packets and OS fingerprints using an entire complex of mechanisms. According to the developers, p0f v3 can detect the OS running on a remote host even when Nmap is unable to perform this task (e.g. when the network is protected by a firewall).
p0f v3 supports several modes used depending on the network configuration and researcher’s goals:
- SYN mode (analysis of incoming connections);
- SYN+ACK mode (analysis of outgoing connections);
- RST+ mode (traffic analysis for a node hidden behind a firewall that refuses connections);
- MiTM (analysis of a connection between nodes whose traffic you can sniff without taking any actions on your side).
In addition, the utility determines whether NAT, shapers, or firewalls are present in the target system; tracks the packet’s path to the destination node; and calculates its uptime. Importantly, the tool does not generate its own requests and other suspicious traffic, which is great if you don’t want to disclose your presence in the attacked network.
The developers have rewritten version 3 from scratch, and its brand new database of signatures is not complete yet. The program is reportedly lacking data on old OS versions, such as Windows 9x, IRIS, etc., and the users are welcome to submit new signatures and report bugs.
NetScanTools
- Official website: netscantools.com
- Platform: Windows
The free version of this utility was released back in 2009 and underwent only slight changes since then. Its capacity is pretty limited: NetScanTools can retrieve Whois data, execute the traceroute command (for those unable to use the command line), send DNS requests, and ping remote hosts with various pinging parameters. Not much…
The functionality of the commercial version, NetScanTools Pro, is much greater. It supports various protocols, including ARP и SNMP, intercepts and analyzes packets, retrieves DNS records for the required IP addresses, searches for open TCP and UDP ports on a remote host, identifies SMB versions supported by it, and searches for devices on the network, including SMTP servers with open relays. In an Active Directory network, NetScanTools Pro can find all shared folders, even hidden ones. The utility generates TCP, UDP, ICMP, CDP, and RAW packets with various parameters and can be used as a flooder.
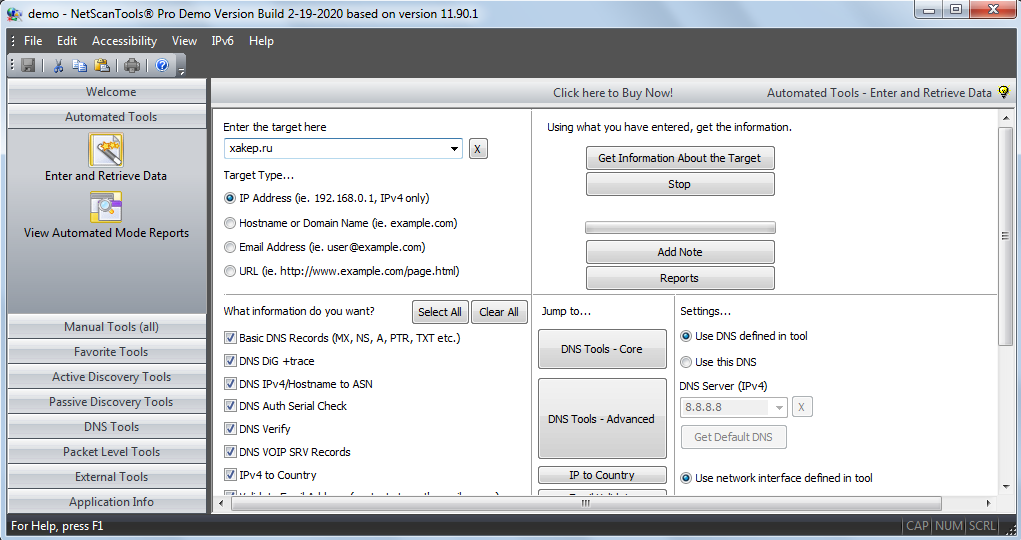
Overall, NetScanTools Pro is a useful utility combining active and passive network scanning tools. However, the price of $249 seems excessive taking that free NetworkMiner and Nmap offer basically the same set of functions. You can download a trial version from the official website, try it, and make a reasoned decision whether to look for a crack bundle of bucks or continue using freeware programs.
X probe
- Official website: https://sourceforge.net/projects/xprobe/
- Platform: GNU/Linux
This Linux utility employs active fingerprinting techniques and uses the same methodologies and scenarios as Nmap. Most importantly, X probe can detect honeypots (i.e. decoy servers deployed to lure and expose unsuspecting hackers) and suspicious nodes with altered TCP/IP stack configurations.
Fuzzy logic algorithms embedded in X probe allow it to detect services hidden behind a firewall. The utility identifies operating systems running on remote hosts using ICMP requests and scans TCP and UDP ports. Too bad, its last version was released in 2014, and the project hasn’t evolved much since then.
Ettercap
- Official website: https://www.ettercap-project.org/
- Platform: GNU/Linux
This sniffer is widely known in hackers’ narrow circles as a tool frequently used for MiTM attacks. Ettercap supports nearly all Linux versions (except for OpenSuSe) and UNIX/BSD platforms (except for Solaris). Some geniuses have reportedly launched Ettercap on macOS, but their names are kept in secret for security reasons.
Similar to other sniffers, Ettercap supports Telnet, FTP, IMAP, SMB, LDAP, and some other protocols; it also intercepts encrypted traffic transmitted through HTTPS and SSH. Although the tool was primarily developed for MiTM attacks, it can identify operating systems using fingerprinting techniques and detect IP addresses, open ports, running services, adapter types, and MAC addresses of network interfaces.
Ettercap sniffs the network traffic and saves the results in specially created profiles from where you can extract the data for analysis. The results of this analysis include the host’s IP address, name, and type, its supposed OS, open ports, and running services. This is more than enough to determine the initial attack vector.
THC Archive
A large archive of useful utilities and exploits is available on GitHub. The software was collected by a team of malefactors enthusiasts called The Hacker’s Choice established back in 1995 and still remainining active.
The guys offer plenty of exciting projects; for instance, the section https://github.com/vanhauser-thc/THC-Archive/tree/master/Tools contains the Amap scanner able to detect services running on nonstandard ports.
Some naive system administrators try to protect themselves against attacks by launching various services, such as FTP servers, SSH, or Telnet, on nonstandard ports. Amap easily ruins their efforts.
Most scanners knock on the standard ports, analyze the responses, and give up if these responses don’t meet their expectations. By contrast, Amap scans the entire range of ports and matches the responses against its database. As a result, services running on nonstandard ports are identified by their unique features contained in their responses.
To simplify your life, you can use Amap in combination with any other scanner. The scanner detects open ports on the target host, and then Amap checks these ports and identifies services running on them. Both Windows and Linux versions of Amap, including old ones, can be downloaded from The Hacker’s Choice page.
Conclusions
Now you are familiar with seven actual and extremely useful utilities whose capacity goes far beyond the OS detection on remote hosts. I strongly recommend spending some time and effort on in-depth research of the above programs. This will enable you to select optimal tools for your hacking pentesting purposes.
