Often, the manufacturers of routers do not particularly care about the quality of their code. As a result, the vulnerabilities are not uncommon. Today, the routers are a priority target of network attacks that allows to steal money and data while bypassing local protection systems. How can you personally check the quality of firmware and adequacy of settings? You can do this by using free utilities, online test services and this article.
Consumer-grade routers have been always criticized for their unreliability, but the high price does not yet guarantee high security. Last December, the experts from Check Point found more than 12 million routers (including some top models) and DSL modems that can be hacked due to vulnerabilities in their mechanism of automatic settings. It is widely used for fast configuration of network equipment on the client side (CPE, Customer Premises Equipment). In the last ten years, ISPs do this by using CWMP (CPE WAN Management Protocol), a subscriber’s equipment management protocol. TR-069 specification allows to use it for sending settings and connecting services through auto configuration server (ACS, Auto Configuration Server). The employees of Check Point found that many routers make an error when handling CWMP requests, and ISPs make this situation even more complicated: most of them do not encrypt the connection between ACS and customer equipment and do not restrict access by IP or MAC addresses. This all creates conditions for an easy ‘man-in-the-middle’ attack.
By using the vulnerable CWMP implementation, an attacker could do practically anything, such as setting and reading the configuration parameters, resetting parameters to their default values, and remotely rebooting the device. The most common type of attack is to substitute DNS addresses in the router settings for addresses of servers controlled by the attacker. They filter the web requests and redirect those addressed to banking services to fake pages. The fake pages have been created for all popular payment systems, such as PayPal, Visa, MasterCard, QIWI and other.
A particular aspect of this attack is that the browser is running on a clean OS and sends a request to a correctly entered address of real payment system. Checks of network settings on the computer and a virus scan do not reveal any problems. Moreover, the effect is the same, if you connect to a payment system through a hacked router from another browser and even from another device on your home network.
Since most people rarely check the settings of their router (or even entrust this process to technicians from ISP), the problem stays undetected for a long time. It is usually discovered by process of elimination after the money was stolen from the accounts and computer check revealed nothing.
To connect to the router via CWMP, the attacker uses one of the most common vulnerabilities specific to entry-level network devices. For example, this devices host RomPager, a third-party web server written by Allegro Software. Many years ago, it was found to have a cookies handling bug, which was quickly fixed, but the problem exists even today. Since this web server is part of a firmware, it cannot be updated at once on all devices. Every manufacturer had to issue a new release for hundreds of models that are already on sale and convince their owners to download the update as quickly as possible. In practice, none of the home users did it. As a result, vulnerable devices number in the millions even ten years after the release of patches. Moreover, even today, in their firmware, the manufacturers continue to use the vulnerable version of RomPager.
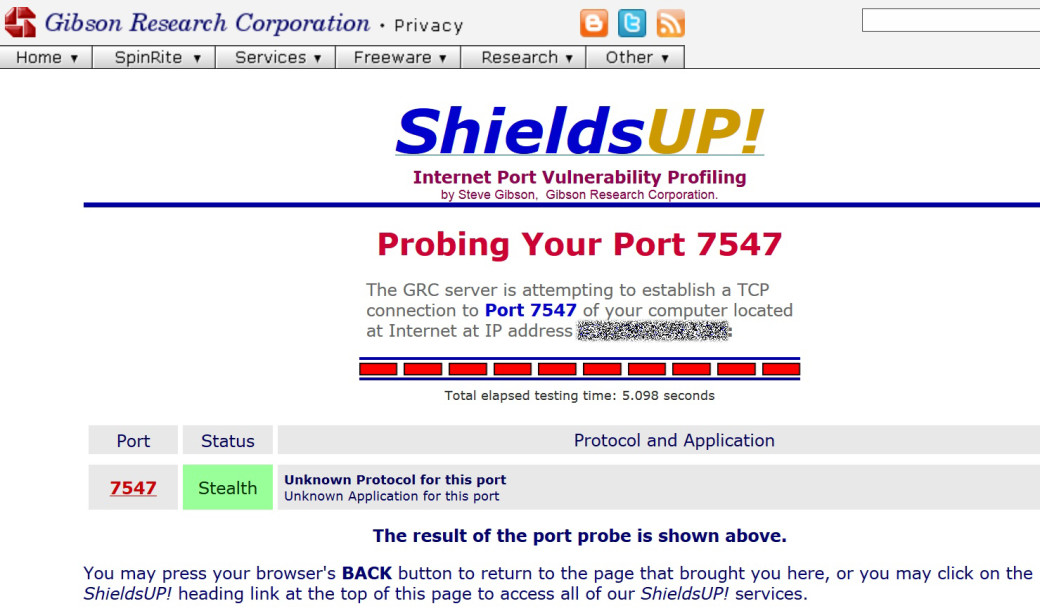
In addition to routers, this vulnerability affects VoIP phones, network cameras and other equipment that allows remote configuration via CWMP. Typically, this is done by using port 7547. You can check its status on the router with Shields Up, a free service from Steve Gibson. To do this, enter its URL (grc.com), and then add /x/portprobe=7547.
