Since its rise Windows was a natural habitat for all kinds of malware. Now the OS itself seems to have become one big trojan. Right after being installed it starts acting weird. The data flows in rivers to dozens of servers belonging to Microsoft and its partner companies. We will try to look into complaints of espionage manners of Windows 10 and find out what data it sneaks and where it sends it.
WARNING!
All the information was obtained through author’s personal research and is published for educational purposes. Neither the editorial staff nor the the author bear any responsibility for any damage caused by the intervention in the OS performance.
Microsoft > NSA
The first reports of new Windows’ strange behavior have emerged as early as the technical preview was delivered. Windows 10 creates a considerable amount of internet traffic even if there are no web applications running whatsoever. At the time this issue was pinned on diagnostics and statistics collected for software debugging. Microsoft experimented on the new product’s operation with various configurations and users acted as beta-testers. Well, it seems quite sensible. Although, nothing has changed after the release: even more complaints have risen.
«This weekend we upgraded my 14-year-old son’s laptop from Windows 8 to Windows 10. Today I got a creepy-ass email from Microsoft titled ‘Weekly activity report for [my son]’, including which websites he’s visited, how many hours per day he’s used it, and how many minutes he used each of his favorite apps. I don’t want this. I have no desire to spy on my boy. Microsoft advised me to turn off activity reporting in my account’s Family section if I did not want to receive such e-mails. There was no such issue in Windows 8.» This quotation from an e-mail send to writer and activist Cory Doctorow by his friend was posted on Boing Boing blog. Many reviewers claim that user data is still being collected – regardless of the account preferences set otherwise. The only thing you can really turn off is the activity reporting itself, in other words you will not receive the e-mails.
It is remarkable that the Privacy Statement particularly declares the gathering of various information by certain means embedded into Windows 10. Of course the overwhelming majority of Windows users will not even skim through the document, and those few who will read it, might feel perplexed. This lengthy document is full of vaguely and intricately worded statements, that make it hard to recognize the changes in privacy policies that will occur after installing Windows 10. The answer is: you can simply forget about your privacy, you won’t have it anymore. Human rights activists are unison in the opinion that the system immediately starts to gather all data it can get hold of. The data is mostly of the following types.
Biometric data
- Samples of voice and pronunciation of certain words;
- samples of handwriting (via handwriting input);
- text samples (typed in any application).
Geolocation data
- Current location;
- locations history including temporary location marks.
Technical data
- Information on equipment including ID numbers of the devices;
- information on networks joined both wireless and by cable;
- telemetric data;
- data from any built-in sensors.
Behavioral analysis
- Web search history;
- visited websites log;
- Windows startup and shut down time;
- startup and shutdown time of every application.
Purchasing activity
- Applications downloaded from Windows Store;
- clicking on contextual ads;
- clicking on personalized ads.
The list can go on although the above is quite enough for our research. Running ahead, I should mention that not all the accusations against Windows 10 were proven true. For example, Czech news portal AE News claimed that OS sends images from the webcam to the Microsoft servers. Whereas during our test once we connected the webcam, the system only installed the drivers. We have detected no irrelevant or unauthorized actions with the camera at all.
Watching the watchman
There are plenty of tools a hacker can use to scrutinize any software. For our test we prepared a computer with an empty SSD, a virtual machine, Wireshark sniffer, an HTTP-proxy and Fiddler debugger, TCP View bandwidth monitoring tool, a registry snapshot tool and several auxiliary utilities. We preferred the versions that run without installation. Wireshark and Fiddler are the only applications that require installation so they were last to be put to use. Hence, the system remained virginal over the most part of the test. We have analyzed network traffic both with default Windows 10 settings and after gradually turning off all the “spying” features.
According to the official documents the user is spied by: Windows, its ever integrated search engine Bing, voice assistant Cortana, MSN services, Microsoft Office suite, cloud storage client OneDrive, Outlook, Skype, Silverlight and Xbox Live. You can read more about it on Microsoft website. Now let’s see how the information is gathered.
