warning
This article is intended for security specialists operating under a contract; all information provided in it is for educational purposes only. Neither the author nor the Editorial Board can be held liable for any damages caused by improper usage of this publication. Distribution of malware, disruption of systems, and violation of secrecy of correspondence are prosecuted by law.
To automate the setup procedure, I recently released a tool called F31. Let’s examine this Bash script in detail and see what it does.
Information presented in this article and F31 don’t provide a 100% guarantee that you circumvent systems monitored by SOC; however, they significantly reduce detection risks. Each pentesting audit is unique, and it’s hardly possible to find a universal solution. I have no doubt that there are plenty of other ways to reduce noise on the air. But this article is focused just on the main aspects.
Above
Above is another tool written by your humble narrator. This is an invisible network protocol sniffer designed to search network equipment for vulnerabilities. Its operation is limited to traffic analysis, which doesn’t create any noise on the air.
Above supports the following protocols:
- L2: CDP, LLDP, DTP, 802.1Q Frames;
- L3: OSPF, EIGRP, VRRP, HSRP; and
- L7: LLMNR, NBT-NS, MDNS, SSDP, MNDP.
By the way, Above was recently included in Kali Linux! Now you can install it directly from Kali repositories:
sudo apt update && sudo apt install above
above --helpTo start traffic analysis, use the following command:
sudo above --interface eth0 --timer 250 --output-pcap vettel.pcap
where
-
--interfaceis the system interface;eth0 -
--timeris analysis duration; and250 -
--output-pcapis the traffic dump file: Above will write to it everything it finds.
