No‑Holds‑Barred Marketing
Modern web development tools make it easy not only to build great web services, but also to cash in through less-than-legal means. Intrusive ads, browser settings hijacking, and JavaScript miners hidden in page code—all of these are byproducts of the relentless pursuit of profit.
You can mitigate this on the client side with filtering. The simplest approach is to add known sources of deceptive ads, phishing sites, and other online junk to the hosts file, forcing them to resolve to localhost instead of their dubious remote IP addresses.
The advantage of this approach is that it doesn’t depend on which browser you use. Localhost is shared by all applications and works on any modern OS. For example, the open-source app AdAway can block ads on rooted devices running Android 4.1 or later.
Another popular approach is to use browser extensions that filter content. Among these ad blockers, AdBlock and its counterparts have become especially popular.
No Pop-Ups!
The most annoying ads are now filtered at the browser level. By default, Chrome, Firefox, Safari, and Edge block pop-up windows. Browsers have also been blocking Flash for years, since it was often used to track user activity, and Flash Player itself was riddled with security vulnerabilities.
Starting with version 53, Chrome tries to load a Flash-free version of a page first, and other browsers have followed suit. Safari, starting with version 11, blocks autoplaying video. Features like this are increasingly common. So before you install any blocker, check your browser settings—some annoyances can be suppressed with built-in tools.
Why AdBlock Isn’t What It Used to Be
Many people confuse AdBlock with Adblock Plus, assuming the latter is a more advanced version of the former. In reality, their origins are much more tangled. Here’s what actually happened…
The first version of an extension called AdBlock for Firefox was written by Henrik Aasted Sørensen in 2002. As the name suggests, it only worked in Firefox. Due to limitations of the browser engine, AdBlock for Firefox struggled with in‑stream video ad inserts, and its interface was pretty bare-bones. A couple of years later, a fork called Adblock Plus appeared, improving many aspects. Partly because of that, development of the original AdBlock for Firefox was put on hold in 2006.