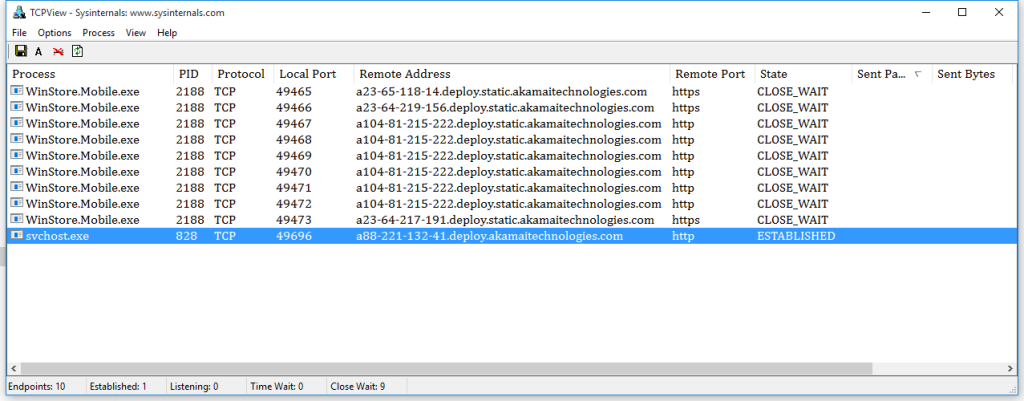
After installing the 10240 build we began watching its networking behavior using TCPView. There was no activity except for listed above. At first nothing happened – just like in Windows 7. Only the Windows Store was ready to download new content from Akamai Technologies.
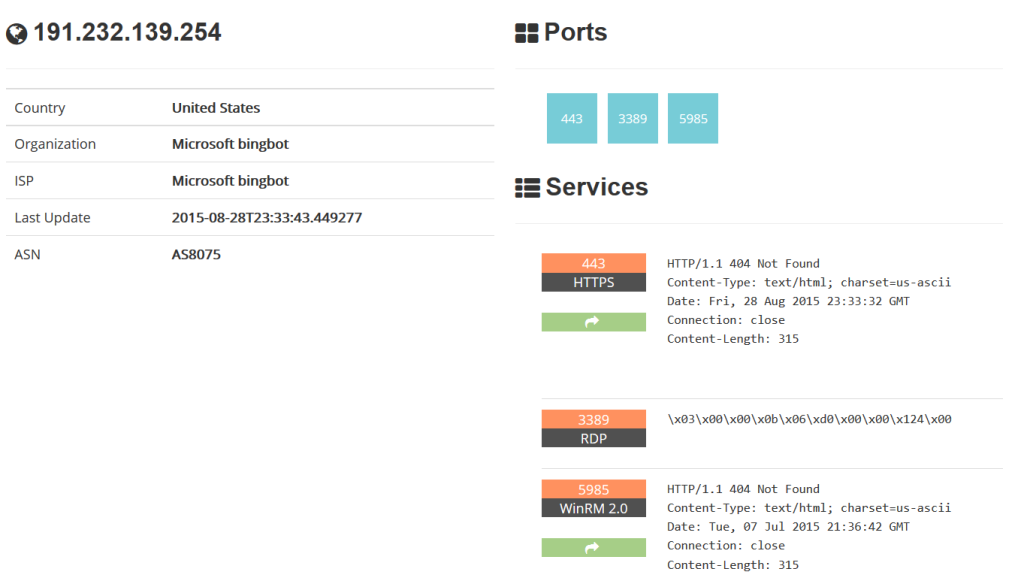
Just as we grew tired to lie in wait, suddenly \Windows\System32\svchost.exe process has come to life. It has connected to the remote host 191.232.139.254 and has sent some 7.5 KB to that host.
We could have found out some info on that host address using WHOIS but Shodan’ results are more informative.
From the description we found out it was some Bing’s bot. Well, that connection would have been justified, if we had made any search, even a local one. But that was not the case, we were just sitting and monitoring computer’s spying activity via TCPView.