On the screenshot, only positive result can be indicative that there is a vulnerability. Negative result does not guarantee that vulnerability is not there. To eliminate the possibility, you need to conduct a full penetration test, for example, by using Nexpose scanner or Metasploit framework (bit.ly/1vlHHHw). Often, the developers are not able to say what version of RomPager is used in a particular release of their firmware or whether it is included there at all. This component is definitely not available only in alternative open source firmware (we will discuss it later).
Specifying Secure DNS
It is a good idea to often check the router settings and immediately specify the alternative DNS server addresses. Here are some of them that are freely > available.
Comodo Secure DNS: 8.26.56.26 and 8.20.247.20
Norton ConnectSafe: 199.85.126.10, 199.85.127.10
Google Public DNS: 8.8.8.8, 2001:4860:4860:8888 — for IPv6
OpenDNS: 208.67.222.222, 208.67.220.220All of them block only infected and phishing sites, without restricting access to resources intended “for adults”.
Unplug and Pray
There are other problems known for a long time, which the owners of network devices or (less often) their manufacturers are unwilling to fix. Two years ago, the experts from DefenseCode found a set of vulnerabilities in routers and other active network equipment of nine major companies. All of them are associated with incorrect software-based implementation of some key program components. In particular, this affects UPnP stack in firmware for Broadcom chips or those that use the older versions of ‘libupnp’, an open source library.
Together with the experts from Rapid7 and CERT, the employees of DefenseCode found about seven thousand vulnerable models of devices. In the six months of active scanning in the random range of IPv4 addresses, they identified over 80 million hosts that responded to a standard UPnP request on WAN port. One in five of them supported SOAP (Simple Object Access Protocol) service, while 23 million allowed to execute any code without authorization.
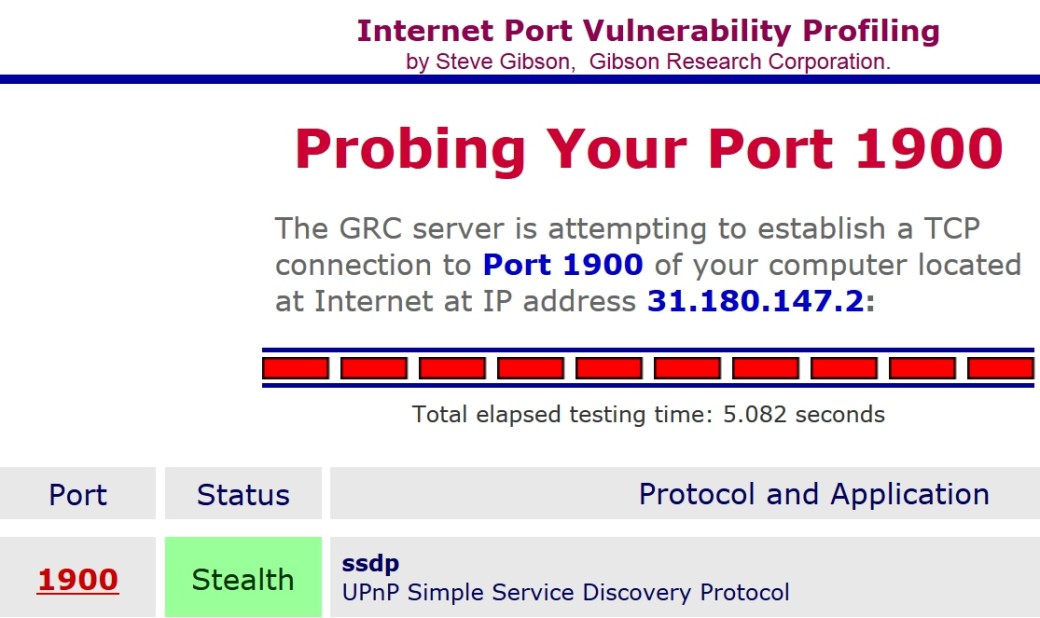
In most cases, the attack against the routers with such hole in UPnP can be launched through a modified SOAP request, which leads to error in data processing and allows the remaining part of the code to get into randomly selected area of router memory, where it runs with root privileges. On home routers, it is better to completely disable UPnP and make sure that the requests to port 1900 are blocked. The service from Steve Gibson, that I already mentioned, can help you to do this.