After a three-year lull, a different developer—Michael Gundlach—built on the work done in Adblock Plus, took the original project’s name, AdBlock, and released his own ad blocker in 2009.
The new AdBlock is a fork of a fork, sharing little with its namesake original. It was released as an extension for Chrome, Firefox, Safari, Opera, and Edge. Its selling points include broad compatibility, a fully redesigned interface, and support for Adblock Plus filter lists thanks to a compatible format. However, not all of these changes were well received by users or website owners.
Ad blocking in AdBlock sometimes behaves oddly. For example, the screenshots below show what the Echo of Moscow website looks like when visited with no blockers and with AdBlock enabled.
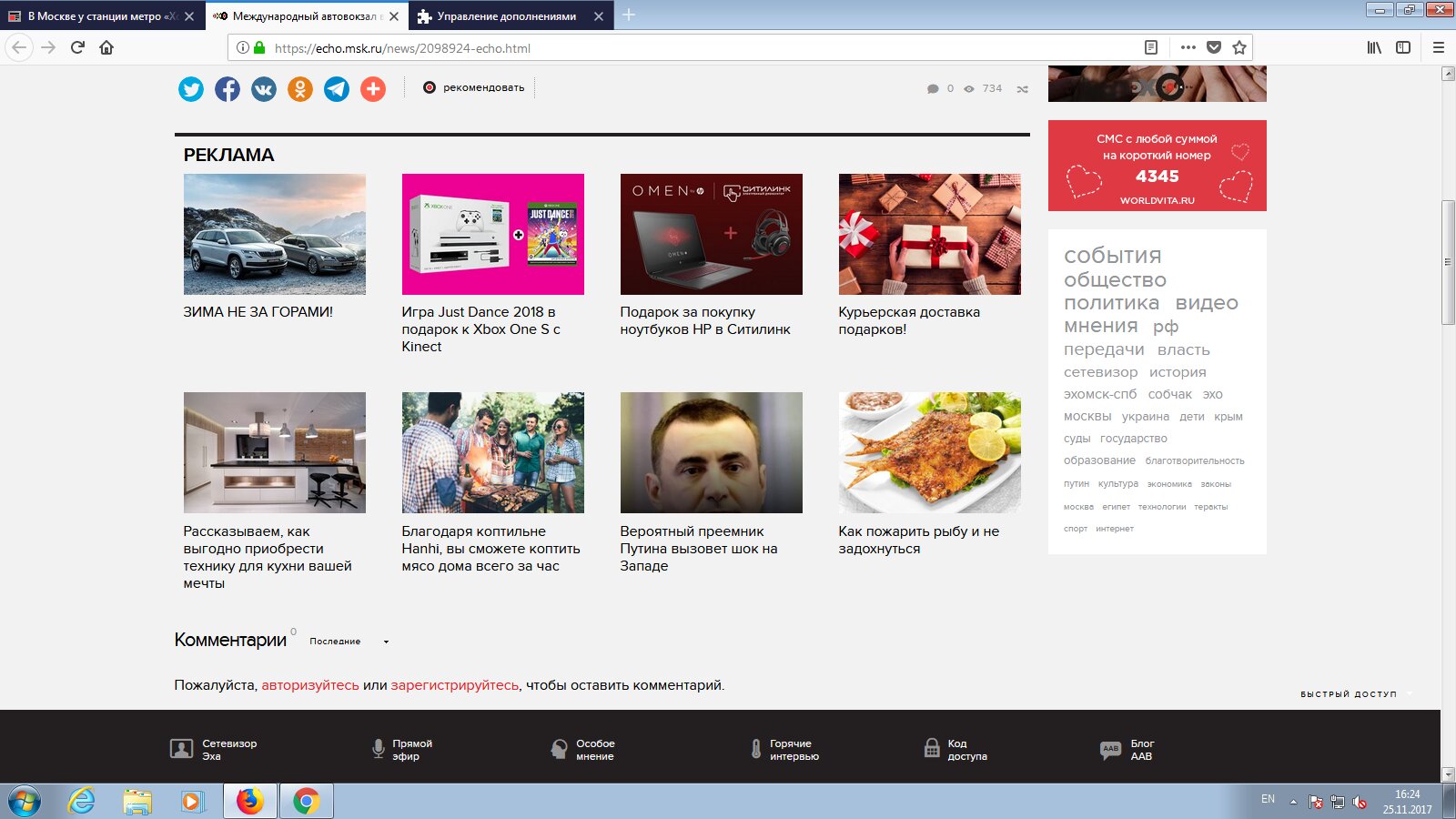
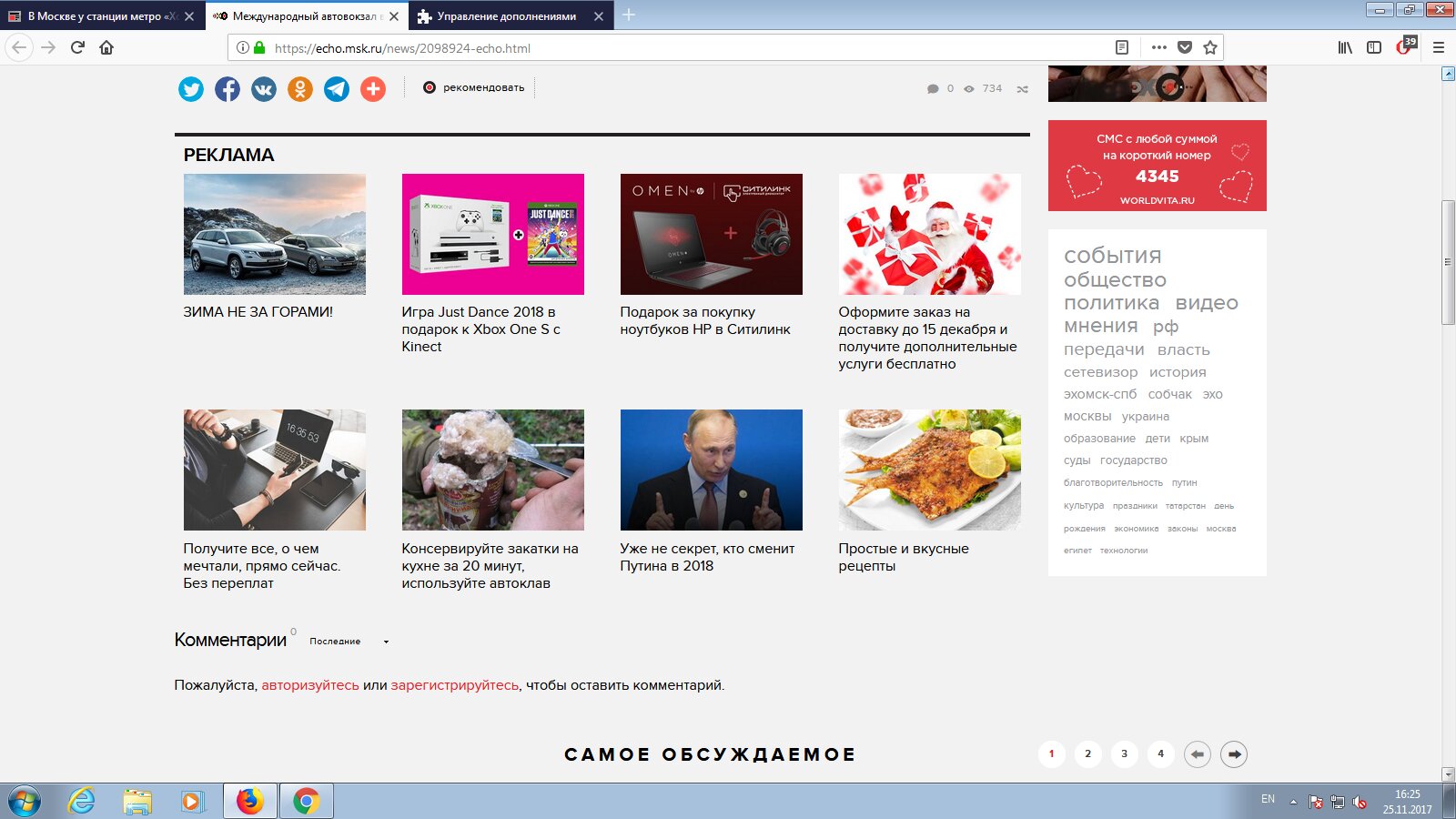
See any difference? I don’t either—yet AdBlock’s counter says there is.
On the REN TV site (yes, we deliberately picked the juiciest pages), it’s a different story. Visit it without an ad blocker and you’re in for a shock: the ads pour in so heavily you can’t fit them into a single screenshot.
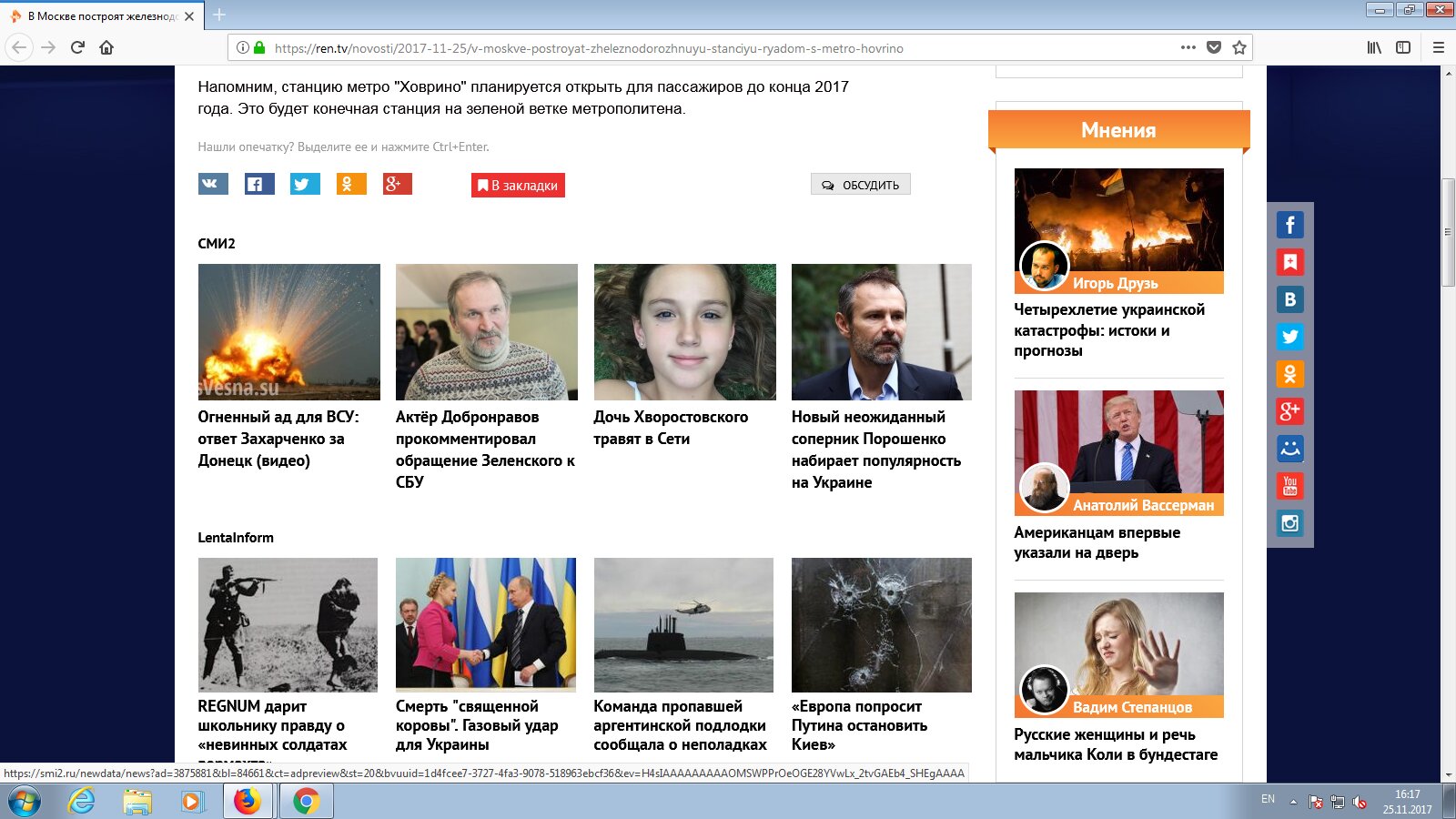
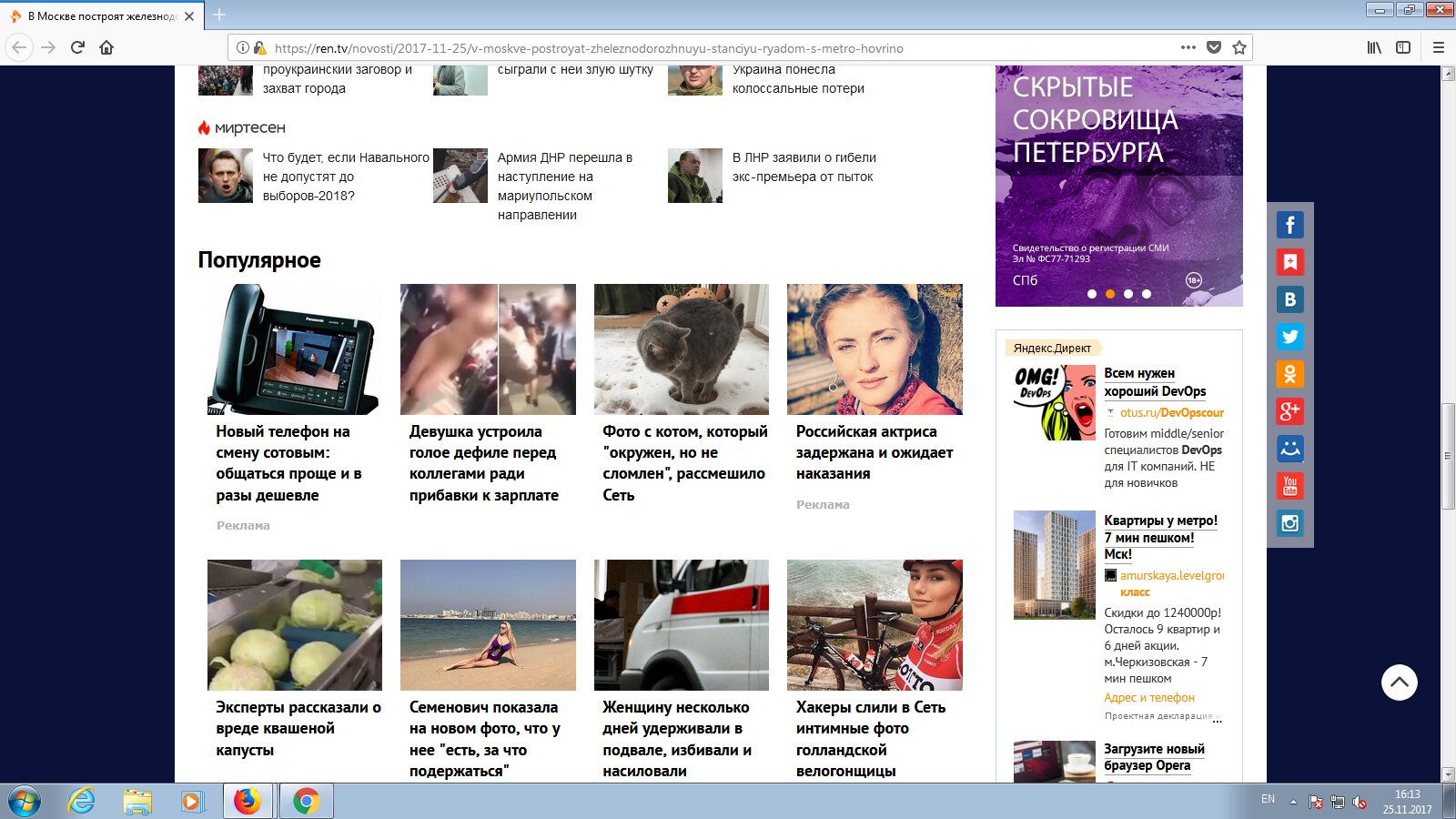
As soon as you enable AdBlock, entire sections get stripped out and the page collapses vertically, yet some ads still slip through.
Ad blocking as a revenue stream
Advertising runs on multi‑million‑dollar budgets, which naturally raises the question: why do people build AdBlock clones and then maintain them for years? It’s unlikely they’re driven purely by altruism. Blocking ads can simply be more lucrative than serving them. According to estimates from Quora users, AdBlock was bringing its developer between 25 million a year just from voluntary donations.