Getting ready for a packet storm
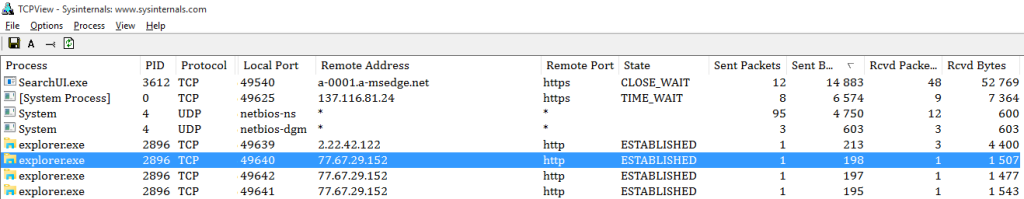
It might take a long time to wait for sleeping services to start. It is time to get active and wake them up. After hitting the Start button the information blocks on the right started to perk up. Weather forecast, news and ads have appeared there. TCPView shows that all this stuff is downloaded via Akamai network and looks legitimate. Once we run the Notepad app and start typing, everything changes at once.
Six connections appear at one stroke and close right away. More than 100 packets travel somewhere unknown. We have turned off the Internet search option allowing Windows to perform only a local search. Although, once we ran Notepad and began typing, SearchUI process launched anyway and started transferring data.
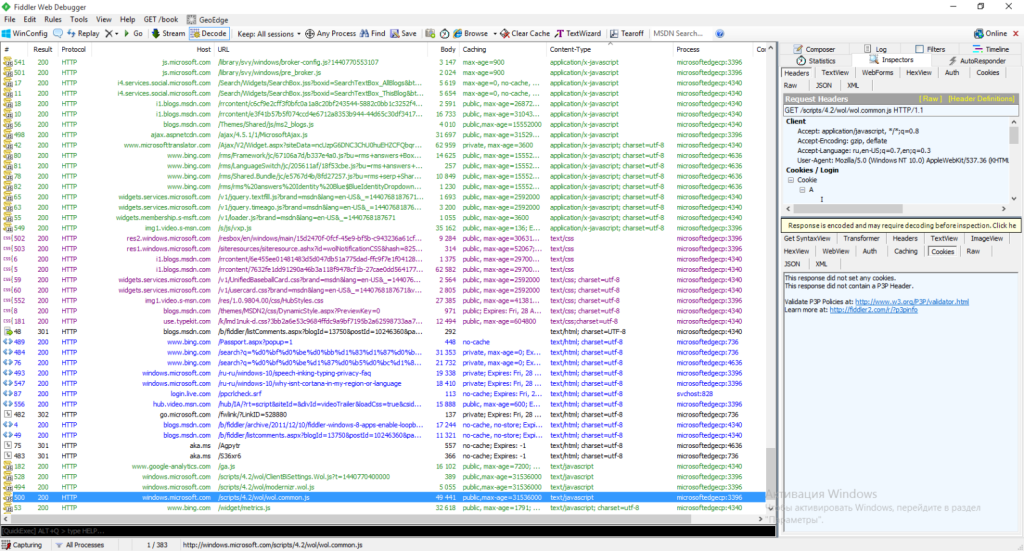
We must have understood the Privacy Statement not quire right. Well, let’s examine it again. It is a simple text page that opens in the Edge browser. Can it create any traffic at all? Oh yes, see the picture.
