warning
This article is intended for informational purposes only and is designed for security professionals conducting testing under a contract. The author and publisher are not liable for any harm caused by the misuse of the information provided. The distribution of malware, disruption of systems, and breach of communication privacy are subject to legal penalties.
The standard firmware significantly limits the potential of Flipper Zero. It restricts the interception and analysis of specific frequency signals, such as car alarm signals, and does not support brute-force attacks on protocols that require transmitting specific values. Additionally, it includes a limited number of built-in signals suitable for attacks on popular systems.
The device’s architecture is open, meaning you can install your own firmware, which broadens experimental possibilities. Since the device launched, numerous third-party and community-developed firmware options have emerged, each offering its own unique features and advantages. Let’s take a closer look at them!
Flipper Zero Firmware
Flipper Zero Firmware is the default software that comes pre-installed on the Flipper Zero device when it leaves the factory. It includes a variety of tools but has built-in limitations that prevent users from fully unlocking the device’s technical potential.
The firmware will be useful for those who have just purchased a Flipper Zero and want to explore its basic capabilities for everyday use. For instance, you can clone all your access cards and remote controls into it, so you don’t have to carry them around daily.
Here are the four sections of the standard firmware that will most significantly vary in custom versions.
- Sub-GHz — This section enables the interception, recording, and emulation of radio signals. In the standard firmware, this tool has limited capabilities. For instance, when trying to intercept a car key signal, the device may detect it but won’t allow it to be recorded or replayed. This limitation is intentional, as in the wrong hands, this tool could be dangerous.
- Infrared: Infrared signal. Enables control over household appliances. The standard firmware supports four types of devices: TVs, audio players, projectors, and air conditioners.
- BadUSB: Allows emulation of a wired keyboard when connecting the “Flipper” to a PC. Includes two demo scripts that open Notepad on the connected PC and display the “Flipper” logo as ASCII art.
- Applications: Contains additional tools not included in any of the previous categories. In the official firmware, this section is primarily notable for allowing you to play the game Snake.
Unleashed
Unleashed is the first fork of the official firmware that removes regional restrictions from the Flipper Zero and adds new tools. It is available in two versions: the basic version and an extended version, which includes a large number of pre-installed applications.
Unleashed is ideal for those who find the basic features of Flipper Zero insufficient. For instance, with this firmware, you can not only intercept, record, and replay signals, but also perform brute-force attacks on systems.
Here, you have access to tools that can automatically cycle through all possible access codes to open a barrier, ensuring it can be opened without intercepting the original signal. In contrast, the official firmware only allows you to record an existing signal and emulate it later.
In the Sub-GHz section, all regional restrictions on signal frequencies have been removed. This means that with the use of Unleashed, you can intercept and emulate virtually any signal that the hardware of the Flipper Zero can access.
Among other things, the Applications section of this firmware is packed with a wide array of tools for all kinds of scenarios: from a unit converter and a barcode generator to a Brainfuck development environment and a Doom remake.
By the way, if you’re not a fan of the name “Flipper” that it comes with from the factory, Unleashed, along with the other unofficial firmware options mentioned in this article, can help you change it.
In other sections, there are also many minor changes. For example, support for classic Mifare keys has been added, along with features for capturing and sending dynamic encrypted protocols and rolling codes.
With the Unleashed firmware, your “Flipper” can now serve as a decent tool for a pentester. Just be careful not to misuse its capabilities, and remember that certain actions can be illegal!
Xtreme
Xtreme is perhaps the perfect balance between the standard firmware and the RogueMaster fork. Essentially, it is a thoroughly revamped official firmware with features borrowed from RogueMaster, but it is significantly more stable.
The main unique innovation is the extensive customization options available for BadUSB/KB. You can also add new features for our “Flipper” (remember, it’s also a virtual pet?), adjust USB/BT modes to work with BadUSB, and manage Sub-GHz protocols. Like the Unleashed firmware, this version allows you to bypass all regional restrictions, perform brute-force attacks, and includes not only all its advantages but also some new features.