How much they actually raised through the donation-based freemium model hasn’t been officially disclosed. Technically, though, there are also more covert ways to monetize. For example, the new AdBlock can not only block ads but also replace the removed banners with anything. In 2012, Gundlach started swapping them for photos of smiling cats (explained as an overlong April Fools’ prank), and by 2016 those banners were being replaced with links to articles about Snowden and other Amnesty International advocacy. As the saying goes, your ad could be here.
At this point, Gundlach has stepped away from development, and AdBlock’s growth is led by Gabriel Cubbage and Antoine Boegler. The details of that deal were never officially disclosed, but talk of AdBlock being sold for a substantial sum has been around since 2015. Meanwhile, AdBlock relies on volunteer contributions. Dozens of people continue to provide translations for free and help improve the product.
Adblock Plus
Today, the Adblock Plus extension is available for Chrome, Firefox, Safari, Opera, and Edge. It’s one of the most popular ad blockers, with over 100 million downloads. It can selectively filter ads (including video ads), disable social media buttons, prevent navigation to phishing sites, and protect users from tracking via analytics and ad tags. However, it also requests a substantial set of permissions—much more than comparable alternatives.
Adblock Plus is distributed free under the GPLv3, but that doesn’t mean its owners aren’t making money. The developers behind this fork just use a different approach to monetization.
Eyeo, the company created to promote the ad blocker, is betting on whitelists. They’re enabled by default and include rules that allow “some non-intrusive advertising.”
Since 2011, Eyeo has worked with advertisers through the AAP — Acceptable Ads Platform. “Acceptable” ads can also be shown in place of those filtered out as “unacceptable.”
The developers of Adblock Plus openly sign contracts with ad networks that want their content added to the whitelist. Officially, they must undergo a review and guarantee that their ads meet the acceptable-ads criteria, but those criteria are defined by Eyeo itself. Of course, blatantly intrusive ads are unlikely to pass moderation even for a hefty fee. A long-standing reputation is simply worth more than a one-time payout.