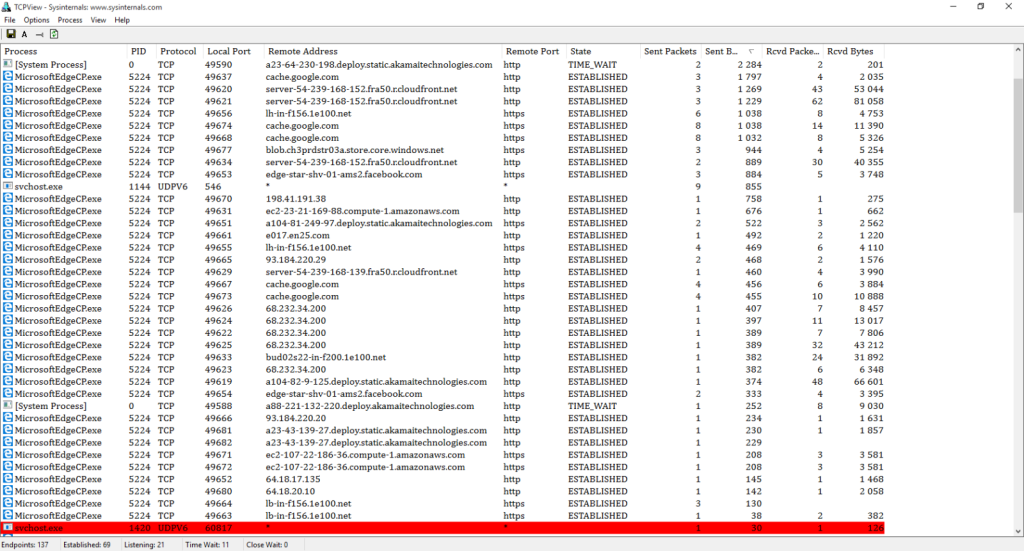
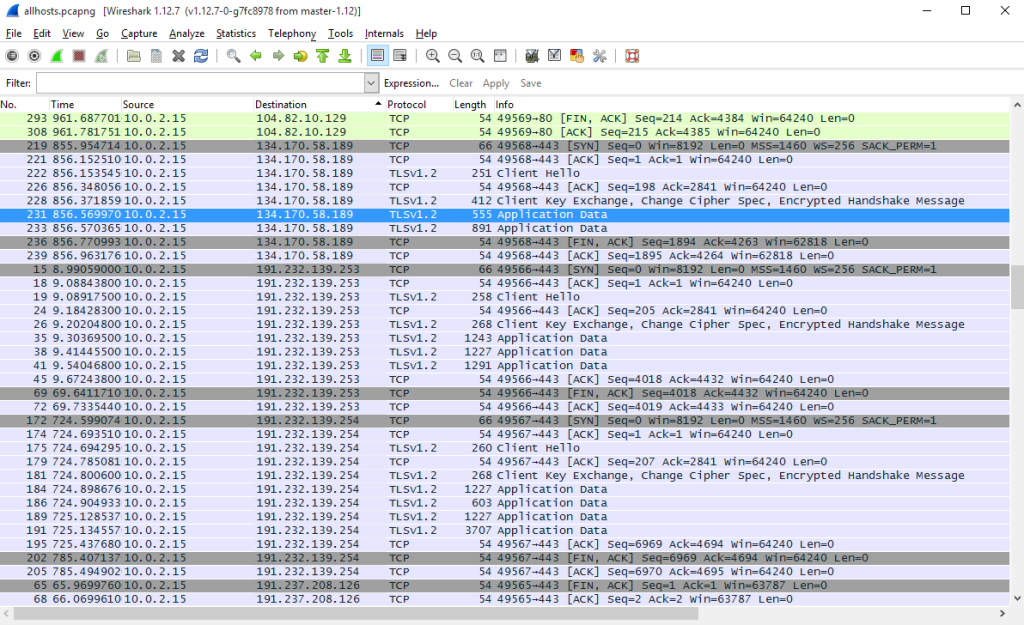
The list of connections changed and renewed so rapidly that we had a hard time keeping track of it. So we proceeded to the second part of the research. We closed every application, installed the Wireshark sniffer and recorded every windows’ activity for the next 30 minutes. To imitate more activity we were wandering through the settings in the Control panel, but did not change anything.