By default, UPnP (Universal Plug and Play) protocol is enabled on most routers, network printers, IP cameras, NAS and home appliances that are probably “too smart”. It is enabled by default in Windows, OS X, and many versions of Linux. If you can fine-tune its use, it’s not so bad. If the only available options are just ‘enable’ or ‘disable’, it is better to choose the latter.
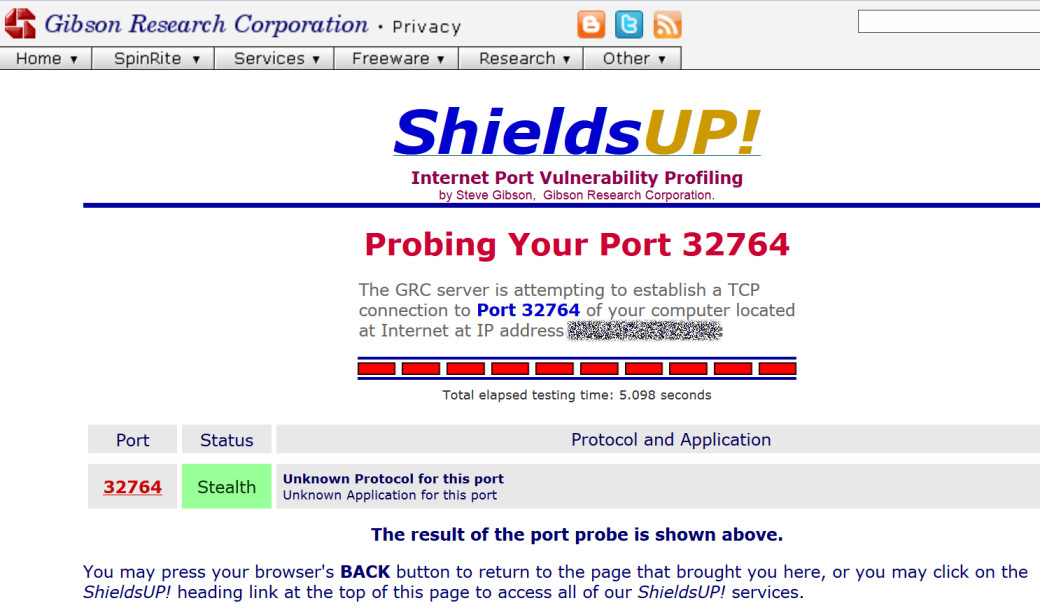
Sometimes, the manufacturers deliberately implement backdoors in their network equipment. Most likely, this is happening at the behest of security services. But, in case of any scandal, the official response always refers to “technical need” or “corporate service to improve communication quality”. Built-in backdoors have been found in some routers from Linksys and Netgear. They opened port 32764 to receive remote commands. Since this number does not correspond to any commonly known service, the issue can be easily detected, for example, by using an external port scanner.
