
Well, how could we ‘boost’ privileges on Windows? First of all, we should say that there were found, lately, a lot of vulnerabilities regarding fonts parsing which make the process of privileges elevation rather simple as long as we have a proper exploit. If you use the Metasploit then you need only one command to get the system shell. However, it will only work if the system is not fully patched. In case if the machine has all the updates installed, despite the Linux, we will not be able to find SUID-binaries in here, furthermore the environmental variables usually do not transmitted to services or processes with higher privileges. So, what we can do then?
From admin to system, or something everybody knows
Usually, the first thought that bumps in mind regarding privileges elevation is to use the task planner. On Windows there are two ways to add a task: using ‘at’ or ‘schtaska’. Second one will launch a task under the authority of the user that added the task, as long as the first one will do it under the system authority. Here is quite standard trick that allows to launch a console under system authorities:
at 13:01 /interactive cmd
Second way is to add a service in order to launch the necessary files/ command:
@echo off @break off title root Cls echo Creating service. sc create evil binpath= "cmd.exe /K start" type= own type= interact > nul 2>&1 echo Starting service. sc start evil > nul 2>&1 echo Standing by... ping 127.0.0.1 -n 4 > nul 2>&1 echo Removing service. echo. sc delete evil > nul 2>&1
Third was is to change the system utility C:\windows\system32\sethc.exe to, for example, ‘cmd’. If you log out after this and push ’Shift’ couple times than the console under the system authorities is appeared.
What is about automate methods then we should remember Metasploit and its ‘get system’.We could also consider PsExec from Sysinternals as an alternative way(psexec -i -s -d cmd.exe).
We are going to take another road
All the methods mentioned above have one common disadvantage – the admin privileges is a must have. Which means that we are going to elevate privileges under privileged account.
In most cases when you have already got administrative privileges you have a bunch of variants of elevating further. So it is not like mission impossible. Well, that is why we are going to consider the methods that doesn’t require any 0day-vulnerabities, supposing that we are running standard system under unprivileged user.
Сredentials hunt
One of the save and sound methods to elevate and to set privileges in the system, is to get admins and more privileged users passwords. And now it is time to remember the automative software update. If you run the domain that included a large ‘fleet’, I really doubt that you will update software manually one by one. Moreover, it will be so time-consuming that simply you will have the lack of time for other purposes.This is why people use Unattended installations that, actually, produce files along with ‘pure’ administrative passwords, which is ‘pennies from heavens’ for pentesters and hackers.
Unattended Installs
In case of using automate installation there is an interesting file Unattended.xml appears on the user side, that usually is stored in %WINDIR%\Panther\Unattend\ or %WINDIR%\Panther\ along with administrative password. On the other hand, we do not need any authentication to get this file from the server, here we could use auxiliary/scanner/dcerpc/windows_deployment _services script from Metasploit. Although Windows Deployment Services is not the only way to run automative installations, the Unattended.xml file is considered as a standard.
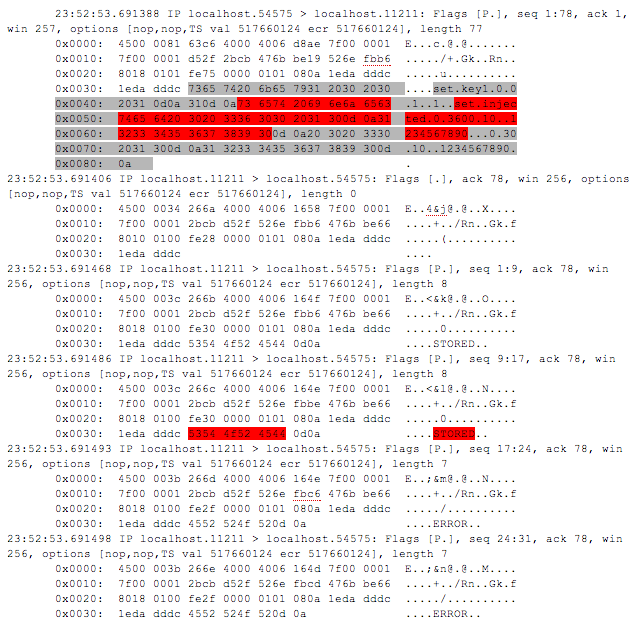
Example of the Unattended.xml file with saved data
GPP
Quite often the Group Policy Preference XML-files contain a set of encrypted data that could be used in order to add new users, share creation and so on. Luckily, the cipher method is documented and, consequently, we can get ‘pure’ passwords. Moreover, the metasploit command has had already done everything for you, the only thing that is supposed to be done is to use the /post/windows/gather/credentials/gpp.rb module. If you are looking forward to details then check the information in here(goo.gl/WW8nNw).