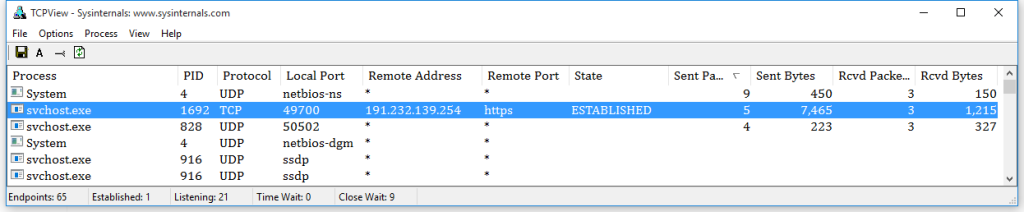
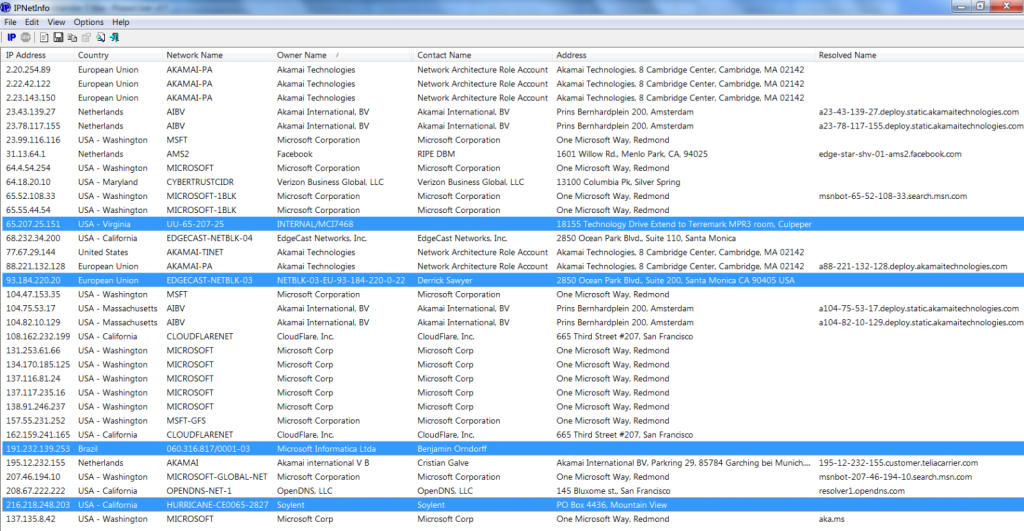
As many as 8000 packets were transferred somewhere. Studying the logs showed that most of the connections were made within a major subnetwork. Two or three last octets have frequently changed. Which shows us that Microsoft has expanded a huge network in order to process all the information gathered from the Windows users. If we sift out the addresses of the same kind, you can see the remains on the picture.
A Brazilian server arrests our attention, it is perhaps another Bing bot, perhaps a specialized one. But not only it raises some questions. For instance why would Windows make a connection with a Facebook server in the Netherlands? Why would it connect to the CloudFlare cloud storage? Not a single file has been created. Even the Microsoft account has not yet been activated.
Uncovering a spy ring
Besides Bing, the main spy in Windows in Cortana. We have developed a bit strained relations from the very beginning. At first she insisted on getting acquainted, then she stated she does not understand Russian and is not going to learn.
Even after we had chosen English as our main language and the US as our region, we did not win her favor. Microsoft Knowledge base advised to simply install the appropriate update. Well it’s a pity the user can not install updates of his or her own choice. They can only be downloaded and installed automatically. The user can only choose not to restart the computer or to start a postponed installation.
