The first thing you might want to try is using Windows tools to fix the errors. To do this, open the command prompt as an administrator and type:
chkdsk f: /f
Naturally, you’ll need to replace “f:” with the current drive letter. The /f parameter indicates that errors should be fixed during the scan.
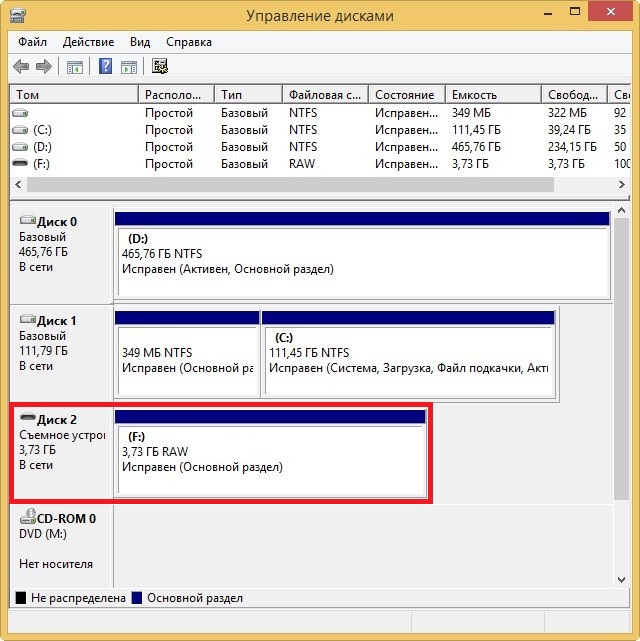
If the operation was successful, you can try opening the files. However, you might encounter the error “Chkdsk is not available for RAW drives.” Don’t worry, we have a couple of other options up our sleeve. Let’s use a specialized program called DMDE.
DMDE is an impressive program that’s useful for searching, editing, and recovering data on disks. The developer claims it employs advanced algorithms that enable it to restore directory structures and files in complex situations where other programs may not succeed.
DMDE includes a disk editor, a basic partition manager, and the ability to create images and clone disks, as well as reconstruct RAID arrays, among other features. The paid versions support unrestricted file and directory recovery, but the free version is also quite effective and helpful in many situations.
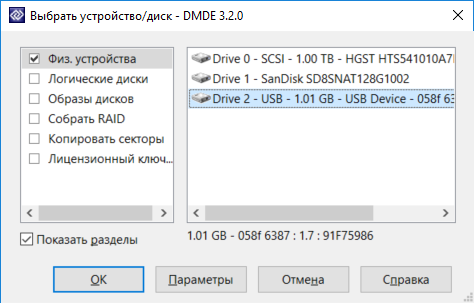
After launching the program, select your storage device.
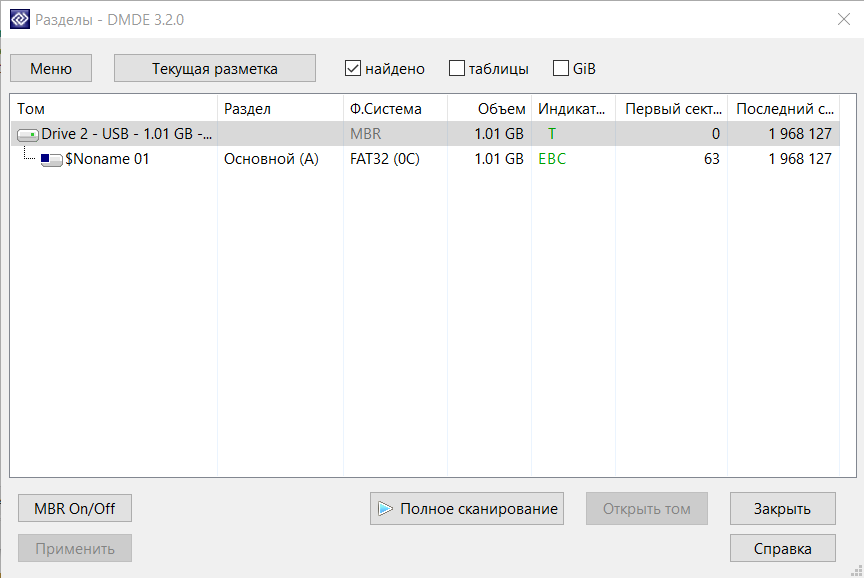
A window with sections opens, where we select full scan by double-clicking.