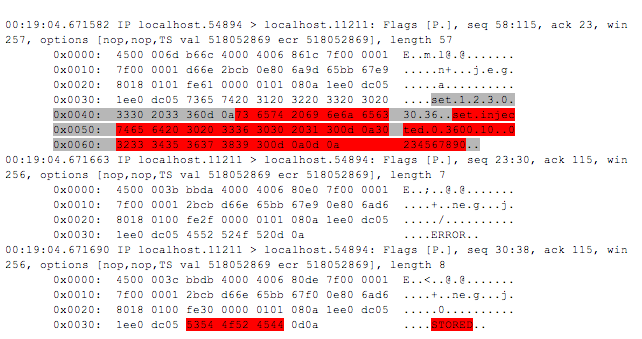
The key that is sed for data encryption
User privileges
Very often the privileges elevation is the result of incorrect user privileges set up. For example when the user is a Local admin or Power user on the host. Or when the domain users (or domain’s groups users) represent local admins among all the hosts. In this particular situation you’re probably have nothing left to do. But it is not like everyday situation.
AlwaysInstallElevated
From time to time, admins allow ordinary users to install programs by themselves, more likely, through further register keys:
HKLM\SOFTWARE\Policies\Microsoft\Windows \Installer\AlwaysInstallElevated
or
HKCU\SOFTWARE\Policies\Microsoft\Window s\Installer\AlwaysInstallElevated
This indicates that any MSI-file in the system has to be installed along with elevated privileges (NT AUTHORITY\SYSTEM). Consequently, we can use the file in a certain way and ‘boost’ our authorities.
The Metasploit contains a special module exploit/windows/local/always_install_elevated
that creates the MSI-files with the run file that is extracted and executed by means of system privileges installer. After the execution MSI- file stops the installation ( by means of a invalid VBS created on purpose) in order to prevent the registration in the system. Moreover, if we launch the installation with the /quiet key the user even will not see the error message.
Lost auto launch
It is often happens, that the system store the record about a file, that is needed to be launched even when the file itself is already gone. Well, that might happen because of a certain service that had been deleted incorrectly, like there is no run file, but there is still the record in the register and along with the launch the system try to start it unsuccessfully, trashing the the history with fail-messages. Actually we can use such situation in order to elevate our privileges. First of all we need to find all such ‘homeless’ records, for example, by means of autorunsc utility by Sysinternals.
autorunsc.exe -a | findstr /n /R "File\ not\ found"
After, as you have probably guessed we need to exchange the ‘missing guy’ with our own one.
Quotation’s magic
Yes, it is true, the quotations could not only play a low-down trick with SQL-requests allowing to proceed an injection but also could help to elevate privileges. The problem is quite old and familiar since the NT appearance. By and large, the paths to the certain services’ run files could not be put in quotation ( for example,ImagePath=C:\Program Files\Common Files\Network Associates\McShield\McShield.exe), however there are gap chars. In this case, if a hacker creates a file that will add new admins in the system or execute some other things and call it C:\Program Files\common.exe, then during the next launch exactly the common.exe command will be running and the rest part of the path will be recognised as an argument ( arguments). It is obvious that an unprivileged user could not do anything in Program Files, however the service’s run file could be placed in other directory, so a user would be able to put his own file.
In order to use this technique we need to find a fragile service first ( that will not use quotation in the path to binaries). We can do it like this:
wmic service get name,displayname,pathname, startmode |findstr /i "auto" |findstr /i /v "c: \windows\\" |findstr /i /v """
However, in order to do it on XP we have to have administrative privileges that is why it is better to run the command like this: to get the list of services:sc query, then to check information about each server – sc qc servicename.
According to plan
There is another mechanism that can help to elevate privileges – task planner.The schtasks utility allows to put tasks on certain events. Time most interesting are – ONIDLE, ONLOGON и ONSTART. As we can understand from the names the ONIDLE will be executed during each shutdown, while ONLOGON and ONSTART will be executed during the log in and system launch retrospectively. Generally, we can put a task on each event. For example, copy a malware binary or key logger during the system launch and run it. Or, dump credit cards during the log in. Briefly, everything depends on your imagination and the target task.
Authority tricks
The first security method to prevent us from the privileges elevating is access authorisation. It would be great simply to rewrite some system file ( for example, sethc.exe) and immediately get system privileges. However, it is only a dream, because we have only the permission to read it and we can not use it in any way. Keep your chin up, here there are,just like everywhere else, certain ‘hidden rocks’, and if we know them it allows us to make the impossible possible.
Program Files – one of the system directories safeguarded by the mechanism, that is very interesting for us in terms of privileges elevating. The unprivileged users have no access there, however, sometimes the file’s privileges could be set up incorrectly during the installation, as the result all the users get the full access to run files. You can understand what is going to happen next? 😉
Another restriction is that the root of the System disk write protected. However, for example, in terms of XP when a new directory is creating the BUILTIN\Users group get FILE_APPEND_DATA and FILE_WRITE_DATApermissions ( even if the folder owner is admin):
BUILTIN\Users:(OI)(CI)R
BUILTIN\Users:(CI)(special access:)
FILE_APPEND_DATA
BUILTIN\Users:(CI)(special access:)
FILE_WRITE_DATA
In terms of Windows 7 everything is pretty much the same, only it is AUTHENTICATED USERS group that get the permissions.How could it become a problem? Simply certain applications are installed outside the secure directories, that is why it is easy to change their run files. For example, this happened to the multiuser installation in the Metasploit Framework. The bug was fixed in the 3.5.2 version and the utility moved to Program Files.