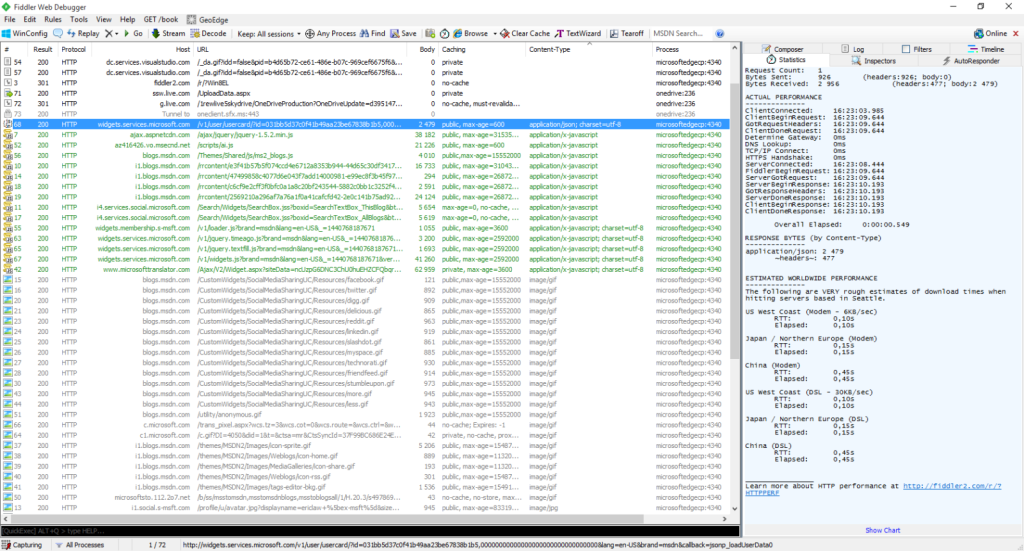
The major part of Windows’ hidden traffic goes through the Akamai content distribution network, this is why it is not displayed in the HTTP-proxy logs. They are not useless though. We can discover something interesting if we run Fiddler. For example, we can find out that the user is identified even before activating the installed copy of Windows.
In Fiddler we can see a lot of interesting things. Windows is contacting Microsoft Live (/usercard/?id=) and visualstudio.com. Why? Who knows.
30 minutes of idling created so much HTTP traffic that it can hardly fit on the screen. We made a couple of screenshots and compiled a list of the hosts that turn up more frequently than the others. We could have put them into the hosts file right away, but let’s do it later for the experiment’s sake.
The only URL on the list one would expect was windowsupdate.com, we did not include it into the block list. According to the installation record, during the experiment Windows has automatically installed 21 update of about 150 MB in total. Besides the Notepad we run only Calculator and our utilities for analyzing Windows activity during the test. The utilities had their automatic update options turned off. Still the network traffic exceeded 500 MB. It seems a bit too much for “the diagnostic data collected to enhance the user experience”!
Well, the experience was spoiled. New Windows’ spying features proved to be extremely numerous. Turning off the integrated search and dismissing Cortana helps but in part. Windows Defender sends the images of files it considers malicious right to Microsoft. SmartScreen not only inspects web content but also makes up a list of all visited pages. Location Service records every movement (mostly relevant for the mobile devices). Also many new applications send user interaction reports. It is impossible to turn it off in Diagnostic and Usage Data preferences, you can only choose to send less detailed reports.
INFO
Lately Microsoft has been working on adding newly introduced spying features to the older versions of Windows. In particular, KB3075249 and KB3080149 updates will include spying features.
Going offline
We determined to try and shut off this legalized espionage using standard Windows means. Most of the preferences can be adjusted via Privacy, Search and Update and recovery sections in Control Panel. There are about 50 switches but will they do any good?