Some website owners view the practice of selectively blocking ads and replacing them with “acceptable” ones as unfair competition. Rather than join the Acceptable Ads Program (AAP), they file lawsuits—and sometimes they win. For example, the German publisher Axel Springer won a court ruling that required Adblock Plus to add its magazines to the whitelist free of charge.
In our tests, Adblock Plus performed on par with the other contenders, reliably stripping out ads. However, some sites simply refused to load until we disabled it. For more details, see the sidebar on the adwall.
How filter lists are compiled
All blockers rely on public blocklists of unsafe sites and sources of intrusive ads. These lists are maintained by different organizations, each with its own criteria for what to block.
Typically, a site or one of its components gets blacklisted after user complaints about intrusive ads or fraud. A site is also considered potentially dangerous when it’s flagged by a cloud-based antivirus scanning service—for example, by Google Safe Browsing or Norton Safe Web.
A list of popular blocklists with brief descriptions is available here. Many of them overlap, so you should merge them and remove duplicates before use. AdAway and modern blockers handle this automatically. You can use as many lists as you like—as long as they use the same format.
However, “permissible” doesn’t mean “recommended.” For most users, the two or three default lists are enough. There’s no point in piling on more, since an extensive catalog of blocked resources can slow the browser down.
It’s far more important to account for regional specifics. For example, ad lists targeting what bothers web users in Argentina are unlikely to be relevant to users in Russia. In practice, it’s more effective to use the default regional lists and add a few custom filters of your own than to try to bolt on as many prebuilt lists as possible.
AdBlock Alternatives
Beyond the revived AdBlock and its “Plus” fork, there are plenty of other ad blockers, but most are niche add-ons or rough knockoffs that fall well short on features. Still, there are some welcome exceptions.
uBlock Origin
In my view, uBlock Origin by Raymond Hill deserves a special mention. It uses more filter lists yet manages to consume fewer system resources than Adblock Plus. Here are the developer’s own benchmarks that back up the code’s quality.
uBlock Origin is highly configurable—more so than any other blocker I’ve used. It loads separate filter lists for standard and intrusive ads, for phishing and malicious sites, and includes both regional and general-purpose lists. Additional lists also block site tracking components to protect your privacy.
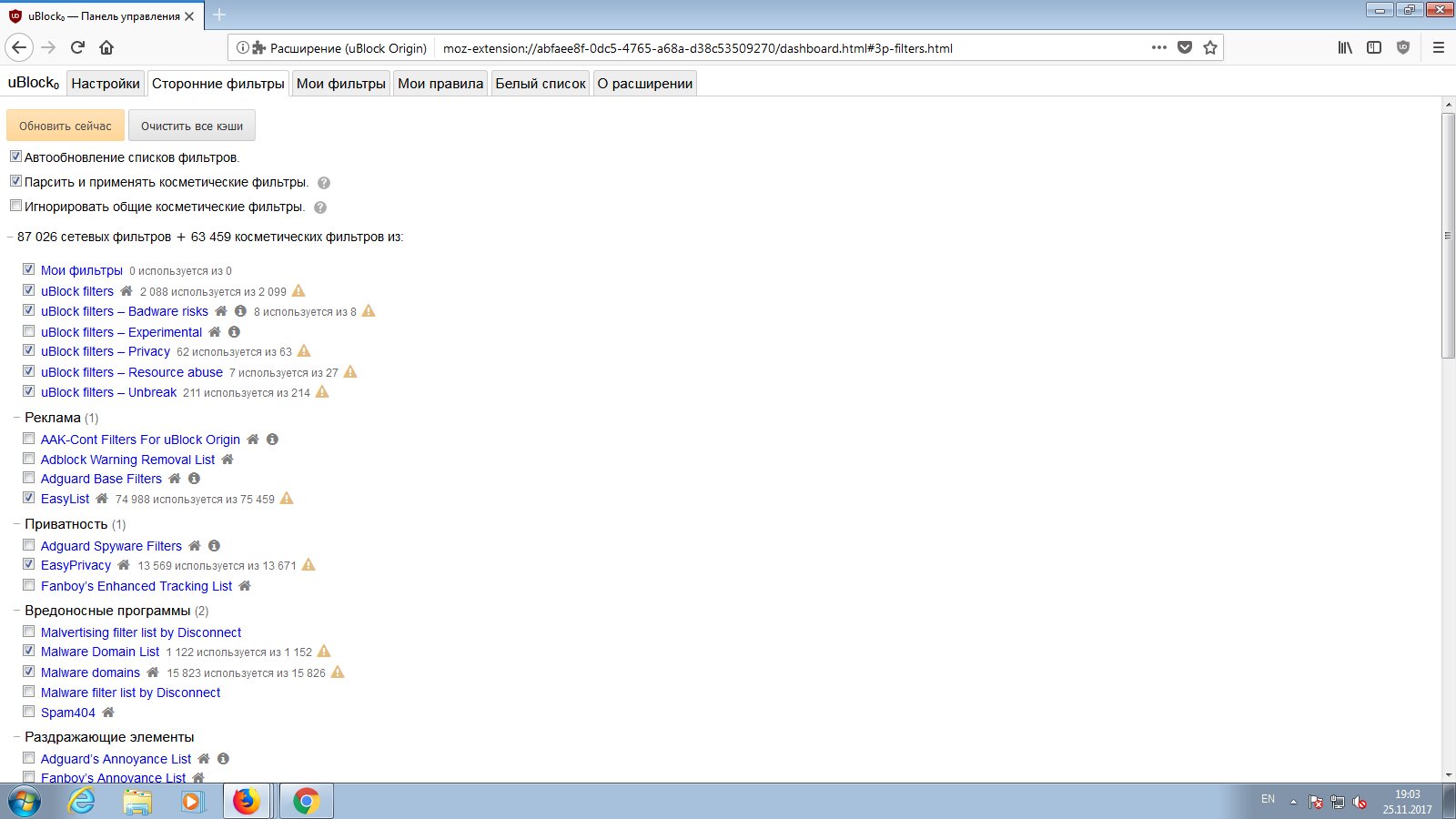
On top of that, uBlock Origin lets you independently configure pop-up blocking, prevent large media files from loading to save bandwidth, and enable “cosmetic filters.” These are essentially style sheets; without them, you’d just see empty boxes where elements were removed. They reflow the page on the fly, making it more compact by shifting the main content into the space previously occupied by ads. Other blockers offer similar features, but in my experience this works best in uBlock Origin.
You can easily set site-specific preferences and even disable uBlock Origin entirely or selectively—for individual pages on a site. It’s even simpler to allow or block requests to specific third-party sites. Just click the list of blocked items on the current page.