INFO
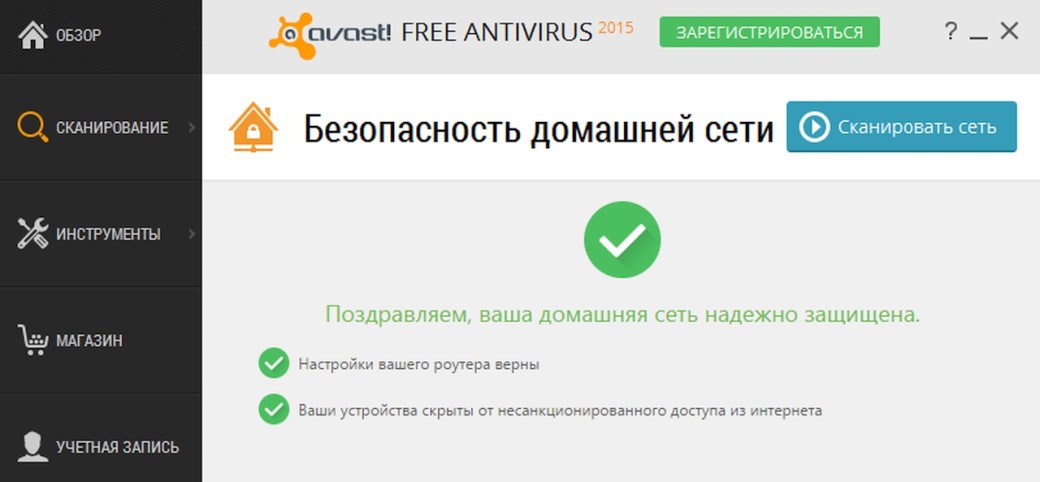
Another way to perform free audit of your home network is to download and run Avast, an antivirus. Its new versions include Network Check, a test wizard that > identifies known vulnerabilities and dangerous network settings.
Default settings are for lambs
Default factory settings of routers continue to be their most common security problem. This is not only about internal IP-addresses that are common for entire series of devices, ‘admin’ used as password and login, but also about some enabled services that increase usability at the expense of security. In addition to UPnP, they also have Telnet, a remote management protocol, and WPS (Wi-Fi Protected Setup) service enabled by default.
The critical bugs are often found in the handling of Telnet requests. For example, D-Link DIR-300 and DIR-600 series routers allowed to get ‘shell’ remotely and run any command via ‘telnetd’ daemon without any authorization. Linksys E1500 and E2500 routers allowed to inject code through a regular ping. They didn’t check ‘ping_size’ setting and, as a result, a backdoor could be created in a router by using one string of code and GET method. In case of E1500, it wasn’t even necessary to try any additional gimmicks during authorization. You could simply specify a new password without entering the current one.
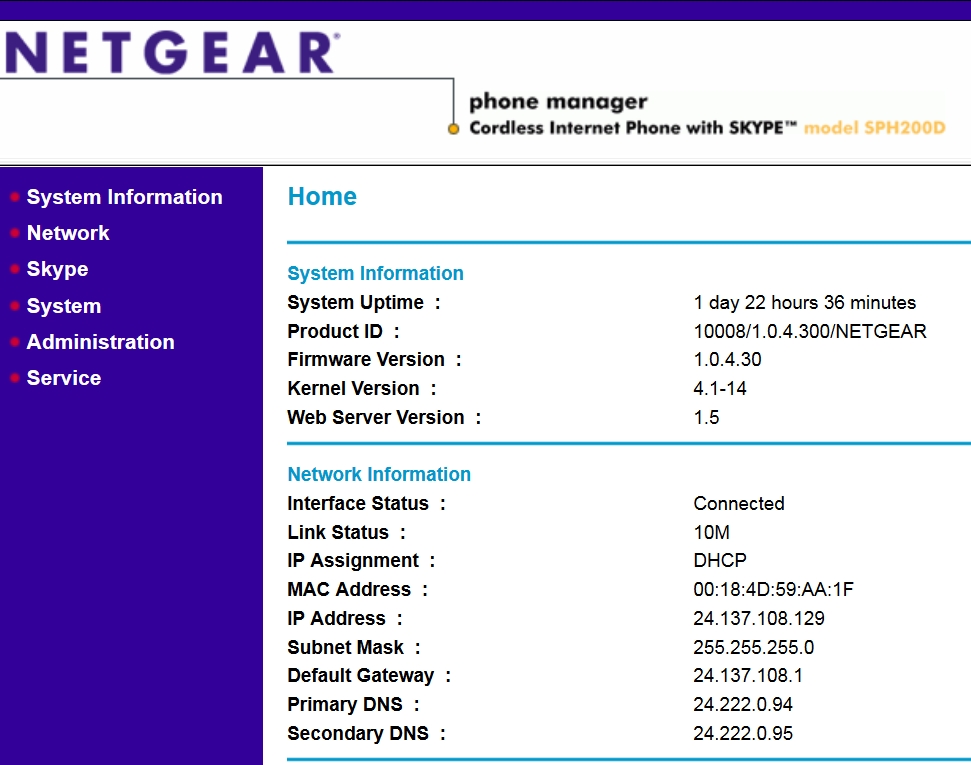
A similar problem was found in Netgear SPH200D, a VoIP phone. In addition, the analysis of firmware revealed that it had an active hidden account named ‘service’ with the same password. With Shodan, you can find a vulnerable router in a couple of minutes. They still allow you to change any of their settings remotely without authorization. You can immediately take advantage of it, or you can do something good: find in Skype this unfortunate user (by IP or by name) and send him a couple of recommendations, for example, to change firmware and read this article.