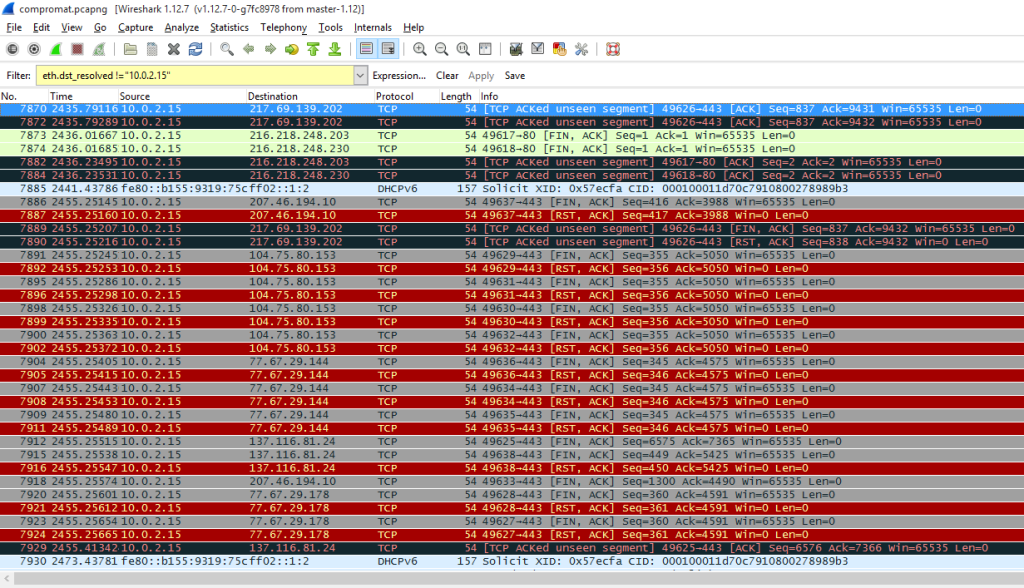
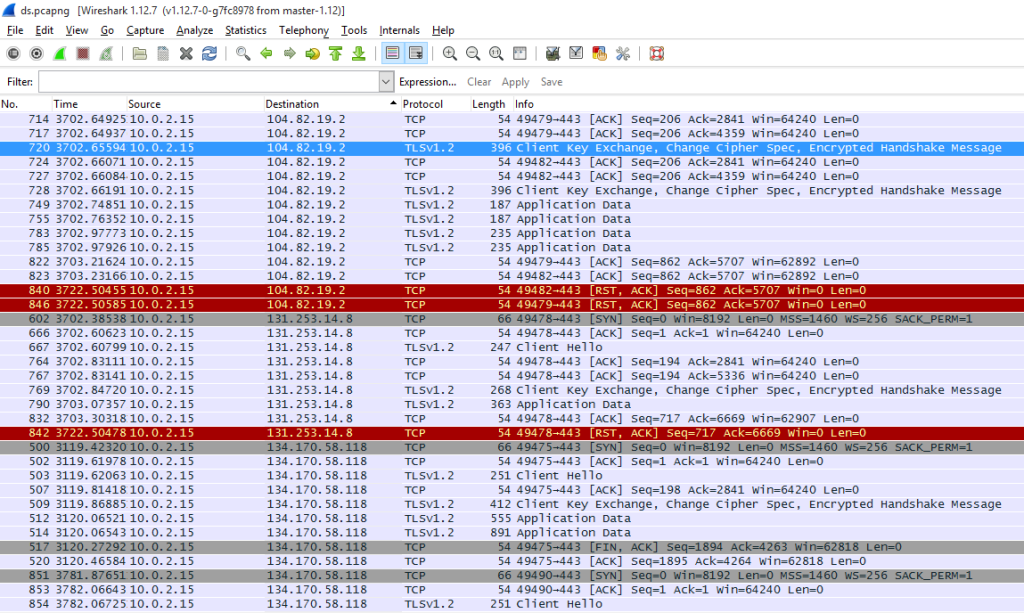
We have turned off all we could and run Wireshark again. This time we did not run any standard applications and did not even touch the mouse. In an hour sniffer’s logs show us the same painfully familiar IP addresses.
Well, Windows is making progress! Total number of queries decreased dramatically. The quantity of remote connections made without user’s knowledge is also three times less than before. Although we have noticed several new addresses. While in the first test Wireshark suddenly found a Facebook server, this time we have noticed some Amazon data-center from Ireland in the logs.