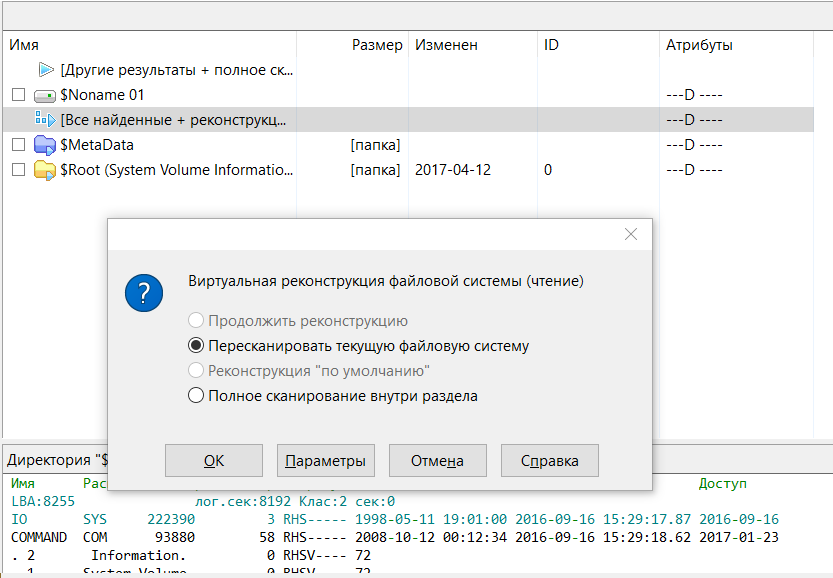
After the quick scan, navigate up to the “Found” folder and click on “All found + reconstruction.” A dialog box will open where you should select “Rescan the current file system” and then wait for the operation to complete.
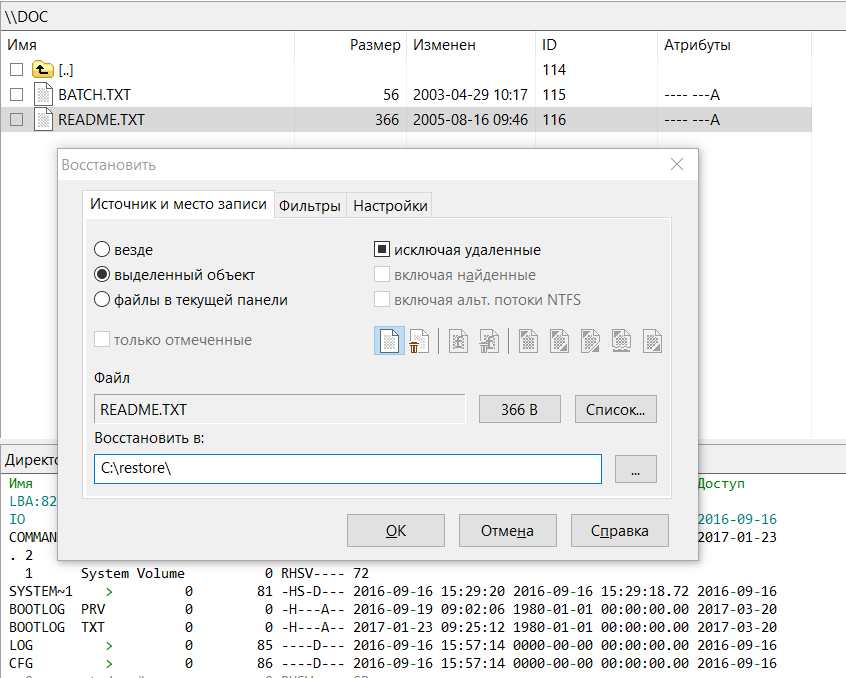
After scanning, DMDE will display a list of found files. Browse through the folders and select what you want to recover. Unfortunately, the free version does not allow you to recover entire folders. To recover individual files, right-click on the file, select “Restore Object,” then specify the destination for recovery and click OK.
It is worth noting that file names are generated automatically and often do not match the originals. Don’t be surprised if some files are “corrupted” or if artifacts appear in the photos. Interestingly, images can sometimes be restored using special utilities. For example, Recuva or R-Studio. To my great surprise, the last program managed to restore almost completely damaged photos to a very good quality with minimal artifacts—many of its competitors failed to achieve this.
In summary, good luck with the recovery! However, it’s best to immediately transfer all data from temporary storage and create backups.