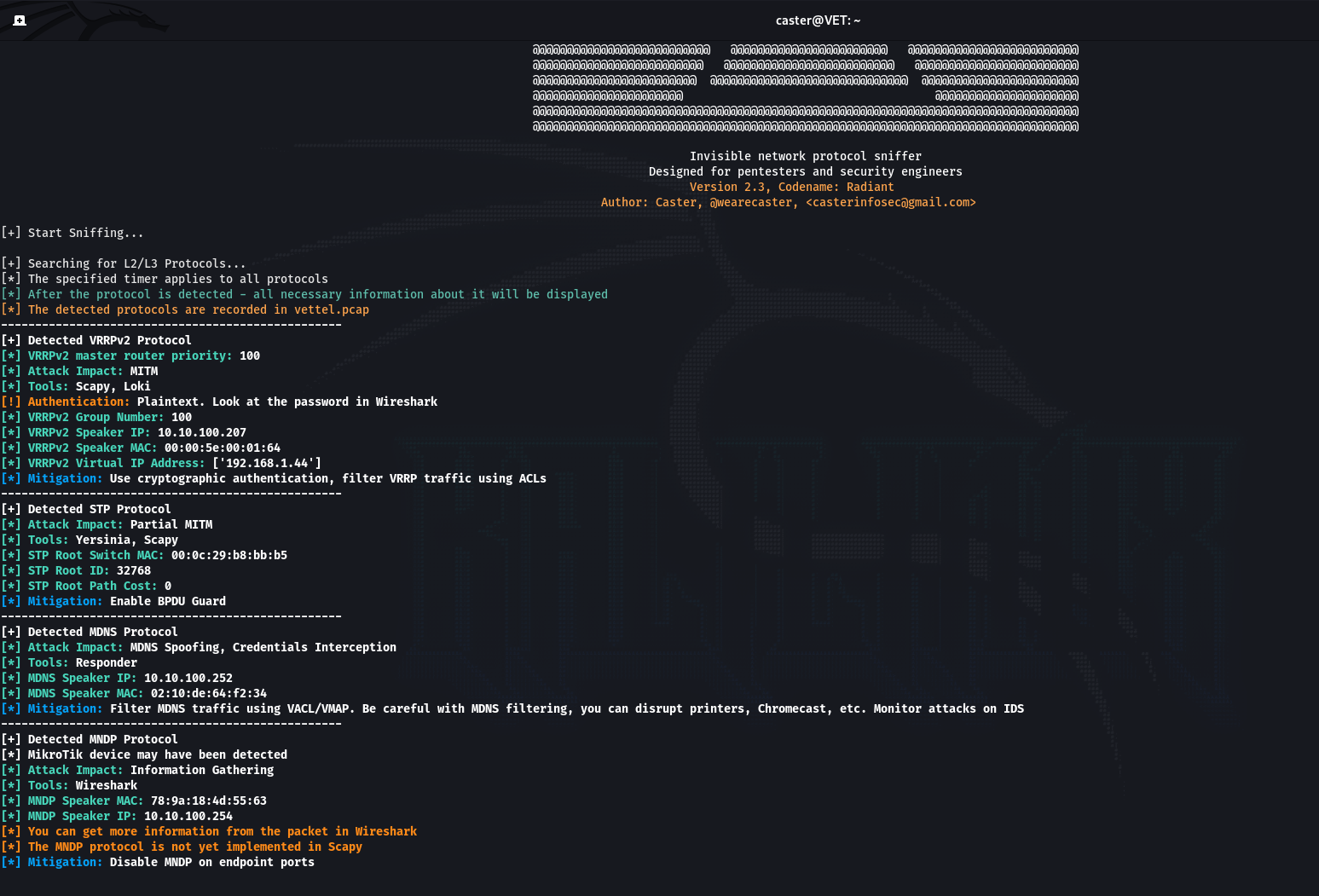
Above can be used to identify attack vectors suitable for the target network without creating any noise on the air.
Accessing repositories
If you access Kali repositories during a pentesting audit, SOC would immediately detect this. Even if you enable access to repositories via HTTPS, you can still be exposed by the DNS request.

Manipulations with system hostname
Yes, a recommendation to change the Kali hostname might sound like a joke. But the harsh truth is that the default Kali hostname is the main indicator used to detect this distribution on the network.
The solution is ridiculously simple: you change the system name and prohibit the transmission of its hostname in DHCP packets (that are sent when an attacker tries to receive an address on the network).
sudo hostnamectl set-hostname DESKTOP-HNA2AEVS
sudo sed -i "s/127.0.1.1.*/127.0.1.1tDESKTOP-HNA2AEVS/" /etc/hosts
To disable the transmission of the system name via DHCP, add the dhcp-send-hostname=false parameter in NetworkManager connection files:
sudo sed -i '/[ipv4]/a dhcp-send-hostname=false' /etc/NetworkManager/system-connections/Wired connection 1
TTL
In Linux distributions, the TTL value is 64. But you can change the default TTL value in the system. For instance, if you want to impersonate Windows, set TTL to 128.
sudo sysctl -w net.ipv4.ip_default_ttl=80
If you intend to deliver a MITM attack on the network, you can hide your address in the traceroute from legitimate hosts. The trick is very simple: you change TTL with an increment of +1:
sudo iptables -t mangle -A PREROUTING -i eth0 -j TTL --ttl-inc 1
Disabling NTP
Your system can access the NTP server on a regular basis to synchronize the current time. In Kali, NTP is periodically accessed via DNS.