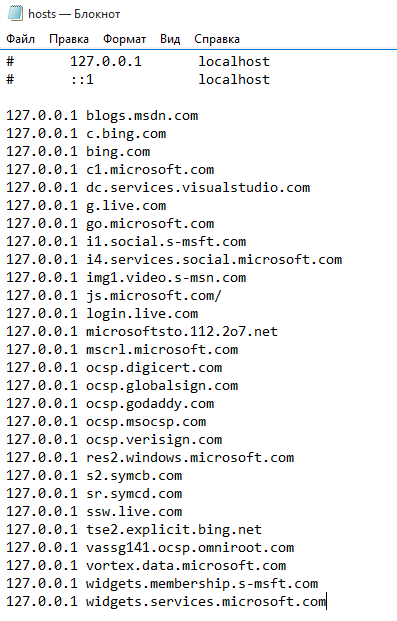
Okay, let’s add the whole list of IP addresses provided by Fiddler to HOSTS.TXT. It must help put an end to spying. We create the block list and run Wireshark again to check.
Compared to the first one, this log looks boring. There are only four IP addresses and all the queries fit in one screen. Two of them refer to the content distribution network and can not be effectively blocked by hosts: Akamai has got too many subnets. Another one belongs to Windows Update service that had not been blocked. BingBot turned out to be the staunchest spy. Its strong bond with Brazilian Microsoft Informatica is unshakable. The process seems to be designed to override the restrictions.
Finishing off the matrix agents
We had to take further steps to defeat the remaining spying agents. We have configured the firewall to block all the connections to the IP addresses discovered by Wireshark. There were 47 of them, but the list would certainly grow further should we continue monitoring. Of course there is a chance that the next automatic update will record new IP addresses into the system files, but for now the modified hosts.txt mostly ensures the security from spying.
The “unremovable” features can be removed via the registry.
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DataCollection
Let’s forbid sending the so-called “diagnostic” data reports by setting the corresponding parameter to zero.
We’d better delete the file containing the data already gathered by the DiagTrack service. Here’s the path to it.
C:\ProgramData\Microsoft\Diagnosis\ETLLogs\AutoLogger\AutoLogger-Diagtrack-Listener.etl
The DiagTrack and dmwappushsvc services can be stopped using Service Control Manager or via the registry node.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\
Use Task Scheduler to see the tasks queue and forbid sending regular data reports if there are still any.
It is better to uninstall OneDrive cloud storage client if you are not going to use it.
It can all be done manually, or you can also use DisableWinTracking utility for the same purpose. Compared to almost all the similar software, it is open source and well documented.
Once we performed all these steps, Windows has completely left behind its naughty spying manners. Yet most of the new features designed for user’s convenience and security were also left behind. However, let’s think of one Ben Franklin’s saying: “Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety.”
WWW


Thank you, Hackmag, for what is probably the most comprehensive article which I have read about Win 10 telemetry (Spying?).
Your site is now bookmarke on my laptop
Anyway to turn windows spying off and still use its calculator? When I employ the anti-spying techniques, my calculator won’t work. It is a couple hundred byte program with no need to be connected to the mothership. PS cut and pasted older versions of calc.exe onto the new computer and can use them on all prior versions of windows, but they won’t open in WIndows 10
That’s one hell of an article, thanks!
Wow! Definitely the most comprehensive article on the subject. You’ve got a new website patron …Thank you.
EXCELLENT! needs a refresh though
Pls. update this article to today’s win10/win11 versions…thx!
Great article
now try windows 11 ultra light from thepiratebay.org it only uses 1 gigabyte and doesnt create an emulator that you are using 🙂 it also comes default with tiny firewall which blocks any remaining bs by default. if you have any remaining programs, threads, or dlls that are transmitting data you can use cheat engine edit the”process” and fill it with bullet holes – aka NOP assembler command(no operation) your welcome. the day of the giant HAS FALLEN. i also helped destroy the darknet, more than 300k darknet websites are now deader than a doornail thanks to me 🙂
I’m disappointed that after all this testing author didn’t come up with a list of microsoft services that should be blocked to prevent data leaks.