Supercluster of Massive Holes
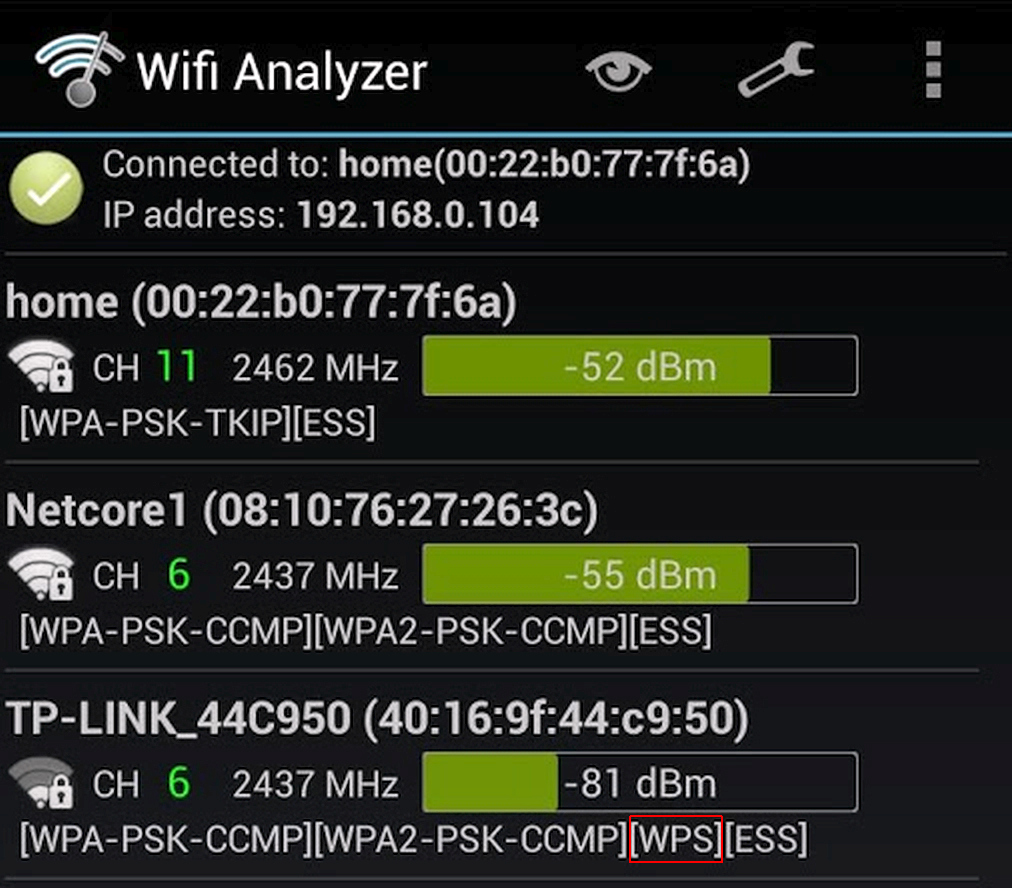
The trouble rarely comes alone, as activating WPS automatically enables UPnP. In addition, the standard PIN code used in WPS or a pre-authentication key negates the advantages of WPA2-PSK cryptographic security.
As a result of firmware bugs, WPS often remains enabled even after you disable it through the web interface. You can find this out by using a Wi-Fi-scanner, such as, Wifi Analyzer, a free application for Android smartphones.