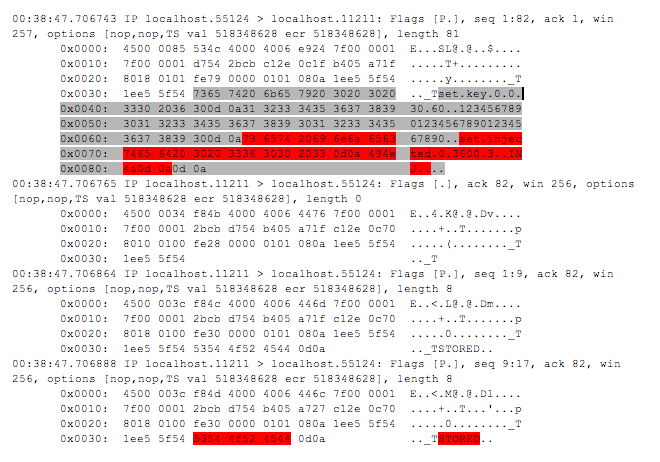
Windows 7. Folder Authorities created by admin
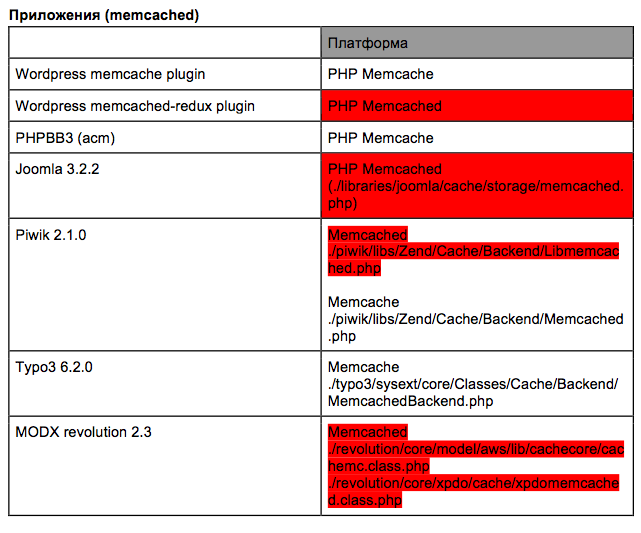
Windows XP. Folder Authorities created by admin
How to search such directories/ files
To find the directory with incorrect permissions is a half of the battle. Nevertheless, it supposed to be found first. In order to do this we could use these two tools: AccessChk and Cacls/ICacls. So, to find the ‘weak directories’ by means of AccessChk, we will need further commands:
accesschk.exe -uwdqs users c:\ accesschk.exe -uwdqs “Authenticated Users” c:\
To find the file with ‘weak permissions’ we are going to use this one:
accesschk.exe -uwqs users c:\*.* accesschk.exe -uwqs “Authenticated Users” c:\*.*
We can do the same thing using Cacls/ICacls:
cacls "c:\Program Files" /T | findstr Users
The example of the common mistake regarding permissions in terms of Windows XP. All we have to do is to switch files 🙂
Tricks with services
Another way to ‘boost’ privileges is to use misconfigurations and service errors. Experience has proven that not only files and folders could have incorrect permissions, but also the services working in the system. In order to find them you can use AccessChk by famous mark russinovich:
accesschk.exe –uwcqv *
The most pleasant thing is to see SERVICE_ALL_ACCESS permission for the authenticate and power users. However, there could be another good variants:
SERVICE_CHANGE_CONFIG— can change service run file;WRITE_DAC— allows to change permissions which might lead toSERVICE_CHANGE_CONFIG;WRITE_OWNER— you can become an owner by means of it;GENERIC_WRITE— inheritsSERVICE_CHANGE_CONFIGpermissions;GENERIC_ALL— inheritsSERVICE_CHANGE_CONFIGpermissions.
If it is found out that one of these permissions is installed then the chance to elevate permissions raises dramatically.
How to boost?
Well, let’s imagine that you have found the proper service and now it is time to work with it. Here the sc utility will be really helpful. First of all we need to get the information about the service we are interested in, let it be upnphost:
sc qc upnphost
Adjust it by means of the same utility:
sc config vulnsrv binpath= "net user john hello /add && net localgroup Administrators john /add" type= interact sc config upnphost obj= “.\LocalSystem” password=“”
As you can see, during the next launch the services will run the net user john hello /add && net localgroup Administrators john /add command instead of run file, so, they add a new user ‘john’ with the ‘hello’ password in the system. All we left to do is to restart the service:
net stop upnphost net start upnphost
That is it.
At the end
Once upon a time i read an article that described basic methods regarding privileges boosting on Windows OS. I set little store by it but the theory settled in my head and once it helped me a lot. Hopefully, you will find something interesting in this article as well to be able to take the hurdle one day.
[…] TOP–10 ways to boost your privileges in Windows systems […]
Notice cautiously, and you may realize that the desk is a manifestation of both side.