On RubyGems, 60 malicious packages were discovered that masqueraded as harmless tools for automating social networks, blogs, and messengers. The gems stole users’ credentials and, since March 2023, have been downloaded more than 275,000 times.
CONTINUE READING 🡒 Stable Diffusion XL: Generate AI Images Locally on Your Computer
You’ve probably heard of Stable Diffusion—a neural network that generates images locally on your computer, with no cloud services or paid tokens. A new version just dropped: SDXL, short for “Extra Large.” In this article, we’ll install…
CONTINUE READING 🡒 Efimer steals cryptocurrency, hacks WordPress, and sends spam
Kaspersky Lab experts have observed a wave of attacks using the Efimer Trojan. The malware spreads via compromised WordPress sites, torrents, and email. Its primary goal is to steal and substitute cryptocurrency wallet addresses, but with additional…
CONTINUE READING 🡒 Wikipedia editors will quickly delete AI-generated articles
Wikipedia has adopted new rules to combat the flood of AI-generated articles inundating the online encyclopedia. Under the new policy, administrators are authorized to quickly delete AI-generated articles if they meet certain criteria.
CONTINUE READING 🡒 DIY Audio: How to Build Your Own Digital-to-Analog Converter (DAC)
This article will help you build your first—or maybe not your first?—digital-to-analog converter (DAC). You’ll have several designs to choose from, ranging from classic to pretty radical. Pick whatever suits you. There are even a couple of…
CONTINUE READING 🡒 How Phone Makers Ruin Android with Bloatware, Heavy Skins, and…
In one of our previous pieces, we took a deep dive into why iPhones have been—and will continue to be—faster than current Android flagships. The article sparked heated debate and mixed reactions. So we decided to expand…
CONTINUE READING 🡒 Modologic. Dissecting the Pathologic virtual machine
Many years ago, I was eager to understand how the game “Pathologic” actually works. But at that time, the format of its scripts was beyond my capacity. Today, I will show you how to crack the game engine to find out how its scripts operate.…
CONTINUE READING 🡒 Turning an Old Android Smartphone into a Fully Functional Home…
Imagine this scenario: you have an old Android smartphone. Its primary function is long gone – maybe the screen is shattered, the mobile connectivity module has died, or the device is simply outdated. Selling it for next…
CONTINUE READING 🡒 The Ultimate Guide to Android Performance Optimization
Running out of battery? Tired of sluggish apps? Don’t panic—and don’t rush to buy a new smartphone. Even a slow phone can be made snappier, and its battery life extended significantly. In this article, we’ll share a…
CONTINUE READING 🡒 Paper Werewolf Group Exploits WinRAR Vulnerabilities for Attacks
In July and early August 2025, the espionage hacking group Paper Werewolf attacked several organizations from Russia and Uzbekistan. The phishing emails had RAR archives attached, supposedly containing important documents, but in reality, they included malware. The…
CONTINUE READING 🡒 Creating a Bootable USB Drive with Arch Linux Live Image
Today, we will create a live USB drive with an Arch Linux installation image. By "live," I mean it will allow you to install and remove programs, modify any files, and save changes while in use. I've…
CONTINUE READING 🡒 SonicWall Fails to Find Zero-Day Vulnerability in Its Products, Links…
SonicWall has announced that the operators of the Akira ransomware exploited an old vulnerability in recent attacks on 7th-generation SonicWall firewalls with SSL VPN enabled. It was previously believed that the attackers were using a zero-day vulnerability.
CONTINUE READING 🡒 150 Firefox Extensions Found to Have Stolen Over $1 Million…
Analysts at Koi Security discovered the malicious GreedyBear campaign, which is active in the Mozilla add-ons store. 150 malicious Firefox extensions have stolen cryptocurrency worth over $1 million from users.
CONTINUE READING 🡒 Unlocking the Secret Features of DuckDuckGo: Unique Tools You Won’t…
If people are familiar with the search engine DuckDuckGo, it's primarily due to its enhanced privacy features. Unlike Google or Yandex, it doesn't collect user data, but its search results aren't as strong. However, if you dig…
CONTINUE READING 🡒 ReVault Vulnerabilities Allow Bypassing Windows Login on Dell Laptops
Vulnerabilities in the ControlVault3 firmware affect over 100 Dell laptop models, allowing attackers to bypass Windows Login and install malware that remains on the system even after an OS reinstallation.
CONTINUE READING 🡒 Adobe Releases Emergency Patches for AEM Forms
Adobe has released emergency patches that address two critical vulnerabilities in Adobe Experience Manager Forms (AEM Forms) in Java Enterprise Edition (JEE), for which public exploits are already available.
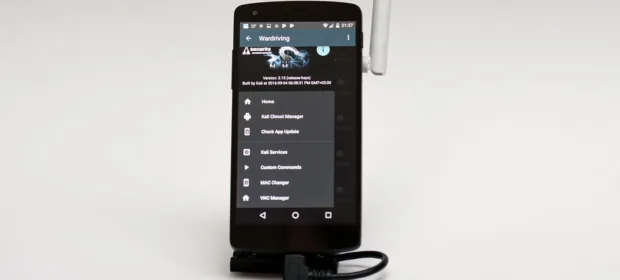
CONTINUE READING 🡒 Conducting a Wi-Fi Security Audit Using a Smartphone with Kali…
Wardriving can be effectively conducted using a smartphone, but the built-in radio module and Android apps are often insufficient for advanced attacks. Instead, external Wi-Fi adapters and console programs for Linux are typically used. All the necessary…
CONTINUE READING 🡒 WhatsApp Introduces a New Feature to Protect Against Scammers
The developers of WhatsApp have introduced a new security feature that will help users identify potential scammers when someone not in their contact list invites them to a group chat.
CONTINUE READING 🡒 Google Data Breach Occurs Due to Salesforce Hack
Google reports that it has suffered a data breach. This incident is the latest attack by the hacker group ShinyHunters, which has been targeting Salesforce CRM in recent months.
CONTINUE READING 🡒 Earn Cryptocurrency by Renting Out Your Hard Drive Space
If you have unlimited internet and plenty of free disk space, you might be able to make some money from it. We'll explain how blockchain is used for data storage and conduct an experiment with the Storj…
CONTINUE READING 🡒