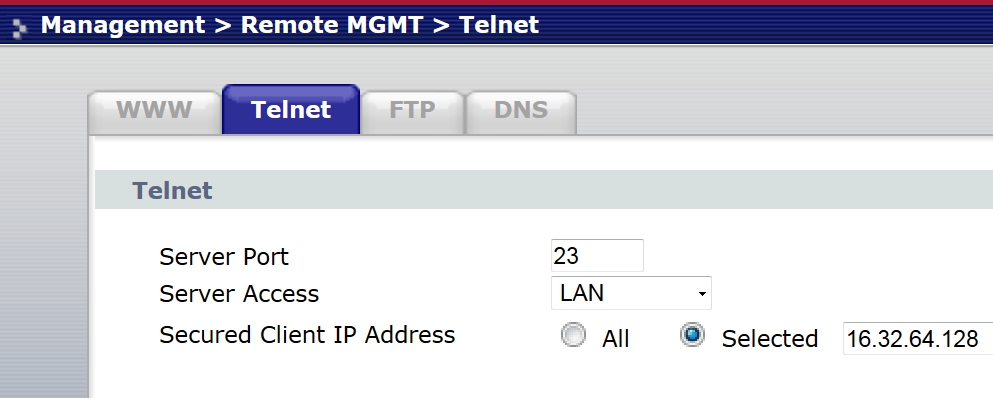
If vulnerable services are used by administrator, they cannot be disabled. Hopefully, the router would at least allow to make them more secure. For example, it can be configured not to accept the commands on WAN port or set a specific IP address for Telnet.
Sometimes, the web interface does not allow to configure or simply disable a dangerous service, and it is impossible to patch the hole with standard tools. In this case, the only solution is to search for new or alternative firmware with advanced features.
Alternative Services
The most popular open source firmware are DD-WRT, OpenWRT and its fork Gargoyle. You can install them only on routers included in the list of supported devices, that is those, for which the chipset manufacturer has disclosed its full specifications.
For example, Asus has a separate series of routers that were originally designed with an eye for the use of DD-WRT (bit.ly/1xfIUSf). These series already have twelve models ranging from entry-level to enterprise-level. MikroTik routers run under RouterOS, which is not inferior to *WRT family in terms of flexibility of settings. This is also a full-fledged network OS based on Linux kernel that supports absolutely all services and every conceivable configuration.
Today, you can install alternative firmware on many routers, but be careful and check the full name of device. While having the same model number and appearance, the routers may have different revisions, which can hide absolutely different hardware platforms.
Testing the Protection
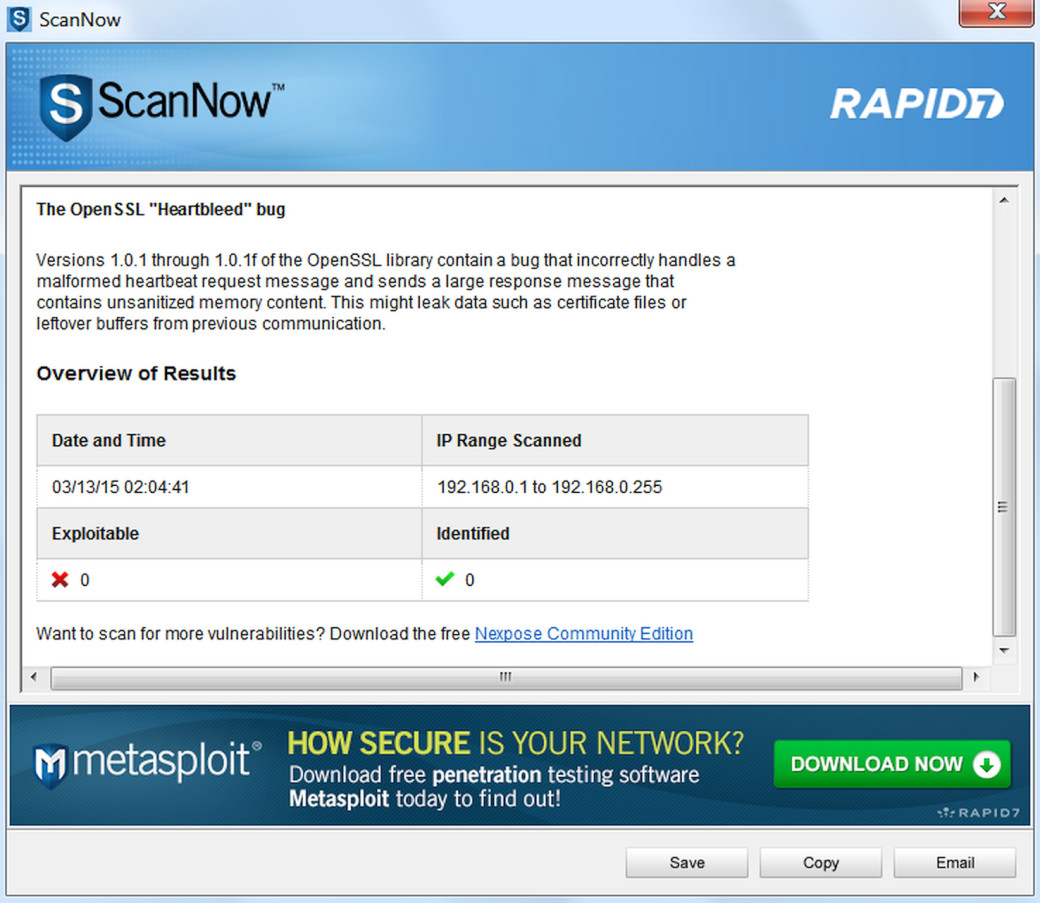
You can test the vulnerability of OpenSSL with ScanNow, a free utility from Rapid7 (bit.ly/18g9TSf), or its simplified online version (bit.ly/1xhVhrM). The > online test takes just a few seconds. In a stand-alone program, you can specify a range of IP addresses, so the test takes a longer time. By the way, the > registration fields of ScanNow are not checked.