The BadKB function enables keyboard emulation to perform HID attacks. You can use an existing script as a base, which displays a “Flipper” greeting through a text editor on any operating system, including Windows, macOS, iOS, Android, and others. It supports Ducky Script Language 1.0. If you search on GitHub, you’ll find over 500 ready-made payloads using it.
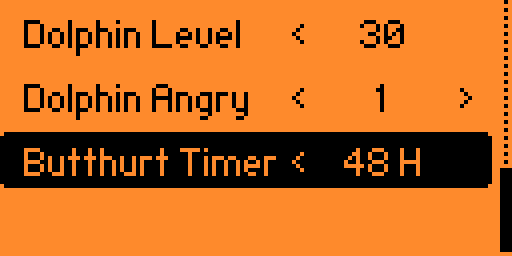
The BadKB has two operating modes: a classic (wired) mode and a Bluetooth mode. The Bluetooth mode can be configured so that the “Flipper” device remembers devices. In subsequent attacks, it will automatically connect to the victim. There’s also the ability to change keyboard layouts and even the MAC address of your cyber dolphin’s BT module.
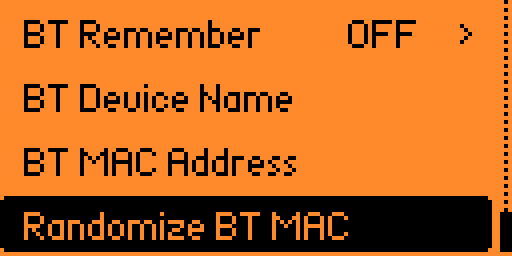
This firmware is designed for advanced users who have a clear understanding of why they need Flipper and all its new features. It is particularly well-suited for physical penetration testing and comprehensive red teaming exercises.
RogueMaster
RogueMaster is a fork of the Unleashed firmware, which is quite similar to the original, but features a unique set of animations. Some of these animations are available for purchase through a Patreon subscription to the creator, RogueMaster.


The new features are similar to those in the Xtreme firmware, except that the BadUSB parameters are somewhat limited (there are no Bluetooth settings like in Xtreme). Additionally, this firmware is less stable compared to others we’ve reviewed. It had the highest crash rate in our tests.
The Application section here is essentially a massive list of tools. You can find various fuzzers for iButton, brute-forcers for RFID and Sub-GHz, as well as a CLI mode. However, I advise caution when using the command line—out of ten attempts I made, three caused the system to crash.

Overall, support for FAP format applications is expected to be included in the main Flipper firmware soon. As a result, RogueMaster will mostly appeal to those who want to practice debugging and study source codes on their own. Alternatively, you might consider installing it if you’re eager to customize your Flipper Zero’s “passport” by changing not only the avatar but also the background.
| Standard | Unleashed | Xtreme | Rogue Master | |
|---|---|---|---|---|
| Regional Restrictions Disabled | – | + | + | + |
| Interface Customization | – | – | + | + |
| Additional Modules | – | + | + | + |
| Operational Stability | + | + | + | – |
| Update Relevance | – | +/– | + | + |
| Doom | – | + | + | + |
Recommendations
After several months of testing and daily use of the Flipper Zero with custom firmware, we can offer some recommendations on choosing the right one for you. First and foremost, decide how you plan to use the device. If you truly intend to conduct advanced attacks (for entirely benign purposes or under a testing contract), then select firmware that provides the necessary features. If such capabilities are not required, there’s no need to compromise the device’s stability.
The best way to start exploring the optional features of the Flipper Zero is to install the extended Unleashed version or the official firmware that includes tools and modules relevant to your needs (many of which are already available in the official Flipper Zero repository).
If you’re into customization, your best options are Xtreme or RogueMaster. However, if stability and advanced features are more important to you, then Unleashed or Xtreme are the way to go. We’ve chosen these two because they are the most stable and practical systems. Throughout our testing and use, they never crashed or hung, unlike RogueMaster. They offer plenty of features, and with Xtreme’s menu-based firmware customization, there’s an added bonus.