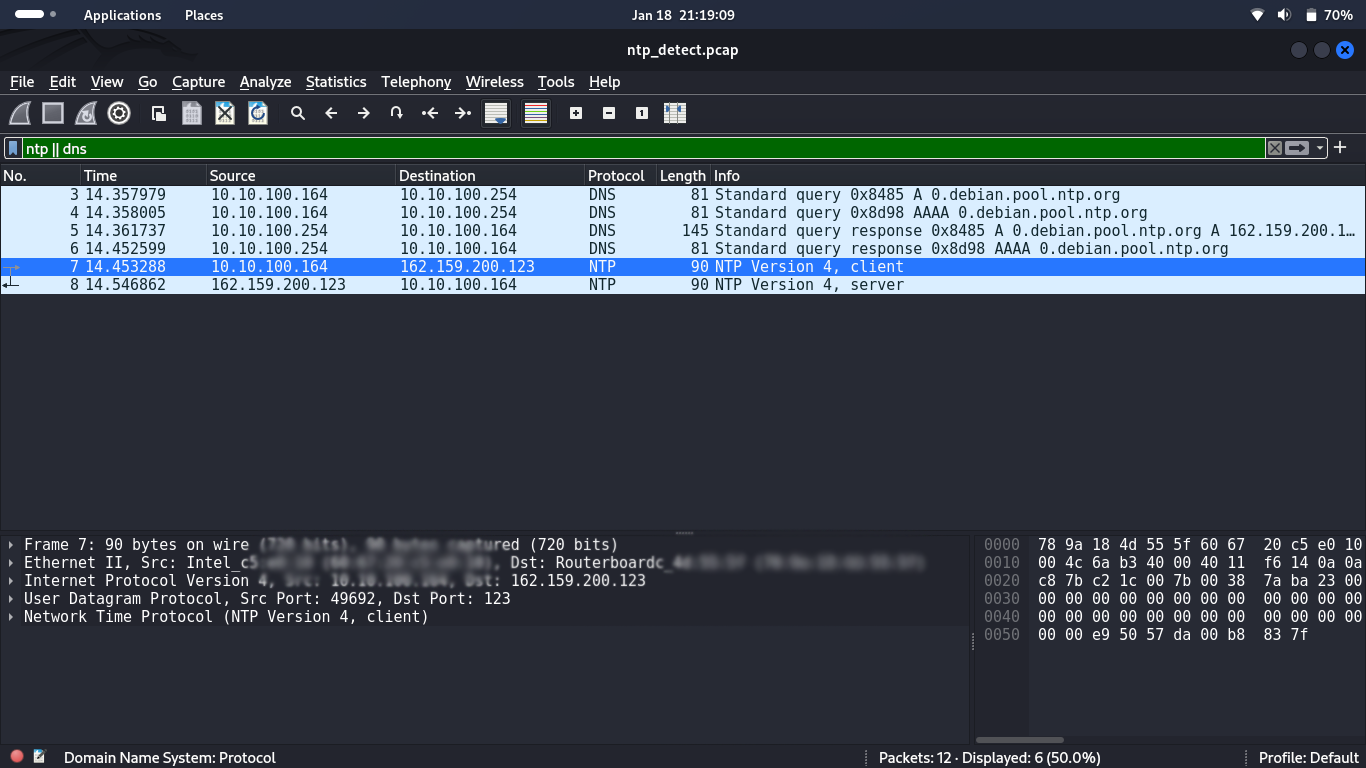
Good news is that time synchronization in Kali can be easily disabled:
sudo systemctl stop systemd-timesyncd
Netfilter
Your goal is to allow established and interrelated connections, block invalid ones, and block TCP segments with suspicious TCP MSS values. Also, you have to filter ICMP traffic and disable pings. Important: make sure you don’t accidentally block ICMP Type 3 that enables the PMTUD system to avoid excessive fragmentation.
sudo iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
sudo iptables -t mangle -A PREROUTING -m conntrack --ctstate INVALID -j DROP
sudo iptables -A INPUT -p icmp --icmp-type 0 -m conntrack --ctstate NEW -j ACCEPT
sudo iptables -A INPUT -p icmp --icmp-type 3 -m conntrack --ctstate NEW -j ACCEPT
sudo iptables -A INPUT -p icmp --icmp-type 11 -m conntrack --ctstate NEW -j ACCEPT
sudo iptables -A INPUT -p icmp -j DROP
sudo iptables -t mangle -A PREROUTING -p tcp -m conntrack --ctstate NEW -m tcpmss ! --mss 536:65535 -j DROP
info
If you limit ICMP traffic on your host, this can affect ICMP scanning. Keep this in mind and monitor the types of ICMP messages that are filtered out.
