More than a year passed since first backers received their devices, but the hype around Flipper Zero is still growing. Script kiddies’ videos on TikTok reaching millions of views, reviews in famous blogs such as Linus Tech Tips, news about the destruction and seizure of Flipper shipments, and the ban on its sales on Amazon and eBay only fuel interest in the device. Access control system,) ads already claim: “Flipper Zero won’t work!”
However, many new owners of this device who fell victims to the hype around it now ask on the Flipper Zero subreddit: “What can I do with it?” The most popular answer is: “Play Snake and open the charging ports in Tesla cars.”
Let’s take a look at the Flipper’s capabilities offered by the factory firmware and find out what uses can a true geek find for it.
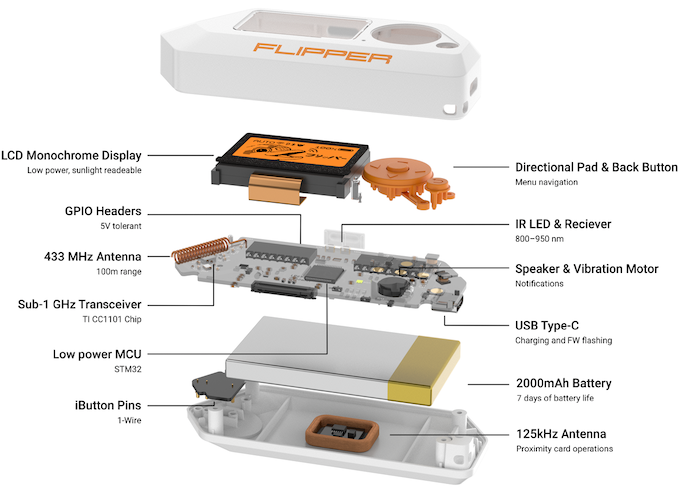
Out-of-the-box, Flipper powers up quickly and is ready to go. The only things you need are a microSD memory card and a firmware update.
Sub-GHz
Let’s start with the most exciting, in my humble opinion, function. Flipper can receive, record, and play radio signals in certain ranges at frequencies up to 1 GHz. But the factory firmware imposes frequency restrictions depending on the region. For instance, in Russia, the permitted ranges are as follows: 433.05-434.79 MHz, 868.15-868.55 MHz, 915 MHz, and 925 MHz.
Based on my practical experience and a quick search on marketplaces, most bar gates in my region operate at 433.92 MHz and use static code. This means that your Flipper Zero can easily receive and save the remote control signal for such a parking bar gate for subsequent use.
Of course, this doesn’t apply to paid underground parking lots, private homes, and other premises that use more advanced access control systems. But bar gate codes used to enter closed courtyards of apartment buildings, small private parking lots, and office parking lots can be copied.
Parking bar gate
Such a bar gate operated by a cheap remote control is used to enter the courtyard of my building. In total, it takes less than a minute to copy signals from all of its three buttons, and these signals recorded on my Flipper work perfectly: there is absolutely no difference with the remote control.
To record signals, you have to select the Read option in the Sub-GHz section and set the center frequency that is usually indicated on the remote opener. After pressing all its buttons in turn, your Flipper will identify and demodulate the signals, and you have to save them under some names.
My next target was a remote underground parking lot opener. I had little hope for it because, unlike the bar gate opener, I had to pay for it a deposit equivalent to $35, and guys at the local radio market flatly refused to copy it repeating: “Rolling code, rolling code.”
However, using the same settings, my Flipper has correctly identified the signal source as Marantec (which was inscribed on the remote opener). Both buttons were successfully recorded and operate perfectly. Even the operating ranges of the remote opener and my Flipper Zero are the same.
To sum up: no need to carry two extra key fobs in your pocket, no need to pay extra money, and kudos to Flipper.