After the test, the utility will display a report and offer you to try Nexpose, a more advanced vulnerability scanner oriented to corporate network. It is > available for Windows, Linux and VMware. Depending on the version, the free trial is limited to a period ranging from 7 to 14 days. The restrictions are related > to the number of IP addresses and scan areas.
Unfortunately, the installation of an alternative open source firmware is just a way to improve the protection and it will not provide full security. All firmware versions are modular and combine a number of key components. When they have an issue, it hits millions of devices. For example, a vulnerability in the OpenSSL library also affected the routers with *WRT. Its cryptographic features were used to encrypt SSH remote access sessions, arrange VPN, manage a local web server, and for other popular tasks. The manufacturers begun to release updates pretty quickly, but the issue is still not completely fixed.
New vulnerabilities are constantly found in routers and some of them are exploited even before a fix is released. All that the owner of router can do is to disable unnecessary services, change default settings, restrict remote control, check settings more often and update firmware.

2022.01.12 — First contact. Attacks against contactless cards
Contactless payment cards are very convenient: you just tap the terminal with your card, and a few seconds later, your phone rings indicating that…
Full article →
2023.04.19 — Kung fu enumeration. Data collection in attacked systems
In penetration testing, there's a world of difference between reconnaissance (recon) and data collection (enum). Recon involves passive actions; while enum, active ones. During recon,…
Full article →
2022.06.01 — Routing nightmare. How to pentest OSPF and EIGRP dynamic routing protocols
The magic and charm of dynamic routing protocols can be deceptive: admins trust them implicitly and often forget to properly configure security systems embedded in these protocols. In this…
Full article →
2022.01.13 — Step by Step. Automating multistep attacks in Burp Suite
When you attack a web app, you sometimes have to perform a certain sequence of actions multiple times (e.g. brute-force a password or the second authentication factor, repeatedly…
Full article →
2023.02.13 — First Contact: Attacks on Google Pay, Samsung Pay, and Apple Pay
Electronic wallets, such as Google Pay, Samsung Pay, and Apple Pay, are considered the most advanced and secure payment tools. However, these systems are also…
Full article →
2023.02.21 — SIGMAlarity jump. How to use Sigma rules in Timesketch
Information security specialists use multiple tools to detect and track system events. In 2016, a new utility called Sigma appeared in their arsenal. Its numerous functions will…
Full article →
2022.04.04 — Fastest shot. Optimizing Blind SQL injection
Being employed with BI.ZONE, I have to exploit Blind SQL injection vulnerabilities on a regular basis. In fact, I encounter Blind-based cases even more frequently…
Full article →
2022.06.02 — Blindfold game. Manage your Android smartphone via ABD
One day I encountered a technical issue: I had to put a phone connected to a single-board Raspberry Pi computer into the USB-tethering mode on boot. To do this,…
Full article →
2022.02.09 — Dangerous developments: An overview of vulnerabilities in coding services
Development and workflow management tools represent an entire class of programs whose vulnerabilities and misconfigs can turn into a real trouble for a company using such software. For…
Full article →
2023.07.29 — Invisible device. Penetrating into a local network with an 'undetectable' hacker gadget
Unauthorized access to someone else's device can be gained not only through a USB port, but also via an Ethernet connection - after all, Ethernet sockets…
Full article →