Disabling ICMP Redirect
ICMP redirects occur during MITM attacks. ICMP redirect messages can trigger IDS/IPS systems, thus, compromising the attacker’s actions. Let’s disable these messages.
sudo sysctl -w net.ipv4.conf.all.accept_redirects=0
sudo sysctl -w net.ipv6.conf.all.accept_redirects=0
Randomizing MAC address
Classics of the genre: changing the MAC address on your interface. I assume this trick doesn’t require elaboration.
sudo ifconfig eth0 down
sudo macchanger -r eth0
sudo ifconfig eth0 up
You can also configure NetworkManager so that your MAC address changes to a random value every time you connect to the network.
echo -e "n[connection]nwifi.cloned-mac-address=randomnn[connection]nethernet.cloned-mac-address=random" | sudo tee -a /etc/NetworkManager/NetworkManager.conf
Noise minimization
Pentesters extensively use scanners (Netdiscover, Nmap, etc.) in their work. When these scanners are run with default settings, they create much noise on the air. As a result, detection risks increase, and there is a chance to overload the network switch (especially when it comes to fast ARP scanning). In addition, the Storm Control system (that controls UCAST/MCAST/BCAST traffic) can raise the alarm.
I found a way to minimize noise on the air by restricting the bit rate on the system interface. You can reduce it to 30 kb/s and set latency to 800 ms; as a result, Netdiscover won’t cause overload on the air. Of course, such a fix affects the scan speed and data transfer rate, but it allows you to avoid overload. The above values were determined experimentally; feel free to adjust them if necessary.
For traffic shaping, I used the tc (traffic control) utility:
sudo tc qdisc add dev eth0 root tbf rate 30kbit burst 30kbit latency 800ms