With regards to the signal reading range. I conducted a small experiment and determined that a signal from such wireless remote controls can be recorded from a distance of some 20 m in line of sight. The reliable reception range (when the signal is successfully recorded after a short press of the button) turned out to be slightly less: some 15-18 m depending on the remote control. However, this distance can be increased if you use an additional RF module with an external antenna.
To sum up: simple unprotected remote controls are vulnerable since their signals can be easily intercepted by evil hackers.
Automobile
Encouraged by the first success, I decided to play with the car key fob. Of course, its code isn’t static, but dynamic (the above-mentioned rolling code).
Rolling (hopping) code is a technology used in radio-frequency remote control to protect against key copying. Its operation principle is very simple: every time it’s used, the code changes, and each code sent by the transmitter and received by the receiver is considered ‘used’ and cannot be accepted anymore.
The technology is pretty reliable, but its description indicates the presence of a flaw: only the code received by the receiver is considered ‘used’.
In other words, you won’t be able to completely copy a key fob to a modern car, but the signal intercepted by your Flipper will work once. Unlike the signal emitted by the parking lot opener, this signal cannot be completely demodulated; so, save it in the RAW format by selecting the respective menu option.
warning
An attempt to use the previously used code after using the next one switches the receiver unit in the car to the lock mode. To disable this mode, I had to disconnect the car battery. Without that, the car didn’t react in any way to pressing buttons on the key fob; accordingly, to open or close it, I had to use its physical key. In many modern cars, the keyhole is hidden behind the door handle plug, and most people have no idea of this. If you don’t want to find yourself in such a situation, refrain from experiments with cars.
I was able to unlock the car once by recording the unlocking code in the RAW mode and playing the unlocking signal close to the car. Important: when you record the code, the key fob must be far from the car; otherwise its signal will be received by it.
To sum up: never leave your key fob unattended and don’t store valuables in your car. An attacker can covertly record the unlocking signal from your key fob and open the car doors while you are away. Even such a simple device as Flipper Zero is suitable for this, and more powerful specialized gadgets are available as well.
Hacking Tesla
A popular trick among Flipper owners in Europe and America is remote opening of charging ports in Tesla cars. For educational purposes only, I opened such a port in one of them to the great surprise of its owner who was sitting in the car. Of course, I performed this operation in the Remote Control stealth mode available in the iPhone app to avoid any misunderstanding and furious reaction from the car owner.

To perform this operation, you have to download four files from GitHub for two signal variations (for European and American Tesla cars). In the standard Flipper firmware, certain frequencies are locked depending on the region. I was unable to reproduce the signal for an American Tesla; when I tried to do this, my Flipper displayed a warning picture. Apparently, several other cars I couldn’t hack were American as well.

RFID
Perhaps the simplest and most useful function of your Flipper Zero is to store entry buzzer keys.
It’s very convenient to store keys to all the buildings you visit in a single device and forget about helpless standing in front of a closed door and listening to squeaks of the speaker.
All keys I came across used the EM4100 protocol. Its reading, as well as key emulation, takes just a couple of seconds. Important: don’t forget to save each key under a meaningful name that uniquely identifies it.
Interestingly, the protocol is so unprotected that you can literally emulate a key based on its photograph. According to the E4100 protocol, significant data are contained in five bytes. If the key has a sequence of numbers like “049, 43317”, then, to enter it manually, you have to convert these two numbers into Hex. In this particular case, it’s 00 . Prior to these four bytes, you have to add the version code (must be guessed) and enter manually: 00 . This code can be used for emulation in the same way as any code received over a radio channel.

EM-Micro EM4100 keys are available in two variants: (1) nonrewritable (most of them are marked and have to be entered into the building intercom system); and (2) rewritable. You’ll need the latter ones to create copies of key fobs. For this purpose, I ordered ten blank key fobs at one of the marketplaces (model T5577). They support rewriting and work well.

NFC
In 2020, when I decided to back Flipper on Kickstarter, I had high hopes for NFC. In Russia, plenty of devices use this technology: bar gates in garage cooperatives, office passes, building intercom systems, fitness club bracelets, etc. But abroad, I couldn’t find a single useful application for this function. All I could do was experiment a little.
My first idea was to read UID from my bank cards. Too bad, their copies cannot be used for payment: the protection prevents this. I also tried to read information from the chip embedded in my Russian passport, but the smartphone implements this function better because the information on the chip is password-protected and can be unlocked only after reading and recognizing the machine-readable zone.
My last experiment involved reading the Troyka transit card. To my surprise, Flipper not only read it, but even showed the balance.

Overall, it seems that smartphones have already mastered NFC, and an additional device won’t give you any new advantage in this area.
IR
A great feature of my Flipper Zero that I use all the time is IR remote.
According to TikTok, the main use of this function is to turn off TV sets and billboards in shopping malls. I don’t see any point in this – unlike the wonderful possibility to control household appliances. Your Flipper can be used as a spare remote control for a TV, receiver, set-top box (too bad, not very convenient due to the specificity of Flipper controls), or a projector.
By the way, this function reveals a huge security hole affecting various publics events. I often deliver presentations in large halls where the projector is attached to the ceiling and controlled only with an IR remote. I wouldn’t want to run into a prankster equipped with a Flipper during such a presentation!
If you’ve ever worked in an office, you’ve probably had problems with the air conditioner remote control. Normally, there is only one remote control for the entire office, and it’s either kept by the employee responsible for its security or is permanently lost. Flipper enables you to solve this issue once and for all: a universal air conditioner remote control is included in its default firmware.
A quick research showed that controlling air conditioners is somewhat more complicated than, for instance, TV sets. Their remote controls transmit all parameters at once when you press any button, and some also receive feedback. However, this doesn’t prevent you from controlling an air conditioner with your Flipper, albeit in a slightly abnormal mode.
If signals used to control a specific air conditioner are absent in the universal app, then you can, like me, record the signals emitted by its original remote control. Alternatively, such recordings can be found online and downloaded. In my experience, both methods work great: I managed to download the file for my TV, but had to copy the remote control to an air conditioner from a little-known manufacturer.
iButton
On the way home from the post office where I picked my Flipper, I made the first attempt to use it by copying the building intercom key. The intercom system in my building is equipped with a contact iButton (that uses the 1-Wire protocol) manufactured by Dallas Semiconductor. The key was copied instantly, but, to my great disappointment, door refused to open when I poked the iButton with the contact pad of my Flipper.
Initially, I blamed the design of its case and the location of pogo pins (spring-loaded contacts). To test this hypothesis, I connected to the intercom via wires since the iButton contacts are duplicated in the upper part of Flipper Zero (GPIO 8 and 17).