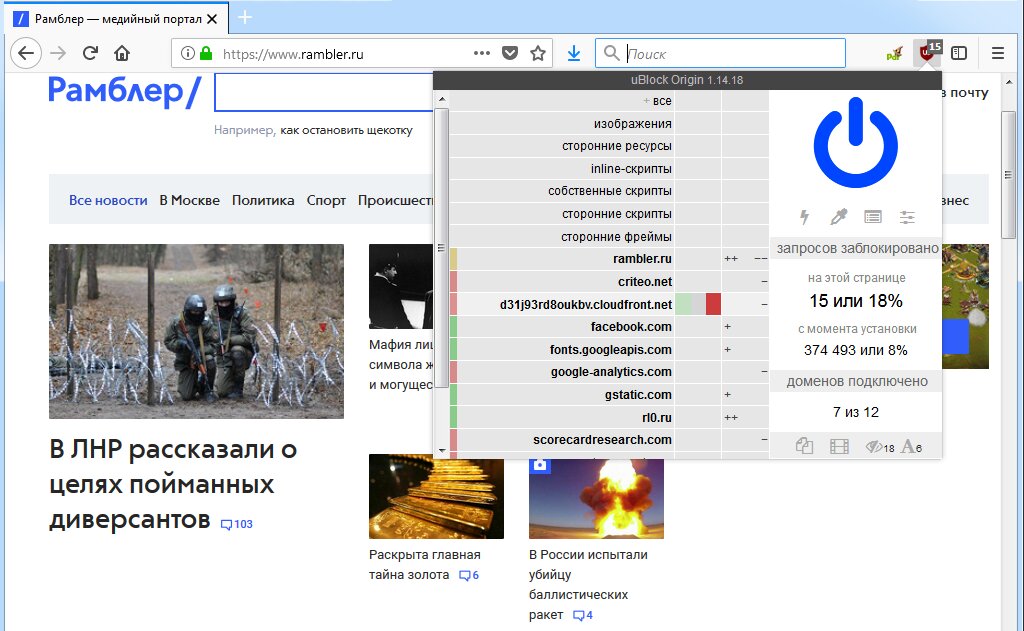
uBlock Origin has a whitelist as well. By default, it includes extension update sources and the behind-the-scene component. This is how uBlock labels any HTTP requests that can’t be associated with a specific browser tab. These include automatic updates for the browser and its extensions, search suggestion services, and other background/system traffic.
If uBlock Origin lets an ad slip through or you just don’t want to see a particular kind of page element, you can create a custom blocking rule. Open Element Zapper mode and click the element you want gone.
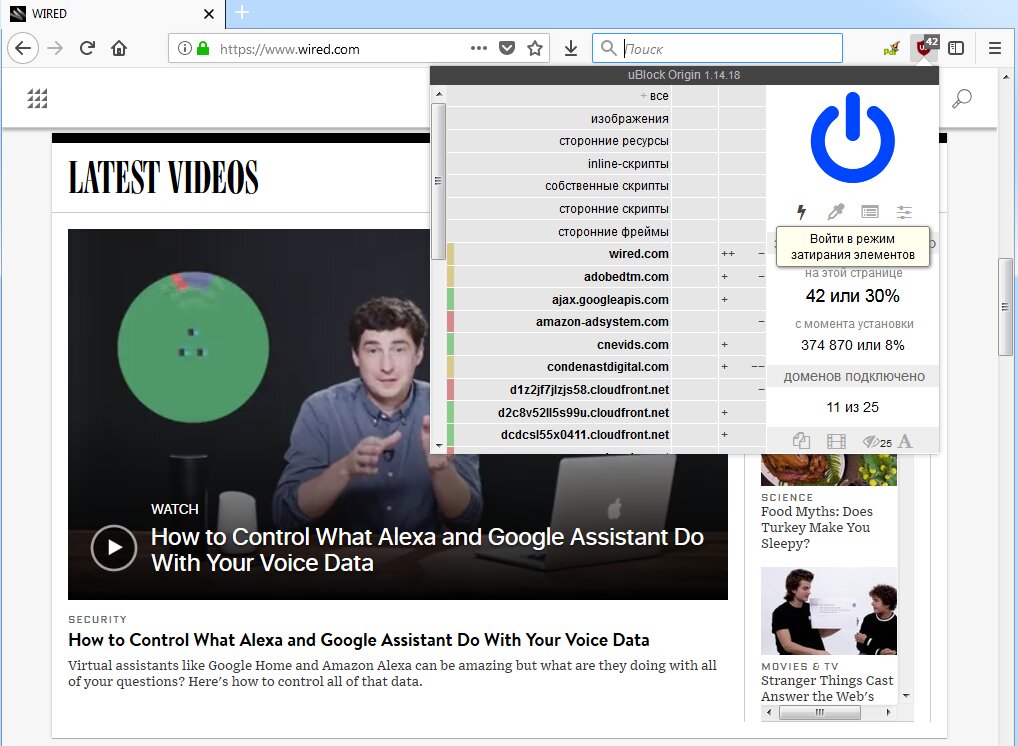
This way I could easily remove message boxes and video embeds on websites—not ads, just distractions.
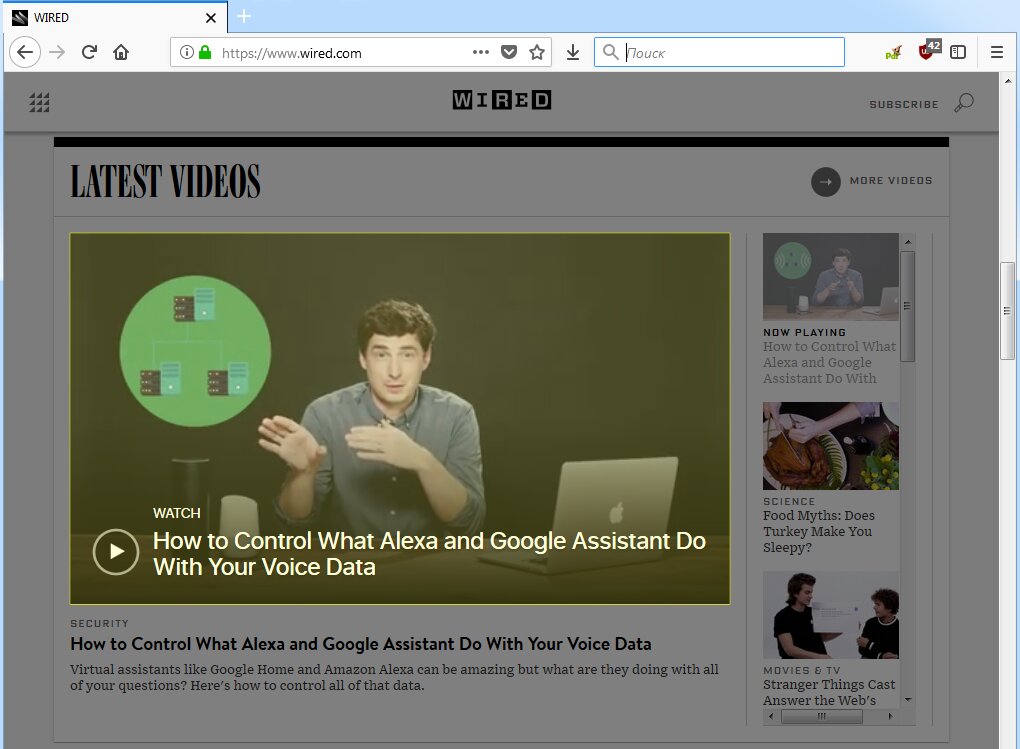
Advanced settings in uBlock become available after you check the “I am an advanced user” option. This enables dynamic content filtering, which primarily targets cross‑site requests to enhance privacy and security.