The screenshots below show the Netdiscover and Nmap scanners in action. The commands were as follows:
sudo netdiscover -i eth0
sudo nmap -n 10.10.100.0/24
Pay attention to the Outgoing section: the nload utility shows outgoing traffic.


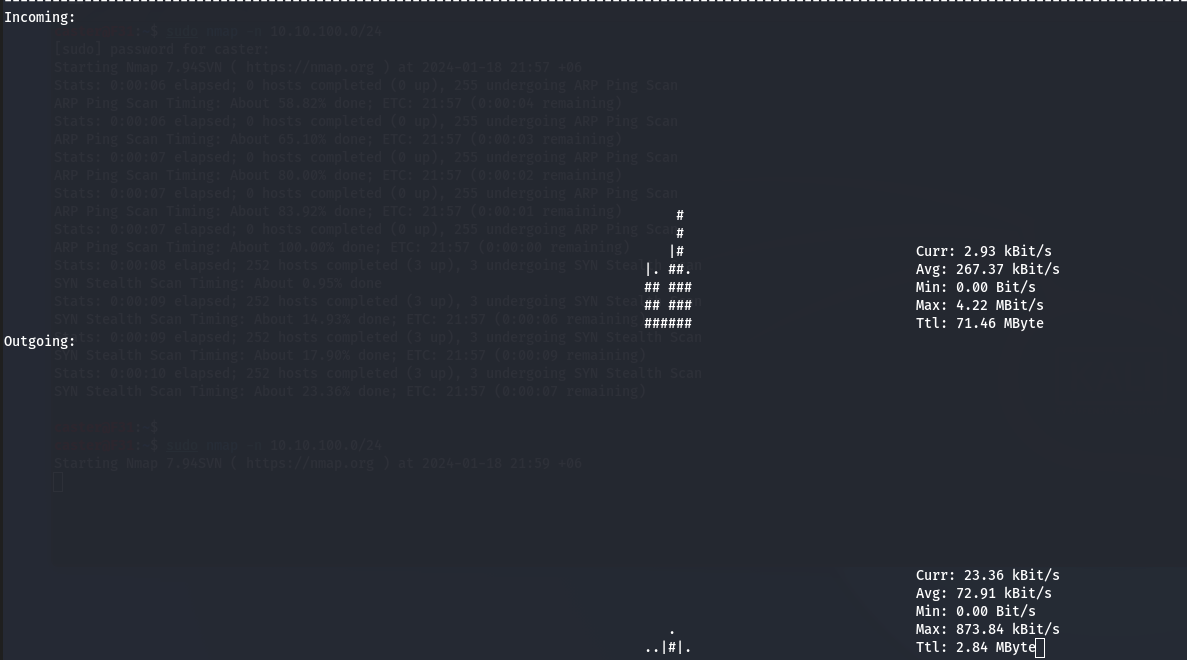
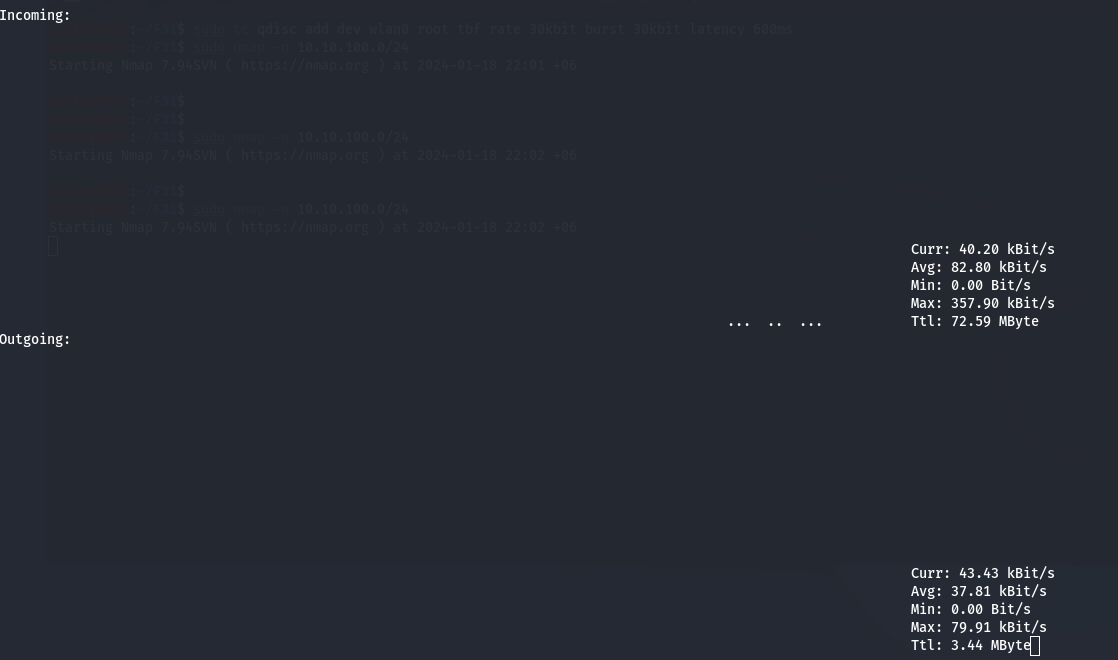
To delete traffic shaping settings, use the following command:
sudo tc qdisc del dev eth0 root
F31
The F31 script automates the entire setup process. It’s fully customizable and must be run with special arguments.
sudo bash F31.sh
███████ ██████ ██
██ ██ ███
█████ █████ ██
██ ██ ██
██ ██████ ██
F31: Tool for hiding Kali Linux on the network
Author: Caster, @wearecaster, casterinfosec@gmail.com
Version: 1.0.0
For instructions and an example of how to use it, visit: https://github.com/wearecaster/F31
Usage: F31.sh –interface
Options:
–interface Specify the network interface to hide
–new-hostname Specify the new hostname for the system
–noise-reduction Enable traffic shaping for noise reduction (optional)
sudo bash F31.sh --interface eth0 --new-hostname DESKTOP-HNA2AEVS --noise-reductionTo revert all changes, I wrote a script called reset.; you can find it in the F31 repository:
sudo bash reset.sh --interface eth0 --old-hostname kali
Conclusions
Now you are familiar with the main techniques used to minimize noise on the air and harden Kali Linux. At all stages of Kali Linux setup, the main focus is put on the network level. It’s hardly possible to write a comprehensive SOC circumvention manual, and, of course, it’s impossible to fit all information into a single article. In the future, I intent to continue the Kali Ashes series. See you soon!