This time, the door immediately opened. It turned out that this problem is common for new users. To open such intercom systems, you need some skill: the pogo pins must simultaneously touch both iButton contacts.
Not only can you emulate a key, but also use the copy function. I bought a blank key, and my Flipper successfully copied all the keys I use onto it.
To sum up: you don’t have to carry yet another key fob in your pocket and can copy keys for your friends. Such blank keys are available at marketplaces; to find them, use the keyword rw1990. In terms of price, they are similar to RFID keys.
U2F
U2F (Universal 2nd Factor) is an open driverless protocol for two-factor authentication. A U2F device can be used as a second factor (e.g. for authentication to online services).
As soon as I found out that my Flipper can serve as a U2F key/token, I immediately decided to configure it for two-factor authentication at one of my mailboxes. In fact, I had planned this for a long time, but I was reluctant to buy and carry an extra flash drive.
I registered my Flipper as a token on a Mac at the first attempt and without any problems. Important: don’t forget to switch two-factor authentication in your browser from standard to physical key.
Now, when I log in to the mail web interface, a request for two-factor authentication appears after entering the login and password. In the login method, select “Security Key”. To successfully login, you have to connect your Flipper to your computer via USB, select U2F in the menu, and confirm the login by pressing the middle Flipper button.
This is yet another reason I always have my Flipper with me.
Bluetooth
Flipper uses Bluetooth LE to connect to smartphones, but this interface can be used for more interesting purposes as well. For instance, to connect your Flipper as a controller to computers and phones.
Flipper can act as a mouse or keyboard. It’s not very handy, but in some situations, this function can be useful. For instance, you can use it as a clicker during presentations. For this purpose, its app has the Keynote option.
In my opinion, this function is extremely useful: Flipper features a handy shape and size; it’s always with you; and it’s really cool to deliver a presentation with a Flipper in your hand. The audience loves this!
With regards to smartphone control, I found an excellent use case. In the past, when I was shooting photos or recording videos from a tripod, I usually used a cheap Chinese remote control: after connecting via Bluetooth, it performed a single action: simulated pressing the physical volume button, which is bound on the iPhone to the camera shutter release.
Flipper fulfils this task without any problems, but if you try to perform this operation in some other apps (e.g. record a reel in Instagram), the recording won’t start. To solve this problem, you can enable AssistiveTouch on your iPhone and use your Flipper in the mouse mode to press the record button (or any other button on the screen).
In addition, Flipper acts as an excellent remote control (e.g. when you stream music from a laptop to a wireless speaker).
Conclusions
An attempt to describe Flipper is similar to an attempt to describe a smartphone or computer. This is a fully-functional open software and hardware platform with its own distinctive features, operating system, etc. It has plenty of capabilities and applications, and the set of favorite features will be different for each of its users.
I always have my Flipper with me and use it every day. It eliminates the need to keep bulky remote controls and extra keys. I often use it as an IR remote control for a TV, air conditioner, or projector; as a Bluetooth remote control or clicker for a computer or phone; and as a U2F key.
So, even if you don’t tinker or hack anything, Flipper will still be handy in everyday life. But if you’re involved in circuits engineering and other DIY stuff, or need a universal and compact tool for physical pentests, then you’ll appreciate Flipper even more.
Custom firmware that removes frequency restrictions and supports brute-force functions makes your Flipper a much more formidable device; while additional hardware modules (e.g. external Wi-Fi adapters) and third-party programs and plugins significantly expand its capabilities.
Importantly, the developers actively support their project. Updates introducing new features and patches are released on a regular basis. For example, the latest (at the time of writing) update (0.82.3) introduces the deep sleep function, which increases the battery life by four (!) times.
Even pre-release firmware versions are pretty stable. Since the time of its purchase, my Flipper froze or suddenly rebooted only a few times.
An active international community has already been formed around the device. If you have any questions about Flipper, you can visit the official forum or subreddit to find answers, ask for help, or discuss a topic of interest.
The main conclusion is as follows: not only is Flipper a magic toy for geeks and an excellent device to study wireless attacks, but also a very useful household tool applicable in a variety of situations.