Starting with version 1.1.0.0, uBlock Origin supports cloud syncing of settings via Firefox Sync or a Google account. This lets you easily export all filtering rules configured on one device to others. You can also use the settings backup feature for the same purpose.
AdGuard
Before browser extensions were a thing, I used the AtGuard software firewall. On a dial-up connection in the ’90s it was a real lifesaver, because it dramatically cut down on traffic. AtGuard wasn’t an ad blocker per se, but it could freeze GIF animations and block scripts and ActiveX controls. That not only made browsing more pleasant, it also went a long way toward avoiding infections.
A lot has changed since then, and today two different products share the AdGuard name: a free browser extension authored by Andrey Meshkov, and a paid cross‑platform firewall developed by his company, AdGuard Software.
In this article, we’ll look at the “AdGuard AdBlocker” browser extension. It’s free and open source. Beyond standard and intrusive ads, AdGuard can block video ads on YouTube and other sites, as well as social media widgets.
“AdGuard Antibanner” is notable not only for blocking ads, but also for preventing the installation of spyware and adware. At the same time, it promotes the full AdGuard product (a separate application), whose installer by default tries to stuff your system with questionable bundled partner software—Yandex’s in particular. I reflexively unchecked those boxes before taking the screenshot.
info
If you’re reading this article in a browser with an ad blocker enabled, there’s a chance you won’t see the image below this callout. Ironically, we only discovered this after publishing: Adblock Plus and uBlock hide the image because the file name contains the word “advert.” False positives are still a major issue for ad-blocker users.

Additionally, AdGuard Antibanner blocks nearly all online tracking systems and checks the sites you visit against a database of malicious and phishing websites.
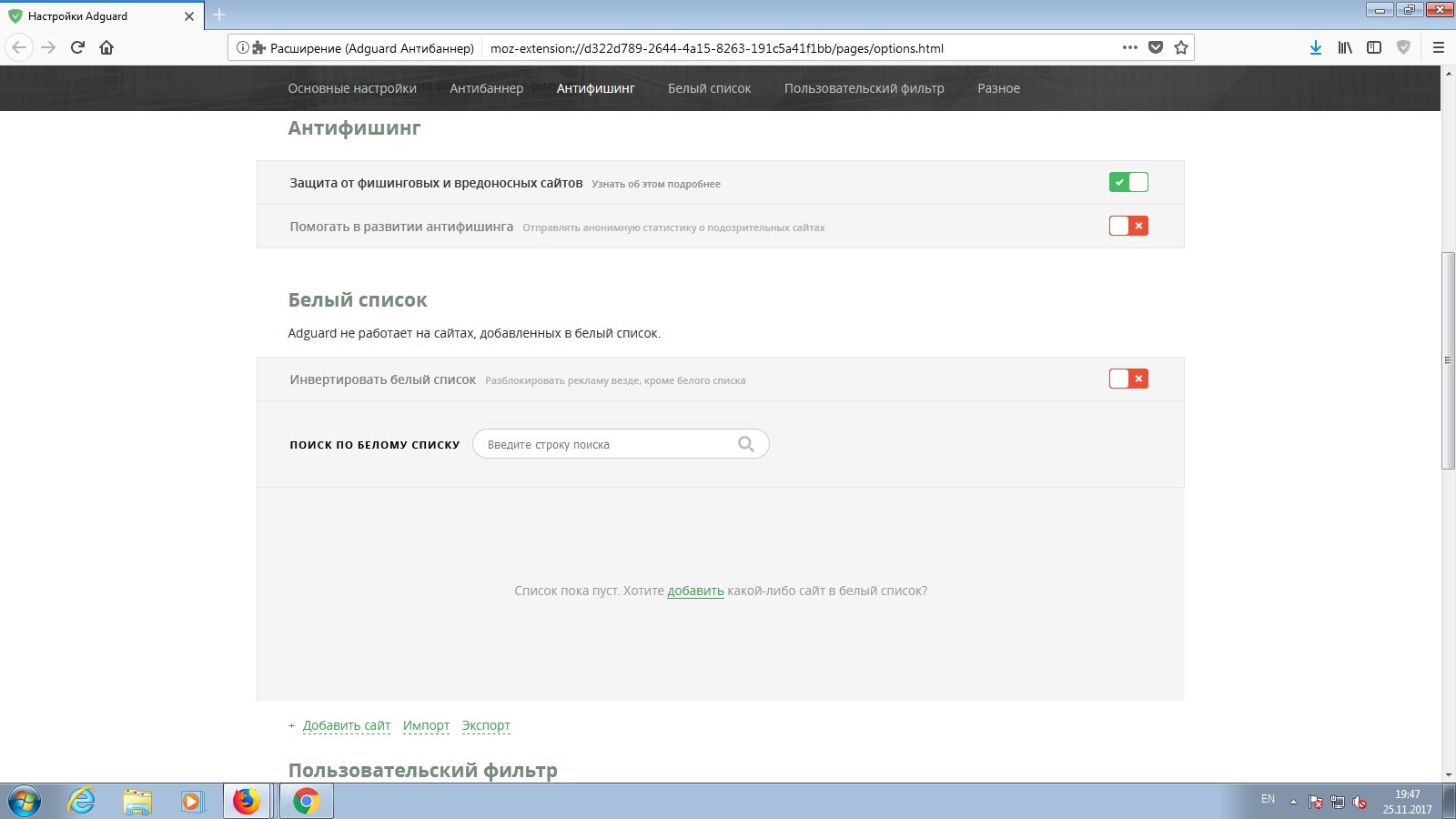
It has a whitelist, which is empty by default. There’s a neat option in the settings to “invert the whitelist.” In that mode, ads are allowed everywhere except on the sites you mark.
Overall, I came away with a very positive impression of AdGuard AdBlocker, but, purely subjectively, using uBlock Origin felt more convenient.
Ad Blockers vs. Cryptojackers
Lately, many websites have been running JavaScript-based miners that start silently as soon as a page loads, regardless of what the user does. In most cases, even the site owners were unaware. Someone quietly compromised popular pages and made them mine cryptocurrency on every visitor’s computer and mobile device. How is that not a botnet?
Since September 2017, Adblock Plus has included a feature to block stealth mining scripts. Technically, it’s just another filter, such as *coinhive., so you can manually turn any configurable blocker into an “anti-miner.” And beyond Coinhive, there are plenty of other in-browser mining scripts. You can find lists of them in the descriptions of add-ons like Mining Blocker and NoMiner.
I don’t recommend using those particular add-ons, since an all-in-one blocker is more capable. Running multiple extensions with overlapping features at the same time can cause conflicts.
Turn Off AdBlock or Leave
You’ve probably seen plenty of sites asking you to disable AdBlock or similar extensions. At some point, those requests turned into demands. Now some web pages hide their content until you add them to a whitelist. This approach has been dubbed an “adwall,” by analogy with a “paywall” — restricting content access to paying subscribers.
Take forbes.com as an example. If you visit it without any ad blockers, ads start popping up while the page is still loading.
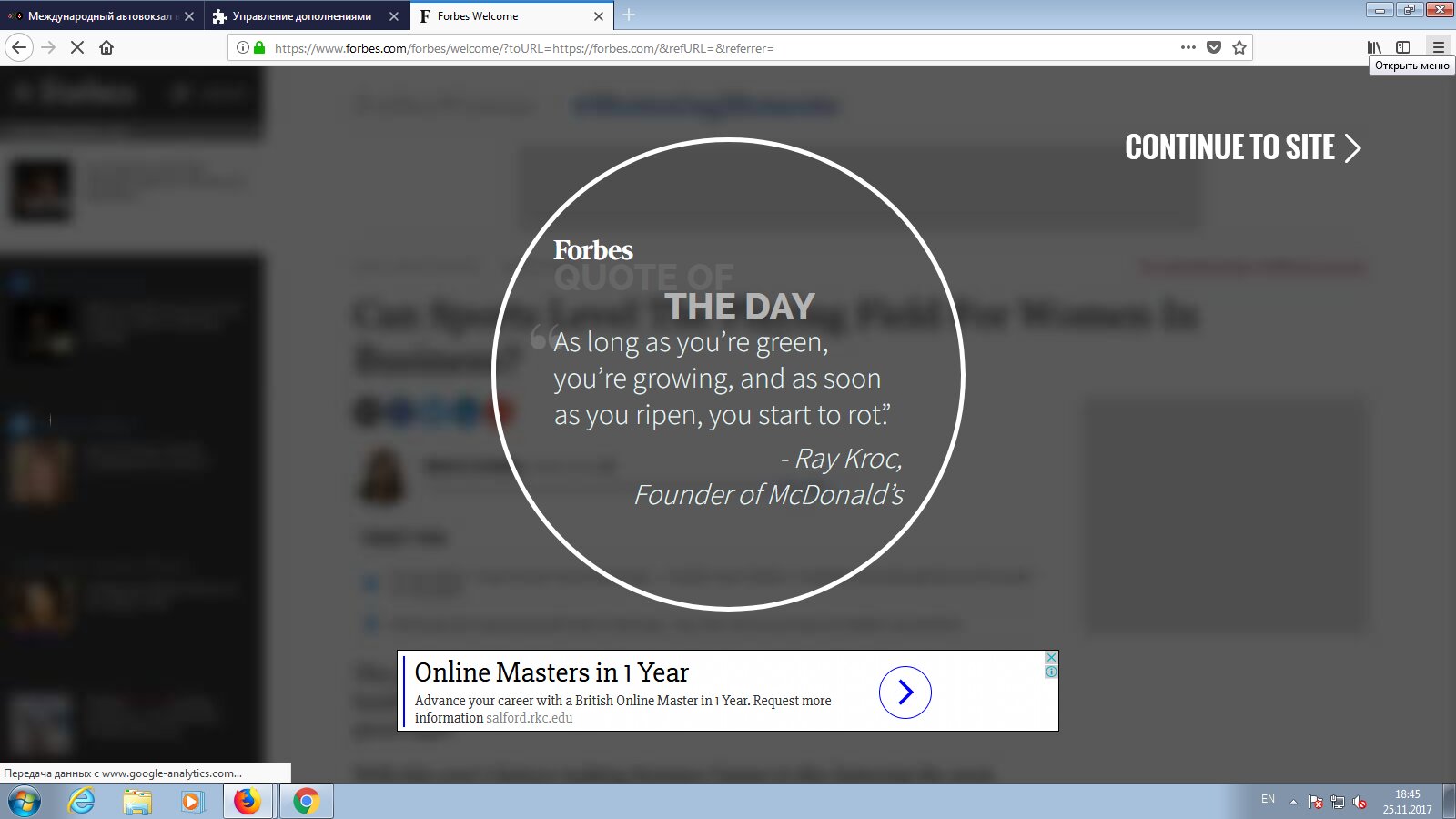
From then on, it will appear on every page in prominent positions—for example, at the top, pushing article titles down.
If you’re running an ad blocker, there’s a good chance the site will simply block access. This is becoming increasingly common on major Western websites, especially those in finance and business. The assumption is that a reasonable user who happens to have Adblock Plus installed will just whitelist the site and move on.
Interestingly, most adblock walls these days detect Adblock Plus but do a poor job of detecting AdBlock.
Blocking the blockers
The standalone IsraBlock extension hides anti‑adblock prompts that ask you to disable AdBlock and similar blockers on web pages.
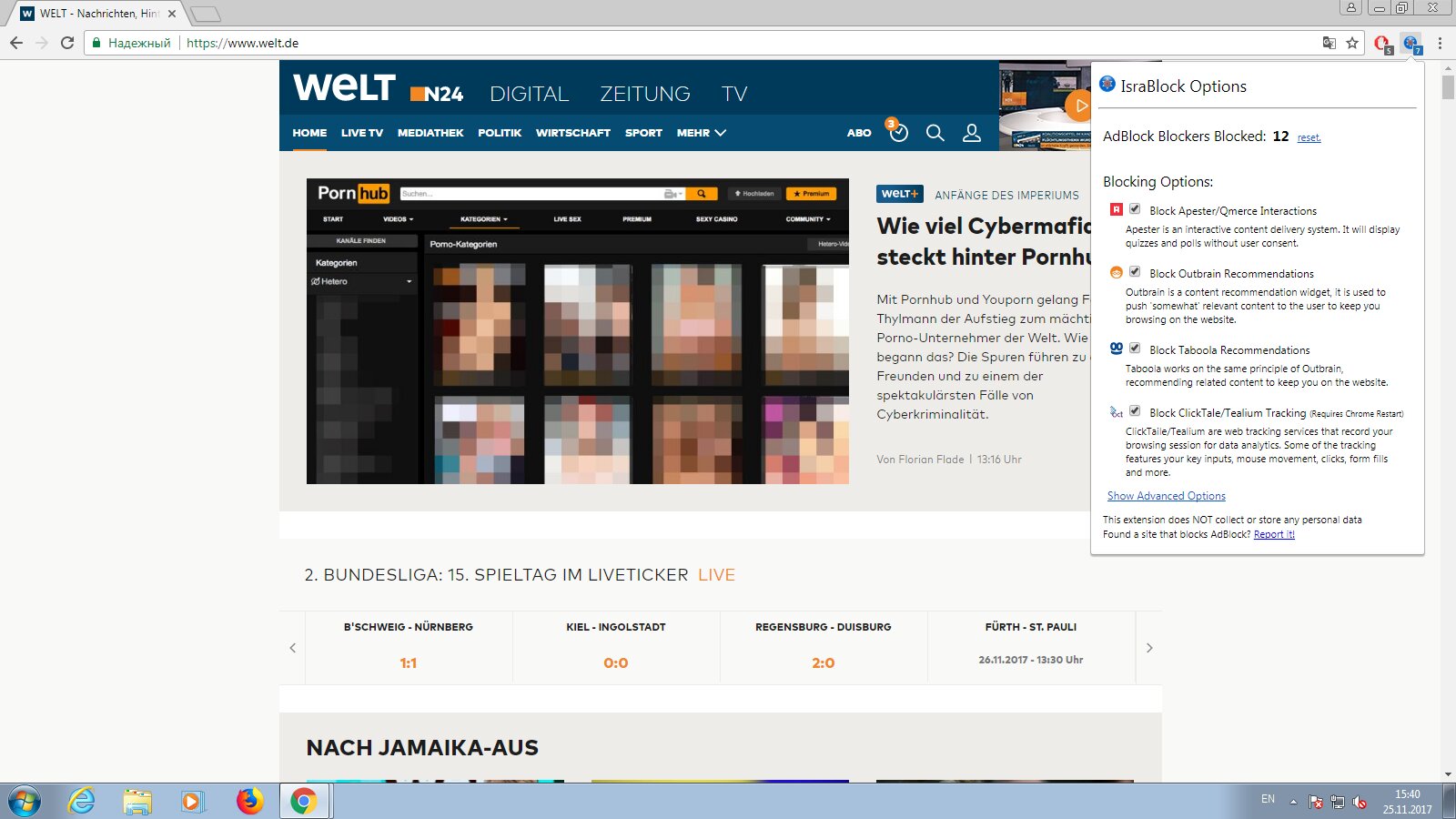
The latest release, IsraBlock 0.0.35, works much better in Chrome than in Firefox. While the Chrome version lets you configure advanced settings, the Firefox add-on has no settings at all.
Active development of IsraBlock is currently on hold, but it continues to work reliably.
In our test, uBlock Origin and AdGuard AdBlocker easily bypassed the adblock wall on Forbes.com. There were no prompts to disable AdBlock when visiting the site with them, and ad elements were cleanly removed from the page content.
The explanation is simple. To counter adwalls, a script and a continuously updated filter list called Anti-Adblock Killer were created. At first it was added separately to various blockers, and later, in a slightly modified form, it was integrated into the more advanced ones.
The Anti‑Adblock Killer feature removes from the loaded page’s code anything it detects as a demand to allow ads (for example, prompts to disable your ad blocker).
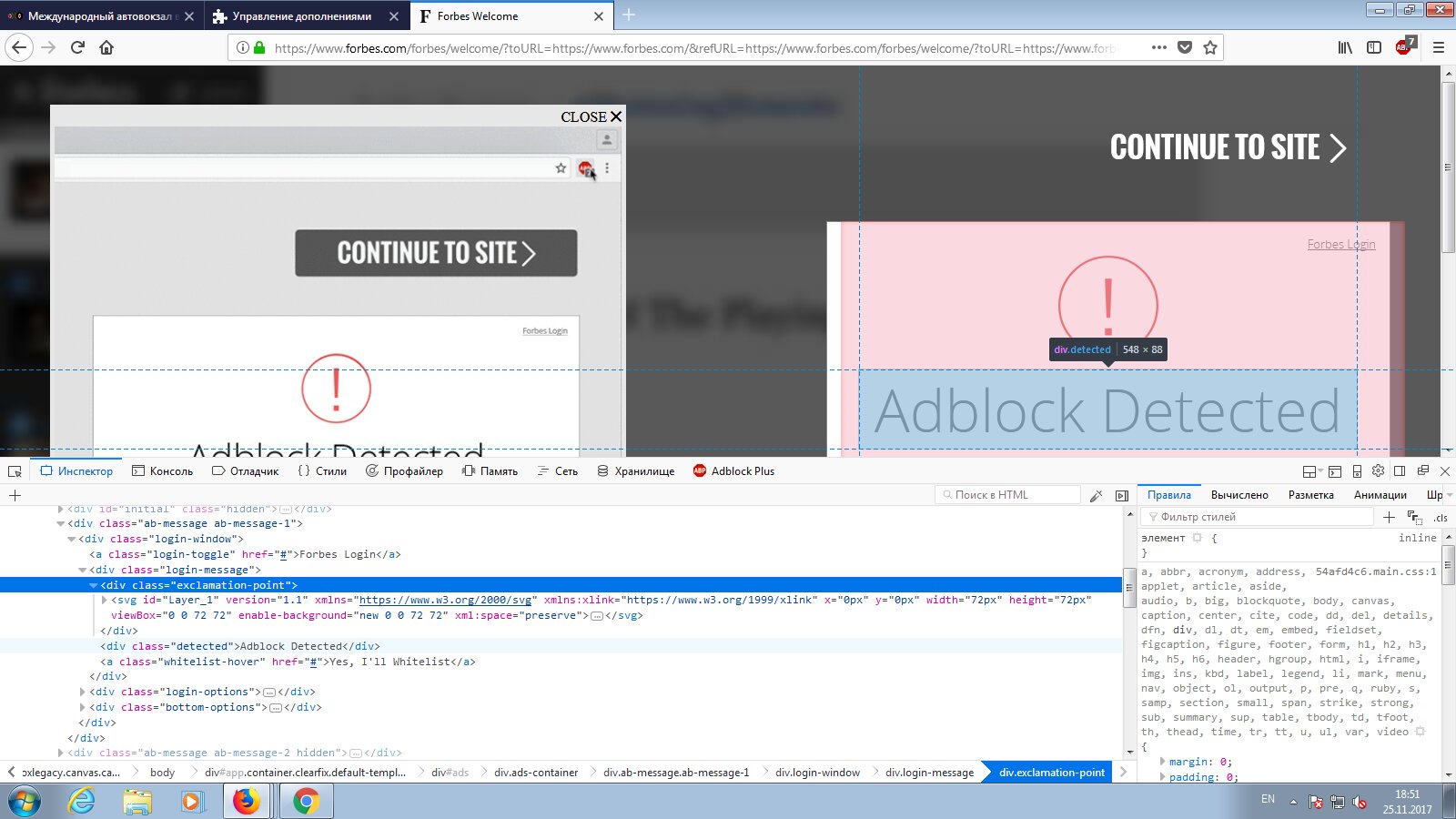
Its further development continues within various forks. For uBlock Origin, there’s uBlock Protector, and for AdBlock and Adblock Plus, AdBlock Protector 2 is currently in development.
Anti‑adblock countermeasures like Anti‑Adblock Killer are already built into the latest versions of uBlock Origin and AdGuard’s Antibanner. I’m confident other blockers will follow soon—it’s only a matter of time.